What is the PassRole permission in AWS and how to use it
An IAM service is provided by many cloud service providers as a measure to control access to cloud resources. It determines who is authenticated and authorized to access these resources. AWS IAM identities consist of users, groups, and roles.
In this guide we will specifically focus on IAM roles. This IAM identity is just like an IAM user in the sense that we can attach IAM policies to it. These policies determine the scope of permission level for this identity. Unlike an IAM user which is associated with a single user and has long term credentials, roles follow a different strategy. They have temporary security credentials and are assumed/taken by others who need them. Normal users, applications, or services which do not have access permission to your AWS resources, assumes the roles to get this access.
What will we see here?
In this tutorial you will learn how to use the ‘IAM Passrole’ permission. We will also demonstrate a simple example on how to connect an EC2 instance with a private S3 bucket using this concept.
What is Passrole permission?
While configuring many AWS services, the user/administrator is required to pass a role to that service. The service then assumes that role to perform the actions that are allowed within that role. In most cases, the role is passed to the service only at one time while setting up the service and not everytime the role is assumed by the service.
A user must have rights to pass a role to a service. This is a strong security aspect as only authorized users are allowed to pass a role to service. Moreover, the administrators can control what type of role a user can pass to service.
Demonstration of Passrole permission
Let us move on this concept by taking a practical example. In this demonstration, we have a S3 bucket, an EC2 instance and an application running on this instance which is AWS CLI itself. We want to configure a role that will allow our application running on the EC2 instance to access our S3 bucket. We need to create the role in such a way that only the EC2 gets the permission to access S3 but not any other AWS service of the user. For this, our application should have temporary credentials for authentication and authorization to access S3. You would have noticed that while launching the EC2 instance, we are asked to select an IAM role, it is this role which provides these temporary credentials to our EC2 instance. Our application running on the EC2 instance will retrieve these credentials to access the S3 bucket.
An IAM user can pass a role to the EC2 service, at the time of launching the instance, using the below three entities:
- First we need to create and attach a policy to our role that will decide the permission boundary or scope of our IAM role.
- Next, a trust policy associated with this role that will basically allow the AWS service (EC2 in our case) to take/assume the role and utilize the permissions listed with the role.
- Finally, an IAM permission policy, attached with the IAM user that allows it to pass the roles which it is authorized to pass.
Creating the Role
In this section we will create a role called as ‘EC2S3Access’ and attach a ‘AmazonS3ReadOnlyAccess’ policy to it:
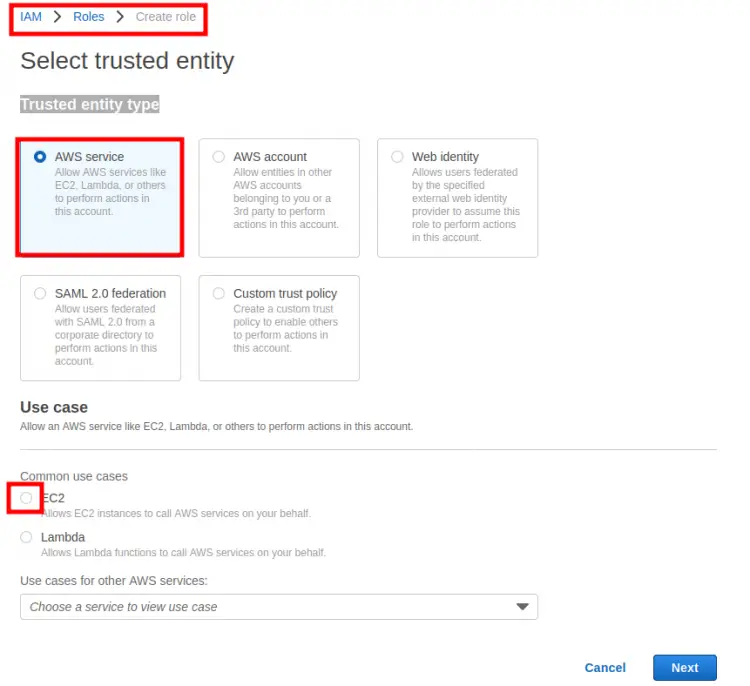
Step 1. Head to the IAM dashboard from the administrator or root account and select ‘Roles’ under the Access management option. Click on the ‘Create Role’ button.
Step 2. In the ‘Select trusted entity’ section, you'll see the ‘Trusted entity type’ and ‘Use case’ option. For the former, select ‘AWS service’ option and for the latter do select ‘EC2’ option.
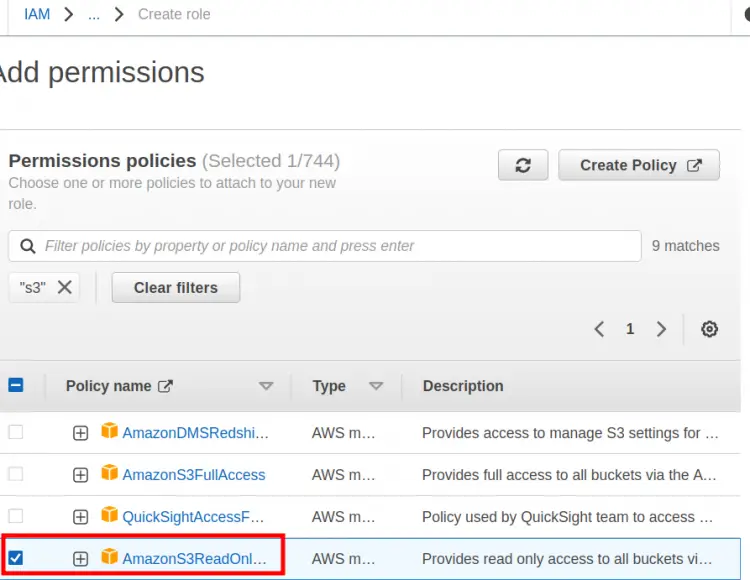
Step 3. In the next section ‘Add permissions’, we will attach a ‘S3ReadOnlyAccess’ policy and then click ‘Next’:
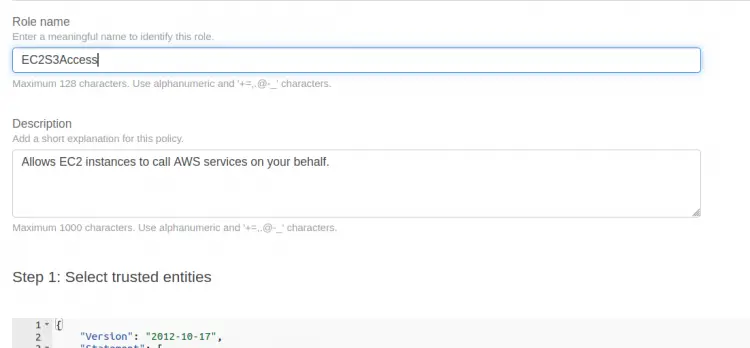
Step 4. Here enter a name for the role:‘EC2S3Access’ and an optional description for it. Note that a trust policy will be automatically attached with this role:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"sts:AssumeRole"
],
"Principal": {
"Service": [
"ec2.amazonaws.com"
]
}
}
]
}
Step 5. Finally, click the ‘Create role’ button to create the above role:
Adding IAM policy for the IAM user
So far we have created a role and attached a policy to it and then we have also got a trusted policy. Now we will create a policy for the IAM user itself. In this policy we will give the user permission for full EC2 access and also for associating the above ‘EC2S3Access’ role with our EC2 instance.
Step 1. Again head to the IAM dashboard from the administrator or root account and select ‘Policies’ and click on ‘Create policy’ button.
Step 2. On the Create policy wizard, click on the json tab and simply paste the following json code for this policy:
{
"Version": "2012-10-17",
"Statement": [{
"Effect":"Allow",
"Action":["ec2:*"],
"Resource":"*"
},
{
"Effect":"Allow",
"Action":"iam:PassRole",
"Resource":"arn:aws:iam::account_ID:role/EC2S3Access"
}]
}
In this code, replace ‘account_ID’ with the account number or ID of the user and ‘EC2S3Access’ with the name of the role in your case. Click ‘Next: Tags’.
Step 3. Specify any optional ‘Tags’ you want to use and click ‘Next: Review’:
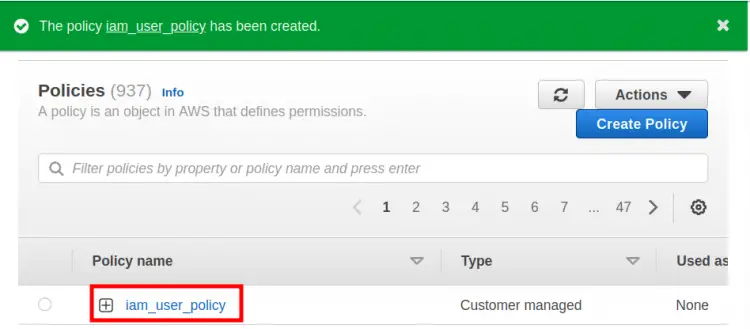
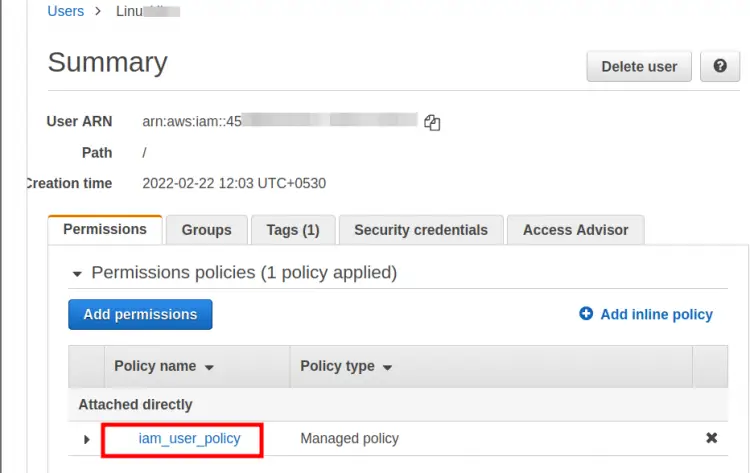
Step 4. Here put a name for this policy(‘iam_user_policy’ in our case) and finally, click ‘Create policy’ button to create this policy:
Step 5. Attach the above-created policy to the IAM user:
Attaching the role to the instance
As our role is ready and the IAM user is attached with the required policy, this is the time to attach this role(‘EC2S3Access’) to the EC2 instance.
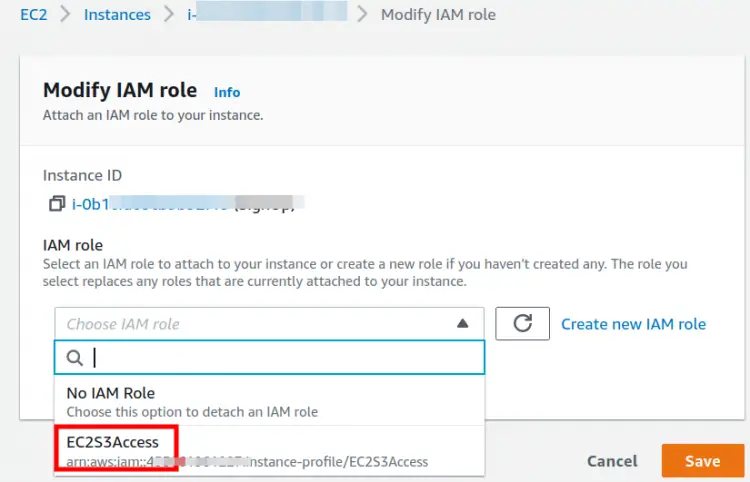
Note: A role can be attached to an instance while launching it and also to a running instance.
In our case the EC2 instance is already running, so navigate to the EC2 console and select the target instance. Select ‘Action > Security > Modify IAM role’. Select the ‘EC2S3Access’ option from the drop down menu on new page and click ‘Save’ to continue:
Testing the Setup
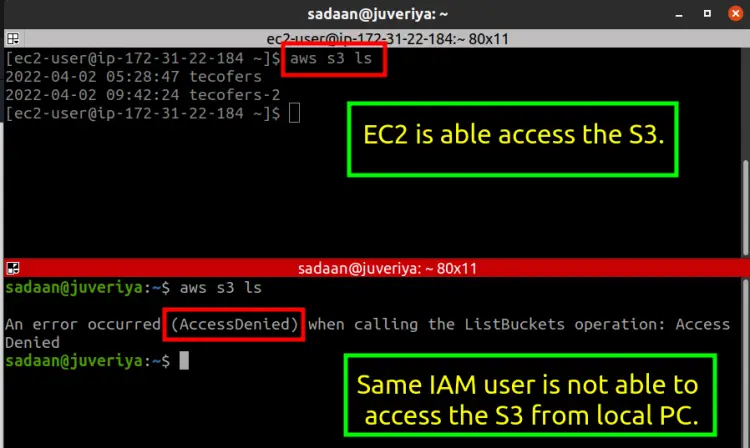
If everything has been set up correctly our EC2 instance should be able to access a S3 bucket. First create a S3 bucket from the administrator account. Next, login to the target EC2 instance and then install and configure the aws cli application for the IAM user with the ‘user-iam-policy’. From a terminal on the instance execute the below S3 listing command:
$ aws s3 ls
To cross verify if the Passrole permission is working run the same command from the same IAM user configured on a different machine. This time you will hopefully find that we are getting an error of accessibility due to limited permission:
The above error has occurred as we have only given the access permission of S3 to the EC2 instance configured with the ‘iam_user_policy’ but have not given any such permission to any other AWS service of the IAM user.
Note: The bucket and its objects are not publicly accessible.
Conclusion
In this guide we have learned how to use the PassRole permission for giving least privilege to an AWS IAM user. We have shown you how to connect an EC2 instance to a S3 bucket.