Samba 4 Domain Controller Installation on CentOS 7
Starting from version 4.0, Samba is able to run as an Active Directory (AD) domain controller (DC). In this tutorial, I will show you how to configure Samba 4 as a domain controller with Windows 10, CentOS 7 and CentOS 6 clients.
In this tutorial, I will compile Samba 4 from source. If you are seeking for a Samba 4 RPM based installation and SELinux configuration for Samba 4, please see my new Samba 4 tutorial here.
I will be using 3 Systems, one CentOS 7 server and a Windows 10 client for remote management, a CentOS 7 and CentOS 6 client.
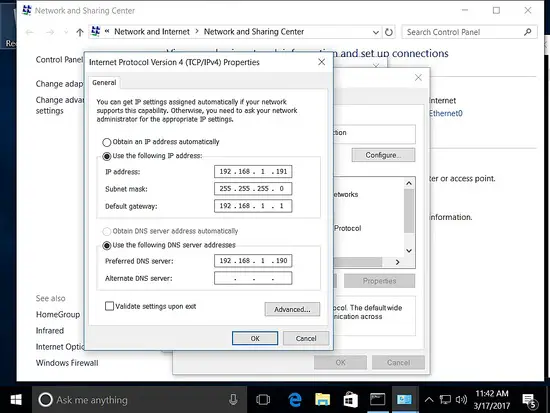
- 192.168.1.190 Samba4 AD centos7
- 192.168.1.191 remote management win 10
- 192.168.1.22 - client Authentication - centos 7
- 192.168.1.192 - client Authentication - centos 6
Installation of Samba 4
192.168.1.190 Samba4 AD centos 7
Basis is a CentOS 7 with a minimal install and SELinux disabled.
[root@samba4 ~]# sestatus
SELinux status: disabled
[root@samba4 ~]#
Make an entry in the /etc/hosts file.
[root@samba4 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.1.190 samba4.sunil.cc samba4
[root@samba4 ~]#
Install the epel repo.
[root@samba4 ~]# yum install epel-release -y
Install all the packages needed to compile samba4.
[root@samba4 ~]# yum install perl gcc libacl-devel libblkid-devel gnutls-devel readline-devel python-devel gdb pkgconfig krb5-workstation zlib-devel setroubleshoot-server libaio-devel setroubleshoot-plugins\ policycoreutils-python libsemanage-python setools-libs-python setools-libs popt-devel libpcap-devel sqlite-devel libidn-devel libxml2-devel libacl-devel libsepol-devel libattr-devel keyutils-libs-devel\ cyrus-sasl-devel cups-devel bind-utils libxslt docbook-style-xsl openldap-devel pam-devel bzip2 vim wget -y
Now download samba4 package . I use samba-4.6.0 which is latest during this setup.
[root@samba4 ~]# wget https://download.samba.org/pub/samba/stable/samba-4.6.0.tar.gz
Now lets install samba4.
[root@samba4 ~]# tar -zxvf samba-4.6.0.tar.gz [root@samba4 ~]# cd samba-4.6.0 [root@samba4 samba-4.6.0]# ./configure --enable-debug --enable-selftest --with-ads --with-systemd --with-winbind [root@samba4 samba-4.6.0]# make && make install
The installation will take about 10 minutes depending on the system speed.
Now we will do the domain provisioning.
[root@samba4 samba]# samba-tool domain provision --use-rfc2307 --interactive
Realm [SUNIL.CC]:
Domain [SUNIL]:
Server Role (dc, member, standalone) [dc]: dc
DNS backend (SAMBA_INTERNAL, BIND9_FLATFILE, BIND9_DLZ, NONE) [SAMBA_INTERNAL]:
DNS forwarder IP address (write 'none' to disable forwarding) [4.2.2.1]:
Administrator password:
Retype password:
Looking up IPv4 addresses
Looking up IPv6 addresses
No IPv6 address will be assigned
Setting up share.ldb
Setting up secrets.ldb
Setting up the registry
Setting up the privileges database
Setting up idmap db
Setting up SAM db
Setting up sam.ldb partitions and settings
Setting up sam.ldb rootDSE
Pre-loading the Samba 4 and AD schema
Adding DomainDN: DC=sunil,DC=cc
Adding configuration container
Setting up sam.ldb schema
Setting up sam.ldb configuration data
Setting up display specifiers
Modifying display specifiers
Adding users container
Modifying users container
Adding computers container
Modifying computers container
Setting up sam.ldb data
Setting up well known security principals
Setting up sam.ldb users and groups
ERROR(ldb): uncaught exception - operations error at ../source4/dsdb/samdb/ldb_modules/password_hash.c:2820
File "/usr/local/samba/lib64/python2.7/site-packages/samba/netcmd/__init__.py", line 176, in _run
return self.run(*args, **kwargs)
File "/usr/local/samba/lib64/python2.7/site-packages/samba/netcmd/domain.py", line 471, in run
nosync=ldap_backend_nosync, ldap_dryrun_mode=ldap_dryrun_mode)
File "/usr/local/samba/lib64/python2.7/site-packages/samba/provision/__init__.py", line 2175, in provision
skip_sysvolacl=skip_sysvolacl)
File "/usr/local/samba/lib64/python2.7/site-packages/samba/provision/__init__.py", line 1787, in provision_fill
next_rid=next_rid, dc_rid=dc_rid)
File "/usr/local/samba/lib64/python2.7/site-packages/samba/provision/__init__.py", line 1447, in fill_samdb
"KRBTGTPASS_B64": b64encode(krbtgtpass.encode('utf-16-le'))
File "/usr/local/samba/lib64/python2.7/site-packages/samba/provision/common.py", line 55, in setup_add_ldif
ldb.add_ldif(data, controls)
File "/usr/local/samba/lib64/python2.7/site-packages/samba/__init__.py", line 225, in add_ldif
self.add(msg, controls)
[root@samba4 samba]#
There will be some errors when we do the provisioning of domain.
To fix them, please comment out the below line in /etc/krb5.conf.
-------- #includedir /etc/krb5.conf.d/ --------
Run the domain provisioning again and now the domain will get created without errors.
[root@samba4 etc]# samba-tool domain provision --use-rfc2307 --interactive Realm [SUNIL.CC]: Domain [SUNIL]: Server Role (dc, member, standalone) [dc]: DNS backend (SAMBA_INTERNAL, BIND9_FLATFILE, BIND9_DLZ, NONE) [SAMBA_INTERNAL]: DNS forwarder IP address (write 'none' to disable forwarding) [4.2.2.1]: Administrator password: Retype password: Looking up IPv4 addresses Looking up IPv6 addresses No IPv6 address will be assigned Setting up secrets.ldb Setting up the registry Setting up the privileges database Setting up idmap db Setting up SAM db Setting up sam.ldb partitions and settings Setting up sam.ldb rootDSE Pre-loading the Samba 4 and AD schema Adding DomainDN: DC=sunil,DC=cc Adding configuration container Setting up sam.ldb schema Setting up sam.ldb configuration data Setting up display specifiers Modifying display specifiers Adding users container Modifying users container Adding computers container Modifying computers container Setting up sam.ldb data Setting up well known security principals Setting up sam.ldb users and groups Setting up self join Adding DNS accounts Creating CN=MicrosoftDNS,CN=System,DC=sunil,DC=cc Creating DomainDnsZones and ForestDnsZones partitions Populating DomainDnsZones and ForestDnsZones partitions Setting up sam.ldb rootDSE marking as synchronized Fixing provision GUIDs A Kerberos configuration suitable for Samba AD has been generated at /usr/local/samba/private/krb5.conf Setting up fake yp server settings Once the above files are installed, your Samba4 server will be ready to use Server Role: active directory domain controller Hostname: samba4 NetBIOS Domain: SUNIL DNS Domain: sunil.cc DOMAIN SID: S-1-5-21-2936486394-2075362935-551615353 [root@samba4 etc]#
Make sure the ports are open in the firewall.
[root@samba4 etc]#firewall-cmd --add-port=53/tcp --permanent;firewall-cmd --add-port=53/udp --permanent;firewall-cmd --add-port=88/tcp --permanent;firewall-cmd --add-port=88/udp --permanent; \ firewall-cmd --add-port=135/tcp --permanent;firewall-cmd --add-port=137-138/udp --permanent;firewall-cmd --add-port=139/tcp --permanent; \ firewall-cmd --add-port=389/tcp --permanent;firewall-cmd --add-port=389/udp --permanent;firewall-cmd --add-port=445/tcp --permanent; \ firewall-cmd --add-port=464/tcp --permanent;firewall-cmd --add-port=464/udp --permanent;firewall-cmd --add-port=636/tcp --permanent; \ firewall-cmd --add-port=1024-5000/tcp --permanent;firewall-cmd --add-port=3268-3269/tcp --permanent [root@samba4 ~]# firewall-cmd --reload
Create a startup script to autostart the service during reboot.
[root@samba4 ~]# cat /etc/systemd/system/samba.service [Unit] Description= Samba 4 Active Directory After=syslog.target After=network.target [Service] Type=forking PIDFile=/usr/local/samba/var/run/samba.pid ExecStart=/usr/local/samba/sbin/samba [Install] WantedBy=multi-user.target [root@samba4 ~]# [root@samba4 ~]# systemctl enable samba Created symlink from /etc/systemd/system/multi-user.target.wants/samba.service to /etc/systemd/system/samba.service. [root@samba4 ~]# systemctl start samba
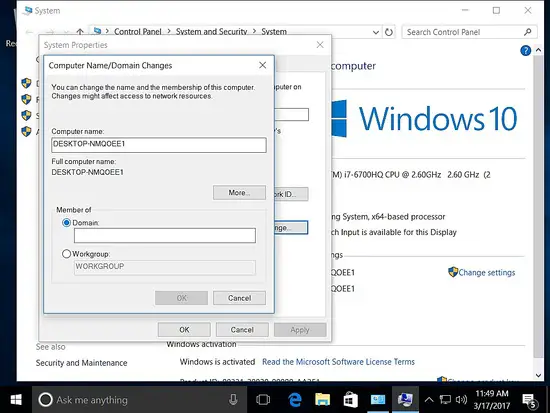
Adding the Windows host to the domain
192.168.1.191 remote management win 10
Make sure the host is added with a static ipaddress.
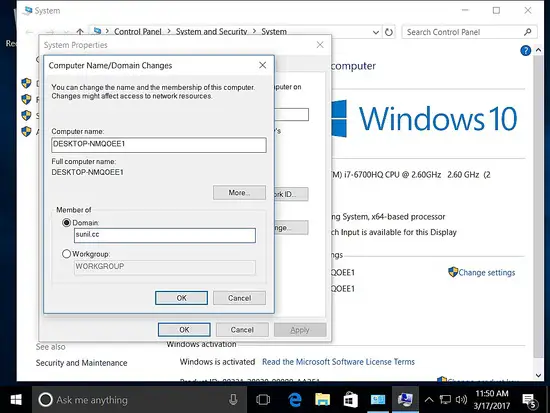
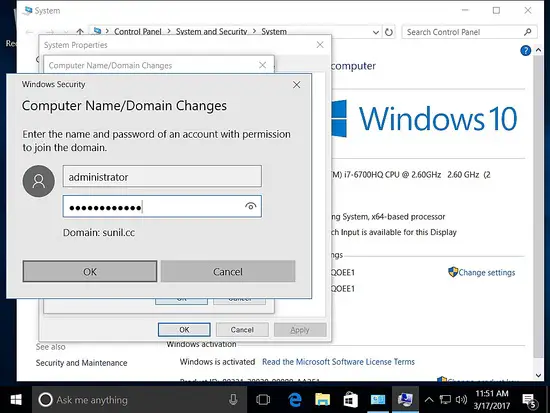
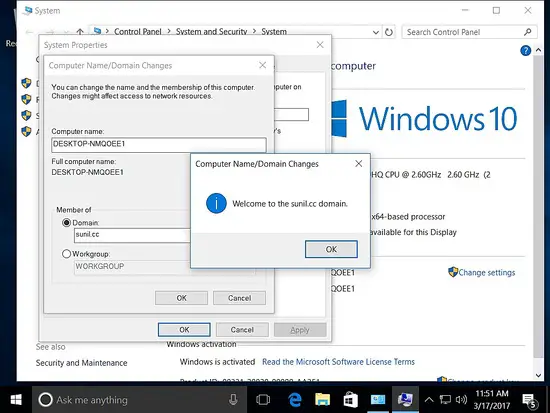
Adding the host to the domain.
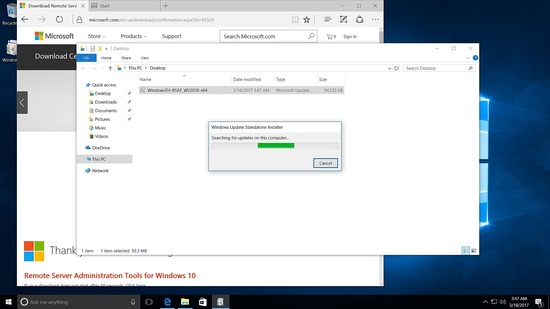
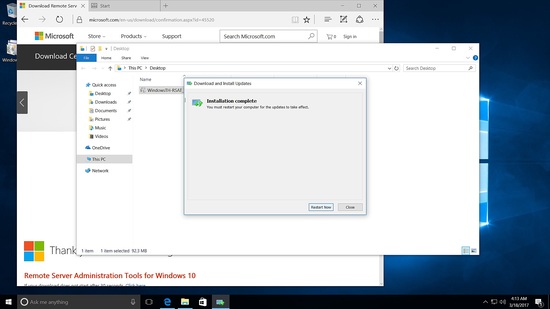
To manage Samba4 from Windows, we need to have the Microsoft Remote Server Tools (RSAT) installed.
The wiki page has the links https://wiki.samba.org/index.php/Installing_RSAT
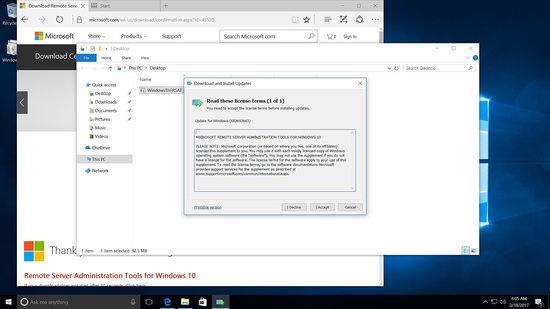
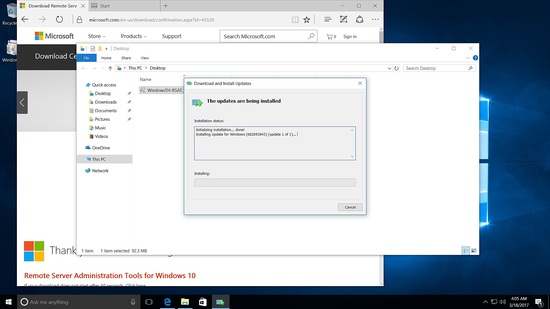
Installing RSAT tool in Windows 10
Run the installer.
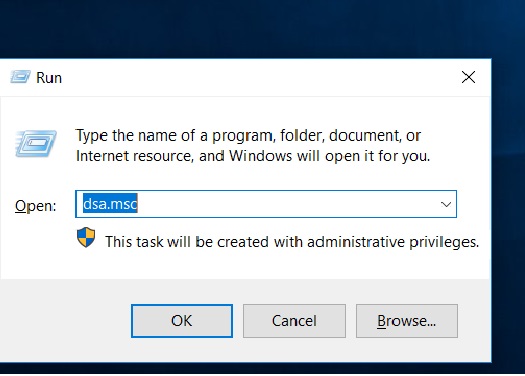
After reboot go to run and type in dsa.msc
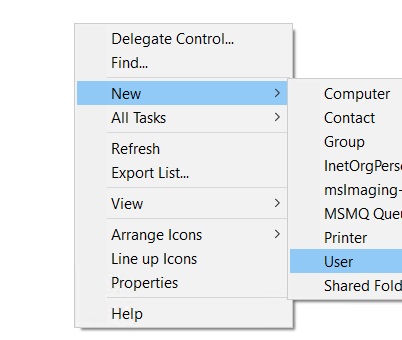
Click on sunil.cc domain and right click new -> Users.
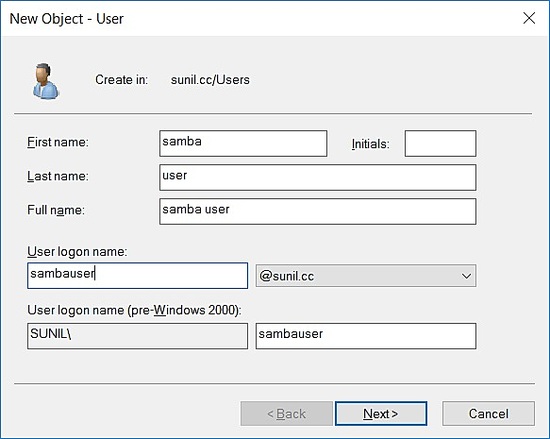
Creating a test user.
Client authentication with Samba 4 on CentOS 7
192.168.1.22 - client Authentication on CentOS 7
Installation of packages:
[root@centos7 ~]# yum -y install realmd sssd oddjob oddjob-mkhomedir adcli samba-common
Check connectivity with samba4:
[root@centos7 ~]# realm discover SUNIL.CC sunil.cc type: kerberos realm-name: SUNIL.CC domain-name: sunil.cc configured: kerberos-member server-software: active-directory client-software: sssd required-package: oddjob required-package: oddjob-mkhomedir required-package: sssd required-package: adcli required-package: samba-common-tools login-formats: %U login-policy: allow-realm-logins [root@centos7 ~]#
Joining the domain.
[root@centos7 ~]# realm join SUNIL.CC Password for Administrator: [root@centos7 ~]#
Check whether we are able to get the user from samba4.
[root@centos7 ~]# id SUNIL\\testuser uid=1570001104([email protected]) gid=1570000513(domain [email protected]) groups=1570000513(domain [email protected]) [root@centos7 ~]#
Configure sssd.
[root@centos7 ~]# cat /etc/sssd/sssd.conf [sssd] domains = sunil.cc config_file_version = 2 services = nss, pam [domain/sunil.cc] ad_domain = sunil.cc krb5_realm = SUNIL.CC realmd_tags = manages-system joined-with-samba cache_credentials = True id_provider = ad krb5_store_password_if_offline = True default_shell = /bin/bash ldap_id_mapping = True use_fully_qualified_names = True fallback_homedir = /home/%u@%d access_provider = ad [root@centos7 ~]#
Restart sssd.
[root@centos7 ~]# systemctl restart sssd [root@centos7 ~]# systemctl enable sssd
Check the user.
[root@centos7 ~]# id [email protected] uid=1570001105([email protected]) gid=1570000513(domain [email protected]) groups=1570000513(domain [email protected]),1570000512(domain [email protected]),1570000572(denied rodc password replication [email protected]) [root@centos7 ~]#
To get the user without domain name.
[root@centos7 ~]# vim /etc/sssd/sssd.conf ----------- ------------ use_fully_qualified_names = False ----------- -----------
Restart sssd and check id command.
[root@centos7 ~]# systemctl restart sssd [root@centos7 ~]# id sambauser uid=1570001105(sambauser) gid=1570000513(domain users) groups=1570000513(domain users),1570000512(domain admins),1570000572(denied rodc password replication group) [root@centos7 ~]#
Client authentication with Samba 4 on CentOS 6
192.168.1.192 - client Authentication on CentOS 6.
Installation of packages.
[root@centos6 db]# yum install pam pam_ldap pam_krb5 sssd sssd-ldap sssd-common authconfig oddjob oddjob-mkhomedir openldap openldap-clients krb5-workstation adcli -y
Change the kerberos config file.
[root@centos6 db]# cat /etc/krb5.conf
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = SUNIL.CC
dns_lookup_realm = false
dns_lookup_kdc = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
[realms]
SUNIL.CC = {
kdc = samba4.sunil.cc
admin_server = samba4.sunil.cc
}
[domain_realm]
.sunil.cc = SUNIL.CC
sunil.cc = SUNIL.CC
[root@centos6 db]#
We will use adcli command to join the domain.
[root@centos6 db]# adcli info sunil.cc [domain] domain-name = sunil.cc domain-short = SUNIL domain-forest = sunil.cc domain-controller = samba4.sunil.cc domain-controller-site = Default-First-Site-Name domain-controller-flags = pdc gc ldap ds kdc timeserv closest writable good-timeserv full-secret domain-controller-usable = yes domain-controllers = samba4.sunil.cc [computer] computer-site = Default-First-Site-Name [root@centos6 db]# [root@centos6 db]# adcli join sunil.cc Password for [email protected]: [root@centos6 db]#
Make sure the kerberos ticket is created.
[root@centos6 db]# klist -ke
Configure authentication.
[root@centos6 db]# authconfig --enablesssd --enablesssdauth --enablemkhomedir --update
Modify the sssd config now to do the authentication.
[root@centos6 db]# cat /etc/sssd/sssd.conf [sssd] services = nss, pam, ssh, autofs config_file_version = 2 domains = sunil.cc [domain/sunil.cc] id_provider = ad # Uncomment if service discovery is not working # ad_server = server.win.example.com default_shell = /bin/bash fallback_homedir = /home/%u [root@centos6 db]#
Restart sssd service.
[root@centos6 db]# chkconfig sssd on [root@centos6 db]# service sssd restart Stopping sssd: [ OK ] Starting sssd: [ OK ] [root@centos6 db]#
Validating user.
[root@centos6 db]# id sambauser uid=1570001105(sambauser) gid=1570000513(domain users) groups=1570000513(domain users),1570000512(domain admins),1570000572(denied rodc password replication group) [root@centos6 db]#