Using Firewall Builder To Configure Cisco ASA & PIX - Page 4
Getting Started: Configuring Cisco ASA & PIX
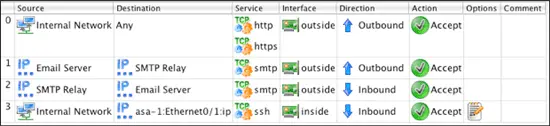
For the following sections we are going to assume that the following Policy rules have been configured for the firewall configuration shown in the diagram above.
And that the following two NAT rules have been configured for the firewall shown in the diagram above.
Step 4: Compile and Install
In Firewall Builder the process of converting the rules from the Firewall Builder GUI syntax to the target device commands is called compiling the configuration.
To compile, click on the Compile icon which looks like a hammer ![]() . If you haven't saved your configuration file yet you will be asked to do so. After you save your file a wizard will be displayed that lets you select which firewall(s) you want to compile. In this example we are going to complie the firewall called asa-1 configured with the rules above.
. If you haven't saved your configuration file yet you will be asked to do so. After you save your file a wizard will be displayed that lets you select which firewall(s) you want to compile. In this example we are going to complie the firewall called asa-1 configured with the rules above.
If there aren't any errors, you should see some messages scroll by in the main window and a message at the top left stating Success.
To view the output of the compile, click on the button that says Inspect Generated Files. This will open the file that contains the commands in Cisco command format. Note that any line that starts with "!" is a comment.
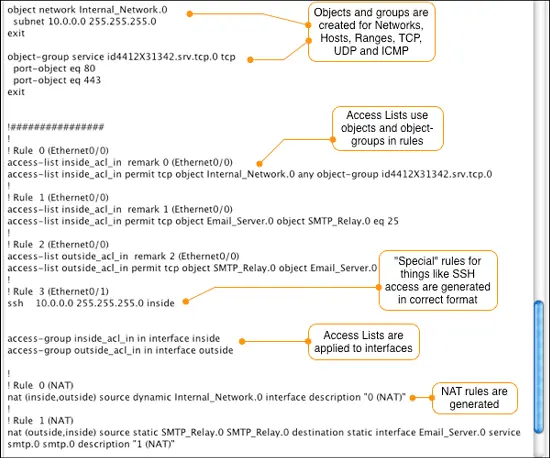
The output from the compiler is automatically saved in a file in the same directory as the data file that was used to create it. The generated files are named with the firewall name and a .fw extension. In our example the generated configuration file is called asa-1.fw. You can copy and copy and paste the commands from this file to your firewall or you can use the built-in Firewall Builder installer.
Installing
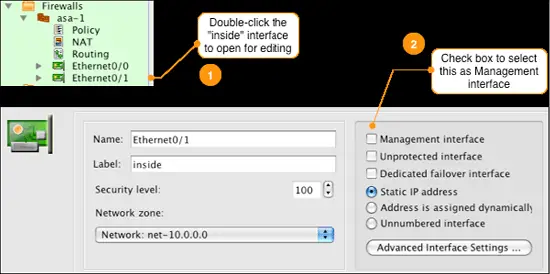
Firewall Builder can install the generated configuration file for you using SSH. To use the installer we need to identify one of the firewall interfaces as the "Management Interface". This tells Firewall Builder which IP address to use to connect to the firewall.
Do this by double-clicking the firewall object to expand it, and then double-clicking on the interface name that you want to assign as the management interface. In our case this is interface Ethernet0/1 which is the interface connected to the internal network.
CAUTION! Any time you are changing access lists on your firewall you face the risk of locking yourself out of the device. Please be careful to always inspect your access lists closely and make sure that you will be able to access the firewall after the access list is installed.
To install your access lists on the firewall, click on the install icon ![]() . This will bring up a wizard where you will select the firewall to install. Click Next > to install the selected firewall.
. This will bring up a wizard where you will select the firewall to install. Click Next > to install the selected firewall.
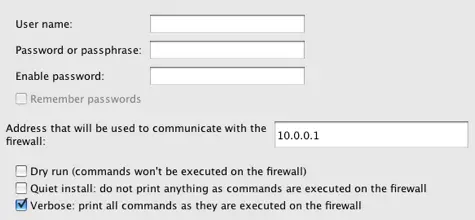
Firewall Builder will compile your rules converting them in to Cisco access list command line format. After the compile completes successfully click Next >. Enter your username, password and enable password.
After the access list configuration is installed you see a message at the bottom of the main window and the status indicator in the upper left corner of the wizard will indicate if the installation was successful.
By default Firewall Builder will use SCP to copy the generated config file to the firewall. Once the file is copied to the firewall, Firewall Builder will connect using SSH to load the transferred config file from memory using the "copy" command to merge the Firewall Builder generated command with the current running configuration.
Firewall Builder requires ssh version 2 to be enabled on the firewall.
You can find more information about Firewall Builder, including the complete Users Guide, at http://www.fwbuilder.org/.