How to Install and Configure Tripwire IDS on Debian 10
Tripwire is a free and open-source Linux Intrusion Detection System. It is used to detect and report any unauthorized change in files and directories on Linux. It will also send you an alert on email on file/directory changes. Tripwire works by comparing the current filesystem state against a known baseline state and reports if detect any changes.
In this post, we will show you how to install and configure Tripwire on Debian 10.
Prerequisites
- A server running Debian 10.
- A root password is configured on the server.
Getting Started
First, update the system packages to the updated version by running the following command:
apt-get update -y
Once all the packages are updated, you can proceed to the next step.
Install Tripwire
By default, the Tripwire package is available in the Debian 10 default repository. You can install it using the following command:
apt-get install tripwire -y
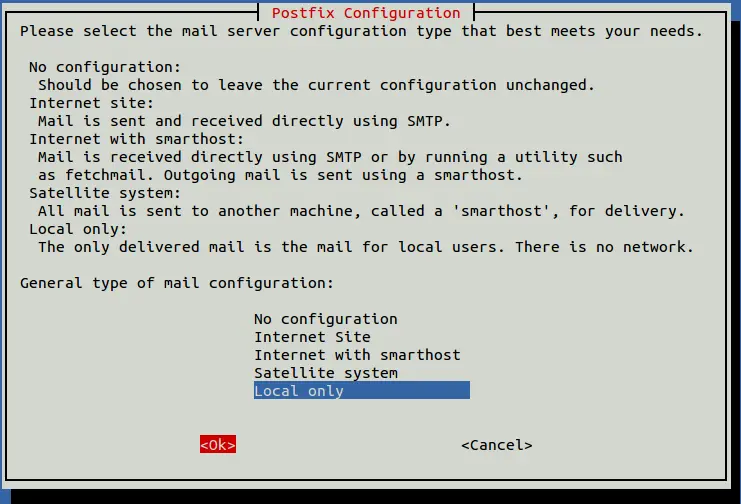
During the installation, you will be asked to select the email configuration as shown below:
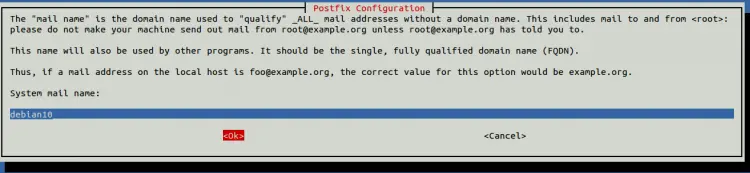
Select your desired option and hit ENTER. You will be asked to set up a system mail name as shown below:
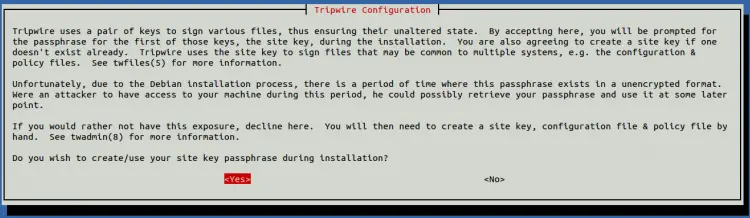
Provide your system mail name and hit ENTER. You will be asked to create your site key passphrase as shown below:
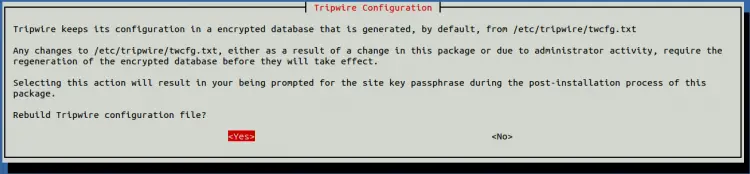
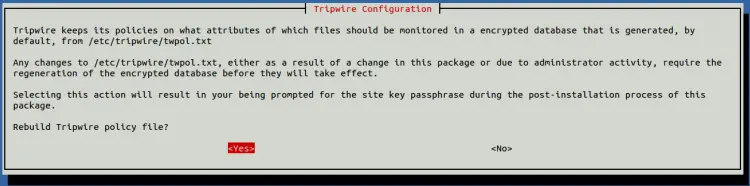
Select Yes and hit ENTER. You will be asked to rebuild the Tripwire configuration file as shown below:
Select Yes and hit ENTER. You will be asked to rebuild your Tripwire policy file as shown below:
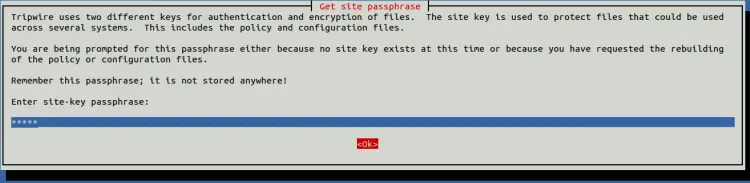
Select Yes and hit ENTER. You will be asked to provide your site-key passphrase as shown below:
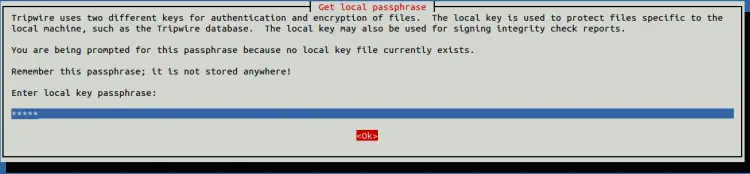
Provide your password and hit ENTER. You will be asked to set your local key passphrase as shown below:
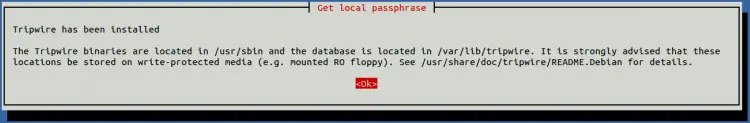
Provide your password and hit ENTER. Once Tripwire has been installed, you should see the following screen:
Click on the Ok button to finish the installation.
Configure Tripwire
Next, you will need to generate Tripwire keys and initialize the database. First, change the directory to Tripwire and list all keys and files with the following command:
cd /etc/tripwire/
ls
You should see the following output:
debian10-local.key site.key tw.cfg twcfg.txt tw.pol twpol.txt
Next, edit the Tripwire configuration file and set REPORTLEVEL to 4
nano /etc/tripwire/twcfg.txt
Change the following line:
REPORTLEVEL =4
Save and close the file when you are finished.
Next, generate a new configuration file with the following command:
twadmin -m F -c tw.cfg -S site.key twcfg.txt
You will be asked to provide your site passphrase as shown below:
Please enter your site passphrase: Wrote configuration file: /etc/tripwire/tw.cfg
Next, create a twpolmake.pl file to optimize Tripwire policy.
nano twpolmake.pl
Add the following lines:
#!/usr/bin/perl $POLFILE=$ARGV[0]; open(POL,"$POLFILE") or die "open error: $POLFILE" ; my($myhost,$thost) ; my($sharp,$tpath,$cond) ; my($INRULE) = 0 ; while () { chomp; if (($thost) = /^HOSTNAME\s*=\s*(.*)\s*;/) { $myhost = `hostname` ; chomp($myhost) ; if ($thost ne $myhost) { $_="HOSTNAME=\"$myhost\";" ; } } elsif ( /^{/ ) { $INRULE=1 ; } elsif ( /^}/ ) { $INRULE=0 ; } elsif ($INRULE == 1 and ($sharp,$tpath,$cond) = /^(\s*\#?\s*)(\/\S+)\b(\s+->\s+.+)$/) { $ret = ($sharp =~ s/\#//g) ; if ($tpath eq '/sbin/e2fsadm' ) { $cond =~ s/;\s+(tune2fs.*)$/; \#$1/ ; } if (! -s $tpath) { $_ = "$sharp#$tpath$cond" if ($ret == 0) ; } else { $_ = "$sharp$tpath$cond" ; } } print "$_\n" ; } close(POL) ;
Save and close the file then create a configuration file with the following command:
perl twpolmake.pl twpol.txt > twpol.txt.new
twadmin -m P -c tw.cfg -p tw.pol -S site.key twpol.txt.new
You should see the following output:
Please enter your site passphrase: Wrote policy file: /etc/tripwire/tw.pol
Next, create a Tripwire database with the following command:
tripwire -m i -s -c tw.cfg
You should see the following output:
Please enter your local passphrase: ### Warning: File system error. ### Filename: /var/lib/tripwire/debian10.twd ### No such file or directory ### Continuing...
You can also display the generated database with the following command:
twprint -m d -d /var/lib/tripwire/debian10.twd
You should see the following output:
Open Source Tripwire(R) 2.4.3.7 Database Database generated by: root Database generated on: Sun 09 May 2021 08:39:18 AM UTC Database last updated on: Never =============================================================================== Database Summary: =============================================================================== Host name: debian10 Host IP address: 45.58.38.142 Host ID: None Policy file used: /etc/tripwire/tw.pol Configuration file used: /etc/tripwire/tw.cfg Database file used: /var/lib/tripwire/debian10.twd Command line used: tripwire -m i -s -c tw.cfg =============================================================================== Object Summary: =============================================================================== ------------------------------------------------------------------------------- # Section: Unix File System -------------------------------------------------------------------------------
If you want to update the Tripwire database, run the following command:
tripwire --update --accept-all
You should get the following output:
### Error: File could not be opened. ### Filename: /var/lib/tripwire/report/debian10-20210509-084141.twr ### No such file or directory ### Exiting...
Now, test the Tripwire using the following command:
tripwire -m c -s -c /etc/tripwire/tw.cfg
You should see the following output:
Open Source Tripwire(R) 2.4.3.7 Integrity Check Report Report generated by: root Report created on: Sun 09 May 2021 08:42:15 AM UTC Database last updated on: Never =============================================================================== Report Summary: =============================================================================== Host name: debian10 Host IP address: 45.58.38.142 Host ID: None Policy file used: /etc/tripwire/tw.pol Configuration file used: /etc/tripwire/tw.cfg Database file used: /var/lib/tripwire/debian10.twd Command line used: tripwire -m c -s -c /etc/tripwire/tw.cfg =============================================================================== Rule Summary: =============================================================================== ------------------------------------------------------------------------------- Section: Unix File System ------------------------------------------------------------------------------- Rule Name Severity Level Added Removed Modified --------- -------------- ----- ------- -------- Other binaries 66 0 0 0 Tripwire Binaries 100 0 0 0 Other libraries 66 0 0 0 Root file-system executables 100 0 0 0 * Tripwire Data Files 100 1 0 0 System boot changes 100 0 0 0 Root file-system libraries 100 0 0 0 (/lib) Critical system boot files 100 0 0 0 * Other configuration files 66 0 0 1 (/etc) Boot Scripts 100 0 0 0 Security Control 66 0 0 0 Root config files 100 0 0 0 Devices & Kernel information 100 0 0 0 (/dev) Invariant Directories 66 0 0 0 Total objects scanned: 27975 Total violations found: 2 =============================================================================== Object Summary: =============================================================================== ------------------------------------------------------------------------------- # Section: Unix File System ------------------------------------------------------------------------------- ------------------------------------------------------------------------------- Rule Name: Tripwire Data Files (/var/lib/tripwire/debian10.twd) Severity Level: 100 -------------------------------------------------------------------------------
By default, Tripwire report files are located at /var/lib/tripwire/report/:
ls /var/lib/tripwire/report/
Output:
debian10-20210509-084215.twr
You can check this report using the following command:
twprint -m r -t 4 -r /var/lib/tripwire/report/debian10-20210509-084215.twr
Verify Tripwire IDS
At this point, Tripwire is installed and configured. Now, it's time to check whether Tripwire is working or not.
First, create some files in your system with the following command:
touch fil1 file2 file3 file4 file5
Now, run the Tripwire to check whether the Tripwire detects these files or not:
tripwire --check --interactive
You should see the newly created files in the following output:
Open Source Tripwire(R) 2.4.3.7 Integrity Check Report Report generated by: root Report created on: Sun 09 May 2021 08:46:36 AM UTC Database last updated on: Never =============================================================================== Report Summary: =============================================================================== Host name: debian10 Host IP address: 45.58.38.142 Host ID: None Policy file used: /etc/tripwire/tw.pol Configuration file used: /etc/tripwire/tw.cfg Database file used: /var/lib/tripwire/debian10.twd Command line used: tripwire --check --interactive =============================================================================== ------------------------------------------------------------------------------- Rule Name: Other configuration files (/etc) Severity Level: 66 ------------------------------------------------------------------------------- Remove the "x" from the adjacent box to prevent updating the database with the new values for this object. Modified: [x] "/etc/tripwire" ------------------------------------------------------------------------------- Rule Name: Root config files (/root) Severity Level: 100 ------------------------------------------------------------------------------- Remove the "x" from the adjacent box to prevent updating the database with the new values for this object. Added: [x] "/root/file4" [x] "/root/file3" [x] "/root/fil1" [x] "/root/file2" [x] "/root/file5" Modified: [x] "/root" ===============================================================================
You can also check the generated report later using the following command:
twprint --print-report --twrfile /var/lib/tripwire/report/debian10-20210509-084636.twr
Automate Tripwire Report
You can also set up a cron job to run a Tripwire at a specific time. You can do it with the following command:
crontab -e
Add the following lines:
00 06 * * * /usr/sbin/tripwire --check
Save and close the file when you are finished.
The above file will run a Tripwire every morning at 06:00 AM. You can check the generated report at /var/lib/tripwire/report/.
Conclusion
Congratulations! you have successfully installed and configured Tripwire IDS on Debian 10. I hope this will help you to check which files or directories are modified on your system.