Virtual Multiserver Environment With Dedicated Web & MySQL, Email & DNS Servers On Debian Squeeze With ISPConfig 3 - Page 4
On this page
- 7 Extending Our Servers
- 7.0.1 SSH with authentication key instead of password
- 7.0.2 Installing Logwatch
- 7.0.3 Enabling additional fail2ban rules
- 7.1 Extending the Node Server
- 7.1.1 Installing Ajenti
- 7.1.2 Installing Archey
- 7.2 Extending The Web/DB Server
- 7.2.1 Installing cURL
- 7.2.2 Installing ionCube Loader
- 7.2.3 Installing APC and other useful apps
- 7.2.5 MySQL Tuning
- 7.2.6 Installing RoundCube
7 Extending Our Servers
We now have a perfectly working environment of one dedicated server running our virtual servers. However there are a lot of tweaks we can and should apply to them. We will do this now. Not that all of these are optinal but highly recommended.
The first steps may be repeated on all the servers.
7.0.1 SSH with authentication key instead of password
Using SSH key authentication is much more secure than password, because you have to own the private keyto access the server. If you don't already have one, create and RSA key pair (on your local machine):
ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/username/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/username/.ssh/id_rsa.
Your public key has been saved in /home/username/.ssh/id_rsa.pub.
Once the public key is installed on the server, access will be granted with no password question. SSH usually comes with an utility called ssh-copy-id that simply adds the contents of client's ~/.ssh/id_rsa.pub to the server's ~/.ssh/authorized_keys:
ssh-copy-id -i .ssh/id_rsa.pub [email protected]
At this point, root account on the server can be locked for password authentication:
Please first try accessing the server using the key before running this command!
passwd -l root
7.0.2 Installing Logwatch
Logwatch is a little package that will send you detailed reports on what happend/is running on your server. It's absolutely useful for monitoring.
apt-get -y install logwatch
Then adjust its configuration:
nano /usr/share/logwatch/default.conf/logwatch.conf
and set these values:
Output = mail Format = text MailTo = [email protected] Detail = High Service = All
You now will receive an email from Logwatch every day. You'll see, this is awesome!
7.0.3 Enabling additional fail2ban rules
Fail2ban is a great way to block unwanted users from accessing our servers. Since we already have it installed on our Web & MySQL Server as well on our Mail Server, you can skip the first step on them. Run this on your node and both DNS servers:
apt-get -y install fail2ban
We now will tell fail2ban what services it should monitor and how to handle bad requests:
These have to be run on all servers (including the Web & MySQL server and the Mail server):
nano /etc/fail2ban/jail.local
and add the following to the file (do not replace already existing content!):
[ssh] enables = true port = ssh filter = sshd logpath = /var/log/auth.log maxretry = 3 [ssh-ddos] enabled = true port = ssh filter = sshd-ddos logpath = /var/log/auth.log maxretry = 5
Fail2ban will now detect SSH break-in attemps and block them. Finally, restart fail2ban:
/etc/init.d/fail2ban restart
7.1 Extending the Node Server
7.1.1 Installing Ajenti
Ajenti is a nice server control panel. I primary use it for managing the firewall and because of the built in filemanager, console and terminal.
First we have to add it's repository to our sources.list:
nano /etc/apt/sources.list
and add:
deb http://repo.ajenti.org/debian main main
Afterwards you have to import it's Key:
wget http://repo.ajenti.org/debian/key -O- | sudo apt-key add -
You should now be able to access the CP via: http://192.168.1.1:8000. The default username/password is: admin
If you plan to use the built in terminal you have to install the Python PIL module:
apt-get -y install python-imaging
7.1.2 Installing Archey
This is very optional, however I like it. Archey will show you some nice information on login.
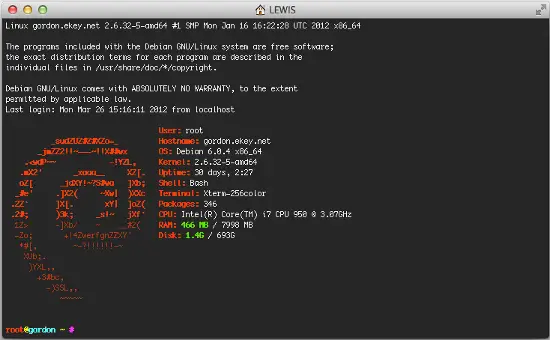
To install it, simply run:
apt-get install lsb-release scrot
cd /tmp
wget https://github.com/downloads/djmelik/archey/archey-0.2.8.deb
dpkg -i archey-0.2.8.deb
rm archey-0.2.8.deb
nano /etc/bash.bashrc
At the very end, add: archey.
7.2 Extending The Web/DB Server
These steps are only run on our Web/DB server.
7.2.1 Installing cURL
apt-get -y install curl php5-curl libcurl3-dev
7.2.2 Installing ionCube Loader
You should now be able to do this by yourself. Just download the correct version over at http://www.ioncube.com/loaders.php and follow its introductions.
7.2.3 Installing APC and other useful apps
In this section we will install apc (php accelarator), which is developed by the guys who develop php and some apps (htop, iptraf, logwatch, tiger).
apt-get -y install php-apc htop iptraf tiger
Edit /etc/php5/conf.d/apc.ini, so as to increase the memory cache:
nano /etc/php5/conf.d/apc.ini
And append the following line:
apc.shm_size=128
Finally restart Apache:
/etc/init.d/apache2 restart
With htop you can see system info in a better way than top, with iptraf you can see real time statistics for your connection and with tiger you can have yourself mailed with a periodically report of your system's security vulnerabilities (if any exists).
As a lot of scripts/apps send a lot of mails to user root, you can alias root's mail, to a more 'real' email address. So, after you set up a 'real' mail for your example.tld domain, you can edit the aliases and add an alias to root user:
nano /etc/aliases
and change the line
root:root
to something like
root:[email protected]
After this execute:
newaliases
If you want to install Drupal (or other cms) you will propably need uploadprogress and json. To accomplish their installation, do:
apt-get -y install php5-dev php-services-json
pecl install uploadprogress
touch /etc/php5/apache2/conf.d/uploadprogress.ini
nano /etc/php5/apache2/conf.d/uploadprogress.ini
And append the following line:
extension=uploadprogress.so
Finally restart Apache:
/etc/init.d/apache2 restart
7.2.4 Installing mod_security
Install the apache mod-security 2 module with apt from the Debian repositories:
apt-get -y install libapache-mod-security
Create the folder for the mod-security configuration files:
mkdir /etc/apache2/mod-security
chmod 600 /etc/apache2/mod-security
Download and unpack the mod-security rules:
cd /tmp
wget http://www.modsecurity.org/download/modsecurity-core-rules_2.5-1.6.1.tar.gz
tar fvx modsecurity-core-rules_2.5-1.6.1.tar.gz
mv *.conf /etc/apache2/mod-security/
ln -s /var/log/apache2 /etc/apache2/logs
Configure apache to load the activated mod-security rules:
nano /etc/apache2/conf.d/mod-security.conf
Include /etc/apache2/mod-security/*.conf
To enable mod-security, edit the file
nano /etc/apache2/mod-security/modsecurity_crs_10_config.conf
and remove the # in front of the line:
SecDefaultAction "phase:2,log,deny,status:403,t:lowercase,t:replaceNulls,t:compressWhitespace"
Then reload Apache.
/etc/init.d/apache2 force-reload
Mod security will now start to block hack attempts to your websites and log the actions in the file /var/log/apache2/modsec_audit.log.
tail /var/log/apache2/modsec_audit.log
You will see very likely some falsely blocked URL's. To whitelist them, you can add the ID's of the rules that should not be used in the whitelist file.
Example:
nano /etc/apache2/mod-security/modsecurity_crs_99_whitelist.conf
SecRuleRemoveById 960015 SecRuleRemoveById 960016
7.2.5 MySQL Tuning
Download tuning-primer.sh and mysqltuner.pl. These will help you to improve mysql's configuration file.
cd /root/scripts
wget http://www.day32.com/MySQL/tuning-primer.sh
wget http://mysqltuner.com/mysqltuner.pl
chmod 700 tuning-primer.sh mysqltuner.pl
To execute them:
perl /root/scripts/mysqltuner.pl
/root/scripts/tuning-primer.sh
The scripts will ask some simple questions (user/pass) and will display in red colour, their suggestions for critical settings. You can use their suggestions to boost the performance of mysql-server.
7.2.6 Installing RoundCube
Following the above instructions you can install roundcube via apt-get. However following another logic (if you have the time and the courage) you can install roundcube in it's own subdomain, manually.
In "Perfect Server ...." you usually install Squirrelmai. However if you don't want it you can remove it:
apt-get remove squirrelmail
rm /etc/apache2/conf.d/squirrelmail.conf
Install roundcube. (You MUST have the mysql administrator's password before you proceed -- Let dbconfig-common configure the database. You will be asked some questions about the password of the db administrator and the password of the new user that will be created for roundcube. Answer those questions and continue:
apt-get -y install roundcube roundcube-mysql
Examle answers:
"Configure database for roundcube with dbconfig-common?" .... Answer Yes
"Database type to be used by roundcube: ...Answer mysql
"Password of the database's administrative
user:" ... Answer your-admin-DB-password
"MySQL application password for roundcube:" ... Answer the-password-you-want-to-give-to-the-roundcube-user
"Password confirmation:"... Answer the-password-you-want-to-give-to-the-roundcube-user
If something goes wrong you can always run:
dpkg-reconfigure roundcube-core
For more information, please see this post.
For everyone to be able to access his webmail (under his domain name) you have to create or edit the file /etc/apache2/conf.d/roundcube so as to set the alias to 'webmail'. If you want SSL you should include the last two directives (IfModule mod_rewrite.c) to have apache ALWAYS redirect to your SSL installation of ISPConfig.
nano /etc/apache2/conf.d/roundcube
# Those aliases do not work properly with several hosts on your apache server
# Uncomment them to use it or adapt them to your configuration
# Alias /roundcube/program/js/tiny_mce/ /usr/share/tinymce/www/
Alias /roundcube /var/lib/roundcube
Alias /webmail /var/lib/roundcube
# Access to tinymce files
<Directory "/usr/share/tinymce/www/">
Options Indexes MultiViews FollowSymLinks
AllowOverride None
Order allow,deny
allow from all
</Directory>
<Directory /var/lib/roundcube/>
Options +FollowSymLinks
# This is needed to parse /var/lib/roundcube/.htaccess. See its
# content before setting AllowOverride to None.
AllowOverride All
order allow,deny
allow from all
</Directory>
# Protecting basic directories:
<Directory /var/lib/roundcube/config>
Options -FollowSymLinks
AllowOverride None
</Directory>
<Directory /var/lib/roundcube/temp>
Options -FollowSymLinks
AllowOverride None
Order allow,deny
Deny from all
</Directory>
<Directory /var/lib/roundcube/logs>
Options -FollowSymLinks
AllowOverride None
Order allow,deny
Deny from all
</Directory>
<IfModule mod_rewrite.c>
<IfModule mod_ssl.c>
<Location /webmail>
RewriteEngine on
RewriteCond %{HTTPS} !^on$ [NC]
RewriteRule . https://%{HTTP_HOST}:50443%{REQUEST_URI} [L]
</Location>
</IfModule>
</IfModule>
<IfModule mod_rewrite.c>
<IfModule mod_ssl.c>
<Location /roundcube>
RewriteEngine on
RewriteCond %{HTTPS} !^on$ [NC]
RewriteRule . https://%{HTTP_HOST}:50443%{REQUEST_URI} [L]
</Location>
</IfModule>
</IfModule>
Edit /var/lib/roundcube/config/main.inc.php:
nano /var/lib/roundcube/config/main.inc.php
and SET some variables in the file (if this is the first time you edit the file the lines are 60 and 66):
auto_create_user = TRUE;
$rcmail_config['default_host'] = 'mail.example.tld';
If you will install the following plugin (the logger that helps fail2ban) you have to extend the list of plugins in the same file. If the only plugin is the one that will be istalled right afterward you have to edit the line (42) as below:
$rcmail_config['plugins'] = array('fail2ban');
Install the roundcube logger plugin from http://mattrude.com/projects/roundcube-fail2ban-plugin/.
Basically you have to download the file (fail2ban.php) and paste it in the fail2ban folder in the plugins folder of roundcube. Finally you must have this file: /usr/share/roundcube/plugins/fail2ban/fail2ban.php. Execute:
cd /usr/share/roundcube/plugins/
wget --no-check-certificate http://cloud.github.com/downloads/mattrude/rc-plugin-fail2ban/roundcube-fail2ban-plugin.1.1.tgz
tar -xvzf roundcube-fail2ban-plugin.1.1.tgz
touch /var/log/roundcube/userlogins
rm roundcube-fail2ban-plugin.1.1.tgz
chown www-data:www-data /var/log/roundcube/userlogins
This plugin will update the log file with each failed login attempt: /var/log/roundcube/userlogins
Don't forget to edit the link for the webmail in ISPConfig (System -> Interface Config -> (tab) Mail) and set it to /webmail. Lastly, restart apache.
/etc/init.d/apache2 restart
You can now access webmail at http://web.example.tld/webmail

