Linux Tutorials on the topic “security”
-
Install and Configure Passbolt Team Password Manager on Ubuntu 20.04
Author: Hitesh Jethva • Tags: linux, security, server, ubuntu, web server • Comments: 3Passbolt is a free, open-source, self-hosted and extensible password manager that helps you to securely share and store login credentials, such as password of the router, website, Wi-Fi, and more.
-
How to Install TeamPass Password Manager on Ubuntu 20.04
Author: Hitesh Jethva • Tags: linux, security, ubuntu • Comments: 1TeamPass is a Collaborative Passwords Manager used for managing passwords and sharing them among team members. In this tutorial, we will be going to show you how to install TeamPass Password Manager on Ubuntu 20.04 with Let's Encrypt SSL.
-
How to Install Matrix Synapse Chat on Ubuntu 20.04 LTS
Author: Muhammad Arul • Tags: linux, nginx, security, server, ubuntu • Comments: 5In this tutorial, we will show you step-by-step how to install and configure Matrix Synapse on Ubuntu 20.04 LTS. Matrix is a new ecosystem for decentralized communication in real time for open federated instant messaging and VoIP services.
-
-
How to Find Active SSH Connections on Linux
Author: Hitesh Jethva • Tags: linux, security • Comments: 0If you are Linux system administrator and responsible for managing servers then you may often need to know how many ssh connections are active on your server and where the connections come from. This tutorial shows you different ways to identify the connections.
-
How to Securely Destroy/Wipe Data on Hard Drives with shred on Linux
Author: Falko Timme • Tags: linux, security • Comments: 20Sometimes you need to destroy or wipe data from hard drives (for example, before you sell your old hard drives on eBay) so that nobody else can access them. Simply deleting data (e.g. with rm) is not enough because that just removes the file system pointer, but not the data, so it can easily be undeleted with recovery software. Even zero'ing out your hard drive might not be enough. Here's where shred comes into play - shred can overwrite the files and partitions repeatedly, in order to make it harder for even very expensive hardware probing to recover the data.
-
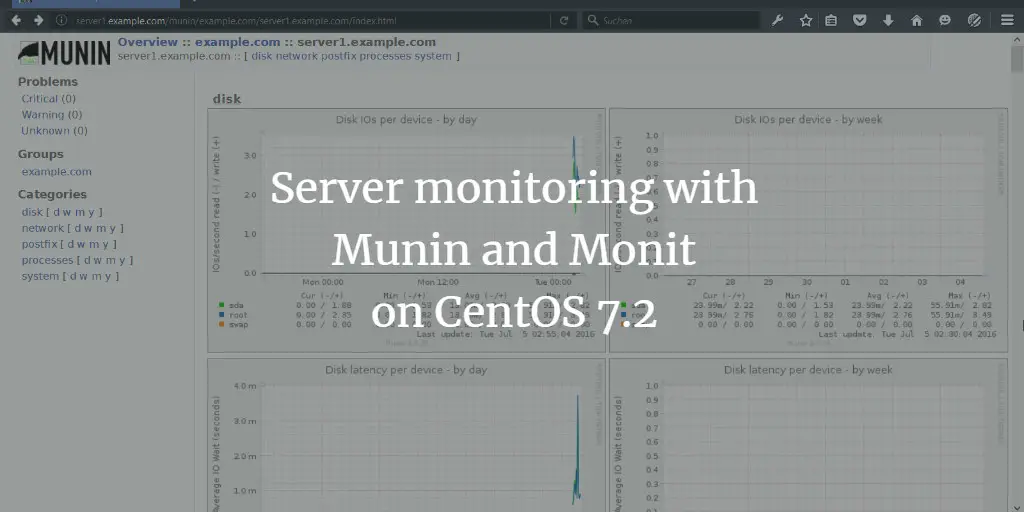
Server monitoring with Munin and Monit on CentOS 7.2
Author: Till Brehm • Tags: centos, monitoring, security • Comments: 9In this article, I will describe how you can monitor your CentOS 7.2 server with Munin and Monit. Munin produces nifty little graphics about nearly every aspect of your server (load average, memory usage, CPU usage, MySQL throughput, eth0 traffic, etc.) without much configuration, whereas Monit checks the availability of services like Apache, MySQL, Postfix and takes the appropriate action such as a restart if it finds a service is not behaving as expected. The combination of the two gives you full monitoring: graphics that lets you recognize current or upcoming problems (like "We need a bigger server soon, our load average is increasing rapidly."), and a watchdog that ensures the availability of the monitored services.
-
How to Install osquery on Debian 10
Author: Hitesh Jethva • Tags: debian, linux, monitoring, security • Comments: 0osquery is a free and open-source tool developed by Facebook that can be used for querying operating system-related information including, memory usage, installed packages, process information, login users, listening ports and many more.
-
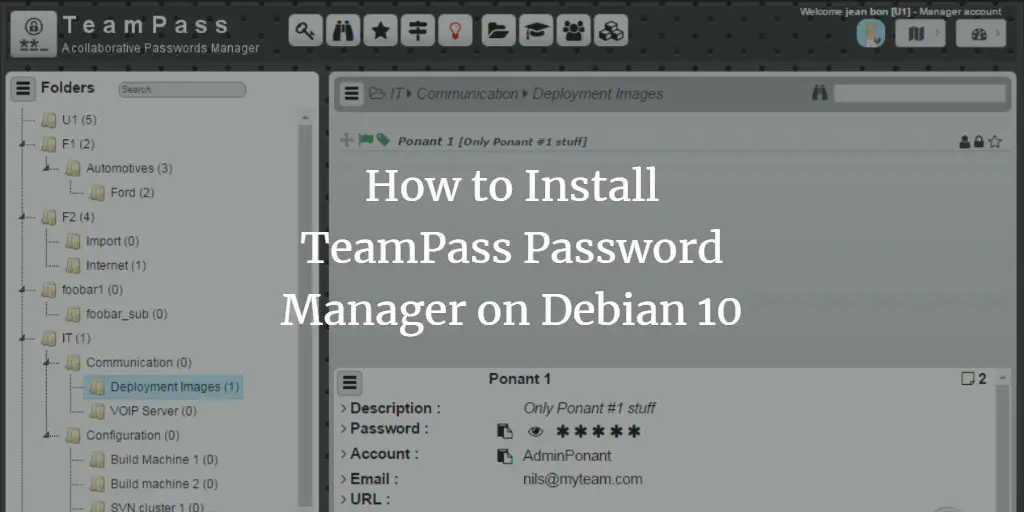
How to Install TeamPass Password Manager on Debian 10
Author: Hitesh Jethva • Tags: debian, linux, security • Comments: 0TeamPass is a collaborative password manager used for managing passwords and sharing them among team members with a specific role. In this tutorial, we will show you how to install TeamPass on Debian 10 and secure it with Let's Encrypt SSL.
-
How to Install and Use AIDE Advanced Intrusion Detection Environment on CentOS 8
Author: Hitesh Jethva • Tags: centos, linux, security • Comments: 0AIDE stands for "Advanced Intrusion Detection Environment" is one of the most popular tools for monitoring changes to Linux-based operating systems. In this tutorial, we will show you how to install and use AIDE to detect intrusions on CentOS 8.
-
How to Setup IKEv2 VPN Using Strongswan and Let's Encrypt on CentOS 8
Author: Muhammad Arul • Tags: centos, linux, security • Comments: 10Strongswan is an open source multiplatform IPSec implementation. It's an IPSec-based VPN solution that focuses on strong authentication mechanisms. In this tutorial, I will show you how to install an IPSec VPN server using Strongswan. We will create an IKEv2 VPN server with the 'EAP-MSCHAPv2' authentication and be using Letsencrypt certificates on CentOS 8 server.