The Perfect Server - OpenSUSE 11.4 x86_64 [ISPConfig 3] - Page 4
8 Install Postfix, Dovecot, MySQL
We need to install Python 2.7 in this chapter, but it conflicts with the package patterns-openSUSE-minimal_base. Therefore we must uninstall that package first. To do so, start YaST:
yast2
In YaST, go to Software > Software Management:
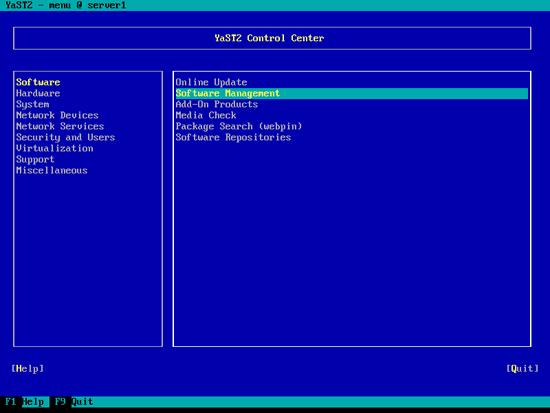
Type patterns-openSUSE-minimal_base in the Search field and press ENTER. The package should be listed as installed (i) in the main window. Mark the package and press the ENTER key until there's a minus (-) sign in front of the package (the minus stands for uninstall), then hit [Accept]:
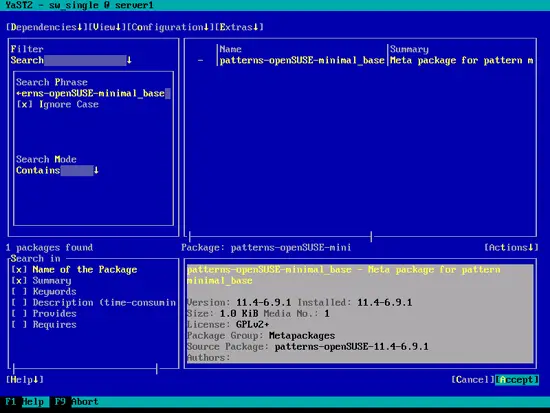
As a replacment for the package, some other packages need to be installed. Accept the selection by hitting [OK]:
Leave YaST afterwards.
Next r un
yast2 -i postfix postfix-mysql mysql mysql-community-server mysql-client libmysqlclient-devel dovecot12 dovecot12-backend-mysql pwgen cron python
Open /etc/postfix/master.cf...
vi /etc/postfix/master.cf
... and uncomment the following line:
[...] tlsmgr unix - - n 1000? 1 tlsmgr [...] |
Create the following symlink:
ln -s /usr/lib64/dovecot/modules /usr/lib/dovecot
Start MySQL, Postfix, and Dovecot and enable the services to be started at boot time.
chkconfig -f --add mysql
/etc/init.d/mysql start
chkconfig --add postfix
/etc/init.d/postfix start
chkconfig --add dovecot
/etc/init.d/dovecot start
You might see the following Dovecot warning which you can safely ignore:
Starting dovecot Warning: There is no way to login to this server: disable_plaintext_auth=yes, ssl=no, no non-plaintext auth mechanisms.
If you have trouble with authentication failures,
enable auth_debug setting. See http://wiki.dovecot.org/WhyDoesItNotWork
This message goes away after the first successful login.
Now I install the getmail rpm package which is not available from the OpenSUSE main repositories.
zypper install http://download.opensuse.org/repositories/server:/mail/openSUSE_11.4/noarch/getmail-4.20.0-1.1.noarch.rpm
To secure the MySQL installation, run:
mysql_secure_installation
Now you will be asked several questions:
server1:~ # mysql_secure_installation
NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL MySQL
SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP CAREFULLY!
In order to log into MySQL to secure it, we'll need the current
password for the root user. If you've just installed MySQL, and
you haven't set the root password yet, the password will be blank,
so you should just press enter here.
Enter current password for root (enter for none): <-- ENTER
OK, successfully used password, moving on...
Setting the root password ensures that nobody can log into the MySQL
root user without the proper authorisation.
Set root password? [Y/n] <-- Y
New password: <-- yourrootsqlpassword
Re-enter new password: <-- yourrootsqlpassword
Password updated successfully!
Reloading privilege tables..
... Success!
By default, a MySQL installation has an anonymous user, allowing anyone
to log into MySQL without having to have a user account created for
them. This is intended only for testing, and to make the installation
go a bit smoother. You should remove them before moving into a
production environment.
Remove anonymous users? [Y/n] <-- Y
... Success!
Normally, root should only be allowed to connect from 'localhost'. This
ensures that someone cannot guess at the root password from the network.
Disallow root login remotely? [Y/n] <-- Y
... Success!
By default, MySQL comes with a database named 'test' that anyone can
access. This is also intended only for testing, and should be removed
before moving into a production environment.
Remove test database and access to it? [Y/n] <-- Y
- Dropping test database...
... Success!
- Removing privileges on test database...
... Success!
Reloading the privilege tables will ensure that all changes made so far
will take effect immediately.
Reload privilege tables now? [Y/n] <-- Y
... Success!
Cleaning up...
All done! If you've completed all of the above steps, your MySQL
installation should now be secure.
Thanks for using MySQL!
server1:~ #
Now your MySQL setup should be secured.
9 Amavisd-new, Spamassassin And Clamav
Install Amavisd-new, Spamassassin and Clamav antivirus. Run
yast2 -i amavisd-new clamav clamav-db zoo unzip unrar bzip2 unarj perl-DBD-mysql
Open /etc/amavisd.conf...
vi /etc/amavisd.conf
... and add the $myhostname line with your correct hostname below the $mydomain line:
[...] $mydomain = 'example.com'; # a convenient default for other settings $myhostname = "server1.$mydomain"; [...] |
Then create a symlink from /var/run/clamav/clamd to /var/lib/clamav/clamd-socket:
mkdir -p /var/run/clamav
ln -s /var/lib/clamav/clamd-socket /var/run/clamav/clamd
To enable the services, run:
chkconfig --add amavis
chkconfig --add clamd
/etc/init.d/amavis start
/etc/init.d/clamd start

