Articles by Ali Imran Nagori
-
How to upload local files to Amazon EC2 instance using Terraform
Author: Ali Imran Nagori • Tags: cloud, linux • Comments: 0In this tutorial, we will look at how to copy a file from a local machine running Terraform to a newly created Amazon EC2 instance (Ubuntu) on AWS. In this method, we will use the File utility provided by Terraform. We demonstrate its use by simply copying a file to an EC2 instance.
-
How to configure Apache virtual hosts on Ubuntu using Terraform
Author: Ali Imran Nagori • Tags: linux, ubuntu, web server • Comments: 1For hosting multiple websites, administrators commonly rely on ‘Virtual Hosting’ technique. In this tutorial, we will see how we can host two virtual hosts on an Ubuntu 22.04 system using Terraform. We will use the Apache web server to perform this lab.
-
How to Configure Apache Virtual Hosts on Ubuntu 22.04
Author: Ali Imran Nagori • Tags: apache, linux, ubuntu • Comments: 5The virtual hosting concept is used by companies to host multiple websites using a single machine. In this tutorial, we will see how we can host two virtual hosts on an Ubuntu 22.04 system using name-based virtual hosting. We will use the Apache web server.
-
-
Enabling Enhanced Monitoring for Amazon RDS
Author: Ali Imran Nagori • Tags: linux • Comments: 0Amazon RDS provides an enhanced monitoring feature for databases. In this tutorial, you will learn how to use the ‘IAM Passrole’ permission for enabling enhanced monitoring for Amazon RDS. We will see this by demonstrating a simple example.
-
What is the PassRole permission in AWS and how to use it
Author: Ali Imran Nagori • Tags: linux • Comments: 1An IAM service is provided by many cloud service providers as a measure to control access to cloud resources. In this tutorial you will learn how to use the ‘IAM Passrole’ permission. We will also demonstrate a simple example on how to connect an EC2 instance with a private S3 bucket using this concept.
-
How to use modules from the Terraform Registry
Author: Ali Imran Nagori • Tags: cloud, linux, virtualization • Comments: 0The Terraform Registry is a place where one can find different providers and modules (re-usable Terraform configurations) and use them with Terraform. In this tutorial, we will see how to use modules from Terraform Registry. We will see this by demonstrating an example of creating an EC2 instance on AWS.
-
How to use loops in Terraform
Author: Ali Imran Nagori • Tags: cloud, linux, server, virtualization • Comments: 0Terraform is an Open source tool developed and maintained by HashiCorp. It uses its own Hashicorp Configuration Language- HCL to provision multiple cloud service providers. In this tutorial, I will show you how to use loops in Terraform. We will see several examples of using some loop constructs.
-
How to launch EC2 instance using new AWS UI console
Author: Ali Imran Nagori • Tags: cloud • Comments: 0On January 12, 2022 AWS introduced a new user interface for the management console. In this post we will discover the new AWS Console Home and specifically we will use the new EC2 launch wizard to provision a new EC2 instance.
-
How to create an S3 bucket using new AWS UI console
Author: Ali Imran Nagori • Tags: • Comments: 0In this post we will discover the new AWS Console Home and specifically we will use the new S3 wizard to create a new S3 bucket. Let's begin the tour of the new AWS Console Home.
-
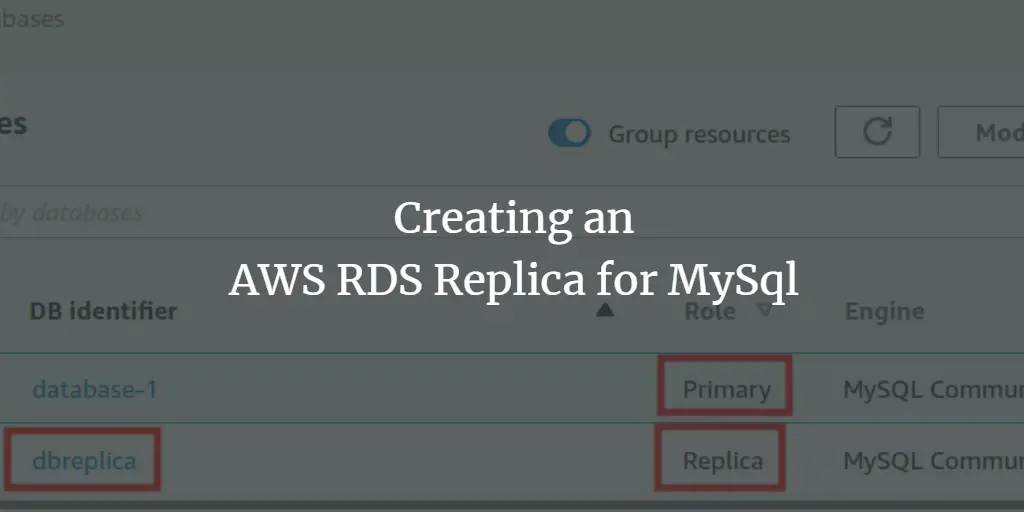
Creating an AWS RDS Replica for MySql
Author: Ali Imran Nagori • Tags: cloud, mysql • Comments: 0Amazon RDS is an easy-to-set up AWS-managed database service. In this guide, we will see how to create a read replica of a MySql RDS database instance.