Samba 4 Additional Domain Controller for failover Replication on CentOS 7
In this tutorial, I will show you how to configure an additional domain controller which is one of the key features of SAMBA 4. I will be using the existing Samba 4 server from my previous tutorial as primary domain controller. This setup provides a degree of load balancing and failover for AD services (Ldap schemas and dns ) and configuring it is really easy. We can also use this feature to scale up the environment.
I will be using an existing Samba4 AD server and a new additional server.
Note: In my previous article I used 192.168.1.190 as primary domain controller due to conflict in ipaddress in my lab environment I have changed it to 192.168.1.180.
Servers
- 192.168.1.180, samba4.sunil.cc - Primary Domain Controller Centos7 AD1
- 192.168.1.170,dc.sunil.cc - Secondary Domain Controller or Additional Domain Controller Centos7 AD2
In the tutorial, whenever I denote AD1 refers to primary AD server and AD2 refers to secondary server, then please refer to this link.
Configure Primary Domain Controller
Please refer to this link
Samba 4 with Active directory on CentOS 7 rpm based installation with share support
Configure Secondary Domain Controller
AD2
On server 192.168.1.170,dc.sunil.cc - (Secondary Domain Controller or Additional Domain Controller) do:
We will be using Centos 7 as the basis, SELinux is enabled.
[root@dc ~]# yum -y update
Selinux is enabled.
[root@dc ~]# sestatus SELinux status: enabled SELinuxfs mount: /sys/fs/selinux SELinux root directory: /etc/selinux Loaded policy name: targeted Current mode: enforcing Mode from config file: enforcing Policy MLS status: enabled Policy deny_unknown status: allowed Max kernel policy version: 28 [root@dc ~]#
Make an entry in host file:
Make sure here to add both the primary AD and secondary AD in /etc/hosts
AD1
[root@samba4 ~]# cat /etc/hosts 127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 192.168.1.180 samba4.sunil.cc samba4 192.168.1.170 dc.sunil.cc dc [root@samba4 ~]#
AD2
[root@dc ~]# cat /etc/hosts 127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 192.168.1.180 samba4.sunil.cc samba4 192.168.1.170 dc.sunil.cc dc [root@dc ~]#
Enable the epel repo.
[root@dc ~]# yum install epel-release -y
Install basic packages.
[root@dc ~]# yum install vim wget authconfig krb5-workstation -y
Install the wing repo for samba4 rpms.
[root@dc ~]# cd /etc/yum.repos.d/ [root@dc yum.repos.d]# wget http://wing-net.ddo.jp/wing/7/EL7.wing.repo [root@dc yum.repos.d]# sed -i 's@enabled=0@enabled=1@g' /etc/yum.repos.d/EL7.wing.repo [root@dc yum.repos.d]# yum clean all Loaded plugins: fastestmirror Cleaning repos: base extras updates wing wing-source Cleaning up everything Cleaning up list of fastest mirrors [root@dc yum.repos.d]#
Now installing samba4 packages.
[root@dc yum.repos.d]# yum install -y samba45 samba45-winbind-clients samba45-winbind samba45-client\ samba45-dc samba45-pidl samba45-python samba45-winbind-krb5-locator perl-Parse-Yapp\ perl-Test-Base python2-crypto samba45-common-tools
Modify the resolv.conf , make sure the nameserver is pointed to primary domain controller , here we use 192.168.1.180.
[root@dc ~]# cat /etc/resolv.conf # Generated by NetworkManager search sunil.cc nameserver 192.168.1.180 [root@dc ~]#
Now we remove these files, since we will be creating them later.
[root@dc ~]# rm -rf /etc/krb5.conf [root@dc ~]# rm -rf /etc/samba/smb.conf
Now add the below content in krb5.conf, here our domain name is sunil.cc, realm name is SUNIL.CC.
[root@dc ~]# cat /etc/krb5.conf
[libdefaults]
dns_lookup_realm = false
dns_lookup_kdc = true
default_realm = SUNIL.CC
[root@dc ~]#
Check whether we are able to get the kerberos key from samba4 server.
[root@dc ~]# kinit [email protected] Password for [email protected]: Warning: Your password will expire in 42 days on Sat 15 Jul 2017 10:54:19 PM CEST [root@dc ~]# klist Ticket cache: FILE:/tmp/krb5cc_0 Default principal: [email protected] Valid starting Expires Service principal 06/03/2017 20:33:08 06/04/2017 06:33:08 krbtgt/[email protected] renew until 06/04/2017 20:33:04 [root@dc ~]#
If you dont get the key, make sure time is in sync and please check the resolv.conf.
Now add the server to the existing domain.
[root@dc yum.repos.d]# samba-tool domain join sunil.cc DC -U"SUNIL\administrator" --dns-backend=SAMBA_INTERNAL Finding a writeable DC for domain 'sunil.cc' Found DC samba4.sunil.cc Password for [SUNIL\administrator]: workgroup is SUNIL realm is sunil.cc Adding CN=DC,OU=Domain Controllers,DC=sunil,DC=cc Adding CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sunil,DC=cc Adding CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sunil,DC=cc Adding SPNs to CN=DC,OU=Domain Controllers,DC=sunil,DC=cc Setting account password for DC$ Enabling account Calling bare provision Looking up IPv4 addresses Looking up IPv6 addresses No IPv6 address will be assigned Setting up share.ldb Setting up secrets.ldb Setting up the registry Setting up the privileges database Setting up idmap db Setting up SAM db Setting up sam.ldb partitions and settings Setting up sam.ldb rootDSE Pre-loading the Samba 4 and AD schema A Kerberos configuration suitable for Samba 4 has been generated at /var/lib/samba/private/krb5.conf Provision OK for domain DN DC=sunil,DC=cc Starting replication Schema-DN[CN=Schema,CN=Configuration,DC=sunil,DC=cc] objects[402/1550] linked_values[0/0] Schema-DN[CN=Schema,CN=Configuration,DC=sunil,DC=cc] objects[804/1550] linked_values[0/0] Schema-DN[CN=Schema,CN=Configuration,DC=sunil,DC=cc] objects[1206/1550] linked_values[0/0] Schema-DN[CN=Schema,CN=Configuration,DC=sunil,DC=cc] objects[1550/1550] linked_values[0/0] Analyze and apply schema objects Partition[CN=Configuration,DC=sunil,DC=cc] objects[402/1614] linked_values[0/0] Partition[CN=Configuration,DC=sunil,DC=cc] objects[804/1614] linked_values[0/0] Partition[CN=Configuration,DC=sunil,DC=cc] objects[1206/1614] linked_values[0/0] Partition[CN=Configuration,DC=sunil,DC=cc] objects[1608/1614] linked_values[0/0] Partition[CN=Configuration,DC=sunil,DC=cc] objects[1614/1614] linked_values[30/0] Replicating critical objects from the base DN of the domain Partition[DC=sunil,DC=cc] objects[97/97] linked_values[23/0] Partition[DC=sunil,DC=cc] objects[360/263] linked_values[23/0] Done with always replicated NC (base, config, schema) Replicating DC=DomainDnsZones,DC=sunil,DC=cc Partition[DC=DomainDnsZones,DC=sunil,DC=cc] objects[40/40] linked_values[0/0] Replicating DC=ForestDnsZones,DC=sunil,DC=cc Partition[DC=ForestDnsZones,DC=sunil,DC=cc] objects[18/18] linked_values[0/0] Committing SAM database Sending DsReplicaUpdateRefs for all the replicated partitions Setting isSynchronized and dsServiceName Setting up secrets database Joined domain SUNIL (SID S-1-5-21-2550466525-3862778800-1252273829) as a DC [root@dc yum.repos.d]#
Add the firewall rules.
[root@dc ~]# firewall-cmd --add-port=53/tcp --permanent;firewall-cmd --add-port=53/udp --permanent;firewall-cmd --add-port=88/tcp --permanent;firewall-cmd --add-port=88/udp --permanent; \ firewall-cmd --add-port=135/tcp --permanent;firewall-cmd --add-port=137-138/udp --permanent;firewall-cmd --add-port=139/tcp --permanent; \ firewall-cmd --add-port=389/tcp --permanent;firewall-cmd --add-port=389/udp --permanent;firewall-cmd --add-port=445/tcp --permanent; \ firewall-cmd --add-port=464/tcp --permanent;firewall-cmd --add-port=464/udp --permanent;firewall-cmd --add-port=636/tcp --permanent; \ firewall-cmd --add-port=1024-3500/tcp --permanent;firewall-cmd --add-port=3268-3269/tcp --permanent [root@dc ~]# firewall-cmd --reload
Now add the startup script since the samba4 rpm from wing doesn't have it.
[root@dc ~]# cat /etc/systemd/system/samba.service [Unit] Description= Samba 4 Active Directory After=syslog.target After=network.target [Service] Type=forking PIDFile=/var/run/samba.pid ExecStart=/usr/sbin/samba [Install] WantedBy=multi-user.target [root@dc ~]#
Samba 4 currently doesn't support sysvol replication, this is required for Groups GID Mappings, here is the workaround to fix it:
Need to take up the backup of idmap.ldb and restore.
DC1
Install the package.
[root@samba4 ~]#yum install tdb-tools
Taking a hot backup.
[root@samba4 ~]# tdbbackup -s .bak /var/lib/samba/private/idmap.ldb
Copy the backup file on to DC2.
[root@samba4 ~]# ls -l /var/lib/samba/private/idmap.ldb.bak -rw-------. 1 root root 61440 Jun 3 09:52 /var/lib/samba/private/idmap.ldb.bak [root@samba4 ~]# scp -r /var/lib/samba/private/idmap.ldb.bak [email protected]:/var/lib/samba/private/idmap.ldb
DC2
Now starting samba service.
[root@dc ~]# systemctl enable samba Created symlink from /etc/systemd/system/multi-user.target.wants/samba.service to /etc/systemd/system/samba.service. [root@dc ~]# systemctl start samba
DC1
Change the resolv.conf file to point it to 192.168.1.180.
[root@samba4 ~]# cat /etc/resolv.conf # Generated by NetworkManager search sunil.cc nameserver 192.168.1.180 [root@samba4 ~]#
Creating a link.
[root@samba4 ~]# ln -s /var/lib/samba/private/krb5.conf /etc/krb5.conf
[root@samba4 ~]# cat /etc/krb5.conf
[libdefaults]
default_realm = SUNIL.CC
dns_lookup_realm = false
dns_lookup_kdc = true
[root@samba4 ~]#
Checking the Kerberos ticket now.
[root@samba4 ~]# kinit [email protected] Password for [email protected]: Warning: Your password will expire in 42 days on Sat 15 Jul 2017 10:54:19 PM CEST [root@samba4 ~]# klist Ticket cache: FILE:/tmp/krb5cc_0 Default principal: [email protected] Valid starting Expires Service principal 06/03/2017 22:03:07 06/04/2017 08:03:07 krbtgt/[email protected] renew until 06/04/2017 22:03:03 [root@samba4 ~]#
Now our Additional domain controller is ready, Lets check the replication.
DC2
[root@dc ~]# samba-tool drs showrepl
Default-First-Site-Name\DC
DSA Options: 0x00000001
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
DSA invocationId: e3f76609-f5f0-421d-99ad-38e1fba10b08
==== INBOUND NEIGHBORS ====
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ Sat Jun 3 22:37:24 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 22:37:24 2017 CEST
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ Sat Jun 3 22:37:24 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 22:37:24 2017 CEST
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ Sat Jun 3 22:37:24 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 22:37:24 2017 CEST
DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ Sat Jun 3 22:37:24 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 22:37:24 2017 CEST
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ Sat Jun 3 22:37:24 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 22:37:24 2017 CEST
==== OUTBOUND NEIGHBORS ====
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
==== KCC CONNECTION OBJECTS ====
Connection --
Connection name: 9a2b9a9c-064d-4de1-8c38-20072735de1c
Enabled : TRUE
Server DNS name : samba4.sunil.cc
Server DN name : CN=NTDS Settings,CN=SAMBA4,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sunil,DC=cc
TransportType: RPC
options: 0x00000001
Warning: No NC replicated for Connection!
[root@dc ~]#
DC1
Running the same command.
[root@samba4 private]# samba-tool drs showrepl
Default-First-Site-Name\SAMBA4
DSA Options: 0x00000001
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
DSA invocationId: 745838cd-21e5-4bea-aa28-400a21d59a83
==== INBOUND NEIGHBORS ====
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:53:48 2017 CEST failed, result 2 (WERR_BADFILE)
1 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:53:49 2017 CEST failed, result 2 (WERR_BADFILE)
1 consecutive failure(s).
Last success @ NTTIME(0)
DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:53:49 2017 CEST failed, result 2 (WERR_BADFILE)
1 consecutive failure(s).
Last success @ NTTIME(0)
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:53:49 2017 CEST failed, result 2 (WERR_BADFILE)
1 consecutive failure(s).
Last success @ NTTIME(0)
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:53:49 2017 CEST failed, result 2 (WERR_BADFILE)
1 consecutive failure(s).
Last success @ NTTIME(0)
==== OUTBOUND NEIGHBORS ====
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:57:06 2017 CEST failed, result 2 (WERR_BADFILE)
3 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:57:06 2017 CEST failed, result 2 (WERR_BADFILE)
3 consecutive failure(s).
Last success @ NTTIME(0)
DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:57:06 2017 CEST failed, result 2 (WERR_BADFILE)
3 consecutive failure(s).
Last success @ NTTIME(0)
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:57:02 2017 CEST failed, result 2 (WERR_BADFILE)
2 consecutive failure(s).
Last success @ NTTIME(0)
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:57:02 2017 CEST failed, result 2 (WERR_BADFILE)
2 consecutive failure(s).
Last success @ NTTIME(0)
==== KCC CONNECTION OBJECTS ====
Connection --
Connection name: 9c5f7fe2-3cb7-4bb4-9f46-d2922a7a7ab4
Enabled : TRUE
Server DNS name : dc.sunil.cc
Server DN name : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sunil,DC=cc
TransportType: RPC
options: 0x00000001
Warning: No NC replicated for Connection!
[root@samba4 private]#
If you see this error, then there is an issue with the replication, we will need to reinitate the replication again.
[root@samba4 private]# samba-tool drs replicate samba4.sunil.cc dc.sunil.cc DC=sunil,DC=cc Replicate from dc.sunil.cc to samba4.sunil.cc was successful. [root@samba4 private]#
Now the replication should work fine.
[root@samba4 private]# samba-tool drs showrepl
Default-First-Site-Name\SAMBA4
DSA Options: 0x00000001
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
DSA invocationId: 745838cd-21e5-4bea-aa28-400a21d59a83
==== INBOUND NEIGHBORS ====
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 10:42:04 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 10:42:04 2017 CEST
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 10:42:04 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 10:42:04 2017 CEST
DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 10:42:04 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 10:42:04 2017 CEST
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 10:42:04 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 10:42:04 2017 CEST
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 10:42:04 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 10:42:04 2017 CEST
==== OUTBOUND NEIGHBORS ====
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
==== KCC CONNECTION OBJECTS ====
Connection --
Connection name: 9c5f7fe2-3cb7-4bb4-9f46-d2922a7a7ab4
Enabled : TRUE
Server DNS name : dc.sunil.cc
Server DN name : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sunil,DC=cc
TransportType: RPC
options: 0x00000001
Warning: No NC replicated for Connection!
[root@samba4 private]#
Now testing if the objects are getting replicated between DC1 and DC2.
We will first create a test user in DC2 and see if the user is seen in DC1.
DC2
[root@dc ~]# samba-tool user create howtoforge New Password: Retype Password: User 'howtoforge' created successfully [root@dc ~]# samba-tool user list Administrator howtoforge test_user1 test_user krbtgt Guest [root@dc ~]#
Now checking the same from DC1.
DC1
[root@samba4 ~]# samba-tool user list Administrator howtoforge test_user1 test_user krbtgt Guest [root@samba4 ~]#
Let's now check the DNS replication.
I will be using the same Windows 10 client that I used in my previous tutorial Samba4 domain controller installation from source.
192.168.1.191 remote management Win 10.
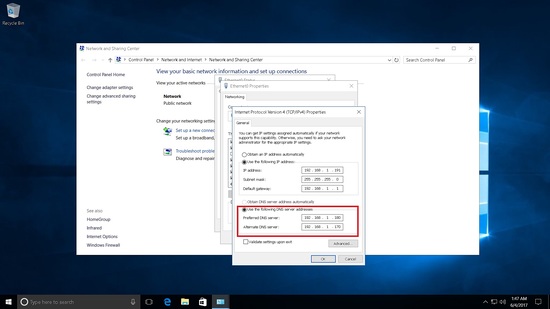
Will add the AD2 server as the secondary DNS.
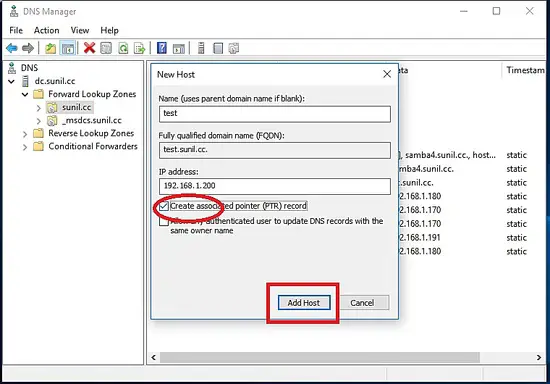
Testing the DNS replication.
Check the name resolution.
[root@samba4 ~]# nslookup test.sunil.cc 192.168.1.170 Server: 192.168.1.170 Address: 192.168.1.170#53 Name: test.sunil.cc Address: 192.168.1.200 [root@samba4 ~]# nslookup test.sunil.cc 192.168.1.180 Server: 192.168.1.180 Address: 192.168.1.180#53 Name: test.sunil.cc Address: 192.168.1.200 [root@samba4 ~]#
This is how DNS and replication is working in Samba 4.