Key-Based SSH Logins With PuTTY - Page 4
9 Disable Username/Password Logins
Up to now, you can log in with your private/public key pair and still with username/password logins, so if someone doesn't attach a private key to his PuTTY session, he will be asked for a username and password. So to achieve a better security, we must disable the username/password logins (you should do this only when you know that your key-based logins are working, because if they aren't and you disable username/password logins, then you have a problem...).
To disable the username/password logins, we must modify the sshd configuration file. On Debian/Ubuntu systems, it's /etc/ssh/sshd_config. You should set Protocol to 2 (1 is insecure and should not be used!), PasswordAuthentication to no, and UsePAM to no (or comment out the UsePAM line), e.g. like this:
vi /etc/ssh/sshd_config
[...] Protocol 2 PasswordAuthentication no UsePAM no [...]
Then restart sshd. On Debian/Ubuntu, you can do it like this:
service ssh restart
On Older versions, use the init script instead of the service command:
/etc/init.d ssh restart
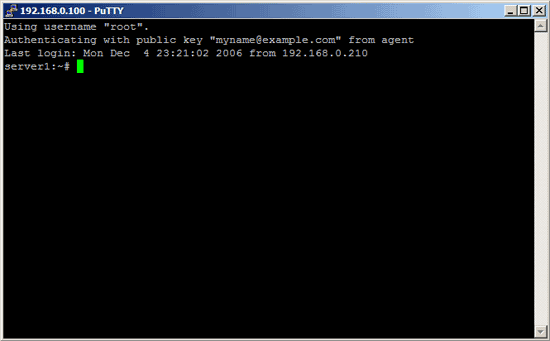
Now if you open a PuTTY session without your private key attached, you shouldn't be able to log in anymore.
10 Let Pageant Remember Your Key Passphrase
Whenever you use your key-based login now, you stilll have to specify your key passphrase. This can be annoying if you connect to the SSH server multiple times a day. Fortunately, you can tell the passphrase to Pageant which will then provide the passphrase whenever you log in to your SSH server.
You can start Pageant by double-clicking its executable file:
Afterwards, you should see running Pageant in the taskbar:
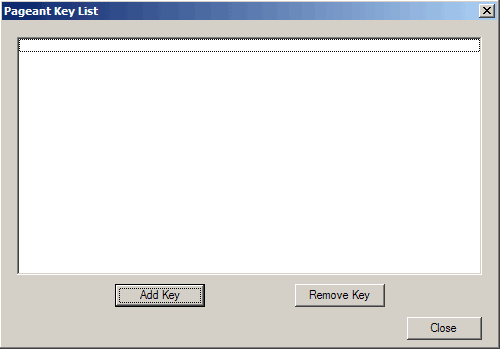
Now double-click the Pageant icon in the taskbar. The following window comes up. Click on Add Key:
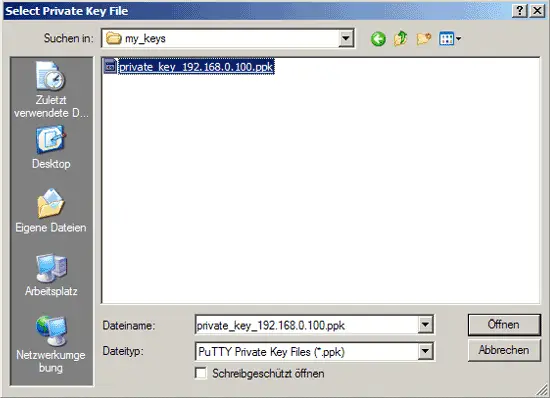
Browse your filesystem and select your private key:
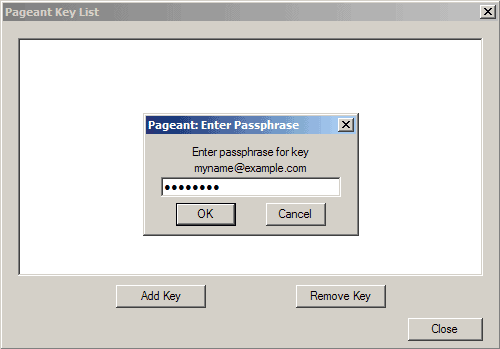
Then enter the passphrase for the private key:
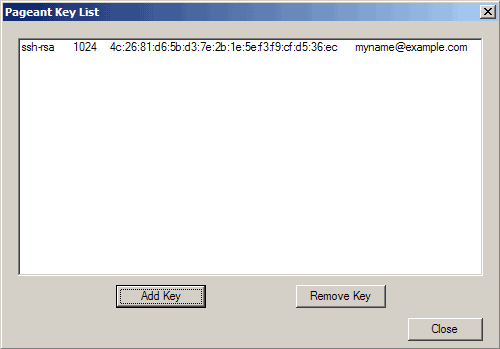
The key is now listed in Pageant's key list. Click on Close:
As long as Pageant is running in the taskbar, you can log in to your SSH server without providing the passphrase - this is done by Pageant:
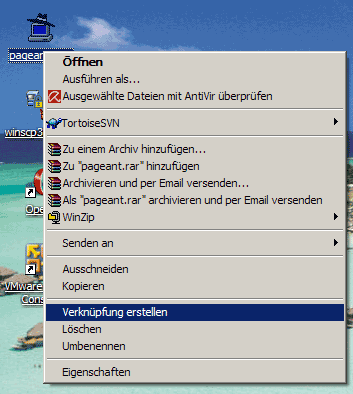
When you stop Pageant, it forgets all keys, so the next time you start Pageant you must add the keys again. This can also be annoying, but to prevent this, we can create a shortcut on the desktop to the Pageant executable. Right-click the Pageant executable and select Create Shortcut:
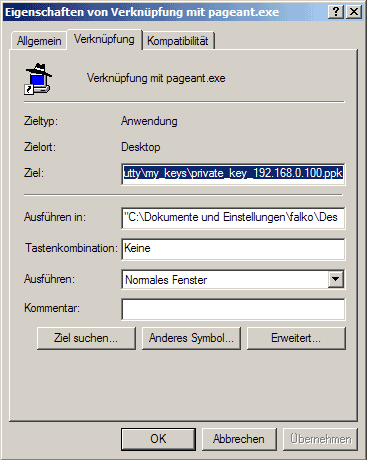
You should now find a shortcut. Right-click it and go to Properties:
Under Target, you will now find the path to pageant.exe, e.g. "C:\Dokumente und Einstellungen\falko\Desktop\pageant.exe" (if there are no spaces in your path, you don't need the quotation marks). You can now simply add the location of your private key to that line, for example if you private key is C:\putty\my_keys\private_key_192.168.0.100.ppk then the line should look like this:
"C:\Dokumente und Einstellungen\falko\Desktop\pageant.exe" C:\putty\my_keys\private_key_192.168.0.100.ppk
(if there are spaces in the path to your private key, you must wrap it in quotation marks again, e.g. like this:
"C:\Dokumente und Einstellungen\falko\Desktop\pageant.exe" "C:\directory with lots of spaces in name\my keys\private_key_192.168.0.100.ppk"
)
Then click on OK:
Now when you double-click on the Pageant shortcut, Pageant will automatically load your private key and ask you for the passphrase. Enter it, and that's it.