ISP-Server Setup - Ubuntu 5.0.4 "The Hoary Hedgehog" - Page 4
MySQL
apt-get install mysql-server mysql-client libmysqlclient12-dev
mysqladmin -u root password yourrootsqlpassword
mysqladmin -h server1.example.com -u root password yourrootsqlpassword
When you run netstat -tap you should now see a line like this:
tcp 0 0 localhost.localdo:mysql *:* LISTEN 2449/mysqld |
which means that MySQL is accessible on port 3306. You can go to the next section (Postfix). If you do not see this line, edit /etc/mysql/my.cnf and comment out skip-networking:
# skip-networking |
If you had to edit /etc/mysql/my.cnf you have to restart MySQL:
/etc/init.d/mysql restart
Postfix
In order to install Postfix with SMTP-AUTH and TLS do the following steps:
apt-get install postfix postfix-tls libsasl2 sasl2-bin libsasl2-modules libdb3-util procmail (1 line!)
dpkg-reconfigure postfix
<- Internet Site
<- NONE
<- server1.example.com
<- server1.example.com, localhost.example.com, localhost
<- No
<- 127.0.0.0/8
<- 0
<- +
postconf -e 'smtpd_sasl_local_domain ='
postconf -e 'smtpd_sasl_auth_enable = yes'
postconf -e 'smtpd_sasl_security_options = noanonymous'
postconf -e 'broken_sasl_auth_clients = yes'
postconf -e 'smtpd_recipient_restrictions = permit_sasl_authenticated,permit_mynetworks,reject_unauth_destination'
postconf -e 'inet_interfaces = all'
echo 'pwcheck_method: saslauthd' >> /etc/postfix/sasl/smtpd.conf
echo 'mech_list: plain login' >> /etc/postfix/sasl/smtpd.conf
mkdir /etc/postfix/ssl
cd /etc/postfix/ssl/
openssl genrsa -des3 -rand /etc/hosts -out smtpd.key 1024
chmod 600 smtpd.key
openssl req -new -key smtpd.key -out smtpd.csr
openssl x509 -req -days 3650 -in smtpd.csr -signkey smtpd.key -out smtpd.crt
openssl rsa -in smtpd.key -out smtpd.key.unencrypted
mv -f smtpd.key.unencrypted smtpd.key
openssl req -new -x509 -extensions v3_ca -keyout cakey.pem -out cacert.pem -days 3650
postconf -e 'smtpd_tls_auth_only = no'
postconf -e 'smtp_use_tls = yes'
postconf -e 'smtpd_use_tls = yes'
postconf -e 'smtp_tls_note_starttls_offer = yes'
postconf -e 'smtpd_tls_key_file = /etc/postfix/ssl/smtpd.key'
postconf -e 'smtpd_tls_cert_file = /etc/postfix/ssl/smtpd.crt'
postconf -e 'smtpd_tls_CAfile = /etc/postfix/ssl/cacert.pem'
postconf -e 'smtpd_tls_loglevel = 1'
postconf -e 'smtpd_tls_received_header = yes'
postconf -e 'smtpd_tls_session_cache_timeout = 3600s'
postconf -e 'tls_random_source = dev:/dev/urandom'
postconf -e 'myhostname = server1.example.com'
The file /etc/postfix/main.cf should now look like this:
# See /usr/share/postfix/main.cf.dist for a commented, more complete version |
/etc/init.d/postfix restart
Authentication will be done by saslauthd. We have to change a few things to make it work properly. Because Postfix runs chrooted in /var/spool/postfix we have to do the following:
mkdir -p /var/spool/postfix/var/run/saslauthd
rm -fr /var/run/saslauthd
Now we have to edit /etc/default/saslauthd in order to activate saslauthd. Remove # in front of START=yes and add the line PARAMS="-m /var/spool/postfix/var/run/saslauthd":
# This needs to be uncommented before saslauthd will be run automatically |
Finally we have to edit /etc/init.d/saslauthd. Change the line
dir=`dpkg-statoverride --list $PWDIR` |
to
#dir=`dpkg-statoverride --list $PWDIR` |
Then change the variables PWDIR and PIDFILE and add the variable dir at the beginning of the file:
PWDIR="/var/spool/postfix/var/run/${NAME}"
|
/etc/init.d/saslauthd should now look like this:
#!/bin/sh -e |
Now start saslauthd:
/etc/init.d/saslauthd start
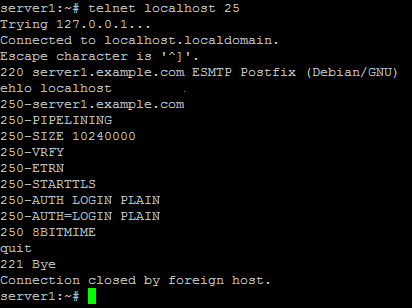
To see if SMTP-AUTH and TLS work properly now run the following command:
telnet localhost 25
After you have established the connection to your postfix mail server type
ehlo localhost
If you see the lines
250-STARTTLS
and
250-AUTH
everything is fine.
Type
quit
to return to the system's shell.
Courier-IMAP/Courier-POP3
Install Courier-IMAP/Courier-IMAP-SSL (for IMAPs on port 993) and Courier-POP3/Courier-POP3-SSL (for POP3s on port 995).
apt-get install courier-authdaemon courier-base courier-imap courier-imap-ssl courier-pop courier-pop-ssl courier-ssl gamin libgamin0 libglib2.0-0 (one line!)
<- No
<- OK
Then configure Postfix to deliver emails to a user's Maildir:
postconf -e 'home_mailbox = Maildir/'
postconf -e 'mailbox_command ='
/etc/init.d/postfix restart
Please go sure to enable Maildir under Management -> Settings -> EMail in the ISPConfig web interface.