How to Install and Configure OpenLDAP and phpLDAPadmin on Ubuntu 20.04
This tutorial exists for these OS versions
- Ubuntu 22.04 (Jammy Jellyfish)
- Ubuntu 20.04 (Focal Fossa)
On this page
LDAP is a Lightweight Directory Access Protocol used for accessing and maintaining distributed directory over an internet protocol. phpLDAPadmin is a web-based LDAP client used for managing and administering the LDAP server. Its powerful search functionality and hierarchical tree view make it easier to manage the LDAP server through the web browser. You can add and delete records, view and edit image attributes, manage user password hashes and many more using phpLDAPadmin.
In this tutorial, we will explain how to install phpLDAPadmin on Ubuntu 20.04.
Prerequisites
- A server running Ubuntu 20.04.
- A valid domain name pointed with your server IP.
- A root password is configured the server.
Getting Started
Before starting, it is always recommended to update your system with the latest version of packages. You can update it with the following command:
apt-get update -y
Once all the packages are updated, you can proceed to the next step.
Install and Configure OpenLDAP Server
First, you will need to install Slapd and other LDAP utilities in your server. You can install them by running the following command:
apt-get install slapd ldap-utils
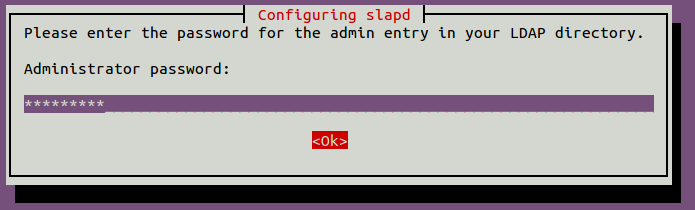
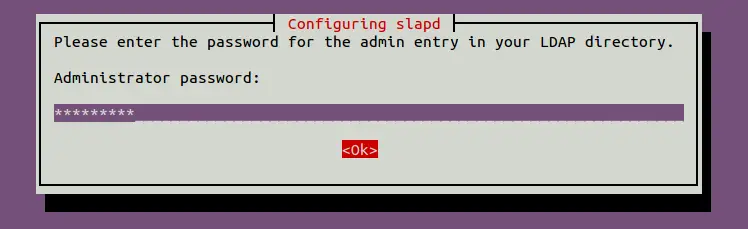
During the installation, you will be asked to set up an administrator password as shown below:
Provide your secure password and hit Enter to continue. Once the installation has been finished, you will need to reconfigure the SLAPD package to set your domain information.
You can reconfigure it with the following command:
dpkg-reconfigure slapd
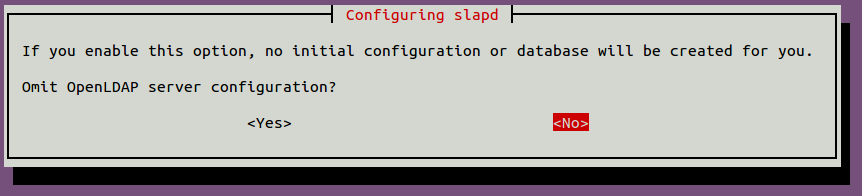
You will be asked to omit the OpenLDAP server configuration as shown below:
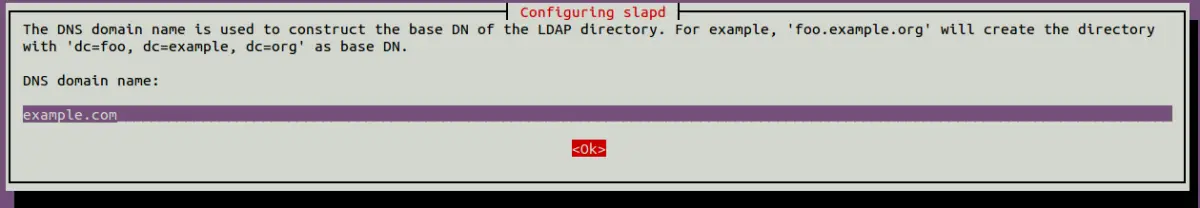
Select No and hit Enter to continue. You will be asked to provide a DNS domain name as shown below:
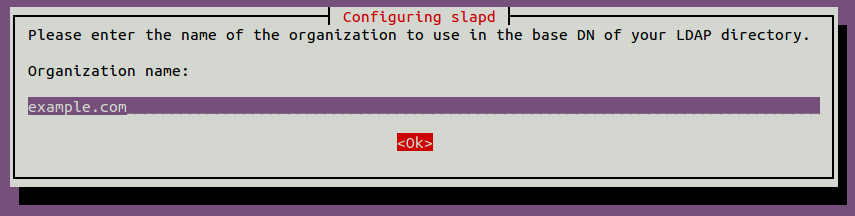
Provide your domain name and hit Enter to continue. You will be asked to provide the organization name as shown below:
Provide your desired organization name and hit Enter to continue. You will be asked for the admin password as shown below:
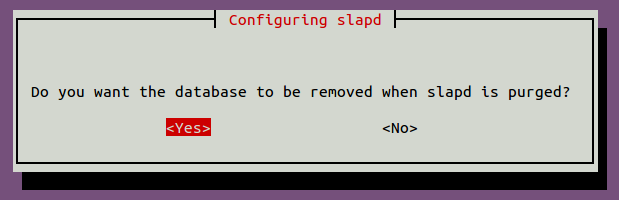
Provide your administrator password and hit Enter to continue. You will be asked to remove the database as shown below:
Select Yes and hit Enter to finish the configuration.
Now, you can verify your LDAP information using the following command:
slapcat
You should get the following output:
dn: dc=example,dc=com objectClass: top objectClass: dcObject objectClass: organization o: example.com dc: example structuralObjectClass: organization entryUUID: 971829cc-ac5f-103a-8e42-9f8486ff5685 creatorsName: cn=admin,dc=example,dc=com createTimestamp: 20201027051828Z entryCSN: 20201027051828.103064Z#000000#000#000000 modifiersName: cn=admin,dc=example,dc=com modifyTimestamp: 20201027051828Z dn: cn=admin,dc=example,dc=com objectClass: simpleSecurityObject objectClass: organizationalRole cn: admin description: LDAP administrator userPassword:: e1NTSEF9Tm5OYlpSMktkYjVnUUprb284MHFPTEVkMjQrQXpQWEk= structuralObjectClass: organizationalRole entryUUID: 9718c198-ac5f-103a-8e43-9f8486ff5685 creatorsName: cn=admin,dc=example,dc=com createTimestamp: 20201027051828Z entryCSN: 20201027051828.107057Z#000000#000#000000 modifiersName: cn=admin,dc=example,dc=com modifyTimestamp: 20201027051828Z
Create OpenLDAP User Accounts
First, you will need to create the organization unit containers to store users and group information. You can create it with the following command:
nano users-ou.ldif
Add the following lines:
dn: ou=people,dc=example,dc=com objectClass: organizationalUnit objectClass: top ou: people dn: ou=groups,dc=example,dc=com objectClass: organizationalUnit objectClass: top ou: groups
Save and close the file when you are finished then adjust the SLAPD database access controls by creating the following file:
nano update-mdb-acl.ldif
Add the following lines:
dn: olcDatabase={1}mdb,cn=config
changetype: modify
replace: olcAccess
olcAccess: to attrs=userPassword,shadowLastChange,shadowExpire
by self write
by anonymous auth
by dn.subtree="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage
by dn.exact="cn=readonly,ou=people,dc=example,dc=com" read
by * none
olcAccess: to dn.exact="cn=readonly,ou=people,dc=example,dc=com" by dn.subtree="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage by * none
olcAccess: to dn.subtree="dc=example,dc=com" by dn.subtree="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage
by users read
by * none
Save and close the file then update database ACL with the above information by running the following command:
ldapadd -Y EXTERNAL -H ldapi:/// -f update-mdb-acl.ldif
You should get the following output:
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "olcDatabase={1}mdb,cn=config"
Next, update the database with the user OU information by running the following command:
ldapadd -Y EXTERNAL -H ldapi:/// -f users-ou.ldif
You should get the following output:
SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "ou=people,dc=example,dc=com" adding new entry "ou=groups,dc=example,dc=com"
Next, create a new user account named hiteshj by creating the following file:
nano hitesh.ldif
Add the following lines:
dn: uid=hiteshj,ou=people,dc=example,dc=com objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount uid: hiteshj cn: Hitesh sn: Jethva loginShell: /bin/bash uidNumber: 10000 gidNumber: 10000 homeDirectory: /home/hiteshj shadowMax: 60 shadowMin: 1 shadowWarning: 7 shadowInactive: 7 shadowLastChange: 0 dn: cn=hiteshj,ou=groups,dc=example,dc=com objectClass: posixGroup cn: hiteshj gidNumber: 10000 memberUid: hiteshj
Save and close the file then add the user to the database with the following command:
ldapadd -Y EXTERNAL -H ldapi:/// -f hitesh.ldif
You should get the following output:
SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "uid=hiteshj,ou=people,dc=example,dc=com" adding new entry "cn=hiteshj,ou=groups,dc=example,dc=com"
Next, you will need to set the password for the user. You can set it with the following command:
ldappasswd -H ldapi:/// -Y EXTERNAL -S "uid=hiteshj,ou=people,dc=example,dc=com"
You should se the following output:
New password: Re-enter new password: SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0
Once you are finished, you can proceed to the next step.
Create OpenLDAP Bind DN
Next, you will need to define username and password for querying the directory server. First, generate the password hash for the bind DN user using the following command:
slappasswd
You should get the following output:
New password:
Re-enter new password:
{SSHA}DhjyJN5akaj2etaFKoyeAY8QMgSD/OTb
Next, create a Bind DN name readonly with the following command:
nano readonly-user.ldif
Add the following lines:
dn: cn=readonly,ou=people,dc=example,dc=com
objectClass: organizationalRole
objectClass: simpleSecurityObject
cn: readonly
userPassword: {SSHA}DhjyJN5akaj2etaFKoyeAY8QMgSD/OTb
description: Bind DN user for LDAP Operations
Save and close the file when you are finished then add the BIND user to the database with the following command:
ldapadd -Y EXTERNAL -H ldapi:/// -f readonly-user.ldif
You should get the following output:
SASL/EXTERNAL authentication started SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth SASL SSF: 0 adding new entry "cn=readonly,ou=people,dc=example,dc=com"
Next, verify the Bind DN ACL with the following command:
ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b cn=config '(olcDatabase={1}mdb)' olcAccess
You should get the following output:
dn: olcDatabase={1}mdb,cn=config
olcAccess: {0}to attrs=userPassword,shadowLastChange,shadowExpire by self writ
e by anonymous auth by dn.subtree="gidNumber=0+uidNumber=0,cn=peercred,cn=ext
ernal,cn=auth" manage by dn.exact="cn=readonly,ou=people,dc=example,dc=com"
read by * none
olcAccess: {1}to dn.exact="cn=readonly,ou=people,dc=example,dc=com" by dn.subt
ree="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth" manage by * non
e
olcAccess: {2}to dn.subtree="dc=example,dc=com" by dn.subtree="gidNumber=0+uid
Number=0,cn=peercred,cn=external,cn=auth" manage by users read by * none
Install and Configure phpLDAPadmin
By default, phpLDAPadmin package is available in the Ubuntu 20.04 default repository. You can install it by running the following command:
apt-get install phpldapadmin -y
After installing phpLDAPadmin, you will need to configure phpLDAPadmin and define your domain information. You can do it by editing the file /etc/phpldapadmin/config.php:
nano /etc/phpldapadmin/config.php
Change the following lines:
$servers->setValue('server','name','My LDAP Server');
$servers->setValue('server','host','69.87.216.102');
$servers->;setValue('server','base',array('dc=example,dc=com'));
$servers->setValue('login','auth_type','session');
$servers->setValue('login','bind_id','cn=admin,dc=example,dc=com');
$servers->setValue('auto_number','min',array('uidNumber'=>10000,'gidNumber'=>10000));
Save and close the file when you are finished.
Configure Apache for phpLDAPadmin
phpLDAPadmin default configuration file for Apache is located at /etc/apache2/conf-available/phpldapadmin.conf. Don't make any changes and go with default settings.
Next, disable the default Apache virtual host configuration file and restart the Apache service to apply the changes:
a2dissite 000-default.conf
systemctl restart apache2
Once you are finished, you can proceed to the next step.
Access phpLDAPadmin Web UI
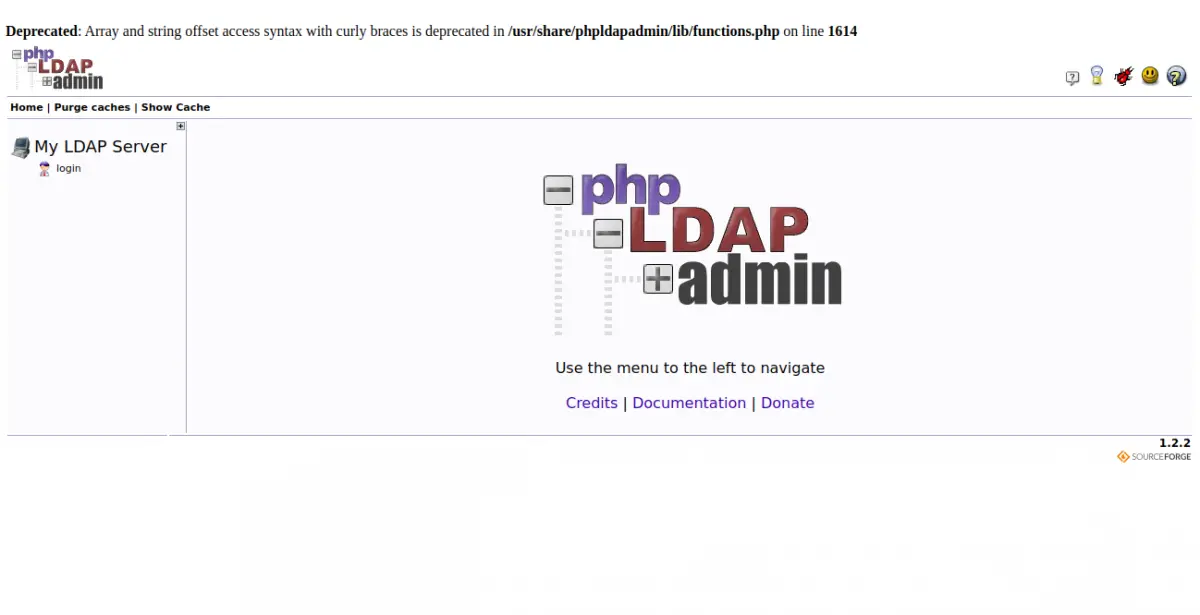
Now, open your web browser and access the phpLDAPadmin using the URL http://your-server-ip/phpldapadmin. You should see the following screen:
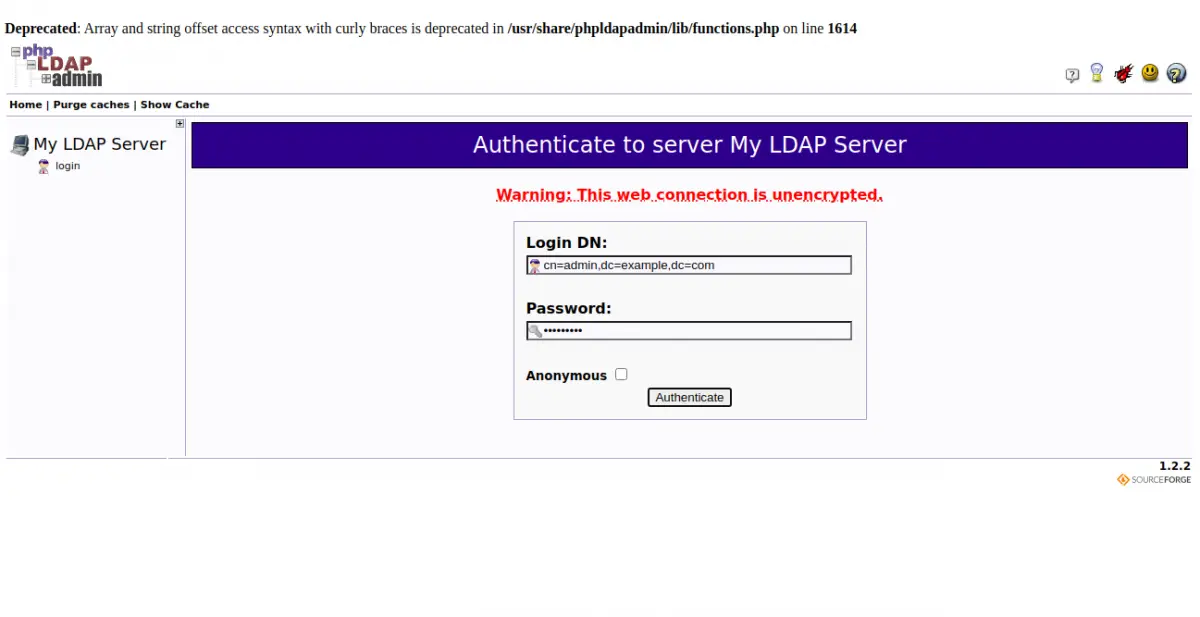
Now, click on the login button. You should see the phpLDAPadmin login screen:
Provide your login DN, password and click on the Authenticate button. You should see the phpLDAPadmin dashboard in the following screen:
Conclusion
Congratulations! you have successfully installed and configured phpLDAPadmin on Ubuntu 20.04 server. You can now manage your LDAP server and perform several tasks including, adding organizational units, groups, and users with phpLDAPadmin web UI. Feel free to ask me if you have any questions.