How to Setup Port-Forwarding on OPNSense
NAT or Network Address Translation is the process of remapping one IP Address space into another by modifying the network addressing information in IP header packets. NAT will enable a LAN network to use one set of IP addresses for internal traffic and a second set of addresses for external traffic.
In a common scenario, NAT will allow a private LAN to access the public internet. It's called an 'Outbound NAT'. And allow public internet to access to the server inside a private LAN. It's called a 'Port Forward'.
By default, the outbound NAT on the OPNSense has been enabled. If you're configuring your firewall correctly, the private LAN already have an internet connection through the OPNSense WAN interface. All outgoing internet connections from the private LAN will be detected as the OPNSense WAN IP address.
This guide will show you how to set up NAT Port Forwarding on the OPNSense Firewall Router. We will allow public internet to access the server inside the private LAN. Allow SSH and HTTP connections from the public internet to the server on the private LAN.
1. Environment Configuration
For this guide, we already have an OPNSense installed on VirtualBox and the Ubuntu Server running inside the OPNSense private LAN.
Below are detailed network configurations for both the OPNSense firewall router and the Ubuntu server.
OPNSense Firewall Router
- LAN IP: 10.5.5.1/24
- WAN IP: 192.168.1.25/24
- DHCP: ON
- DHCP Range IP: 10.5.5.10-10.5.5.50
Ubuntu Server
- Interface: eth0
- LAN IP: 10.5.5.11/24
2. Testing Ubuntu Server
Firstly, we will ensure the connection on the Ubuntu server is working correctly by checking its IP address and the default route of the network.
Run the following command on the Ubuntu Server.
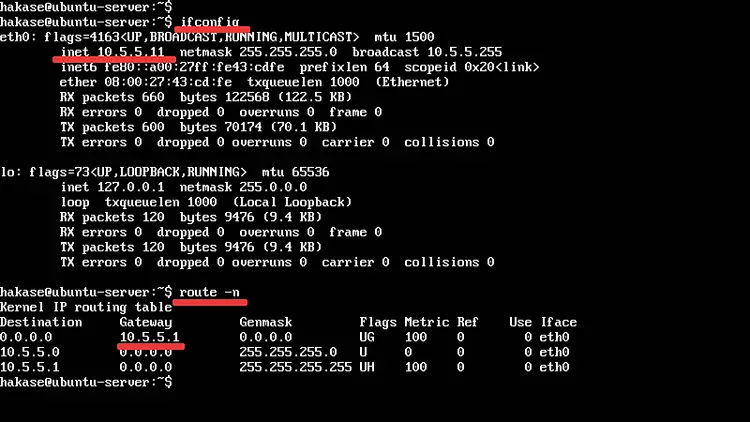
ifconfig
route -n
And you will get the result as below.
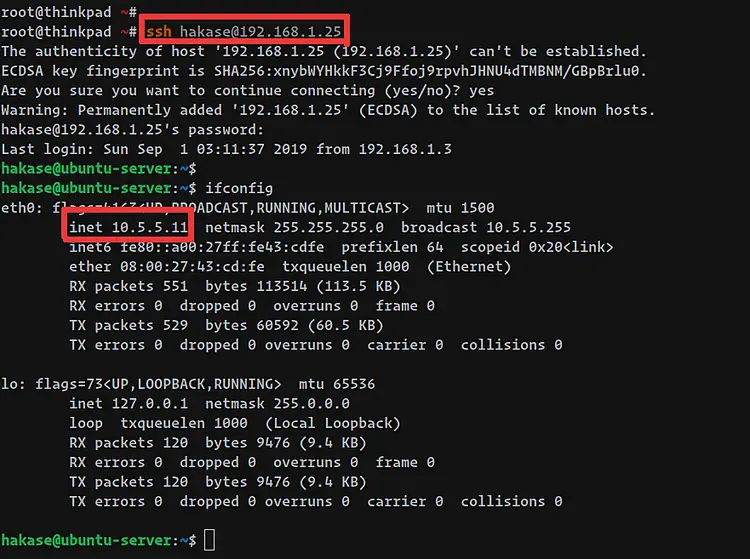
The Ubuntu Server with the IP address '10.5.5.11', and the default gateway '10.5.5.1'.
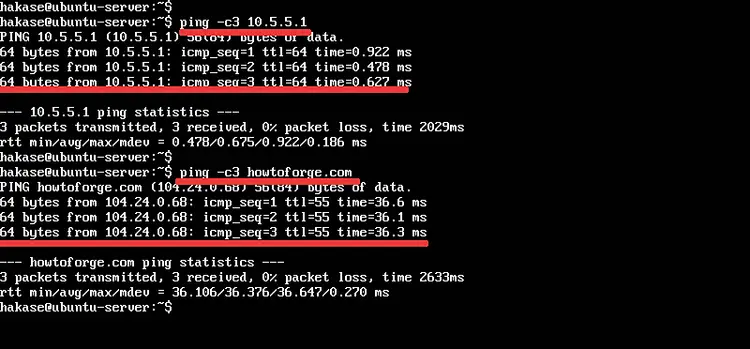
Next, test the internet connection on the Ubuntu server using the ping command below.
ping -c3 10.5.5.1
ping -c3 howtoforge.com
Below is the result.
The Ubuntu server on the private LAN has an internet connection through the OPNSense firewall router.
3. Create NAT Port Forwarding for SSH Service
This step will create the NAT Port Forwarding for the SSH Connection to the Ubuntu Server.
Log in to the OPNSense web admin dashboard with your root user and password.
https://10.5.5.1:8443/
Note:
Change the port '8443' with your own port because it's the custom port for the OPNSense Admin Dashboard.
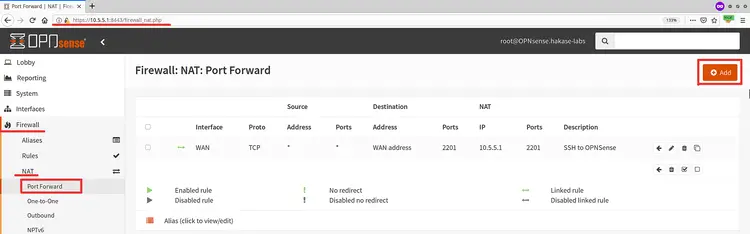
Next, we will create the NAT Port Forwarding on the WAN interface port 22, and any incoming connection to the WAN IP address on port 22 will be redirected to the private LAN IP address '10.5.5.11' port 22.
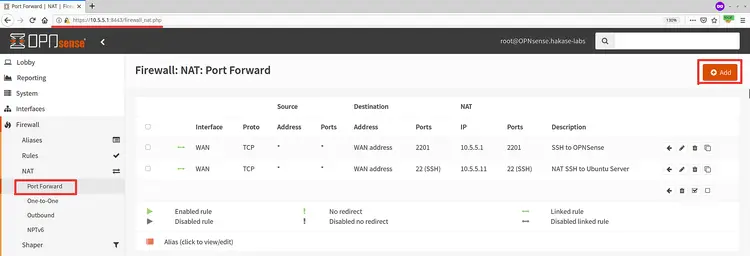
On the left side, click the menu 'Firewall > NAT > Port Forward'.
Now click the 'Add' button to add a new NAT Port Forwarding rule.
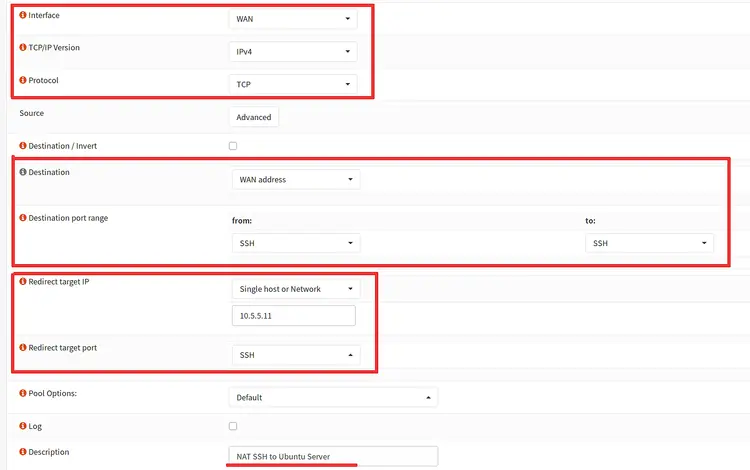
Now, create the NAT Port Forwarding configuration for the SSH service as below.
Interface: WAN
TCP/IP Version: IPv4
Protocol: TCP
Destination: WAN Address
Destination Port Range: SSH
Redirect target IP: 10.5.5.11
Redirect target Port: SSH
Description: NAT SSH to Ubuntu Server
Now click the 'Save' button on the bottom, and you will be redirected to the Port Forward page. Click the 'Apply Changes' button to apply new configuration. The NAT Port Forwarding for SSH access to the Ubuntu Server has been created and applied.
Next, we will try to access the Ubuntu server through the OPNSense WAN IP address using the ssh command below.
ssh [email protected]
Type Your Password:
You will be logged in to the Ubuntu Server on the Private LAN through the OPNSense NAT Port Forwarding.
Test the server using the ifconfig command, and you will get the same results as on top (See section 1).
ifconfig
route -n
The NAT Port Forwarding for SSH service to the Ubuntu Server has been created. You can connect to the Ubuntu Server from outside of the network.
4. Create NAT Port Forwarding for HTTP Service
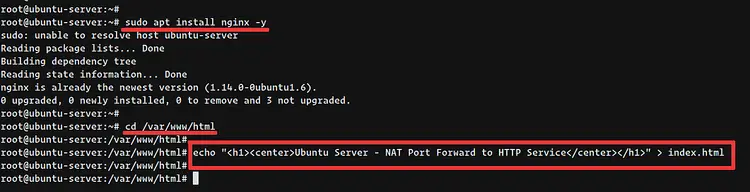
Before creating the NAT rule for the HTTP service, let's install the Nginx web server on the Ubuntu server.
sudo apt install nginx -y
Once the installation is complete, go to the siteroot directory '/var/www/html' and create a new custom 'index.html' page.
cd /var/www/html
echo "<h1><center>Ubuntu Server - NAT Port Forwarding to HTTP Service</center></h1>" > index.html
After that, back to the OPNSense administration dashboard.
Click the 'Firewall > NAT > Port Forward' menu on the left.
Now click the 'Add' button to add a new NAT Port Forwarding rule.
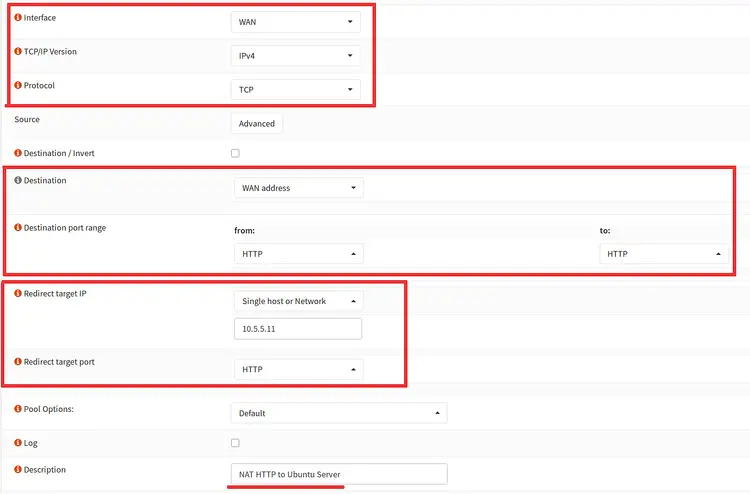
Now create the NAT Port Forwarding configuration for the HTTP service as below.
Interface: WAN
TCP/IP Version: IPv4
Protocol: TCP
Destination: WAN Address
Destination Port Range: HTTP
Redirect target IP: 10.5.5.11
Redirect target port: HTTP
Description: NAT HTTP to Ubuntu Server
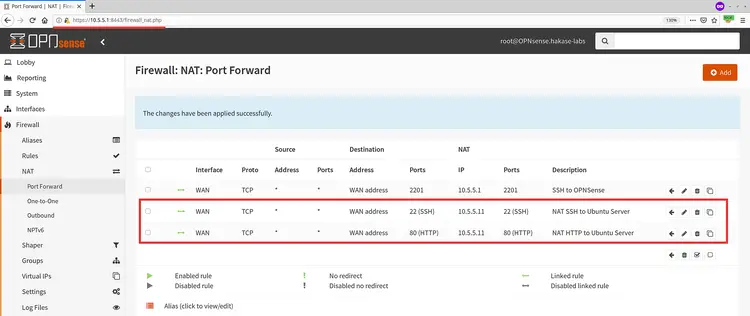
Now click the 'Save' button on the bottom page, and you will be redirected to the Port Forward page. Click the 'Apply Changes' button to applied the changes. The NAT Port Forwarding for HTTP Service has been added.
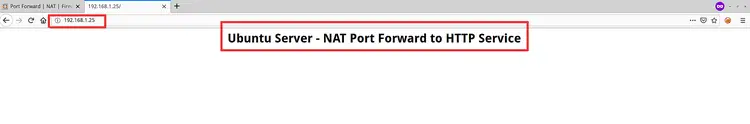
Next, open your web browser and type the OPNSense WAN IP address.
http://192.168.1.25/
And you will get the result as below.
As a result, the Nginx HTTP web server on the Private network is accessible from the outside through the OPNSense firewall router.
Now, you can try to set up another NAT Port Forwarding for your application through the OPNSense firewall router.