Virtualization With KVM On A Fedora 17 Server - Page 2
On this page
5 Connecting To The Guest
Fedora 17 Desktop:
The KVM guest will now boot from the Debian Squeeze Netinstall CD and start the Debian installer - that's why we need to connect to the graphical console of the guest. You can do this with virt-manager on the Fedora 17 desktop.
Go to Applications > System Tools > Virtual Machine Manager to start virt-manager:
Type in your password:
When you start virt-manager for the first time, you will most likely see the message Unable to open a connection to the libvirt management daemon. You can ignore this because we don't want to connect to the local libvirt daemon, but to the one on our Fedora 17 KVM host. Click on Close and go to File > Add Connection... to connect to our Fedora 17 KVM host:
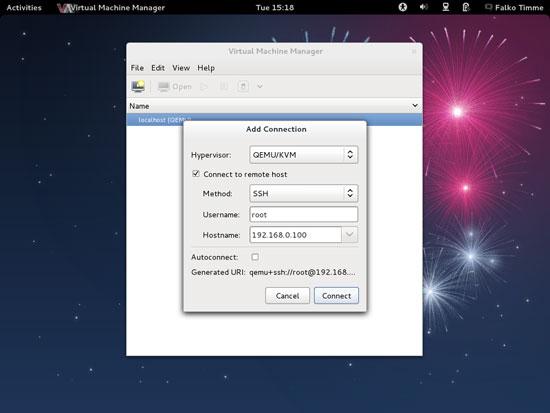
Select QEMU/KVM as Hypervisor, then check Connect to remote host, select SSH in the Method drop-down menu, type in root as the Username and the hostname (server1.example.com) or IP address (192.168.0.100) of the Fedora 17 KVM host in the Hostname field. Then click on Connect:
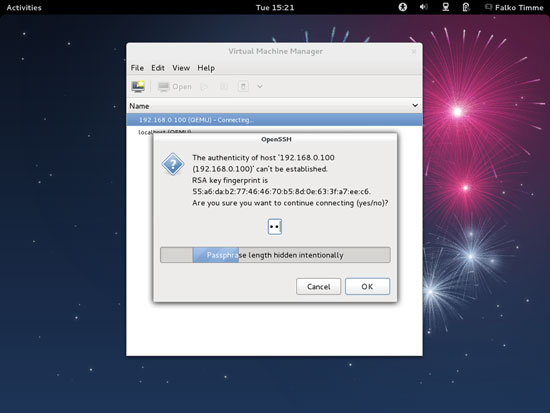
If this is the first connection to the remote KVM server, you must type in yes and click on OK:
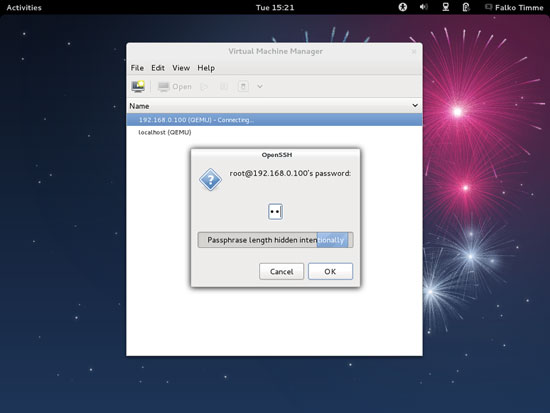
Afterwards type in the root password of the Fedora 17 KVM host:
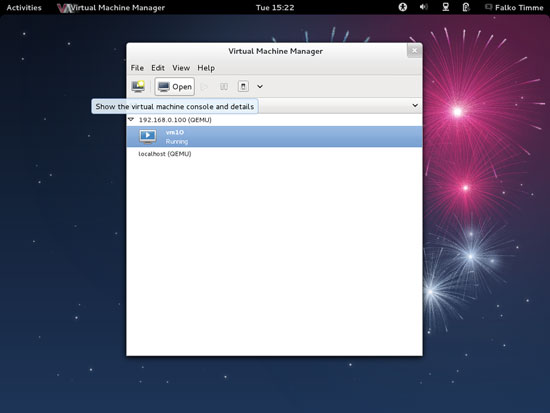
You should see vm10 as running. Mark that guest and click on the Open button to open the graphical console of the guest:
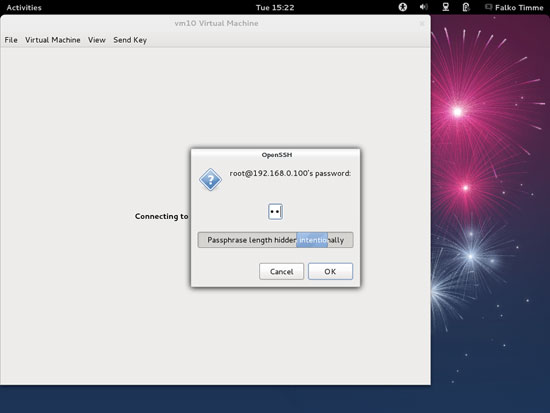
Type in the root password of the KVM host again:
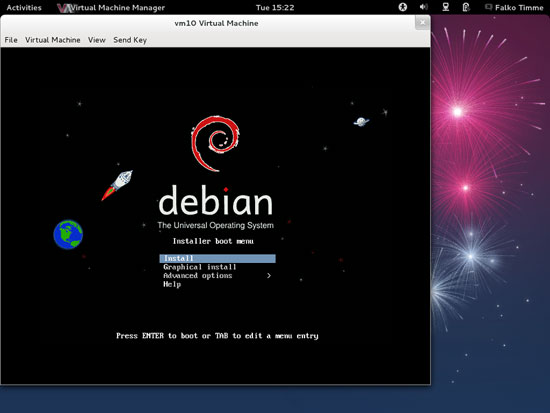
You should now be connected to the graphical console of the guest and see the Debian installer:
Now install Debian as you would normally do on a physical system. Please note that at the end of the installation, the Debian guest needs a reboot. The guest will then stop, so you need to start it again, either with virt-manager or like this on our Fedora 17 KVM host command line:
Fedora 17 KVM Host:
virsh --connect qemu:///system
start vm10
quit
Afterwards, you can connect to the guest again with virt-manager and configure the guest. If you install OpenSSH (package openssh-server) in the guest, you can connect to it with an SSH client (such as PuTTY).