Virtual Hosting Howto With Virtualmin On CentOS 5.1 - Page 6
On this page
Configure Virtualmin
Introduction
Virtualmin is a powerful and flexible hosting control panel that integrates with webmin. We will be using it to provide the virtual hosting functions such as creation of domains, accounts and maintaining configurations on the system.
Start Services
You need to start up services that are required to be able to configure virtualmin. Start the following services:
service named start
service spamassassin start
service spamass-milter start
service clamav-milter start
service postfix start
service dovecot start
service imapproxy start
service httpd start
Initial Settings
MySQL
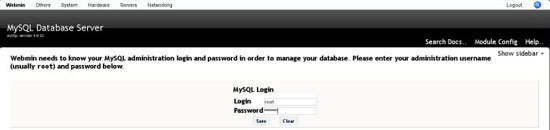
Webmin needs to be able to communicate with mysql since we have set a password for mysql we need to set that up in webmin, go to servers ? mysql and enter this information:
Configure Features
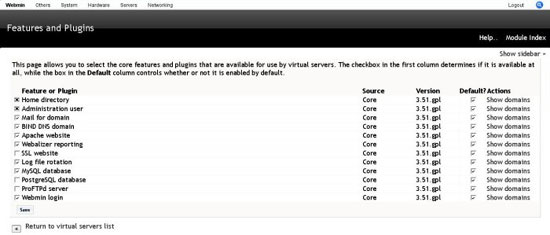
You need to enable the features and plugins that we want to use. On login this is the screen that you will see.
- Enable the following features and save
- Home directory
- Administration user
- Mail for domain
- BIND DNS domain
- Apache website
- Webalizer reporting
- Log file rotation
- Mysql database
- Webmin user
Configure Server Templates
Server template are used to customize the services and to create packages for different hosting account types.
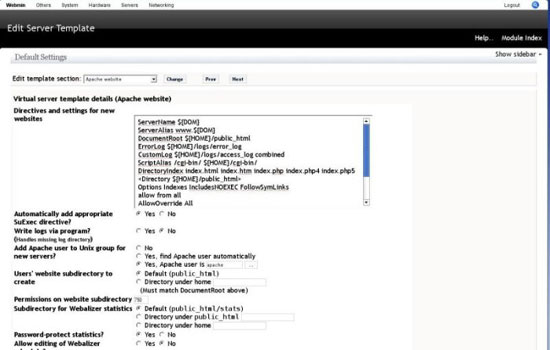
Apache Template
You can make changes to the way apache virtual hosts are created by editing this template, The defaults however will do for purposes of this howto.
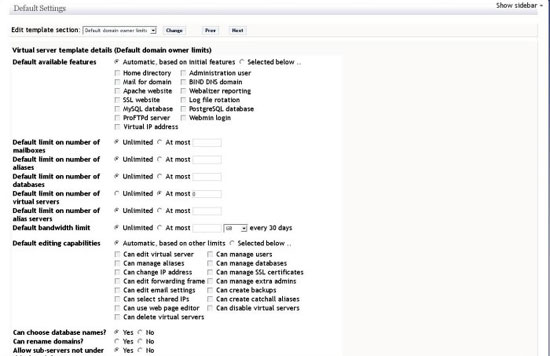
Domain Owner Template
This template is used to configure various server limits such as number of mailboxes,aliases,databases,virtual servers and other options like bandwidth limits, admin abilities. For this howto we will use the default values.
Home Directory Template
This template allows you to set a skel directory to hold setting for new users for this howto we will use the defaults.
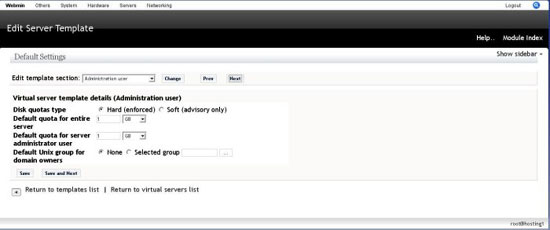
Administration User
This template lets you set the quota for the virtual server and the admin user for this howto we will use the default quota 1GB.
Mail For Domain Template
This template sets various mail related options, we will modify the email message sent on server creation to have the content below:
The following virtual server has been set up successfully :
Domain name: ${DOM}
Hosting server: ${HOSTNAME}
${IF-VIRT}
Virtual IP address: ${IP}
${ENDIF-VIRT}
Administration login: ${USER}
Administration password: ${PASS}
${IF-WEBMIN}
Administration URL: ${WEBMIN_PROTO}://www.${DOM}:${WEBMIN_PORT}/
${ENDIF-WEBMIN}
${IF-WEB}
Website: http://www.${DOM}/
${IF-WEBALIZER}
Webalizer log reporting: Enabled
${ELSE-WEBALIZER}
Webalizer log reporting: Disabled
${ENDIF-WEBALIZER}
${ENDIF-WEB}
${IF-MAIL}
Email domain: ${DOM}
SMTP server: mail.${DOM}
POP3 server: mail.${DOM}
Webmail: webmail.${DOM}
${ENDIF-MAIL}
${IF-DNS}
DNS domain: ${DOM}
Nameserver: ${HOSTNAME}
${ENDIF-DNS}
${IF-MYSQL}
MySQL database: ${DB}
MySQL login: ${MYSQL_USER}
MySQL password: ${PASS}
${ENDIF-MYSQL}
${IF-POSTGRES}
PostgreSQL database: ${DB}
PostgreSQL login: ${USER}
PostgreSQL password: ${PASS}
${ENDIF-POSTGRES}
We will leave the other options as the defaults.
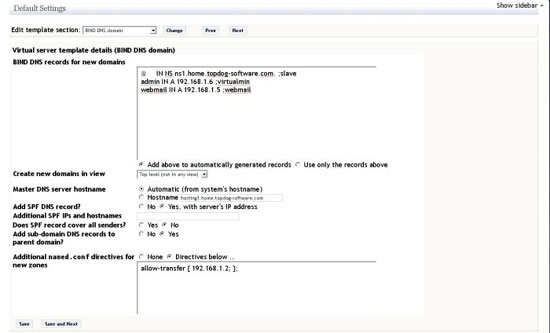
BIND DNS Domain Template
This template is used to customize the zones that will be created by virtualmin. The changes to be made are adding a spf record, add the following records to auto generated text box (replace ns1.home.topdog-software.com. with your slave server):
@ IN NS ns1.home.topdog-software.com. ;slave admin IN A 192.168.1.6 ;virtualmin webmail IN A 192.168.1.5 ;webmail
In the directives text box add the following with the IP address of your slave server such that the slave is allowed to do zone transfers.
allow-transfer { 192.168.1.2; };
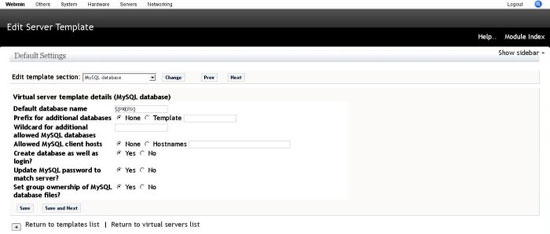
MySQL Database Template
Contains options on creation of databases by virtualmin, for the howto we will use the defaults.
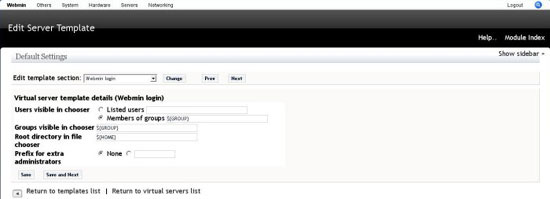
Webmin Login Template
Contains option on creation of new users by virtualmin, for the howto we will use the defaults.
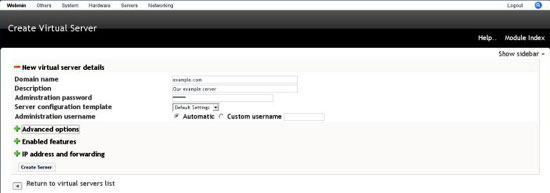
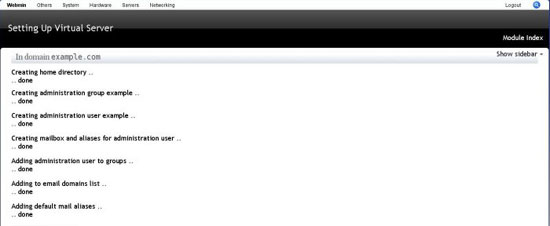
Create Virtual Server
Finally we have a working virtual server system, lets create our first virtual server. Go to servers ? virtualmin virtual servers and click add new virtual server, owned by new user.
Fill in the require fields and click create.
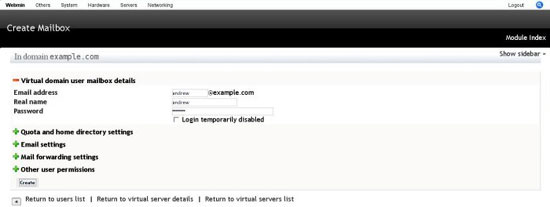
Add a mail user to the domain. click on the domain name, then click edit mail and FTP users, then add user and fill in the information.
Testing
Postfix
Test SMTP
telnet 192.168.1.5 25
Connected to localhost.
Escape character is '^]'.
220 tds mail cluster
helo me
250 hosting1
mail from:[email protected]
250 2.1.0 Ok
rcpt: [email protected]
250 2.1.0 Ok
DATA
354 End data with <CR><LF>.<CR><LF>
From:[email protected]
To:[email protected]
Subject:This is a test
Hi
This is a test
.
250 2.0.0 Ok: queued as 4ACCC7C5A6
telnet 192.168.1.5 25
Trying 192.168.1.5...
Connected to localhost.
Escape character is '^]'.
220 tds mail cluster
ehlo me
250-hosting1
250-PIPELINING
250-SIZE 10240000
250-ETRN
250-STARTTLS
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
Test dkim
Send a mail to [email protected].
Test domainkeys
Send a mail to [email protected].
Dovecot
Test POP3
telnet 192.168.1.5 110
+OK Dovecot ready.
user andrew.example
+OK
pass password
+OK Logged in.
quit
+OK Logging out.
Test IMAP
telnet 192.168.1.5 143
* OK Dovecot ready.
01 login andrew.example password
01 OK User logged in
01 list "" "*"
* LIST (\HasNoChildren) "." "Trash"
* LIST (\HasNoChildren) "." "Drafts"
* LIST (\HasNoChildren) "." "Junk"
* LIST (\HasNoChildren) "." "Sent"
* LIST (\HasNoChildren) "." "INBOX"
01 OK List completed.
01 logout
* BYE LOGOUT received
01 OK Completed
BIND
dig example.com @127.0.0.1
Clamav-milter
We are using the test virus from www.eicar.org.
telnet 192.168.1.5 25
Connected to localhost.
Escape character is '^]'.
220 tds mail cluster
helo me
250 hosting1
mail from:[email protected]
250 2.1.0 Ok
rcpt: [email protected]
250 2.1.0 Ok
DATA
354 End data with <CR><LF>.<CR><LF>
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
.
550 5.7.1 virus Eicar-Test-Signature detected by ClamAV - http://www.clamav.net
quit
221 2.0.0 Bye
Take a lot at your /var/log/maillog you should see something like this:
73BC87C4E4: milter-reject: END-OF-MESSAGE from localhost[127.0.0.1]: 5.7.1 virus Eicar-Test-Signature detected by ClamAV - http://www.clamav.net; from=<[email protected]> to=<[email protected]> proto=SMTP helo=<me>
Spamass-milter
We are using the test message from http://spamassassin.apache.org/gtube/.
telnet 192.168.1.5 25
Connected to localhost.
Escape character is '^]'.
220 tds mail cluster
helo me
250 hosting1
mail from:[email protected]
250 2.1.0 Ok
rcpt: [email protected]
250 2.1.0 Ok
DATA
354 End data with <CR><LF>.<CR><LF>
XJS*C4JDBQADN1.NSBN3*2IDNEN*GTUBE-STANDARD-ANTI-UBE-TEST-EMAIL*C.34X
.
550 5.7.1 Blocked by SpamAssassin
quit
221 2.0.0 Bye
You will see this in your log files:
spamd: result: Y 1002 - AWL,GTUBE,MISSING_SUBJECT,TVD_SPACE_RATIO,UNPARSEABLE_RELAY scantime=0.5,size=723,user=root,uid=99,required_score=5.0,