How to Install Icinga 2 Monitoring Tool on Debian 9.2
This tutorial exists for these OS versions
- Debian 12 (Bookworm)
- Debian 11 (Bullseye)
- Debian 10 (Buster)
- Debian 9 (Stretch)
On this page
In this guide we will discuss how to install and configure the latest version Icinga 2 web monitoring tool in Debian 9.2 release, in order to monitor all important network infrastructure devices, such as physical or virtual servers or VMs, routers, switches, firewall appliances and other network IoT devices. It can also monitor the state of network protocols, such as HTTP, FTP, SMTP, IMAP or other network services, hosts resources, physical sensors, as well as software, CPU load, memory, disk space etc. and almost all inter-connected network devices via ICMP or ping requests.
Icinga, at origin a fork of Nagios monitoring system, is an Open-Source modern network monitoring application, written in PHP and highly deployed in Linux under Apache/Nginx, PHP and MySQL/MariaDB components, also known as LAMP or LEMP stacks. Icinga 2 can be configured to notify system or network administrators via mail, SMS, chat, or other types of alerts about network, systems, services or other related network outage and can also generate graphics about network downtime or performance.
Requirements
- Debian 9.2 installed on a bare-metal machine or on a virtual private server.
- One of the server’s network interfaces cards configured with a static IP address.
- Direct access to root account via console or remotely via SSH service or sudo root privileges on a local or remote account.
- A domain name, private or public, depending on your deployment, with the proper DNS records configured for web services.
- A mail service properly configured at your premises in order to send mail alerts.
Initial Configuration
Before starting to install and configure Icinga 2 web monitoring tool on your own server, first assure the system meets all the software requirements for compiling and installing the application. On the first step, update your system repositories and software packages by issuing the below command.
apt update
apt upgrade
In the next step, execute the following command in order to install some necessary utilities that will be used to further manage your system from command line.
apt install wget bash-completion unzip
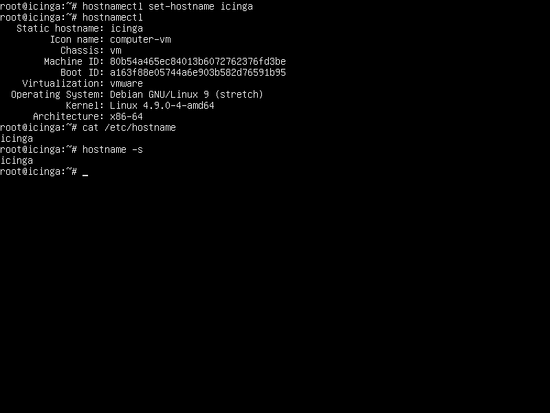
Next, setup the hostname for your system by executing the following command. Replace your hostname variable accordingly.
hostnamectl set-hostname icinga
Verify machine hostname and hosts file by issuing the below commands.
hostnamectl
cat /etc/hostname
hostname –s
Finally, reboot Debian server in order to apply kernel updates and the hostname changes properly.
init 6
Icinga 2 is a network monitoring application which can be configured from web and its functionality is mainly based on PHP server-side programming language. In order to execute application’s PHP file scripts, a web server, such as Apache HTTP server, and a PHP processing gateway must be installed and operational in the system. In order to install Apache web server and the PHP interpreter alongside with all required PHP modules needed by Icinga to run properly, issue the following command in your server console.
apt install apache2 libapache2-mod-php7.0 php7.0-xml php7.0-opcache php7.0-xml php7.0-mbstring php7.0-json php7.0-curl php7.0-ldap php7.0-cli php7.0-gd php7.0-intl php7.0-readline
After Apache and PHP have been installed, test if the web server is up and running and listening for network connections on port 80 by issuing the following command with root privileges.
netstat –tlpn
In case netstat network utility is not installed by default in your Debian system, execute the below command to install it.
apt install net-tools
By inspecting the netstat command output you can see that Apache web server is listening for incoming network connections on port 80. For the same task, you can also use the ss command, which is automatically installed by default on Debian 9.
ss- tulpn
In case you have a firewall enabled in your system, such as UFW firewall application, you should add a new rule to allow HTTP traffic to pass through firewall by issuing the following command.
ufw allow WWW
or
ufw allow 80/tcp
If you’re using iptables raw rules to manage Firewall rules in your Debian server, add the following rule to allow port 80 inbound traffic on the firewall so that visitors can browse Icinga2 web interface.
apt-get install -y iptables-persistent
iptables -I INPUT -p tcp --destination-port 80 -j ACCEPT
systemctl iptables-persistent save
systemctl iptables-persistent reload
Next, enable and apply the following Apache modules which will be used to redirect HTTP connections to HTTPS, by issuing the below command.
a2enmod rewrite
systemctl restart apache2
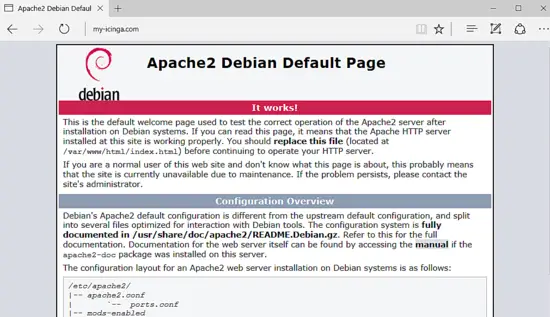
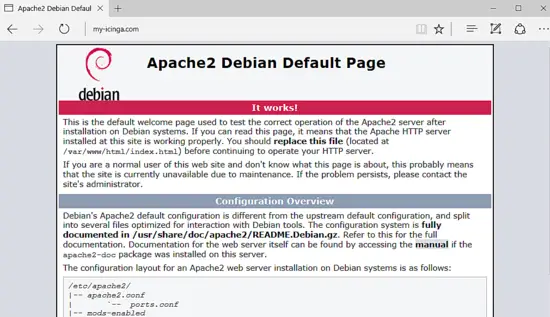
Finally, test if Apache web server default web page can be displayed in your client’s browsers by visiting your Debian machine IP address or your domain name or server FQDN via HTTP protocol. If you don’t know your machine IP address, execute ifconfig or ip a commands to reveal the IP address of your server. The default Apache page for Debian will be displayed in your browser, as shown in the below screenshot.
http://your_domain.tld
In order access Icinga 2 monitoring application via HTTPS protocol that will secure the traffic for your clients, issue the following command to enable Apache web server SSL module and SSL site configuration file. Also, enable Apache rewrite module in order to force users to visit the interface via HTTPS.
a2enmod ssl rewrite
a2ensite default-ssl.conf
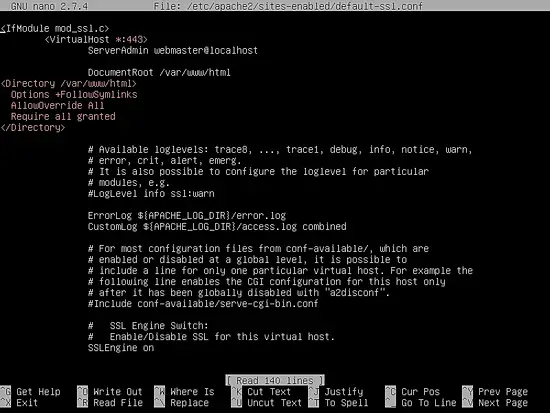
Next, open Apache default SSL site configuration file with a text editor and enable URL rewrite rules by adding the following lines of code after DocumentRoot directive, as shown in the below sample:
nano /etc/apache2/sites-enabled/default-ssl.conf
SSL site configuration file excerpt:
<Directory /var/www/html>
Options +FollowSymlinks
AllowOverride All
Require all granted
</Directory>
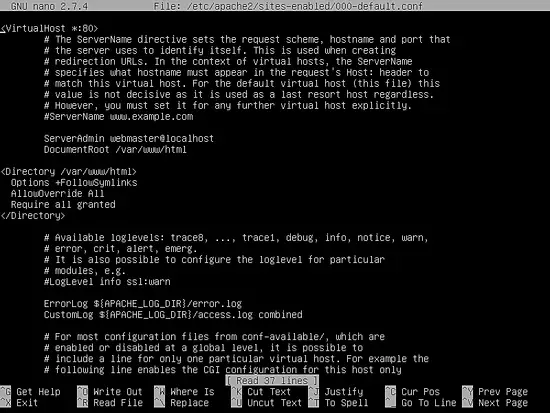
Also, make the following change to VirtualHost line to look like shown in the below excerpt:
<VirtualHost *:443>
Close the TLS Apache file and open /etc/apache2/sites-enabled/000-default.conf file for editing and add the same URL rewrite rules as for SSL configuration file. Insert the lines of code after DocumentRoot statement as shown in the below example.
<Directory /var/www/html>
Options +FollowSymlinks
AllowOverride All
Require all granted
</Directory>
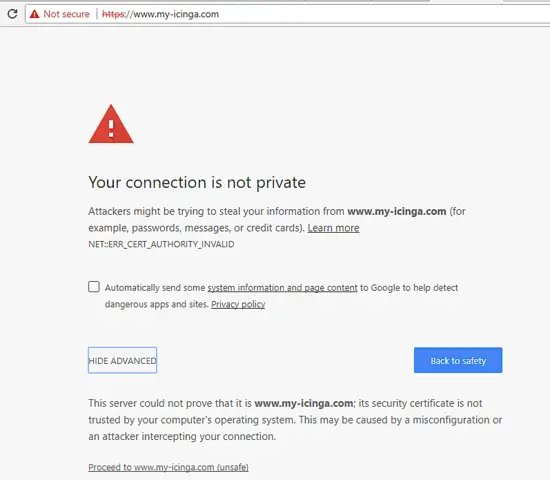
Finally, restart Apache daemon to apply all rules configured so far and visit your domain via HTTP protocol. Because you’re using the automatically Self-Signed certificate pair issued by Apache at installation, an error warning should be displayed in the browser, as shown in the below screenshot.
systemctl restart apache2
https://yourdomain.tld
Accept the warning in order to continue and be redirected to Apache default webpage via HTTPS protocol. The following page will be displayed in your browser.
In case the UFW firewall application blocks incoming network connections to HTTPS port, you should add a new rule to allow HTTPS traffic to pass through the firewall by issuing the following command.
ufw allow 'WWW Full'
or
ufw allow 443/tcp
If iptables is the default firewall application installed to protect your Debian system at network level, add the following rule to allow port 443 inbound traffic in the firewall so that visitors can browse your domain name.
iptables -I INPUT -p tcp --destination-port 443 -j ACCEPT
systemctl iptables-persistent save
systemctl iptables-persistent reload
In the next step, we need to make some further changes to PHP default configuration file in order to assure that the following PHP variables are enabled and the PHP timezone setting is correctly configured and matches your system geographical location. Open /etc/php/7.0/apache2/php.ini file for editing and assure that the following lines are set up as follows. Also, initially, make a backup of PHP configuration file.
cp /etc/php/7.0/apache2/php.ini{,.backup}
nano /etc/php/7.0/apache2/php.ini
Search, edit and change the following variables in php.ini configuration file:
php_value max_execution_time 300
php_value memory_limit 128M
php_value max_input_time 300
date.timezone = Europe/London
Replace the time.zone variable accordingly to your physical time by consulting the list of time zones provided by PHP docs at the following link http://php.net/manual/en/timezones.php
If you want to increase the load speed of your website pages via OPCache plugin available for PHP7, append the following OPCache settings at the bottom of the PHP interpreter configuration file, as detailed below:
opcache.enable=1
opcache.enable_cli=1
opcache.interned_strings_buffer=8
opcache.max_accelerated_files=10000
opcache.memory_consumption=128
opcache.save_comments=1
opcache.revalidate_freq=1
Close the php.ini configuration file and check if the verify the end of PHP configuration file to check if the variables had been correctly added by issuing the below command.
tail /etc/php/7.0/apache2/php.ini
After you’ve made the changes explained above, restart apache daemon to apply the new changes by issuing the following command.
systemctl restart apache2
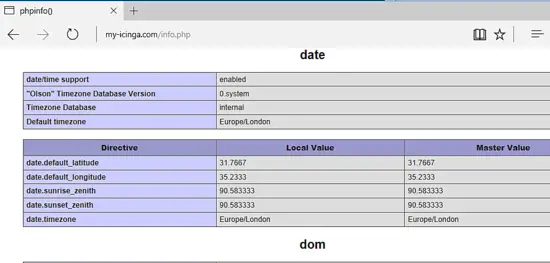
Finally, create a PHP info file by executing the following command and check if the PHP time zone has been correctly configured by visiting the PHP info script file from a browser at the following URL, as illustrated in the below image. Scroll down to date setting to check php time zone configuration.
echo '<?php phpinfo(); ?>'| tee /var/www/html/info.php
https://domain.tld/info.php
Icinga 2 stores users, contacts, and other collected data in a specific RDBMS database, such as MySQL, SQLite or PostgreSQL. In this guide we’ll configure Icinga with MariaDB database, a fork of MySQL database, as backend. Issue the below command to install MariaDB database and the PHP module needed to access mysql database.
apt install mariadb-server mariadb-client php7.0-mysql
After you’ve installed MariaDB, verify if the daemon is running and listens for connections on localhost, port 3306, by running netstat or ss command.
netstat –tlpn | grep mysql
Then, log in to MySQL console and secure MariaDB root account by issuing the following commands.
mysql -h localhost
use mysql;
update user set plugin='' where user='root';
flush privileges;
exit
Now we'll secure the MariaDB by executing the script mysql_secure_installation provided by the installation packages from Debian repositories. While running, the script will ask a series of questions designed to secure MariaDB database, such as: to change MySQL root password, to remove anonymous users, to disable remote root logins and delete the test database. Execute the script by issuing the below command and assure you type yes to all questions asked in order to fully secure MySQL daemon. Use the below script output except as a guide.
sudo mysql_secure_installation
NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL MariaDB
SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP CAREFULLY!
In order to log into MariaDB to secure it, we'll need the current
password for the root user. If you've just installed MariaDB, and
you haven't set the root password yet, the password will be blank,
so you should just press enter here.
Enter current password for root (enter for none):
OK, successfully used password, moving on...
Setting the root password ensures that nobody can log into the MariaDB
root user without the proper authorisation.
You already have a root password set, so you can safely answer 'n'.
Change the root password? [Y/n] y
New password:
Re-enter new password:
Password updated successfully!
Reloading privilege tables..
... Success!
By default, a MariaDB installation has an anonymous user, allowing anyone
to log into MariaDB without having to have a user account created for
them. This is intended only for testing, and to make the installation
go a bit smoother. You should remove them before moving into a
production environment.
Remove anonymous users? [Y/n] y
... Success!
Normally, root should only be allowed to connect from 'localhost'. This
ensures that someone cannot guess at the root password from the network.
Disallow root login remotely? [Y/n] y
... Success!
By default, MariaDB comes with a database named 'test' that anyone can
access. This is also intended only for testing, and should be removed
before moving into a production environment.
Remove test database and access to it? [Y/n] y
- Dropping test database...
... Success!
- Removing privileges on test database...
... Success!
Reloading the privilege tables will ensure that all changes made so far
will take effect immediately.
Reload privilege tables now? [Y/n] y
... Success!
Cleaning up...
All done! If you've completed all of the above steps, your MariaDB
installation should now be secure.
Thanks for using MariaDB!
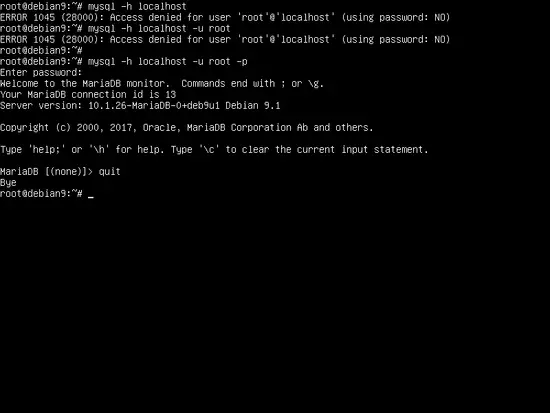
In order to test MariaDB security, try login to the database from console with no root password. The access to the database should be denied if no password is provided for the root account. If the password is supplied, the login process should be granted to MySQL console, as shown in the below screenshot.
mysql -h localhost -u root
mysql -h localhost -u root –p
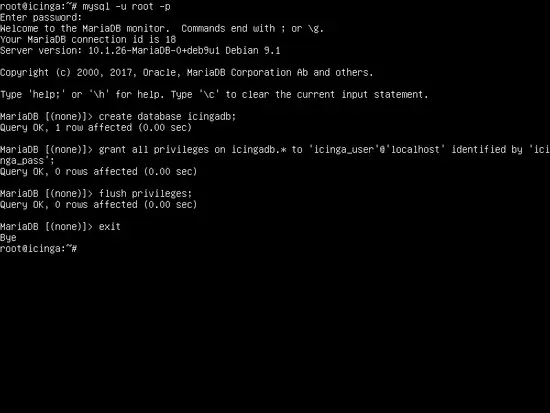
Next, login to MariaDB database console and, first, create a database to be used by the Icinga2 application and a user with a password that will be used to manage this database, by issuing the following commands. Replace this database name, user, and password accordingly.
mysql –u root -p
create database icingadb;
grant all privileges on icingadb.* to 'icinga_user'@'localhost' identified by 'icinga_pass';
flush privileges
exit
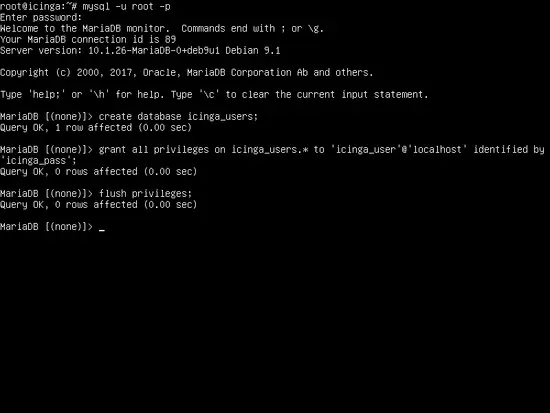
Next, create a second MySQL database that will be used to store Icinga2 web interface users, groups and other web interface custom data, by issuing the following commands. Also, as on the above database, make sure you replace the database name and credentials accordingly and choose a strong password for database user.
mysql –u root –p
create database icinga_users;
grant all privileges on icinga_users.* to 'icinga_user'@'localhost' identified by 'icinga_pass';
flush privileges
exit
In order to apply all changes made so far, restart MySQL and Apache daemons and verify if daemons are running by issuing the following commands.
systemctl restart mysql apache2
systemctl status mysql apache2
Install Icinga 2
After all system requirements are met to install our web monitoring application, proceed with installing the application alongside with MySQL module, needed to access MySQL database, by issuing the below command. Icinga 2 has pre-compiled binary packages offered by Debian 9 repositories. The installation will be performed via Debian 9 apt package manager.
apt install icinga2 icinga2-ido-mysql
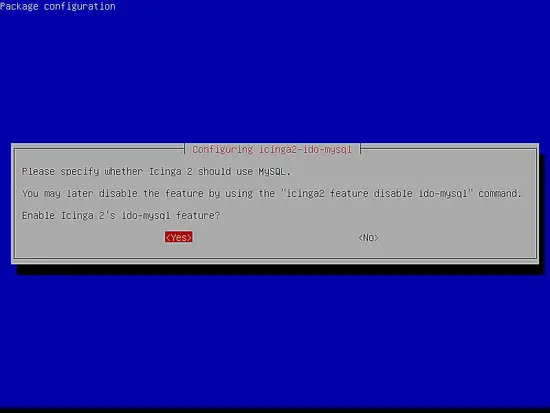
While installing Icinga2 pre-compiled binaries from Debian 9 repositories, a series of prompts will appear on your screen in order to configure the application. At the first prompt, you will be asked if you want to configure and enable Icinga 2 to use MySQL module. Select Yes from the prompt and hit [enter] key to continue as illustrated in the below image.
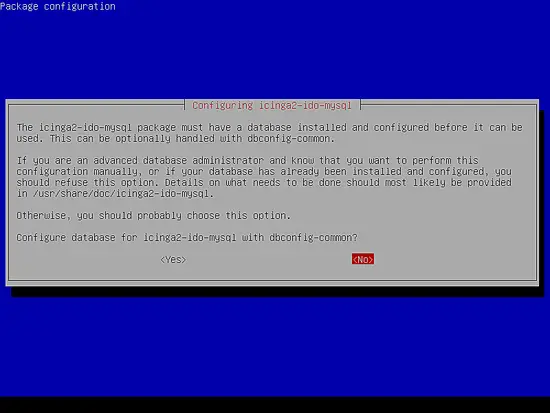
In the next prompt, you will be asked if you want to configure the database for icinga2-ido-mysql with dbconfig-common option. Choose No from the prompt and press [enter] key to finish Icinga 2 installation.
After Icinga 2 has been installed, start Icinga 2 daemon and verify the service status by running the following commands.
systemctl start icinga2.service
systemctl status icinga2.service
In the next step, install Icinga 2 web interface and command line utility packages from Debian 9 with the help of the below command.
apt install icingaweb2 icingacli
Before starting to configure Icinga 2 from web, restart Icinga 2 daemon to pick-up all changes and verify application status by issuing the below command.
systemctl restart icinga2.service
systemctl status icinga2.service
Next, remove the default index.html file installed by Apache web server to webroot path and also delete the info.php file created earlier.
rm /var/www/html/index.html
rm /var/www/html/info.php
Now install MySQL schema for Icinga database by executing the following command. The MySQL database schema is located in /usr/share/icinga2-ido-mysql/schema/ directory.
mysql -u root icingadb -p < /usr/share/icinga2-ido-mysql/schema/mysql.sql
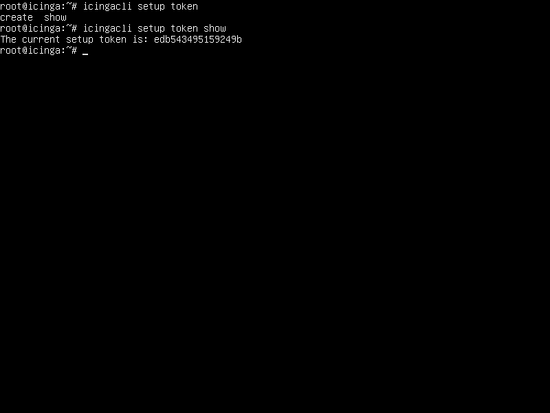
In order to perform Icinga 2 installation from the web, generate an installation token with the following command. Make sure you note down this token, because we’ll write it later in the web interface when asked.
icingacli setup token create
In case you can’t find this token later, you can run the below command to show the generated token.
icingacli setup token show
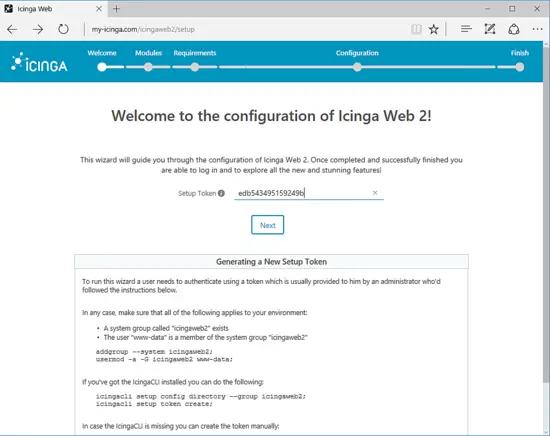
Now proceed with Icinga2 web interface installation process by opening a browser and navigate your server’s IP address or domain name via HTTP protocol to the following URL.
http://your_domain.tld/icingaweb2/setup
On the first installation screen, you will be asked to write down the token generated earlier in order to start the installation process, as shown in the below screenshot. After you add your token, hit in Next button to continue with the installation process.
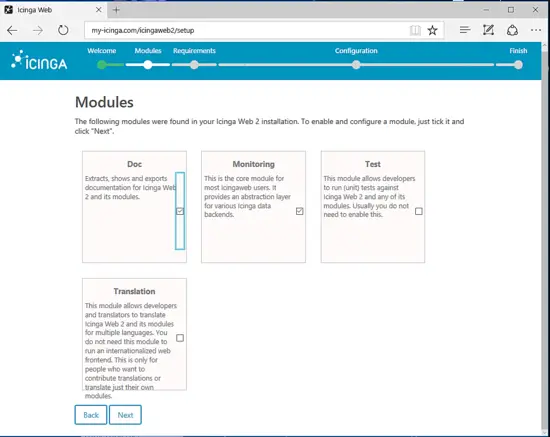
On the next installation screen you will be asked to enable some modules for Icinga 2 web installation. Select Doc and Monitoring modules and hit on next button to continue, as illustrated in the below image.
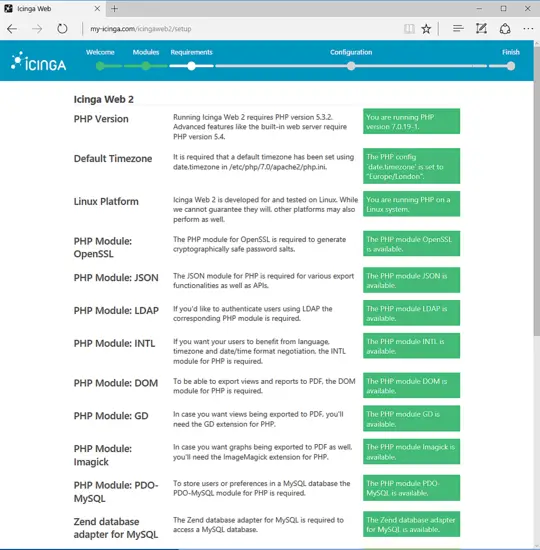
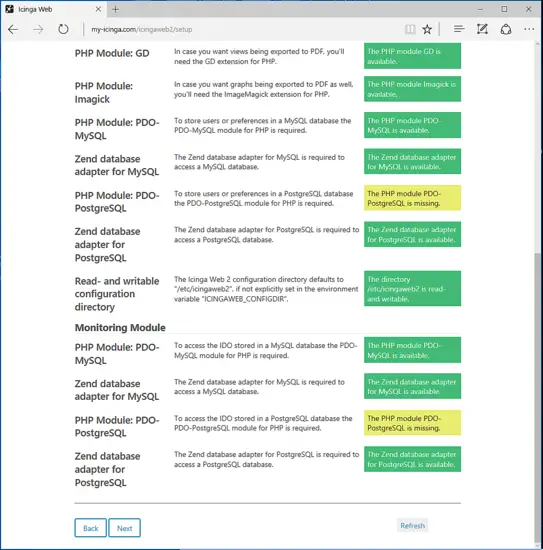
Next, Icinga2 web installer will perform a series of system and PHP modules checks in order to detect if all requirements are meet to continue with the installation process. Scroll down to list of all required PHP modules are installed and properly configured and press Next button to move to the next installation section, as shown in the below images.
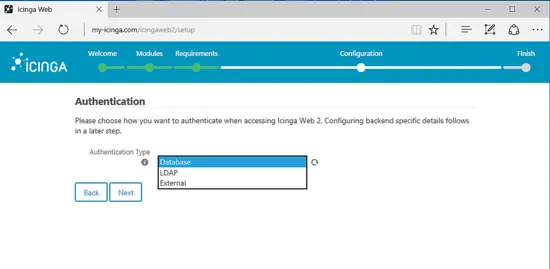
On the next screen, choose Database as authentication backend method for Icinga Web 2 and hit Next button to continue.
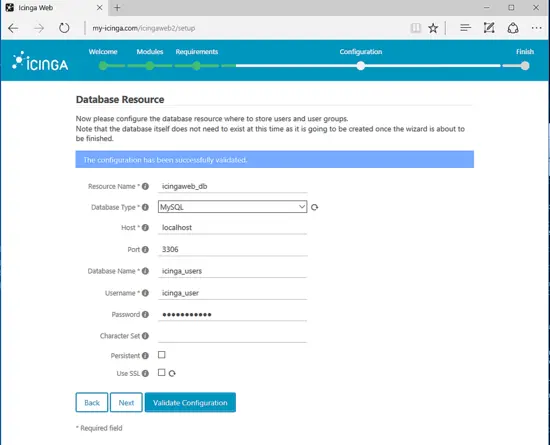
In the next step, add Icinga 2 Web MySQL database name and the access credentials for this database. This database will be used for storing Icinga 2 web interface users and groups. Use the database information for the second database created earlier. Add icingaweb_db as a name for this resource and leave the Host, Port and Character set variables as default. Don’t check Persistent and SSL options and hit on Validate Configuration button to validate the database connection, as shown in the below image. When you finish hit on Next button to move to the next installer section.
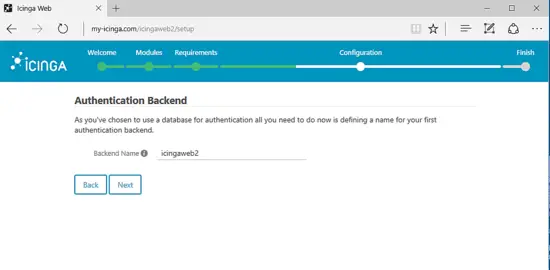
Now set a name for database authentication backed and hit on Next button to continue, as illustrated in the below screenshot.
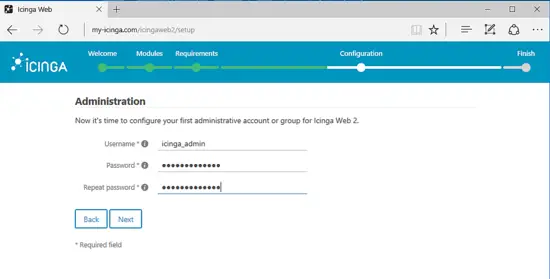
On the next screen, supply an administrative username for managing Icinga2 Web interface and choose a strong password for this account. When you finish hit on Next button to move to the next installation screen.
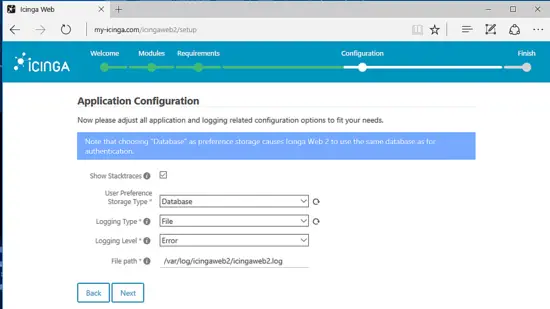
Configure Icinga application and logging configuration with the following settings and when you finish hit on Next button to continue.
- Check Show Stacktraces
- Storage Type = Database
- Logging Type = File
- Logging Level = Error
- File path = /var/log/icingaweb2/icingaweb2.log
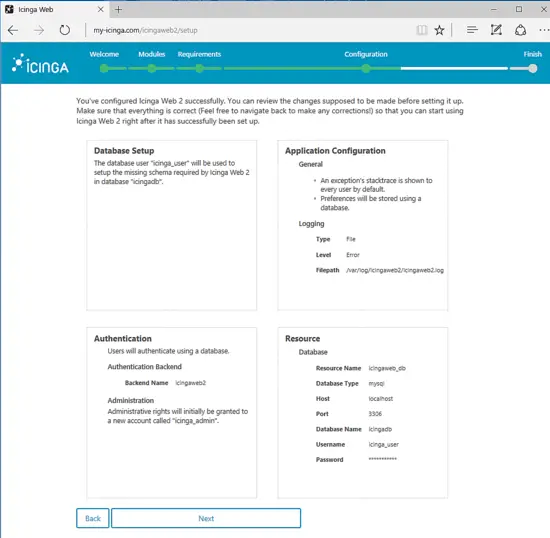
On the next screen, a message will inform you that Icinga Web2 has been successfully configured and a detailed report will display all configuration made so far. Review the report and hit on Next button to continue to the next installation section.
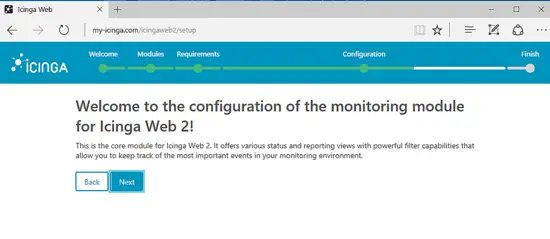
Hit the Next button to move forward with Icinga 2 monitoring module configuration, as shown in the below image.
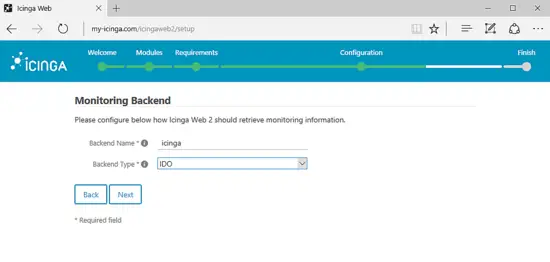
On the next screen add a name for Icinga2 Backend, select IDO as backend type and hit on Next button to continue.
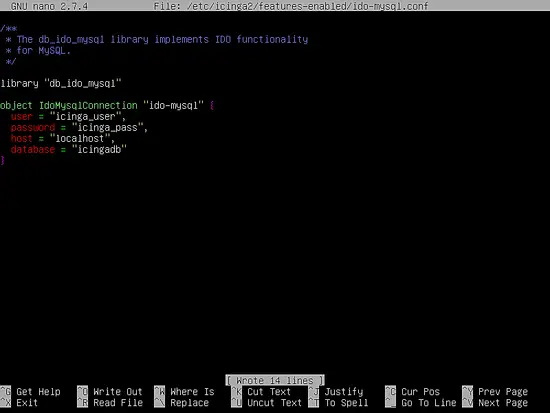
Go back to server’s console, open and edit Icinga MySQL IDO configuration file and add Icinga database credentials (the first database information), as shown in the below sample.
nano /etc/icinga2/features-enabled/ido-mysql.conf
ido-mysql.conf file excerpt:
library "db_ido_mysql"
object IdoMysqlConnection "ido-mysql" {
user = "icinga_user",
password = "icinga_pass",
host = "localhost",
database = "icingadb"
}
Save the file and restart Icinga2 daemon to apply settings by issuing the following command. Afterward, go back to Icinga web interface and continue the installation process.
systemctl restart icinga2.service
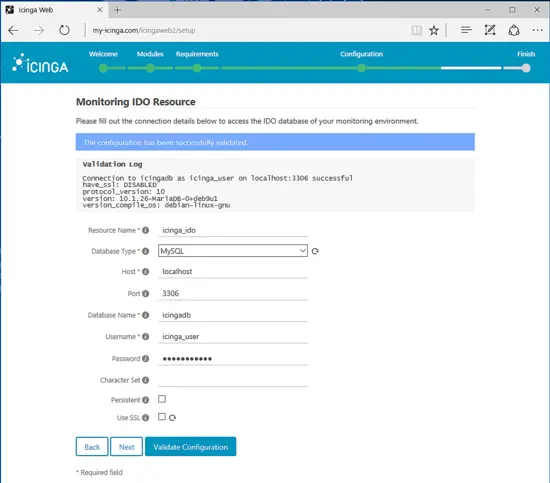
Add Icinga database information in order to setup the IDO resource environment. Use the database information for the first created database, as illustrated in the below image. After you finished editing database information, hit on Validate Configuration button to validate Icinga Monitoring IDO Resource and hit on Next button to move to the next installation screen.
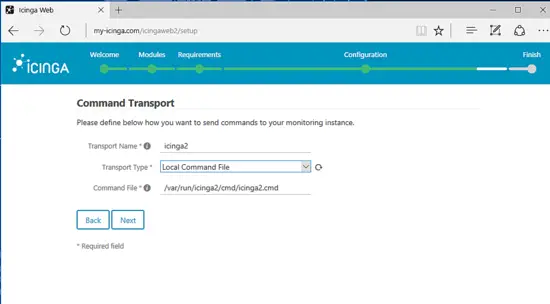
Configure Icinga Command Transport with the following settings and hit Next button to continue.
- Transport Name = icinga2
- Transport Type = Local Command File
- Command File = /var/run/icinga2/cmd/icinga2.cmd
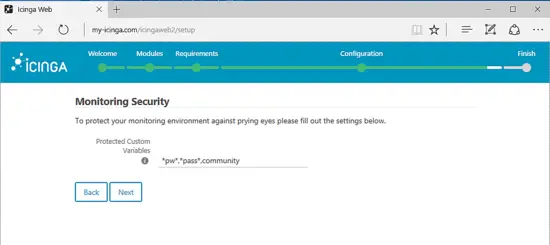
On the next screen leave the default variables configured for monitoring security as illustrated in the below image and press Next button to continue.
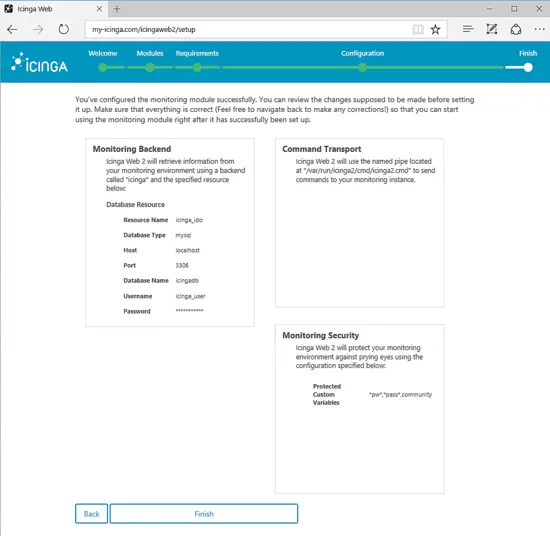
On the next screen, a new message will inform you that Icinga2 Monitoring module has been successfully configured. Review the displayed report to check if everything is correctly configured and press Finish button to complete the installation.
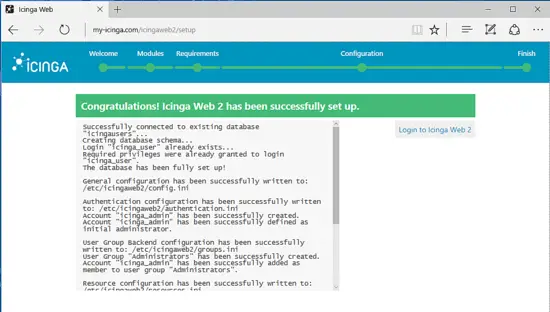
After the installation process has been successfully completed, a congratulation message will inform you that Icinga Web 2 has been successfully installed. Hit on the Login link in order to be redirected to Icinga2 login page.
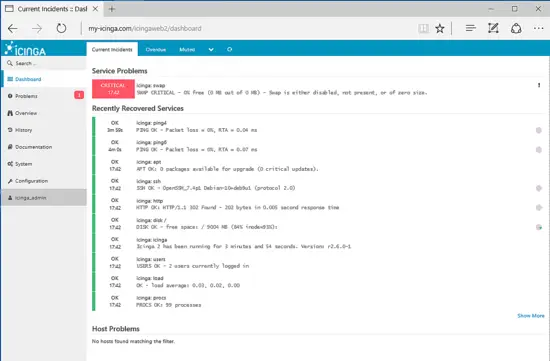
Login to Icinga Web 2 with the credentials configured during the installation process and you will be directed to Icinga Web 2 Dashboard, where you will see a list of current monitored services and system resources belonging to your server.
Finally, log in to server’s command line again and execute the following commands in order to make sure that Icinga Web 2 logs will be created.
mkdir -p /var/log/icingaweb2/
chgrp -R icingaweb2 /var/log/icingaweb2/
chmod -R 775 /var/log/icingaweb2/
In order to force visitors to browse Icinga Web 2 interface via HTTPS protocol, create a new .htaccess file in your web server document root path with the following content.
nano /var/www/html/.htaccess
.htaccess file excerpt:
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule (.*) https://%{SERVER_NAME}/$1 [R,L]
</IfModule>
RewriteEngine on
Options -Indexes
That’s all! You have successfully installed and configured Icinga 2 network monitoring application on Debian 9.2. However, because the Apache HTTP server uses Self-Signed certificates to encrypt the traffic between the server and client’s browser, a warning message will always be generated and displayed in your browser each time you access your domain. In this case, you should buy a certificate issued by a trusted Certificate Authority or get a free certificate pair from Let’s Encrypt CA.
For other custom configurations regarding Icinga 2, visit the documentation page at the following address: https://www.icinga.com/docs