Install WireGuard VPN on Debian 12
This tutorial exists for these OS versions
- Debian 12 (Bookworm)
- Debian 11 (Bullseye)
On this page
Wireguard is an open-source VPN protocol alternative to IPSec, IKEv2, and OpenVPN. Wiruguard is designed for Linux and Unix operating systems, it runs on Linux kernel space, which makes the Wireguard faster and more reliable. Wireguard is used to create secure tunnel connections between two computers or more.
Wireguard aims to replace VPN protocols such as IPSec, IKEv2, and OpenVPN. Wireguard is lighter, faster, easy to set up, and more efficient. At the same time, Wiregurad did not sacrifice the security aspect of the VPN protocol. Wireguard supports modern cryptography like the Noise protocol framework, Curve25519, ChaCha20, Poly1305, BLAKE2, SipHash24, HKDF, and secure trusted constructions.
This guide will show you how to install Wireguard VPN on the Debian 12 server and configure the Wireguard client on a Linux machine.
Prerequisites
Before diving in, make sure you have these requirements:
- A Linux server running Debian 12.
- A non-root user with sudo privileges.
- A client machine - In this case using the Debian-based distribution.
Preparing System
Before installing Wireguard, you must prepare your Debian server by making the following changes:
- Enable Port Forwarding via /etc/sysctl.conf
- Installing and configuring UFW
Now let's start.
Enable Port Forwarding
To enable port forwarding, you must enable the kernel module net.ipv4. ip_forward for IPv4 or net. ipv6.conf. all. forwarding for IPv6. Those kernel modules can be enabled via the/etc/sysctl.conf file.
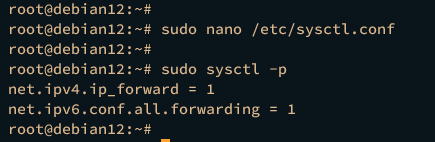
Open the /etc/sysctl.conf file using the following nano editor command.
sudo nano /etc/sysctl.conf
Insert the following configuration to enable port-forwarding for both IPv4 and IPv6 (if needed).
# Port Forwarding for IPv4
net.ipv4.ip_forward=1
# Port forwarding for IPv6
net.ipv6.conf.all.forwarding=1
Save the file and exit the editor when finished.
Now apply the changes via the sysctl command below.
sudo sysctl -p
Installing UFW
The default firewall on Debian is iptables, and now you will install UFW. You will use both UFW and iptables for the Wirguard server.
Execute the apt command below to update your repository and install UFW to your Debian system.
sudo apt update && sudo apt install ufw -y
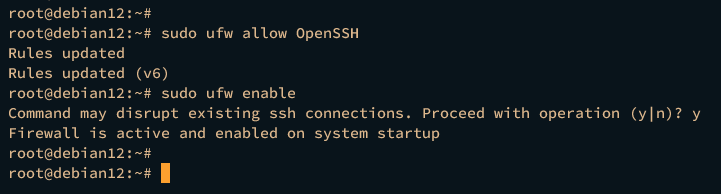
Next, run the ufw command below to add the OpenSSH application profile and enable UFW. Type y and press ENTER to confirm, and you should get the message "Firewall is active and enabled on system startup".
sudo ufw allow OpenSSH
sudo ufw enable
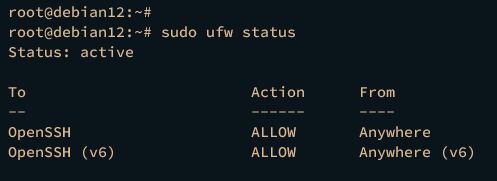
Lastly, verify the UFW status using the command below.
sudo ufw status
If running, you should get the output "Status: active." You will also see that the OpenSSH application profile is added to UFW.
Installing Wireguard Server
After configuring the Debian server, you're ready to create a Wireguard VPN Server on your Debian machine. Complete the following task to achieve it:
- Installing Wireguard
- Generating Wireguard Server Key
- Generating Wireguard Client Key
- Configuring Wireguard Interface
- Setting up NAT for Wireguard Interface
Let's do this.
Installing Wireguard
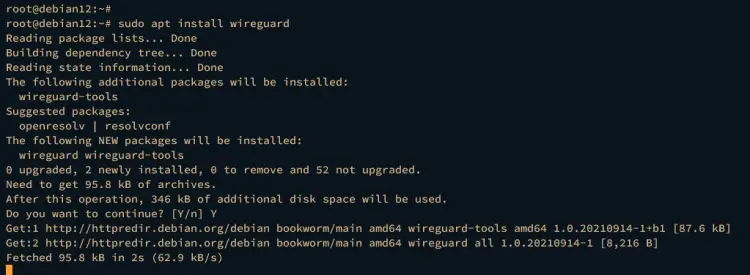
First, install the wireguard package to your Debian server by executing the following command.
sudo apt install wireguard
Type y to proceed with the installation.
Generating Wireguard Server Key
After the wireguard package is installed, the next task is to generate server certificates, which can be done using the wg command line tool.
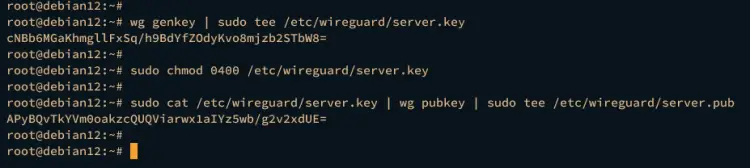
Execute the following command to generate the wireguard server private key to /etc/wireguard/server.key. Then, change the permission of the server private key to 0400, which means you will disable the write access to the file.
wg genkey | sudo tee /etc/wireguard/server.key
sudo chmod 0400 /etc/wireguard/server.key
Next, run the following command to generate the wireguard server public key to /etc/wireguard/server.pub.
sudo cat /etc/wireguard/server.key | wg pubkey | sudo tee /etc/wireguard/server.pub
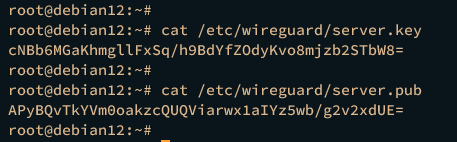
Now that you've generated the private key to /etc/wireguard/server.key and public key to /etc/wireguard/server.pub for your wireguard server. You can execute the cat command below to show the content of both private and public keys.
cat /etc/wireguard/server.key
cat /etc/wireguard/server.pub
You may have a different output, but the generated keys look like the following:
Generating Wireguard Client Key
With the wireguard server key generated, the next task is to generate keys for clients. You can generate client keys for each of user, but you can also use a single key for multiple users.
In this example, you will generate a client key for a specific user alice.
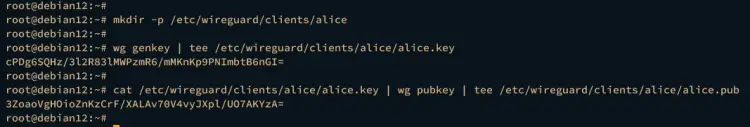
To begin, execute the following command to create a new directory for storing client keys. In this case, the public and private keys for user alice will be generated to the /etc/wireguard/clients/alice directory.
mkdir -p /etc/wireguard/clients/alice
Now, run the following command to generate the private key /etc/wireguard/clients/alice/alice.key and public key /etc/wireguard/clients/alice/alice.pub for user alice.
wg genkey | tee /etc/wireguard/clients/alice/alice.key
cat /etc/wireguard/clients/alice/alice.key | wg pubkey | tee /etc/wireguard/clients/alice/alice.pub
Lastly, run the below command to show the content of private and public keys for user alice.
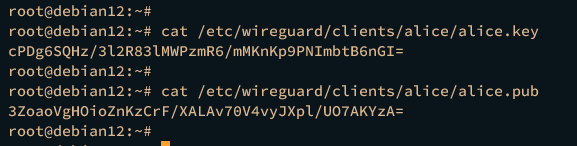
cat /etc/wireguard/clients/alice/alice.key
cat /etc/wireguard/clients/alice/alice.pub
The similar output like the following will be displayed:
Configuring Wireguard Interface
Now that you've generated private and public keys for both the server and client, the next task is to configure the Wireguard interface and peer. You will configure an interface for the Wireguard network VPN and peer that will establish between the client and server.
Create a new Wireguard configuration /etc/wireguard/wg0.conf using the following nano editor command.
sudo nano /etc/wireguard/wg0.conf
Insert the following configuration into the file.
[Interface]
# Wireguard Server private key - server.key
PrivateKey = cNBb6MGaKhmgllFxSq/h9BdYfZOdyKvo8mjzb2STbW8=
# Wireguard interface will be run at 10.10.0.1
Address = 10.10.0.1/24
# Clients will connect to UDP port 51820
ListenPort = 51820
# Ensure any changes will be saved to the Wireguard config file
SaveConfig = true
Below details parameters that will be used within the [Interface] section:
- PrivateKey: Input the content wireguard server private key server.key.
- Address: the IP address that will be assigned to the Wireguard interface. In this case, the wireguard interface will have an IP address of 10.10.0.1.
- ListenPort: This is the port that will be used by the client to connect to the wireguard server. In this case, port 51820 will be used.
- SaveConfig: the value true means any changes will be saved from the current state of the interface to shutdown.
Now add the following [Peer] section for wireguard clients.
[Peer]
# Wireguard client public key - alice.pub
PublicKey = 3ZoaoVgHOioZnKzCrF/XALAv70V4vyJXpl/UO7AKYzA=
# clients' VPN IP addresses you allow to connect
# possible to specify subnet ⇒ [10.10.0.0/24]
AllowedIPs = 10.10.0.2/24
Below are the parameters that are used within the [Peer] section:
PublicKey: Input the wireguard client public key to this parameter. In this case, the content of the public key alice.pub.
AllowedIPs: Define the IP address for the client and route the traffic to the wireguard interface.
Save and close the file when you're done.
Lastly, run the following command to open port 51820/udp for client connections.
sudo ufw allow 51820/udp
Setting up NAT for Wireguard Interface
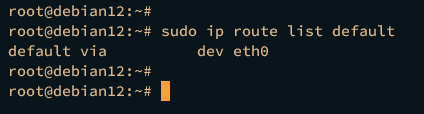
First, run the following command to show the default gateway interface that is used to connect to the internet.
sudo ip route list default
In this case, the default network internet gateway is interface eth0.
Now open the wireguard configuration /etc/wireguard/wg0.conf using the following nano editor command.
sudo nano /etc/wireguard/wg0.conf
Add the following configuration under the [Interface] section, and be sure to change the interface eth0 with the default internet gateway interface.
[Interface]
...
PostUp = ufw route allow in on wg0 out on eth0
PostUp = iptables -t nat -I POSTROUTING -o eth0 -j MASQUERADE
PostUp = ip6tables -t nat -I POSTROUTING -o eth0 -j MASQUERADE
PreDown = ufw route delete allow in on wg0 out on eth0
PreDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
PreDown = ip6tables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
Save and close the file when finished.
At this point, you have configured your Wireguard server.
Managing Wireguard Service
Now that the Wireguard server installation and configuration are complete, you're ready to start the Wireguard service on your Debian system. This can be done via systemctl command or by using the wg-quick utility.
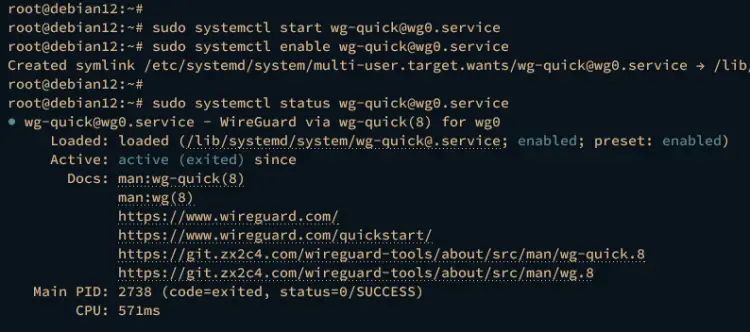
To start and enable the wireguard server, run the following systemctl command. With the service name wg-quick@wg0, you will start the Wireguard within the wg0 interface, which is based on the configuration /etc/wireguard/wg0.conf.
sudo systemctl start [email protected]
sudo systemctl enable [email protected]
Now verify the wirguard@wg0 service using the following command.
sudo systemctl status [email protected]
If the service is running, the following output will be displayed.
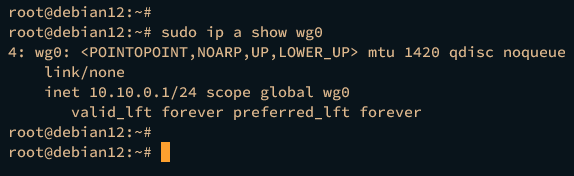
Next, run the ip command below to show details of wireguard interface wg0. And you should see the wireguard interface wg0 has an IP address 10.10.0.1.
sudo ip a show wg0
You can also start or stop the wireguard manually via the wg-quick command below.
sudo wg-quick up /etc/wireguard/wg0.conf
sudo wg-quick down /etc/wireguard/wg0.conf
With this, you have configured the wireguard server and started it in the background via the systemctl command. Your client is now ready to connect to the wireguard server.
Setting up Wireguard Client on Debian-based Distribution
In the following section, you will configure the wireguard client for the Debian-based distribution. You will install wireguard tools, create a wireguard client configuration, connect to the wireguard server, verify the connection via the wg utility, and access the Internet.
Install the wireguard-tools package to the client machine via APT. The client machine is a Debian-based distribution, so the APT package manager will be used.
sudo apt install wireguard-tools resolvconf
After installing the wireguard-tools, create a new wireguard client configuration /etc/wireguard/wg-alice.conf using the following nano editor.
sudo nano /etc/wireguard/wg-alice.conf
Insert the following configuration into the file.
[Interface]
# Define the IP address for the client - must be matched with wg0 on the Wireguard Server
Address = 10.10.0.2/24
# specific DNS Server
DNS = 1.1.1.1
# Private key for the client - alice.key
PrivateKey = cPDg6SQHz/3l2R83lMWPzmR6/mMKnKp9PNImbtB6nGI=
[Peer]
# Public key of the Wireguard server - server.pub
PublicKey = APyBQvTkYVm0oakzcQUQViarwx1aIYz5wb/g2v2xdUE=
# Allow all traffic to be routed via Wireguard VPN
AllowedIPs = 0.0.0.0/0
# Public IP address of the Wireguard Server
Endpoint = 192.168.128.15:51820
# Sending Keepalive every 25 sec
PersistentKeepalive = 25
Save and close the file when you're done.
Below are some of the parameters within the [Interface] section for wireguard clients:
- Address: specify the internal IP address of the wireguard interface on the client machine.
- DNS: set up the default DNS server for the client.
- PrivateKey: the wireguard client private key, in this case, is alice.key.
And within the [Peer] section on the wireguard client configuration:
- PublicKey: this is the public key of the wireguard server, which is server.pub.
- AllowedIPs: Allow any access to be routed via the wireguard interface.
- Endpoint: the IP address and port of the wireguard server.
- PersistentKeepalive: send keepalive for every x seconds to keep the connection up.
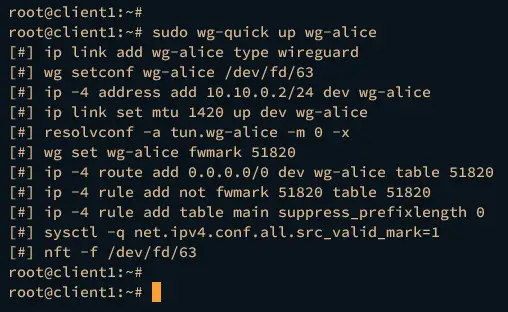
Next, run the wg-quick command below to start the wireguard on the interface wg-alice.
sudo wg-quick up wg-alice
If everything goes well, the similar output below will be shown.
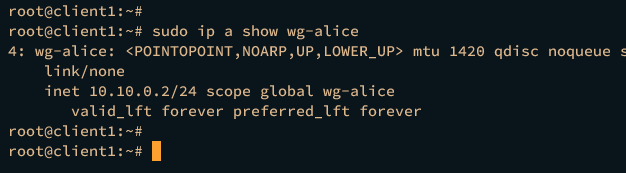
After that, run the ip command below to check the details interface wg-alice. And you should see the wg-alice interface with the local IP address 10.10.0.2.
sudo ip a show wg-alice
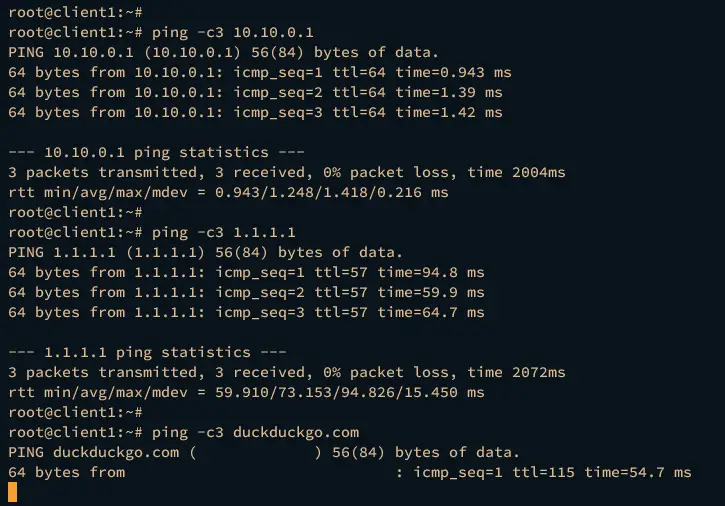
Next, verify the internet connection of the client machine by executing the following command.
ping -c3 10.10.0.1
ping -c3 1.1.1.1
ping -c3 duckduckgo.com
If your wireguard server installation is successful, you will the answer from each target server like the following:
Furthermore, you can also detail connections between the wireguard server and the client by executing the following command on the wireguard server or the client machine.
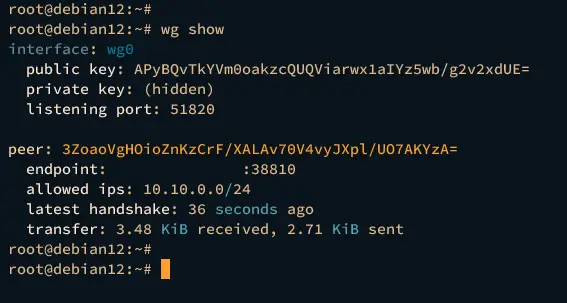
wg show
The similar output below will be shown.
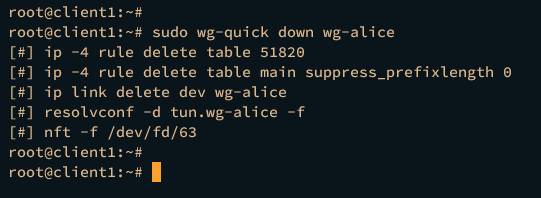
Lastly, to stop the wireguard connection on the client machine, run the wg-quick command below.
sudo wg-quick down wg-alice
Conclusion
To wrap up, you have now completed the installation of Wireguard VPN on the Debian 12 server step-by-step. You've also configured A Debian-based client machine with Wireguard and connected to the Wireguard Server. With this in mind, you can now add more clients by adding more Wireguard keys and Peer configuration.