How to Set up Teleport Cluster on Rocky Linux 9
Teleport is an open-source that can be used as an access plane for your global infrastructure. It provides zero-trust access to a variety of services such as servers, Kubernetes clusters, database servers, DevOps applications like AWS Management Console, CI/CD, version control, and desktops. Teleport is the single source of truth for access, synchronized across your entire infrastructure.
Teleport can eliminate the need for VPNs by providing a single gateway to access your global computing infrastructure. It's an Identity-Native Access Proxy that allows you to access your infrastructure securely.
Teleport has been publicly audited by security companies such as Cure53 and Doyensec. Teleport is currently deployed and used in production by companies such as Samsung, NASDAQ, IBM, Epic Games, and many more.
In this tutorial, you will set up and secure an access plane for your infrastructure via Teleport on a Rocky Linux 9 server. You'll install Teleport, initialize Teleport Cluster, enable Teleport Web Service, add a Teleport user, and then add Nodes/Servers to the Teleport Cluster via different methods.
Once you've completed this tutorial, you will have a secure server infrastructure that can only be accessed via Teleport. Also, you can disable SSH access on your local nodes/servers.
Prerequisites
To complete this tutorial, you must have the following requirements:
- A Rocky Linux 9 server - This example uses a Rocky Linux with hostname 'teleport-rocky' and the server IP address '192.168.5.100'.
- A non-root user with sudo/root administrator privileges.
- A domain name pointed to your server IP address.
- Generate SSL Certificates - You can generate free SSL certificates via Certbot and Letsencrypt.
- An SELinux is running in permissive mode.
- Two Fact Authentication application - You can use KeepassXC with the 2FA plugin on a Desktop. You can use Aegis (Android users) or Google Authentication (iOS users) for phone users.
You'll also need additional servers/nodes to add to the Teleport Cluster. You can use any Linux distribution, but this example uses two additional Rocky Linux servers with hostname 'client1' and 'client2'.
Installing Teleport on Rocky Linux 9
Teleport is an application that provides a secure way to access your infrastructure. You can securely access Linux servers, Kubernetes Cluster, Database servers, applications, and Desktops via a gateway.
To set up Teleport as an access plane for your infrastructure, you will add the Teleport repository to your system, then install it. For RHEL-based distributions, you can install Teleport via the official Teleport repository.
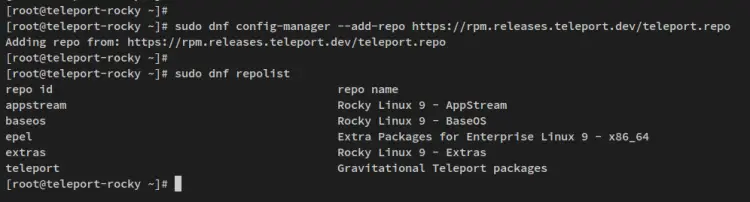
Run the below dnf command to add the Teleport repository to your Rocky Linux system. Then, verify the list of active repositories.
sudo dnf config-manager --add-repo https://rpm.releases.teleport.dev/teleport.repo
sudo dnf repolist
The Teleport repository should now be available on your system.
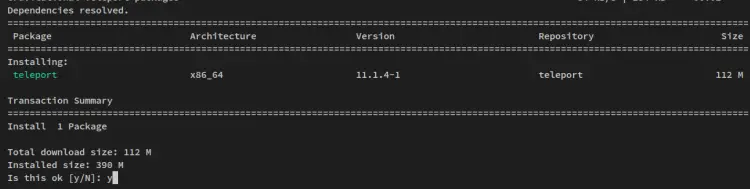
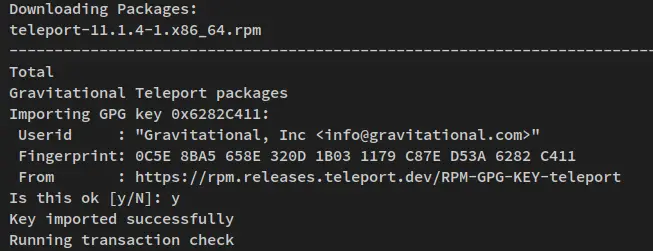
Install the Teleport package via the dnf command below. When prompted for confirmation, input y and press ENTER.
sudo dnf install teleport
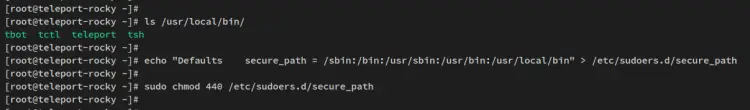
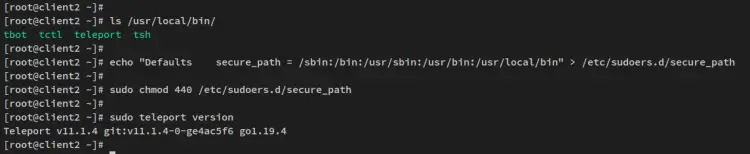
The Teleport package should be installed on the '/usr/local/bin' directory. Run the below command to verify the list of command lines by Teleport.
ls /usr/local/bin/
You should Teleport command lines such as teleport, tsh, and tctl.
Next, add the '/usr/local/bin' directory to the sudoers secure_path by using the below command. This allows you to run Teleport command lines with sudo at the beginning.
echo "Defaults secure_path = /sbin:/bin:/usr/sbin:/usr/bin:/usr/local/bin" > /etc/sudoers.d/secure_path
sudo chmod 440 /etc/sudoers.d/secure_path
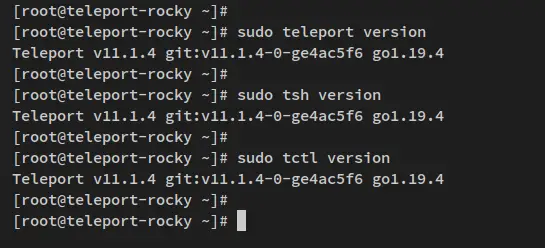
Lastly, verify the Teleport version via the below commands.
sudo teleport version
sudo tsh version
sudo tctl version
You should receive an output like the screenshot: You have now installed Teleport v11 on your Rocky Linux system.
With the Teleport is installed, you'll then initialize and configure the Teleport Cluster.
Configuring Teleport Server
To use Teleport, you must first configure the Teleport itself. But before that, you must ensure that your domain name is pointed to the server IP address and that you have generated SSL certificates. This example uses the domain name 'teleport.howtoforge.local' and SSL certificates from Letsencrypt that are available in the directory '/etc/letsencrypt/live/teleport.howtoforge.local'.
After the Teleport is installed, you'll now initialize the Teleport cluster and enable the Teleport web service that provides an administration dashboard for managing Teleport Cluster. Lastly, you'll start and enable the Teleport service.
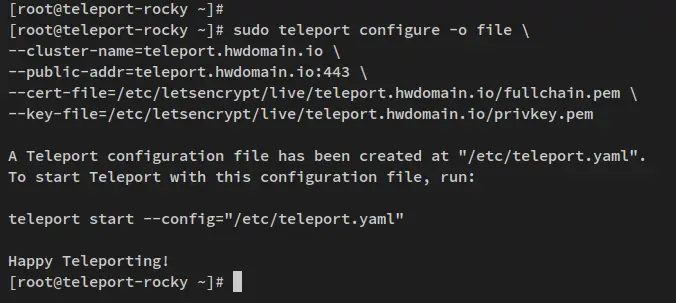
To begin, run the below teleport command to initialize the Teleport server configuration. Also, be sure to change the domain name, cluster name, and the path of both SSL certificates, public and private keys.
sudo teleport configure -o file \
--cluster-name=teleport.howtoforge.local \
--public-addr=teleport.howtoforge.local:443 \
--cert-file=/etc/letsencrypt/live/teleport.howtoforge.local/fullchain.pem \
--key-file=/etc/letsencrypt/live/teleport.howtoforge.local/privkey.pem
In your terminal screen, you should receive an output like this - The Teleport configuration file is generated at the '/etc/teleport.yaml' file.
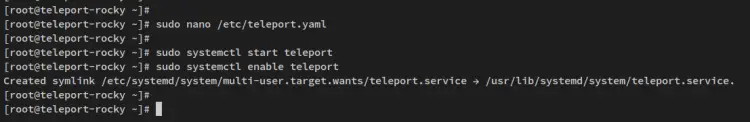
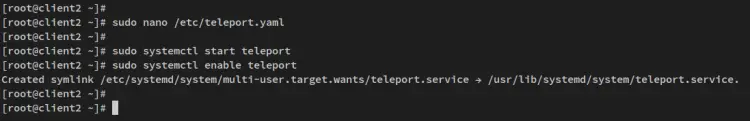
Next, open the Teleport config file '/etc/teleport.yaml' using the below nano editor command.
sudo nano /etc/teleport.yaml
Add the following lines to the file. With these lines, you'll enable the Teleport Web Service that will be running on the Teleport domain name 'teleport.howtoforge.local'.
app_service:
enabled: yes
apps:
- name: "teleport-webapp"
uri: "http://localhost:9000"
public_addr: "teleport.howtoforge.local"
Save and close the file when finished.
Now run the below systemctl command utility to start and enable the Teleport service on your system.
sudo systemctl start teleport
sudo systemctl enable teleport
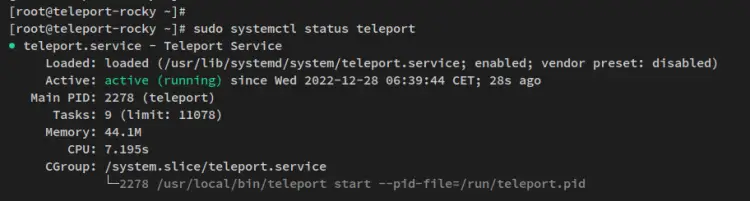
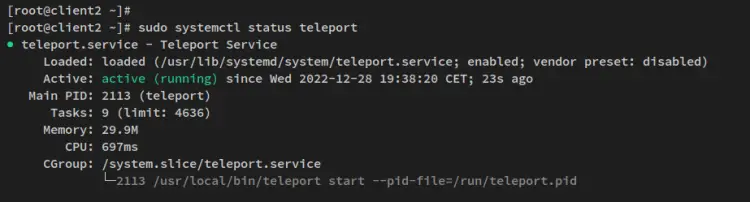
The Teleport service should be running and enabled, run the below command to verify and ensure that the Teleport service is running.
sudo systemctl status teleport
You'll receive an output similar to this - The Teleport service is running and it's enabled, which means the Teleport service will be run automatically upon the bootup.
With the Teleport service is running, you should now be able to access Teleport via your web browser. But before that, you must open some ports that will be used by the Teleport service. You can check the Teleport Network page for the list of details ports for the Teleport Cluster.
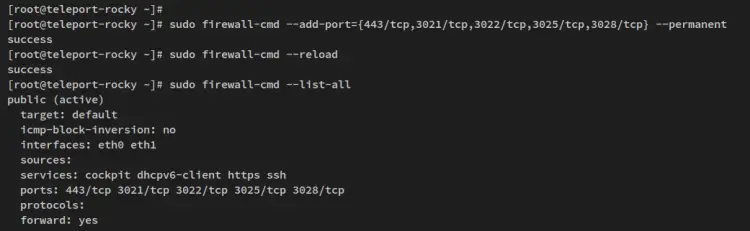
Run the below firewall-cmd command to add ports that will be used by Teleport.
sudo firewall-cmd --add-port={443/tcp,3021/tcp,3022/tcp,3025/tcp,3028/tcp} --permanent
Now reload the firewalld to apply the changes, then verify the list of firewalld rules.
sudo firewall-cmd --reload
sudo firewall-cmd --list-all
Now ensure that you've got a similar output to the following.
Lastly, open up your web browser and visit your Teleport domain name (i.e: https://teleport.howtoforge.local/). You should see the Teleport login page if your Teleport installation is successful.
In the next step, you'll create and set up a Teleport user that can be used for managing Teleport Cluster via the command line and the administration dashboard.
Adding Teleport User
At this point, you have the Teleport Cluster running with web service enabled on top of it. In this step, you'll create and set up the Teleport user that will be used for managing Teleport Cluster.
Before you start, ensure that the 2FA application is installed on your devices, you can use KeepassXC for desktop, Aegis for Android, or Google Authentication for iOS.
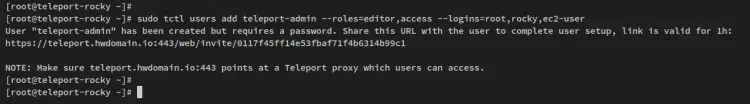
To begin, run the below command on the 'teleport-rocky' server to create a new Teleport user. This will create a new user 'teleport-admin' with roles editor and access. The flag '--logins' allows 'teleport-admin' to log in to any nodes via user root, rocky, or ec2-user. Users behind the '--login' flag must be created on target nodes.
sudo tctl users add teleport-admin --roles=editor,access --logins=root,rocky,ec2-user
You should receive an output like this - The Teleport user 'teleport-admin' is created and you should get the generated link that will be used to configure your new user.
Copy the generated link to your web browser and you should now get the welcome message for setting up a Teleport user. Click the GET STARTED button to set up the new Teleport user.
Input the username for your Teleport user, and input the password. Be sure that you're using a strong and easy-to-remember password. Click NEXT to continue.
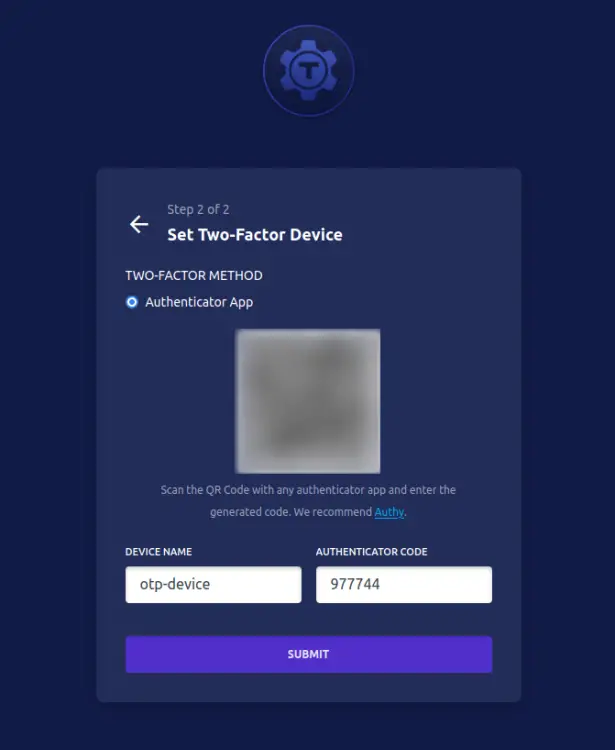
After configuring the username and password, you will now set up the two-factor authentication for your Teleport user.
Scan the QR code on the Teleport setup page and input the generated OTP code. Then click SUBMIT to confirm.
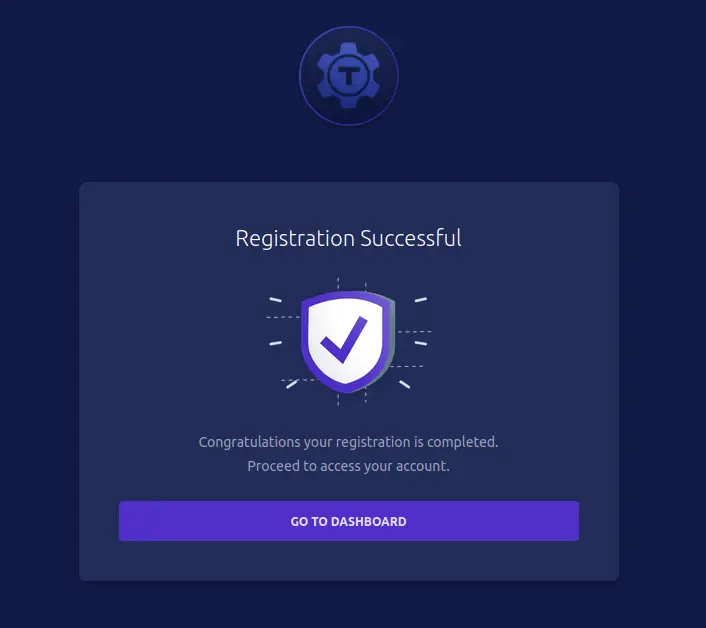
Now you should get the message 'Registration Successful' if your OTP code is correct. And you have now configured the password and 2FA for the new Teleport user.
Click GO TO DASHBOARD.
You should now get the web administration dashboard of your Teleport deployment, which is running securely with HTTPS enabled and the user is created with 2FA enabled.
Managing Teleport Cluster via Command Line
The Teleport package includes the command line ts and tctl that are available in the '/usr/local/bin' directory.
The tsh command allows users to authenticate and manage Teleport Cluster from the terminal. You can add, edit, or delete Teleport resources on the cluster. For security, you must run the tsh command as a non-root user.
The tctl command to set up and configure the Teleport Auth Service. This must be run with sudo or root privileges.
In this step, you'll access and manage Teleport Cluster via both command lines tsh and tctl.
First, log in to the non-root user via the below command. This example uses the user 'rocky'.
su - rocky
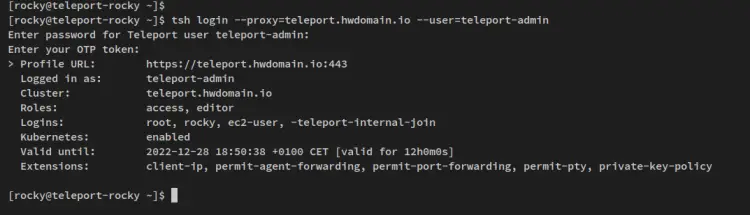
Now run the below tsh command to authenticate to your Teleport Cluster. This example will authenticate to the Teleport Cluster that runs on the domain name 'teleport.howtoforge.local' with the user 'teleport-admin'.
tsh login --proxy=teleport.howtoforge.local --user=teleport-admin
You'll be asked to input the password for the 'teleport-admin' user and input the OTP authentication code. Input the correct password for your user and the correct OTP code from your 2FA application.
When successful and authenticated, you should receive the detailed connections to the Teleport Cluster as the following.
You can also verify the current connection to the Teleport Cluster via the below tsh command. This will generate the same output as the screenshot on top.
tsh status
Now that you've authenticated to the Teleport Cluster via tsh, you can now manage resources in Teleport via terminal.
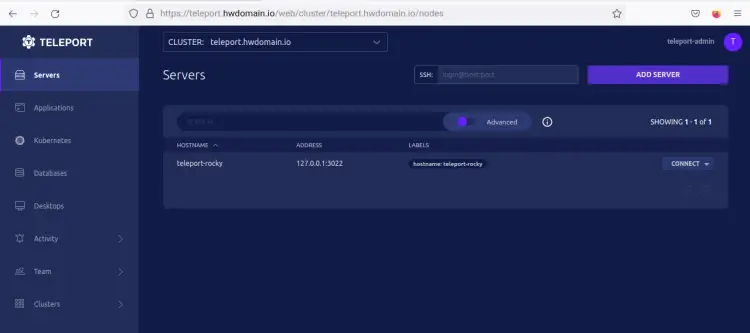
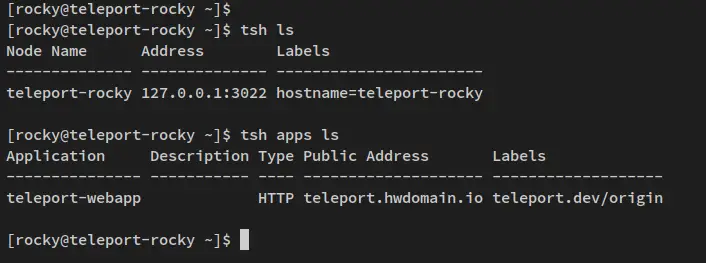
Run the below tsh command to check the list of hosts/nodes/servers that are available on the Teleport Cluster.
tsh ls
Now verify the enabled application on Teleport CLuster via the tsh command below.
tsh apps ls
In the output, you should see one node is available on the Teleport Cluster (teleport-rocky) and the application 'teleport-webapp' is enabled.
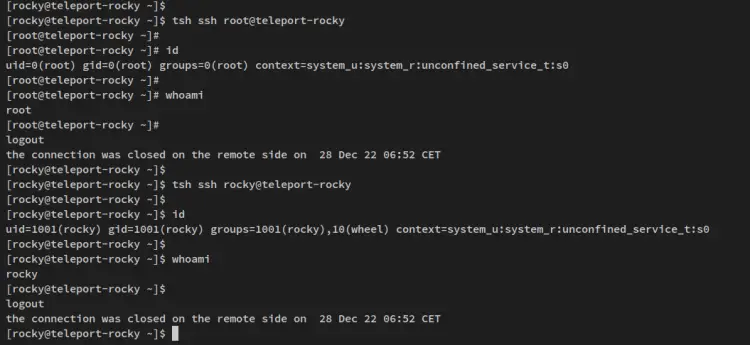
Next, you can also log in to nodes that are available on the Teleport Cluster via the tsh command as below. With this, you'll be logging into the 'teleport-rocky' via the tsh command with the user 'root' or/and 'rocky'.
tsh ssh root@teleport-rocky
tsh ssh rocky@teleport-rocky
You should see the output like the following - With both tsh commands you have successfully logged in to the 'teleport-rocky' via the tsh command.
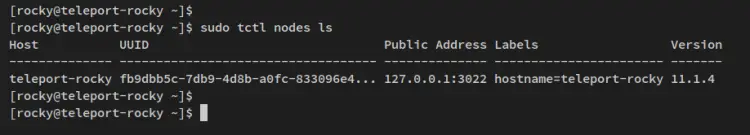
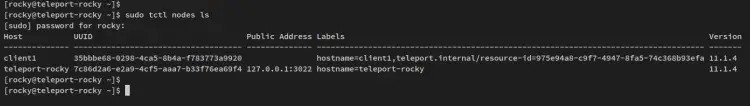
For the tctl command, you should run with sudo at the beginning. Run the below tctl command to check available nodes/servers on the Teleport Cluster.
sudo tctl nodes ls
In the next step, you'll learn how to add Nodes/Servers to the Teleport Cluster via two different methods, automatically via the web administration dashboard or manually via the command line.
Adding Nodes to Teleport Cluster
To add nodes/servers to the Teleport Cluster, you must ensure that the server is reachable. And you can use two different methods to add Nodes/Servers to your Teleport Cluster.
In this step, you'll add two different nodes to the Teleport Cluster. You'll add the node 'client1' via the installer script that will be generated from the web administration dashboard, and add the 'client2' node manually via the command line.
Adding Nodes via Teleport Administration Dashboard
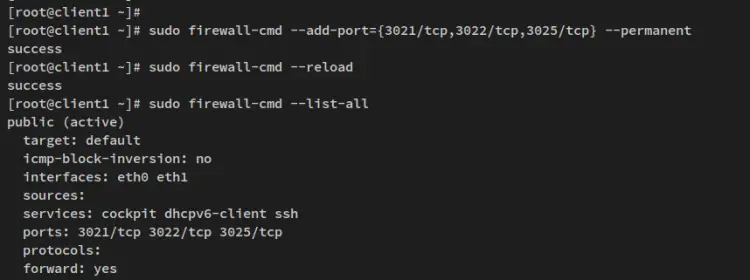
Before you start, run the firewall-cmd command below to open some ports on the 'client1' node.
sudo firewall-cmd --add-port={3021/tcp,3022/tcp,3025/tcp} --permanent
Now reload the firewalld to apply the changes and verify the status of firewalld rules on the 'client1' node.
sudo firewall-cmd --reload
sudo firewall-cmd --list-all
You'll then receive an output like this.
Next, access the Teleport web administration dashboard and click the ADD SERVER button.
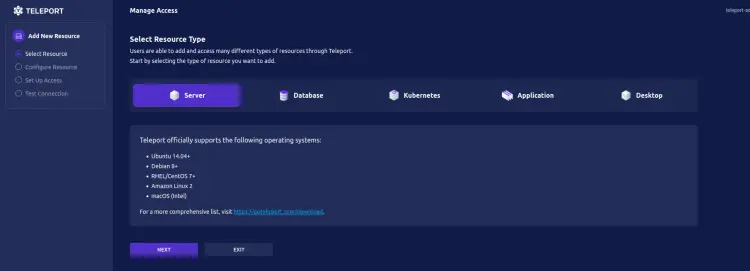
Select the resource type you want to add. You can add Kubernetes Cluster, Database servers, Applications, and Desktops. Select SERVERS to add resource type server and click NEXT.
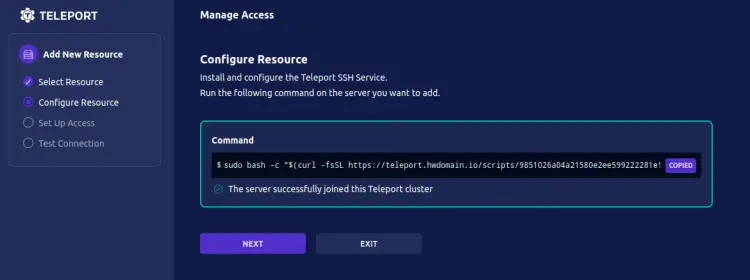
Now you'll see the generated installer script and command line that can be used to add the 'client1' node. Copy that generated command line.
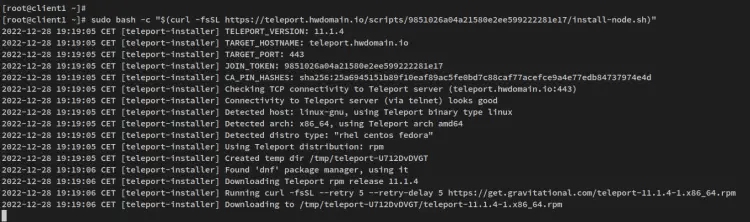
Now log in to the 'client1' node, access the root privileges via the sudo command, then paste and run the generated command line on the 'client1' node. This will download and run the generated script on the 'client1' node.
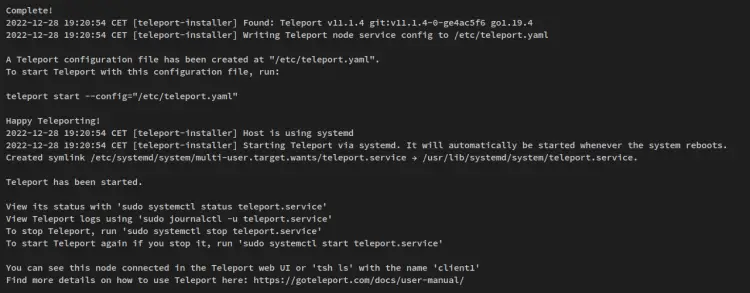
You'll receive a similar output like this on your terminal - The installer script will add the 'client1' node by using the generated token and the ca pin of the Teleport Cluster. Also, the installer script will detect your current operating system, install the Teleport package automatically, and generate the Teleport configuration '/etc/teleport.yaml' file.
After the process is finished, you should receive the output like this. The Teleport service on the 'client1' node also automatically started and enabled.
Now back to the Teleport web administration dashboard and you should see a message such as 'The server successfully joined this Teleport cluster'. Click NEXT to continue.
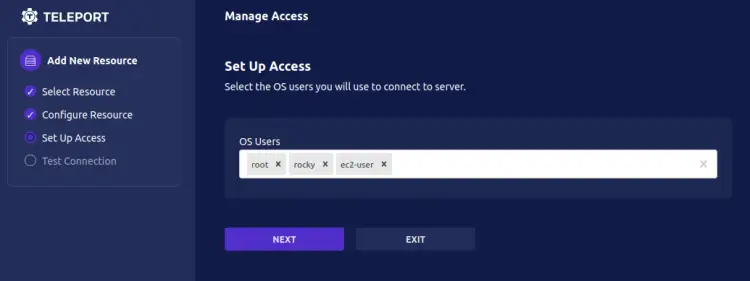
Now input the usernames that are allowed to access the 'client1' node. Ensure users are available and created on the 'client1' node. Click NEXT again to continue.
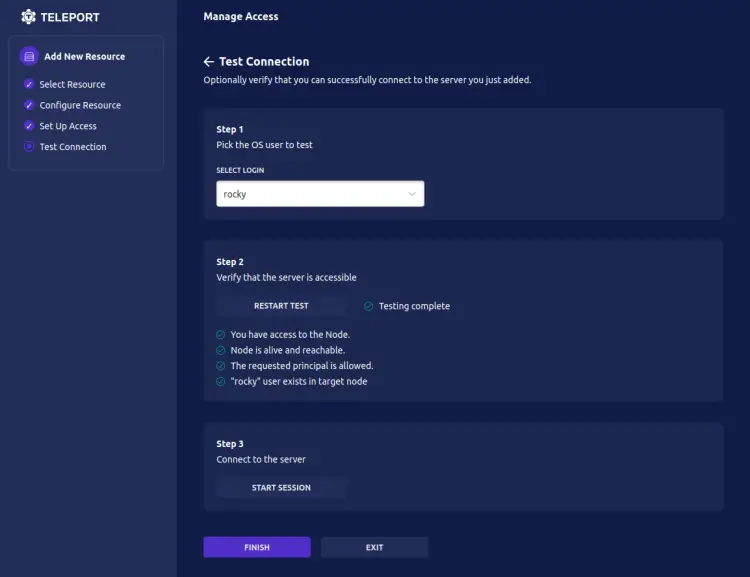
Lastly, you can verify the connections to the 'client1' node by using the steps available on the web administration dashboard.
- First, select the user that you want to use to log in.
- Secondly, click the TEST SERVER button on 'Step 2' and ensure all tests are checked/marked as complete.
- Lastly, click the START SESSION button that will automatically open a new tab on your web browser and access the 'client1' node via the selected user.
Below is the screenshot of the 'Test Connection' section with the status successful.
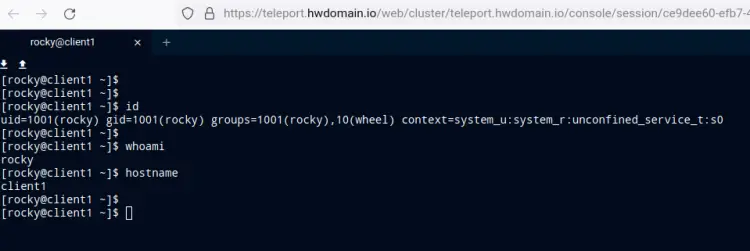
Below is the screenshot after logging in to the 'client1' node via the START SESSION in Step 3.
Click FINISH to complete the processes.
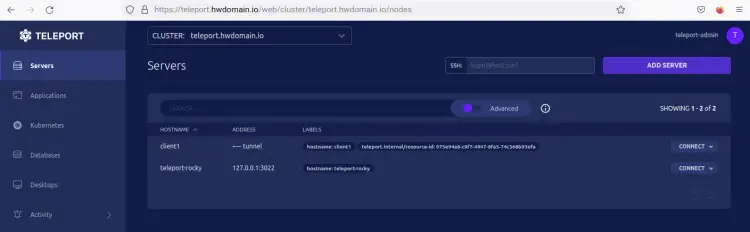
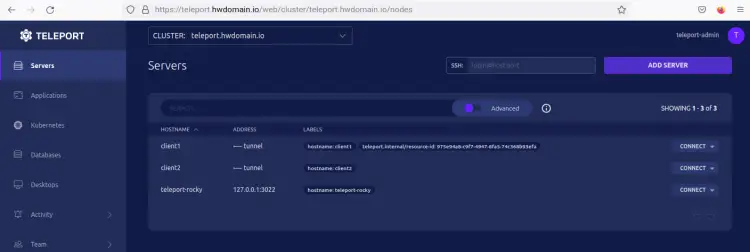
You'll then be redirected to the Teleport web administration dashboard and you should see that the 'client1' node is added to the Teleport Cluster.
Additionally, you can also verify the list of nodes/servers on the Teleport Cluster via the tsh and tctl command lines.
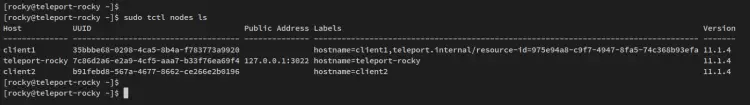
Back to the 'teleport-rocky' and run the below command to verify the list of nodes/servers on the Teleport Cluster.
sudo tctl nodes ls
You should receive the output similar to this - The client1 node is available and added to the Teleport Cluster.
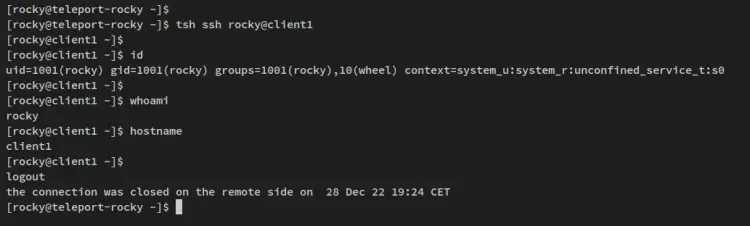
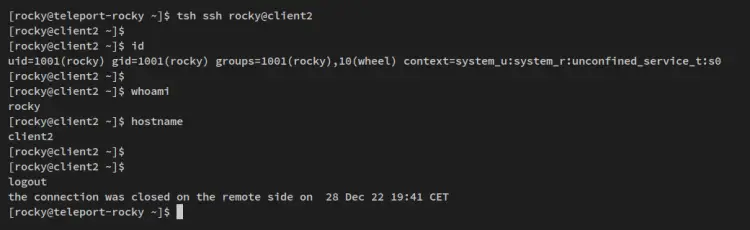
Lastly, run the below tsh command to log in to the client1 node as the user 'rocky'. You should now be logged in to the 'client1' node via Teleport.
tsh ssh rocky@client1
Below is the terminal screen after logging into the client1 node via Teleport.
With this in mind, you have now successfully added the 'client1' node/server to the Teleport Cluster automatically via the installer script generated from the Teleport web administration dashboard.
Adding Nodes Manually
Now you'll add the 'client2' node manually to the Teleport Cluster via the following steps:
- Checking the CA pin of the Teleport Cluster
- Generate Teleport token
- Setting up firewalld on cleint2 node
- Installing and configuring Teleport on the client2 node
Llet's get started.
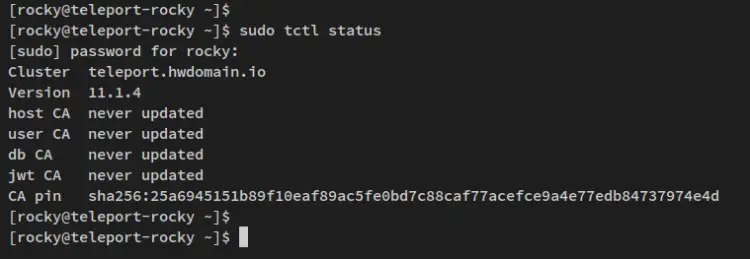
Run the below command to check the 'CA pin' fingerprint of your Teleport Cluster. The 'CA pin' fingerprint will be used to add the 'client2 node.
sudo tctl status
Below is a similar output you should receive - Be sure to copy the 'CA pin' fingerprint.
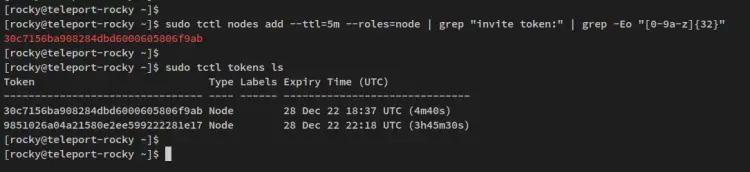
Next, run the below tctl command to generate a new token that will be used by the client2 node to join the Teleport Cluster. Then, verify the list of tokens on your Teleport Cluster.
sudo tctl nodes add --ttl=30m --roles=node | grep "invite token:" | grep -Eo "[0-9a-z]{32}"
sudo tctl token ls
You should receive a similar output to this - Be sure to copy the generated token that will be used by the client2 node to join the Teleport Cluster.
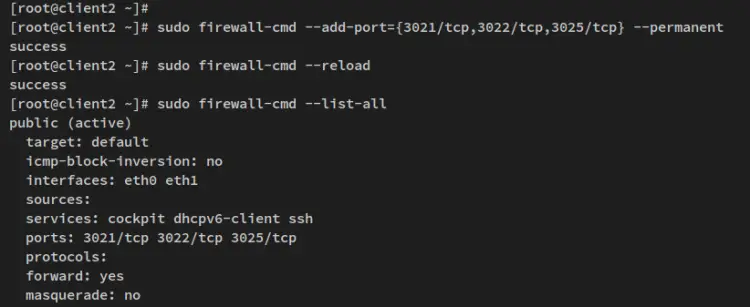
Next, connect to the 'client2' node and run the below command to open ports.
sudo firewall-cmd --add-port={3021/tcp,3022/tcp,3025/tcp} --permanent
Reload the firewalld and verify the list of ports via the below command.
sudo firewall-cmd --reload
sudo firewall-cmd --list-all
Below is the list of ports that should be opened on the client2 node.
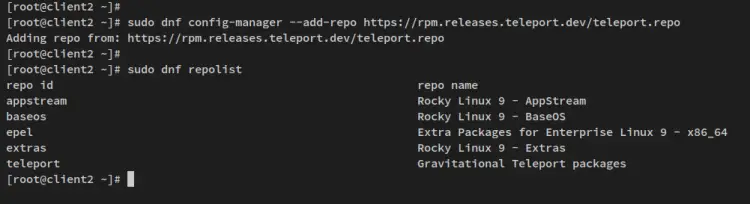
Now run the below command to add the Teleport repository to the client2 node.
sudo dnf config-manager --add-repo https://rpm.releases.teleport.dev/teleport.repo
sudo dnf repolist
Below is a similar output after verifying the list of repositories on the client2 node.
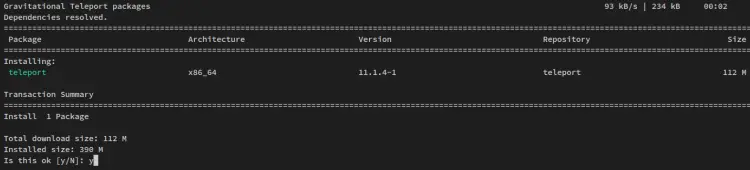
Run the below dnf command to install Teleport on the client2 node. Input y when prompted and press ENTER to proceed.
sudo dnf install teleport
You'll also be prompted to accept the GPG key of the Teleport repository. Input y and press ENTER to confirm.
Teleport should now be installed on the '/usr/local/bin' directory. Run the below command to verify the list of Teleport binary packages.
ls /usr/local/bin/
Now run the below command to add the '/usr/local/bin' directory to the sudoers secure_path. This allows you to run Teleport command lines with sudo or root privileges.
echo "Defaults secure_path = /sbin:/bin:/usr/sbin:/usr/bin:/usr/local/bin" > /etc/sudoers.d/secure_path
sudo chmod 440 /etc/sudoers.d/secure_path
You can verify the Teleport version on the client2 node via the below command. You should see that Teleport v11 is installed.
sudo teleport version
Next, create a new Teleport configuration file '/etc/teleport.yaml' using the below nano editor command.
sudo nano /etc/teleport.yaml
Add the following lines to the file. Be sure to change the namenode with the node hostname, the token_name with your generated token, the proxy_server with the domain name of your Teleport Cluster, and the ca_pin with the Teleport Cluster CA pin fingerprint.
version: v3
teleport:
nodename: client2
data_dir: /var/lib/teleport
join_params:
token_name: 30c7156ba908284dbd6000605806f9ab
method: token
proxy_server: teleport.howtoforge.local:443
log:
output: stderr
severity: INFO
format:
output: text
ca_pin: sha256:25a6945151b89f10eaf89ac5fe0bd7c88caf77acefce9a4e77edb84737974e4d
diag_addr: ""
auth_service:
enabled: "no"
ssh_service:
enabled: "yes"
commands:
- name: hostname
command: [hostname]
period: 1m0s
proxy_service:
enabled: "no"
https_keypairs: []
acme: {}
Save the file and exit the editor when finished.
Next, run the below systemctl command utility to start and enable the Teleport service on the client2 node.
sudo systemctl start teleport
sudo systemctl enable teleport
Then verify the Teleport service via the below command.
sudo systemctl status teleport
You should receive the output similar to the following screenshot - The Teleport service on the client2 node is configured and it's running and enabled.
Now back to the 'teleport-rocky' terminal to verify the list of available nodes/servers from there. Run the below command to check the list of nodes on the Teleport Cluster
sudo tctl nodes ls
You should see the client2 node is available and added to the Teleport Cluster.
Next, run the below tsh command to access the client2 node via Teleport SSH. You should now be logged in to the client2 node via Teleport. Ensure that the 'rocky' user is available on the client2 node.
tsh ssh rocky@client2
Below is the output you should get after logging in to the client2 node via Teleport.
Now back to the Teleport web administration dashboard and you should see that the client2 node is available on the Teleport Cluster.
Lastly, click the 'CONNECT' button on the 'client2' node to start and connect to the 'client2'. You should now be logged in to the 'client2' node via the Teleport web administration dashboard.
With this in mind, you've now successfully added and configured the client2 node manually by generating a Teleport token, using the CA pin fingerprint of the Teleport Cluster, installing the Teleport package, and creating a Teleport configuration file.
Conclusion
Your server infrastructure is now secured via Teleport Cluster, and You can now disable SSH services on every node and allow only access from the Teleport Server. You have now learned how to install Teleport Cluster on a Rocky Linux 9 server and learned the basic configuration to set up Teleport.
You have also learned how to set up Teleport users with Two Factor Authentication enabled and learned how to use Teleport command lines (TSH and tctl) for managing Teleport Cluster.
Lastly, you've successfully configured and added two nodes client1 and client2 to the Teleport Cluster using two different methods. The first method is via the installer script generated by the Teleport web administration dashboard. The second method is manually adding nodes/servers by installing and configuring Teleport on the target machine.