How to Enable TLS 1.3 in Nginx
On this page
Transport Layer Security (TLS) 1.3 is the latest version of the Transport Layer Security (TLS) protocol, published as an IETF standard in RFC 8446 in August 2018. TLS 1.3 protocol provides privacy and performance enhancements compared to the previous versions of TLS and non-secure HTTP.
Since version 1.13.0, Nginx has been added support for TLS 1.3. Currently, most Linux distributions don't contain the required versions of Nginx and OpenSSL in its default software repositories, so you will probably need to compile Nginx yourself against OpenSSL 1.1.1+. The only Linux distributions that have native support for TLS 1.3 are Ubuntu 18.10, Fedora 29 and Debian 10 (not yet released as of today). If you need a guide on how to compile Nginx from source you can follow this Howtoforge tutorial, if you want to install the latest OpenSSL, check out this guide. In this tutorial, I'm going to assume you already have a working TLS configuration, and you have compiled Nginx against OpenSSL 1.1.1+ by following my linked tutorial and you know how to use Let's Encrypt, or you know how to issue a self-signed certificate.
Requirements
To enable TLS 1.3 in Nginx you will need to fulfill the following requirements:
- Nginx version
1.13.0or greater built against OpenSSL 1.1.1 or greater. - A valid TLS certificate or a self-signed one. You can get a free one from Let's Encrypt.
Enable TLS 1.3 in Nginx
To enable TLS 1.3 in Nginx, just add TLSv1.3 parameter to the ssl_protocols directive.
ssl_protocols TLSv1.2 TLSv1.3;
And reload your Nginx configuration:
sudo systemctl reload nginx.service
That's all there is to do when it comes to configuring Nginx. Just one simple change and TLS 1.3 should work.
Here is the minimal virtual server configuration for TLS 1.3 that can look something like this:
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name example.com;
root /var/www/example.com/public;
ssl_certificate /path/to/your/certificate.crt;
ssl_certificate_key /path/to/your/private.key;
ssl_protocols TLSv1.2 TLSv1.3;
}
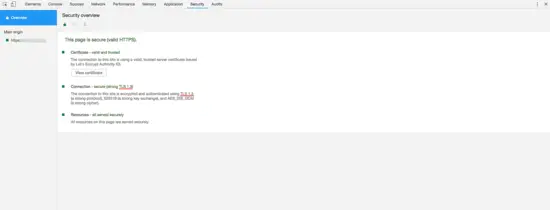
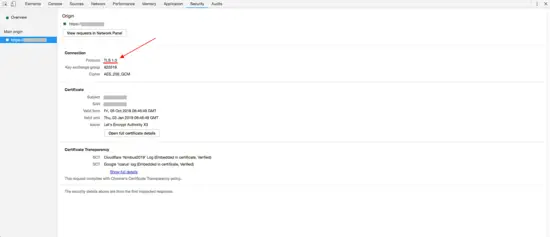
To check if your server supports TLS 1.3, you can use your browser dev tools or SSLLabs server test. The below are the screenshots from Google Chrome browser that show TLS 1.3 in action.
And that's all there is to enabling TLS 1.3 on your Nginx server.