How to Install a DNS Server with BIND on Rocky Linux 9
BIND or Berkeley Internet Name Domain is free and open-source DNS Server software. It's one of the most popular DNS server software used by more than 70% of DNS on the Internet. BIND has been around since the 1980s, well-known for its flexibility, performance, and features. BIND can be used as both authoritative DNS and caching DNS, and supports load balancing, dynamic update, split DNS, DNSSEC, IPv6, and many more.
The BIND DNS software is one of the most reliable DNS servers for Unix-like operating systems. It's available on most Linux distributions and provides additional tools for diagnostics and testing of the DNS server.
This tutorial will show you how to set up DNS Server with BIND on a Rocky Linux 9 server. BIND is one of the most popular DNS Server software that provides various features such as Authoritative DNS, Cache-Only DNS, Basic DNS load balancing, Split DNS, DNSSEC, IPv6, and many more.
Prerequisites
With this tutorial, you will set up and implement a BIND DNS Server with Master-Slave architecture. So, you will need two Rocky Linux servers. Also, you'll need root/administrator privileges on each server.
To set up a public DNS server that can handle your domain (Authoritative DNS Server), you must also have the domain name registered and 'Glue Records' configured.
Also, in this guide, we'll assume that you have the SELinux is running with the 'permissive' mode.
Preparing the System
To begin with this guide, you'll set up the correct FQDN (Fully Qualified Domain Name) on each of your Rocky Linux servers. This can be done via the 'hostnamectl' command utility and the '/etc/hosts' file.
Below are the details servers that will be used as an example for this guide:
Hostname IP Address FQDN Used as
---------------------------------------------------------------
ns1 192.168.5.100 ns1.howtoforge.local Master
ns2 192.168.5.120 ns2.howtoforge.local Slave
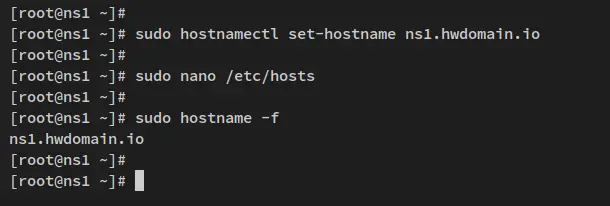
On the master server, run the below hostnamectl command utility to set up the fqdn to 'ns1.howtoforge.local'.
sudo hostnamectl set-hostname ns1.howtoforge.local
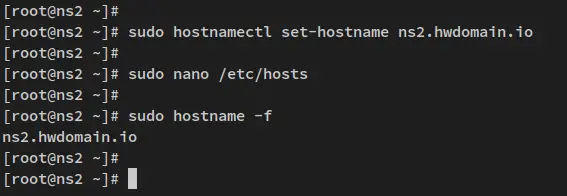
Below you also need to run the hostnamectl command on the Slave server to set up the fqdn to 'ns2.howtoforge.local'.
sudo hostnamectl set-hostname ns2.howtoforge.local
Next, open the file '/etc/hosts' on both Master and Slave servers using the following nano editor command.
sudo nano /etc/hosts
Add the following line to the file.
192.168.5.100 ns1.howtoforge.local ns1
192.168.5.120 ns2.howtoforge.local ns2
Save the file and exit the editor when you're finished.
Lastly, run the following 'hostname' command to verify the fqdn on each server. You should see the Master server has the fqdn as 'ns1.howtoforge.local', and the Slave server has the fqdn 'ns2.howtoforge.local'.
sudo hostname -f
Below is the output from the Master server.
And below is the output from the Slave server.
With the fqdn configured, you're ready to install BIND on Rocky Linux servers.
Installing BIND Packages
By default, the Rocky Linux AppStream repository provides the latest stable version of the BIND package. At the time of this writing, the current stable version of BIND is v9.16.
In this step, you will install BIND packages on both Master and Slave servers. Then set up BIND to run on the IPv4 only, and configure the firewalld to allow DNS port.
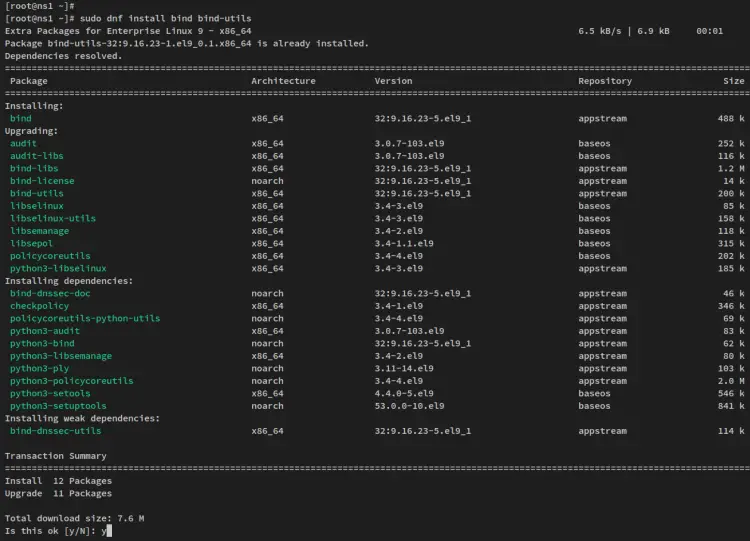
Run the below dnf command to install BIND packages to both the Master and Slave servers. When prompted for the confirmation, input y to confirm and press ENTER to proceed.
sudo dnf install bind bind-utils
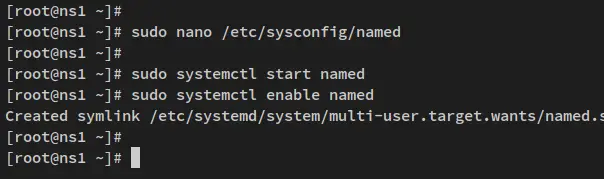
After the BIND packages is installed, open the configuration '/etc/sysconfig/named' using the following nano editor command.
sudo nano /etc/sysconfig/named
Add the default 'OPTIONS=..' with the following line. This command option for 'bind' or 'named' will run the BIND on IPv4 only.
OPTIONS="-4"
Save the file and exit the editor when you are finished.
Next, run the below systemctl command utility to start and enable the BIND service 'named'. The 'named' service should now be running and enabled, which will automatically start upon the bootup.
sudo systemctl start named
sudo systemctl enable named
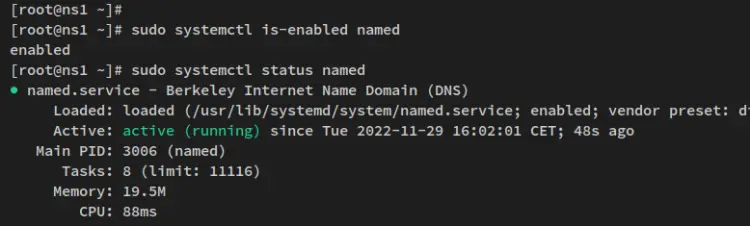
Now verify the 'named' service to ensure that the service is running and enabled via the following command.
sudo systemctl is-enabled named
sudo systemctl status named
You'll receive similar output to the following - The BIND 'named' service is enabled, and it's currently running.
With the BIND 'named' service is running, you'll need to add the DNS port to the firewalld, which is enabled and running by default on Rocky Linux.
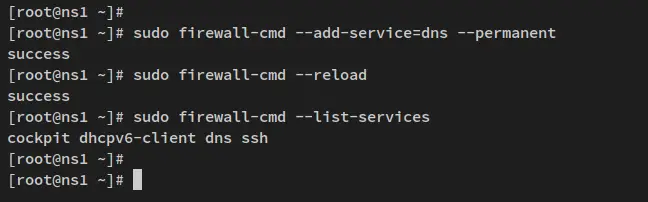
Run the below firewall-cmd command utility to add the DNS service to the firewalld. Then reload the firewalld to apply the changes.
sudo firewall-cmd --add-service=dns --permanent
sudo firewall-cmd --reload
If you verify the list of enabled services on firewalld, you should see that the DNS service is enabled. Run the below firewall-cmd command to check the list of services.
sudo firewall-cmd --list-services
Output:
At this point, you've finished the fqdn configuration, installed BIND packages, and also configured the firewalld. With this in mind, you can now start configuring the BIND Master on the Master server.
Configuring Master BIND DNS Server
In this step, you will set up the BIND Master server using the Rocky Linux 'ns1.howtoforge.local' and the server IP address is '192.168.5.100'. Ensure that you run the following commands on the Master server.
You'll configure the BIND Master server with the following steps:
- Basic Configuration will include the configuration of ACLs (Access Control Lists), setting up which IP address to run the BIND service, setting up forwarders, and many more.
- Setting up Zones - This is where you create configurations for your domain. This includes the main domain configuration and the reverse DNS configuration.
Basic Configuration
The default BIND configuration on RHEL-based distribution is available at '/etc/named.conf'.
Now open the file '/etc/named.conf' using the following nano editor command below.
sudo nano /etc/named.conf
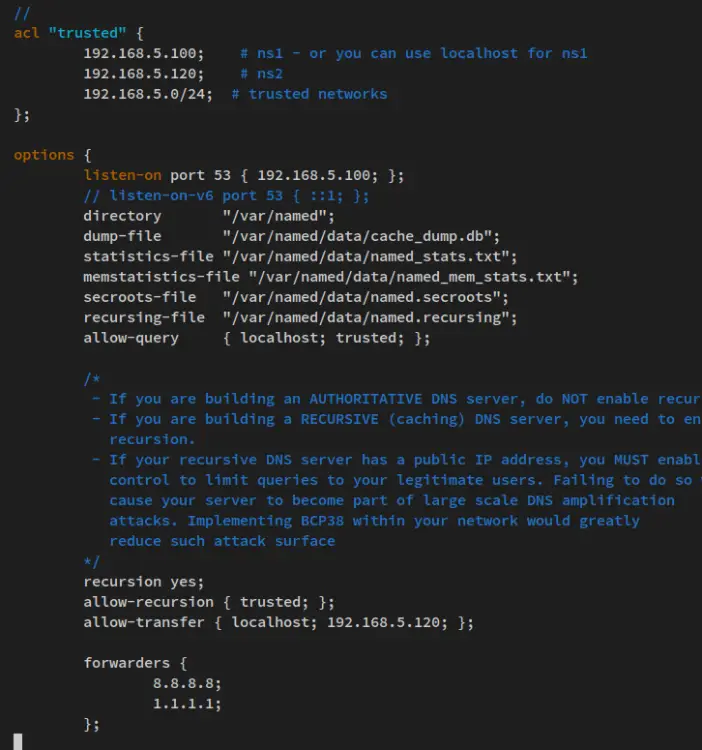
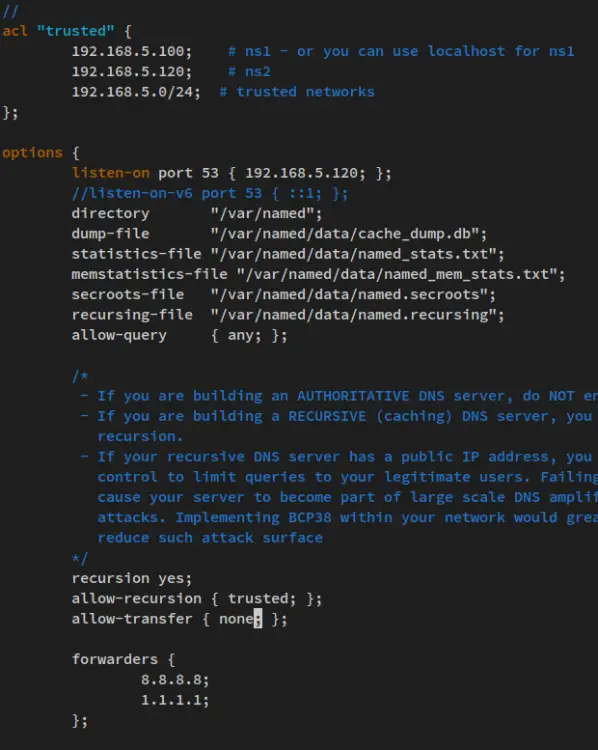
Change the default configuration with the following lines.
acl "trusted" {
192.168.5.100; # ns1 - or you can use localhost for ns1
192.168.5.120; # ns2
192.168.5.0/24; # trusted networks
};
options {
listen-on port 53 { 192.168.5.100; };
// listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
secroots-file "/var/named/data/named.secroots";
recursing-file "/var/named/data/named.recursing";
allow-query { localhost; trusted; };
recursion yes;
allow-recursion { trusted; };
allow-transfer { localhost; 192.168.5.120; };
forwarders {
8.8.8.8;
1.1.1.1;
};
Save the file and exit the editor when you're finished.
With this configuration, you'll set up BIND with the following configurations:
- Set up an ACL 'trusted' that allows any query from local networks.
- Run the BIND service at '192.168.5.100' with default port '53'.
- Enable recursion and allow recursion from the 'trusted' ACL networks.
- Allow zones transfer to the Slave server with IP address '192.168.5.120'.
- Set up forwarders with the public DNS server 1.1.1.1 from Cloudflare and 8.8.8.8 from Google.
Next, run the below command to verify the BIND configuration '/etc/named.conf'.
sudo named-checkconf /etc/named.conf
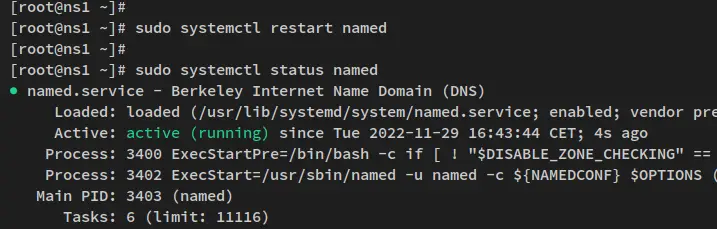
Lastly, run the below systemctl command utility to restart the BIND 'named' service and apply the changes.
sudo systemctl restart named
You have now finished the basic configuration of the BIND DNS Server.
Setting up Zones
Now you'll set up zones with the BIND DNS Server. You'll create a new DNS Server with the address 'ns1.howtoforge.local' and 'ns2.howtoforge.local'.
To start, open the BIND configuration '/etc/named.conf' via the nano editor command below.
sudo nano /etc/named.conf
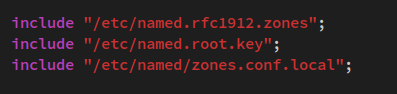
Add the following configuration to the bottom of the line.
include "/etc/named/zones.conf.local";
Save the file and exit the editor when you're finished.
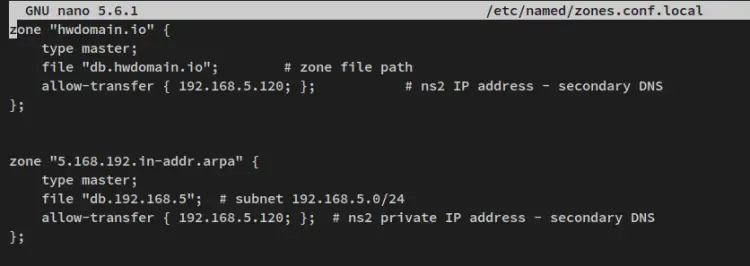
Next, create a new configuration '/etc/named/zones.conf.local' using the below nano editor.
sudo nano /etc/named/zones.conf.local
Add the following lines to the file.
zone "howtoforge.local" {
type master;
file "db.howtoforge.local"; # zone file path
allow-transfer { 192.168.5.120; }; # ns2 IP address - secondary DNS
};
zone "5.168.192.in-addr.arpa" {
type master;
file "db.192.168.5"; # subnet 192.168.5.0/24
allow-transfer { 192.168.5.120; }; # ns2 private IP address - secondary DNS
};
Save and close the file when you're finished.
With this configuration, you'll define the following configurations:
- Create two zones for the domain 'howtoforge.local' and the reverse DNS '5.168.192.in-addr.arpa'.
- Both zones type as 'master'.
- Allow zone transfer to the Slave DNS Server that will be running on server IP address '192.168.5.120'.
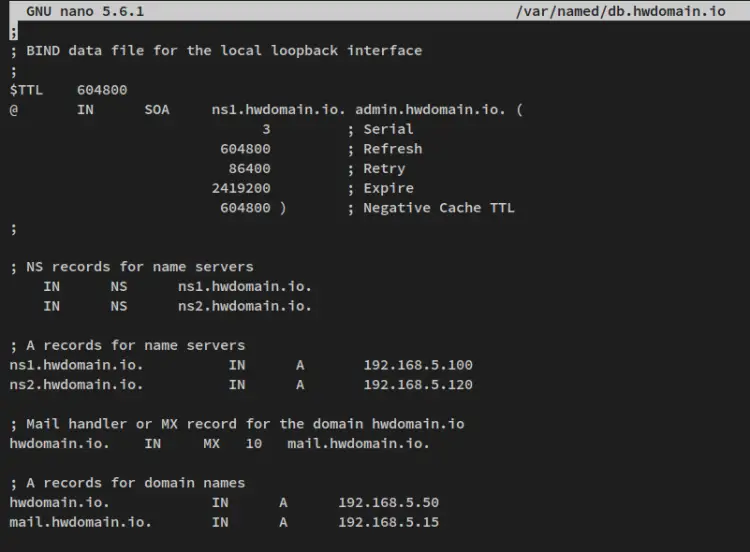
Next, create a new DNS zone configuration, '/var/named/db.howtoforge.local', using the following nano editor command.
sudo nano /var/named/db.howtoforge.local
Add the following lines to the file.
;
; BIND data file for the local loopback interface
;
$TTL 604800
@ IN SOA ns1.howtoforge.local. admin.howtoforge.local. (
3 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
; NS records for name servers
IN NS ns1.howtoforge.local.
IN NS ns2.howtoforge.local.
; A records for name servers
ns1.howtoforge.local. IN A 192.168.5.100
ns2.howtoforge.local. IN A 192.168.5.120
; Mail handler or MX record for the domain howtoforge.local
howtoforge.local. IN MX 10 mail.howtoforge.local.
; A records for domain names
howtoforge.local. IN A 192.168.5.50
mail.howtoforge.local. IN A 192.168.5.15
Save and close the file when you are finished.
In this example, you'll set up zones with the following configurations:
- Define the Name Server records 'ns1.howtoforge.local' with the IP address '192.168.5.100' and the 'ns2.howtoforge.local' with the IP address '192.168.5.120'.
- Define two additional domains, 'howtoforge.local', that will be resolved to the server IP address '192.168.5.50' and the domain 'mail.howtoforge.local' to the IP address '192.168.5.15'.
- You'll also create an MX record for the domain 'howtoforge.local' that the mail server ' mail.howtoforge.local will handle.
Next, you'll start configuring the reverse DNS for the domain howtoforge.local.
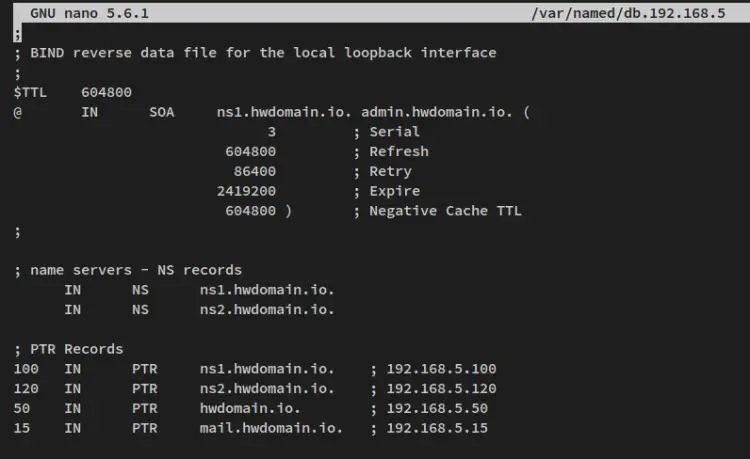
Create a new reverse DNS configuration '/var/named/db.192.168.5' using the below nano editor command.
sudo nano /var/named/db.192.168.5
Add the following lines to the file.
;
; BIND reverse data file for the local loopback interface
;
$TTL 604800
@ IN SOA ns1.howtoforge.local. admin.howtoforge.local. (
3 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
; name servers - NS records
IN NS ns1.howtoforge.local.
IN NS ns2.howtoforge.local.
; PTR Records
100 IN PTR ns1.howtoforge.local. ; 192.168.5.100
120 IN PTR ns2.howtoforge.local. ; 192.168.5.120
50 IN PTR howtoforge.local. ; 192.168.5.50
15 IN PTR mail.howtoforge.local. ; 192.168.5.15
Save and close the file when you are finished.
With this configuration, you will set up the reverse DNS or PTR records as below.
- In the reverse DNS configuration, you'll also define the name server ns1.howtoforge.local and ns2.howtoforge.local.
- Each reverse DNS configuration uses the last number of the IP address that is resolved to each domain. In this example, the name server ns1.howtoforge.local with IP address '192.168.5.100', and the PTR record should be '100'.
- The rest of the PTR records are the same as described on top.
At this point, you've created two zones configuration for the domain 'howtoforge.local' and created a name server 'ns1.howtoforge.local' and 'ns2.howtoforge.local'.
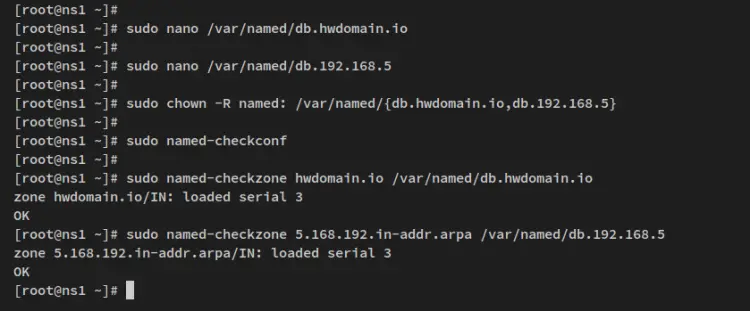
Now run the below chmod command to change the ownership of both zone configurations.
sudo chown -R named: /var/named/{db.howtoforge.local,db.192.168.5}
Then verify zone config files via the 'named-checkconf' command utility below.
sudo named-checkconf
sudo named-checkzone howtoforge.local /var/named/db.howtoforge.local
sudo named-checkzone 5.168.192.in-addr.arpa /var/named/db.192.168.5
If you have proper BIND configurations, you'll receive the output like the following screenshot.
Lastly, run the below systemctl command to restart the BIND 'named' service and apply changes. Then, verify the BIND service status to ensure that the service is running.
sudo systemctl restart named
sudo systemctl status named
You'll receive output similar to the following - the BIND 'named' service is running and you've finished the BIND Master configuration.
In the next step, you will set up the BIND Slave server.
Setting up Slave BIND DNS Server
After configuring the DNS Master server, you'll start configuring the BIND Slave server on the server 'ns2.howtoforge.local' with the IP address '192.168.5.120'.
The basic configuration for 'named.conf' is similar to the BIND Master, and for the zone files, you can define the filename without creating an actual file on the BIND Slave server.
Before you start, ensure that you run the following commands on the BIND Slave server.
Now open the BIND configuration '/etc/named.conf' on the Slave server via the nano editor command below.
sudo nano /etc/named.conf
Change the default configuration with the following lines.
acl "trusted" {
192.168.5.100; # ns1 - or you can use localhost for ns1
192.168.5.120; # ns2
192.168.5.0/24; # trusted networks
};
options {
listen-on port 53 { 192.168.5.120; };
//listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
secroots-file "/var/named/data/named.secroots";
recursing-file "/var/named/data/named.recursing";
allow-query { any; };
recursion yes;
allow-recursion { trusted; };
allow-transfer { none; };
forwarders {
8.8.8.8;
1.1.1.1;
};
};
The settings are similar to the BIND Master server, and below are some differences in the configurations.
- The BIND service will be running on the IP address '192.168.5.120' on the Slave server.
- The recursion is enabled, but the 'allow-transfer' is configured to 'none'.
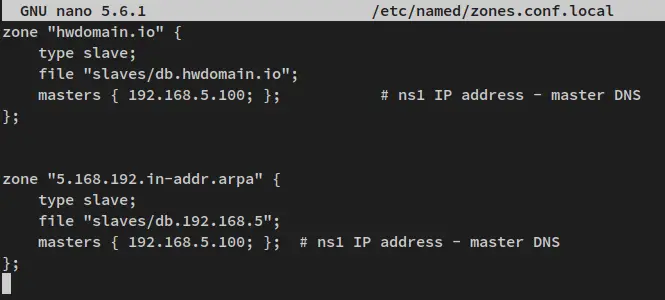
Now add the following line to the bottom of the 'named.conf' file for defining zones.
include "/etc/named/zones.conf.local";
Save the file and exit the editor when you're finished.
Next, create a new configuration '/etc/named/zones.conf.local' using the following nano editor command.
sudo nano /etc/named/zones.conf.local
Add the following lines to the file.
zone "howtoforge.local" {
type slave;
file "slaves/db.howtoforge.local";
masters { 192.168.5.100; }; # ns1 IP address - master DNS
};
zone "5.168.192.in-addr.arpa" {
type slave;
file "slaves/db.192.168.5";
masters { 192.168.5.100; }; # ns1 IP address - master DNS
};
Save and close the file when you are finished.
With this, you will define some configurations below on the BIND Slave server:
- Define two zones for the domain 'howtoforge.local' and its reverse DNS.
- Both zones type is 'slave'.
- The zone file for each will be taken from the '/var/named/slaves' directory, which is transferred from the BIND Master server.
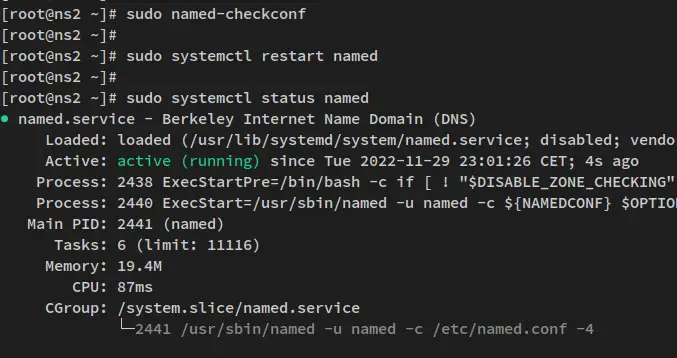
Next, run the following 'named-checkconf' command utility to verify BIND configurations. Then, restart the BIND 'named' service on the Slave server via the systemctl command as below.
sudo named-checkconf
sudo systemctl restart named
You will not have any error messages if you have a proper BIND configuration.
Lastly, run the following systemctl command to verify the BIND 'named' service on the Slave server to ensure that the service is running.
sudo systemctl status named
You'll now receive the output similar to the following - the BIND 'named' service is running on the BIND Slave server.
At this point, you have finished the BIND DNS installation with the Master-Slave architecture. You'll now be ready to start testing from the client machine.
Testing from Client
This example uses a Debian system as the client machine, so install some packages below via the APT before you start.
sudo apt install dnsutils bind9-utils
Input y when prompted for the confirmation and press ENTER to proceed.
Next, run the following command to remove the default link file "/etc/resolv.conf" and create a new file using the nano editor.
sudo unlink /etc/resolv.conf
sudo nano /etc/resolv.conf
Add the following configuration to the file. In the following configuration we are defining three different resolvers, the BIND DNS Master, the Secondary BIND DNS server, and the public Cloudflare DNS resolver. When the client machine requests information about the domain name, the information will be taken from the DNS resolver, from the top to the bottom.
nameserver 192.168.5.100
nameserver 192.168.5.120
nameserver 1.1.1.1
search howtoforge.local
Save and close the file when you are done.
Now you're ready to verify your DNS server from the client machine.
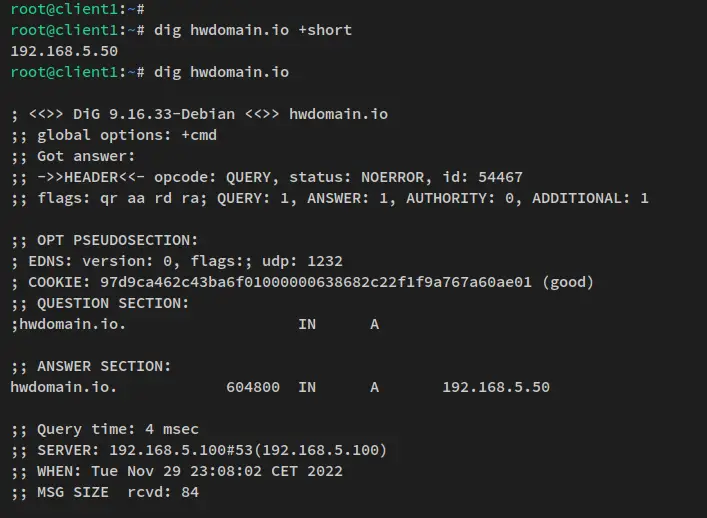
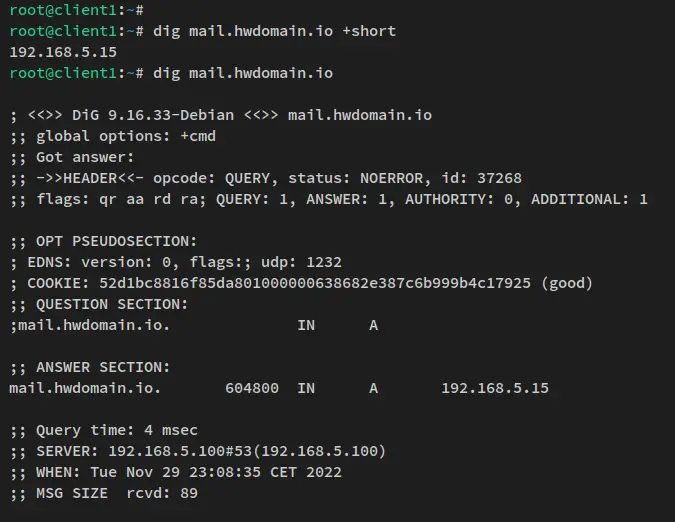
Run the dig command below to check the domain name "howtoforge.local" and "mail.howtoforge.local". And you should see the "howtoforge.local" is resolved to the server IP address "192.168.5.50", while the sub-domain "mail.howtoforge.local" is handled by the server IP address "192.168.5.15".
dig howtoforge.local +short
dig howtoforge.local
dig mail.howtoforge.local +short
dig mail.howtoforge.local
Verifying the domain name howtoforge.local.
verifying the sub-domain mail.howtoforge.local.
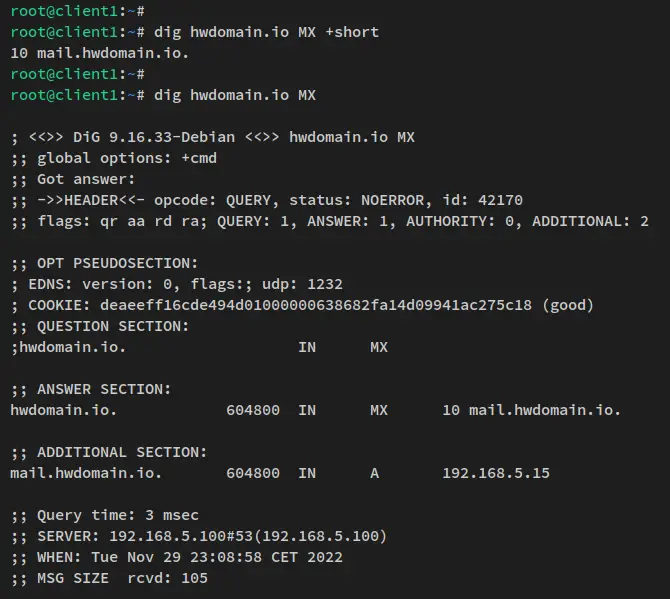
Next, run the dig command below to check the mail handler for the domain name "howtoforge.local". And you should get the output that the "mail.howtoforge.local" is handled mail for the main domain "howtoforge.local.
dig howtoforge.local MX +short
dig howtoforge.local MX
You can verify the reverse zone configuration for your domain name using the nslookup command.
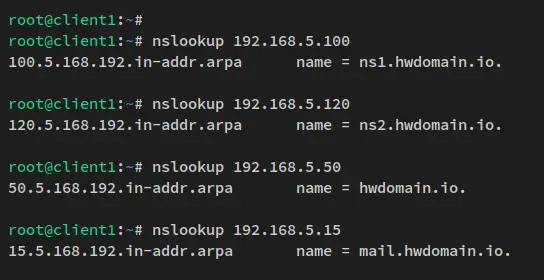
Run the nslookup command below to check and verify the reverse DNS for some IP addresses.
Now you should see that the IP address "192.168.5.100" is reversed to the name server "ns1.howtoforge.local", the IP address "192.168.5.120" is reversed to the name server "ns2.howtoforge.local", and the IP address "192.168.5.50" is reversed to the main domain name "howtoforge.local", and lastly the IP address "192.168.5.15" is reversed to the sub-domain "mail.hwdomain.io.
nslookup 192.168.5.100
nslookup 192.168.5.120
nslookup 192.168.5.50
nslookup 192.168.5.15
At this point, you've finished the BIND DNS Server installation with Master-Slave architecture on Rocky Linux. You've also learned how to test DNS Server via various command utilities such as dig and nslookup.
Conclusion
Congratulation! throughout this tutorial, you have learned the installation and configuration of BIND DNS Server on Rocky Linux 9 servers. You have successfully configured the Master-Slave BIND DNS Server using two different Rocky Linux servers. Also, you have learned the basic command of Dig and Nslookup for checking and verifying DNS records and configuration.