How to Install and Configure Fail2ban on Ubuntu 22.04
Fail2ban is free and open-source IPS (Intrusion Prevention Software) that helps administrators secure Linux servers against malicious login and brute-force attacks. Fail2ban is written in Python and comes with filters for various services such as Apache2, SSH, FTP, etc. Fail2ban reduces malicious login attempts by blocking the IP addresses of the source attacks.
Fail2ban works by scanning log files of services (e.f /var/log/auth.log) and banning IP addresses that show malicious login attempts such as too many incorrect passwords, seeking exploits, etc. Fail2ban also supports multiple firewall backend such as iptables, ufw, and firewalld. Also allows you to set up an email notification for every blocked login attempt.
In this tutorial, we will show you how to install and configure Fail2ban for securing the Ubuntu 22.04 server. This guide also covers the basic command of fail2ban-client for managing Fail2ban service and jails.
Prerequisites
- An Ubuntu server 22.04
- A non-root user with sudo privileges.
Setup UFW Firewall
Before you start installing Fail2ban, you will need to set up the Firewall on your Ubuntu server.
The default Ubuntu server installation comes with the UFW Firewall, which is easier to manage than another firewall like iptables.
Now check the UFW firewall status using the following command.
sudo ufw status
If you get the output message such as "Status: inactive", then your UFW firewall is not yet started. But if you get the output message such as "Command ufw not found", then the UFW firewall is not installed on your server.
To install the UFW firewall package, run the apt command below.
sudo apt install ufw -y
After UFW installation is completed, run the below command to add the SSH service to the UFW firewall.
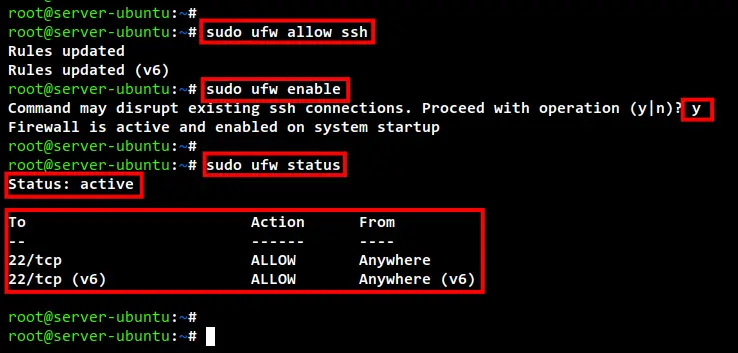
sudo ufw allow ssh
Next, run the below command to start and enable the UFW firewall.
sudo ufw enable
Input y to confirm and start the UFW firewall.
Lastly, check again the UFW firewall using the following command.
sudo ufw status
Below you can see the UFW firewall "Status: active" with the SSH port 22 added to the firewall rules.
Installing Fail2ban on Ubuntu 22.04
After you have installed and configured the UFW firewall, now you will be installing the Fail2ban package to your server.
Run the following command to update and refresh your Ubuntu repository.
sudo apt update
Now install the Fail2ban package using the below command.
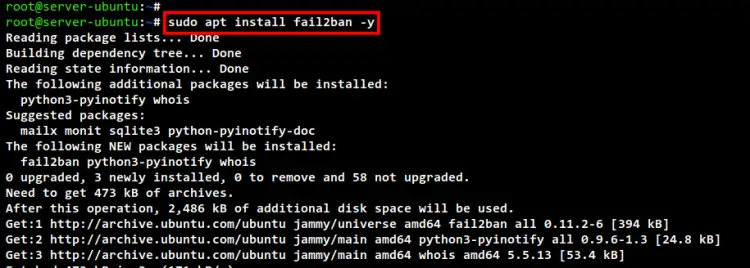
sudo apt install fail2ban -y
The installation will begin.
After the Fail2ban installation is completed, enable the Fail2ban service and start the service using the command below.
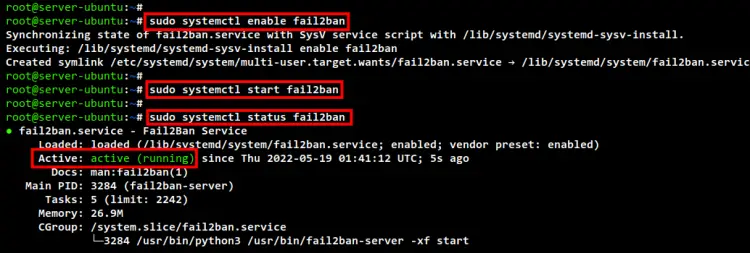
sudo systemctl enable fail2ban
sudo systemctl start fail2ban
Lastly, check the Fail2ban service status using the following command.
sudo systemctl status fail2ban
In the below screenshot, you will see the Fail2ban service is running on the Ubuntu 22.04 server.
Configuring Fail2ban
After you have installed the Fail2ban, now it's time to set up and configure the Fail2ban.
All Fail2ban configuration is stored at the /etc/fail2ban directory. Below detailed Fail2ban configuration you must know:
- The configuration fail2ban.conf is the main configuration of Fail2ban.
- The configuration jail.conf is an example of the Fail2ban jail configuration.
- The directory action.d contains fail2ban actions settings such as mail settings and firewall settings.
- The directory jail.d contains additional configuration for fail2ban jail.
To start configuring Fail2ban, you will need to copy the default jail configuration jail.conf to jail.local using the following command.
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Now edit the configuration jail.local using nano editor.
sudo nano /etc/fail2ban/jail.local
First, uncomment the ignoreip option and add your IP address. All IP addresses inside the ignoreip option will not be blocked by Fail2ban.
ignoreip = 127.0.0.1/8 ::1 192.168.1.0/24 192.168.10.20
For the ban settings, you can change the configuration as you need. In this example, the global bantime will be 1day, the findtime will be 10minutes, and the maxretry is up to 5times.
The bantime option is the time of IP address will be banned to access the server. The findtime option is the duration between the number of failures before the ban action. And the maxretry option is the number of failures for IP addresses to get banned.
bantime = 1d
findtime = 10m
maxretry = 5
The default action for Fail2ban is only to ban the IP address. But also you can set up mail notification whenever an IP address gets banned.
Change the action option as below and change the default sender and destination mail address.
action = %(action_mw)s
destemail = [email protected]
sender = [email protected]
Next, for the UFW firewall integration, you need to change the banaction option to ufw as below.
banaction = ufw
Lastly, for the jails configuration. This section is where you add your service and secure it using fail2ban.
In this example, we will enable the jail for SSH service, but also we override the global default configuration for the sshd jail. The bantime will be 1week with maxretry of failures 3times and the findtime in 10minutes.
[sshd]
enabled = true
maxretry = 3
findtime = 1d
bantime = 1w
port = ssh
logpath = %(sshd_log)s
backend = %(sshd_backend)s
Save and close the file when you are done.
Now run the following command to restart the Fail2ban service and apply new changes to the jail.local configuration.
sudo systemctl restart fail2ban
You have now completed the Fail2ban configuration with email notification enabled and the sshd jail enabled for securing SSH service.
Using Fail2ban-client to Verify Fail2ban Status
The fail2ban provides a command-line fail2ban-client for interacting with the Fail2ban service. This allows you to manage and configure the Fail2ban from the command line, and also allows you to manage Fail2ban jails.
To verify fail2ban installation and configuration, run the fail2ban-client below command.
sudo fail2ban-client ping
If you get the output message such as "Server replied: pong", this means the Fail2ban is running without an error.
Next, run the fail2ban-client command below to check the status of sshd jail.
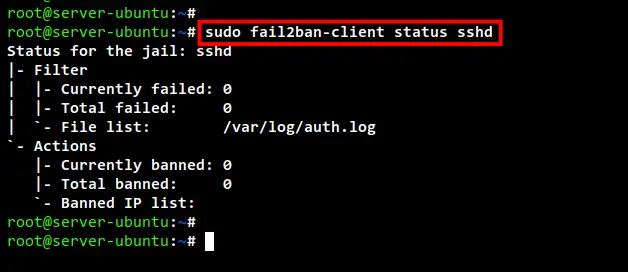
sudo fail2ban-client status sshd
Below you can see the detailed status of sshd jail. This includes the log file for the SSH service and the list of banned IP addresses on the sshd jail.
Now if you want to get a detailed configuration of the sshd jail, you can use the fail2ban-client command as below.
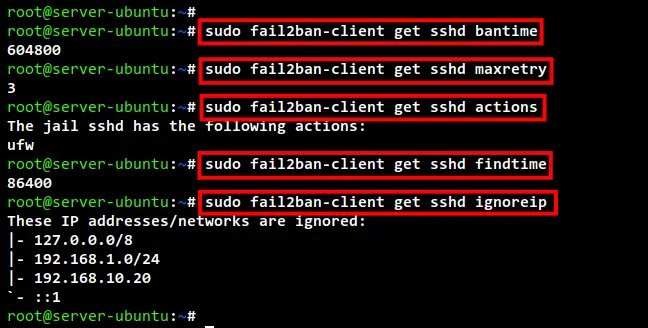
Check the bantime configuration for sshd jail. You will get the output of the bantime here in seconds.
sudo fail2ban-client get sshd bantime
Check the maxrtey configuration for the sshd jail. You will see the maxretry here is 3 because it is overridden from the global configuration, which is maxrety 5times.
sudo fail2ban-client get sshd maxretry
For the banaction in sshd jail, you can use the following command. And you should get the output of ufw as the default banaction for sshd jail.
sudo fail2ban-client get sshd actions
For the findtime here, you will also see the override value fr the sshd jail. The output here also will be in seconds format.
sudo fail2ban-client get sshd findtime
Lastly, you can also check the default ignoreip for sshd jail using the below command. And you will see the ignoreip has the same value as the global Fail2ban configuration.
sudo fail2ban-client get sshd ignoreip
Ban and Unban IP using Fail2ban-client
Another important thing about Fail2ban here is how to ban and unban IP addresses on Fail2ban. To do that, you can also use the fail2ban-client command.
To ban IP address manually on the sshd jail, you can use the fail2ban-client command below. Change the IP address with the IP address you want to ban.
sudo fail2ban-client set sshd banip IP-ADDRESS
To unban the IP address from sshd jail, you can use the fail2ban-client command below. Just be sure to change the IP address with the IP address you want to unban.
sudo fail2ban-client set sshd unbanip IP-ADDRESS
Now after you ban an IP address manually or unban an IP address, you can verify using the fail2ban-client command below.
sudo fail2ban-client status sshd
If you ban an IP address manually, make sure the IP address is available on the list of banned IP addresses. But if you unban an IP address, make sure the IP address disappears from the list of banned IP addresses.
Conclusion
Congratulation! You have now successfully installed and configured Fail2ban for securing Ubuntu 22.04. You have also learned how to enable the UFW firewall, and how to integrate Fail2ban with the UFW firewall. Lastly, you have also learned how to manage Fail2ban using the fail2ban-client command, which includes how to ban and unban IP addresses from Fail2ban.