Using eBox As A Gateway: Firewall, Traffic Shaping, HTTP Proxy And More - Page 2
4.- Multigateway setup
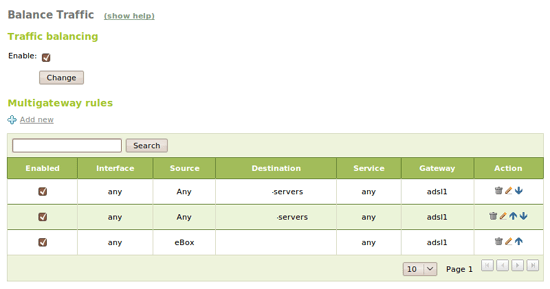
Now, to enable balancing between both gateways, this is as easy as going to Network -> Balance Traffic and checking the Balance Traffic checkbox:
Additionally, multigateway rules can be defined to force connections going through one of the gateways based on source, destination or port.
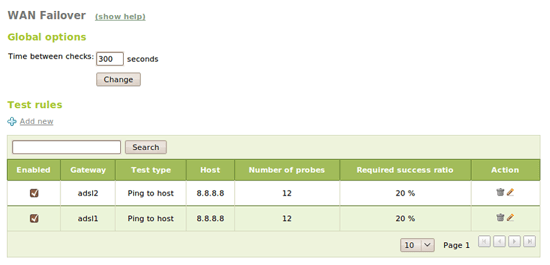
With the WAN failover feature, you can configure a set of probes: pings, DNS queries or HTTP requests to check if your gateway and Internet connection is working properly. If a percentage of probes fail, the gateway is disabled and in the next test, we try again to see if it's back working.
Multigateway rules for the failing gateways are disabled and use the default interface. When the gateways come back, they are set up again automatically.
5.- Traffic shaping
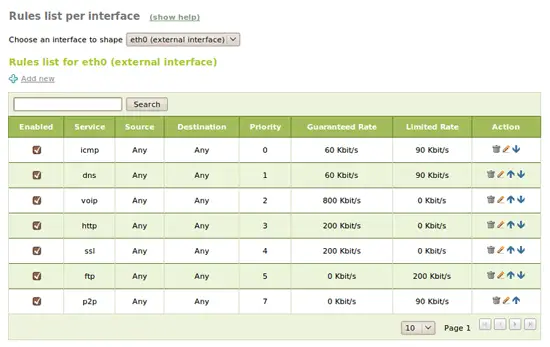
Traffic shaping, also known as Quality of Service (QoS) is important to establish the priorities between our outgoing traffic, giving more priority to the interactive services like ICMP, DNS or VoIP and giving less priority to the file transfers and P2P. eBox supports traffic shaping rules based on source, destination, ports and application (Layer 7) patterns:
We will do the same for the other external interface eth2.
6.- DHCP, DNS cache and NTP
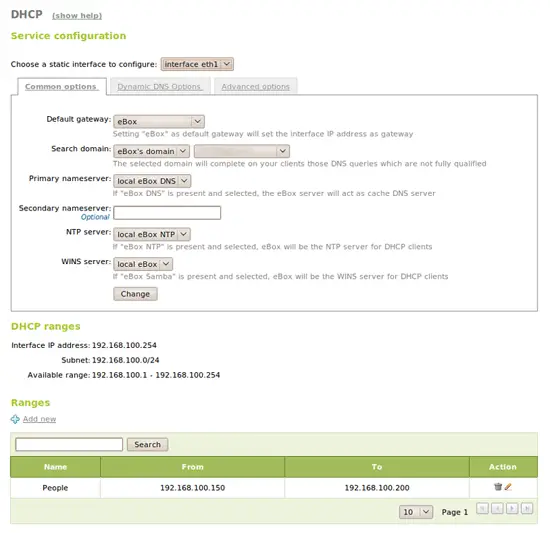
To easily configure all the computers on our LAN network, we will need a DHCP server, a DNS server and a NTP server.
DNS caching server and NTP server will work out of the box when we enable the modules. To configure DHCP, just go to the DHCP menu. There, set up the eBox as the default gateway, DNS, NTP and maybe other advanced options and a network range for the DHCP pool. Static leases based on MAC and other features like dynamic DNS or PXE are also possible.
7.- HTTP proxy
The last module to configure in order to have a full featured Gateway is our HTTP proxy. eBox uses Squid and Dansguardian for this. The HTTP proxy module uses the network objects to apply the rules, like Firewall or Traffic Shaping.
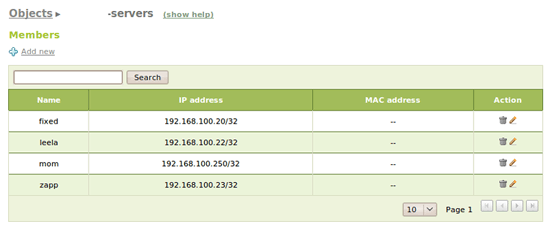
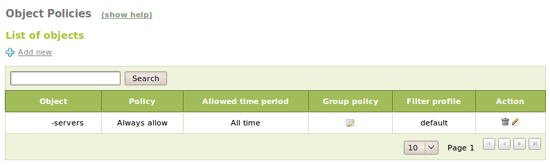
As we will be applying two different policies, we are going to create an object called lan for the whole LAN and other one for some servers we have within the LAN whose traffic won't be filtered at all. We go to the Objects menu and we create a new object lan with one member with the subnet 192.168.100.0/24 and other called -servers with the addresses of our servers:
7.1.- General configuration
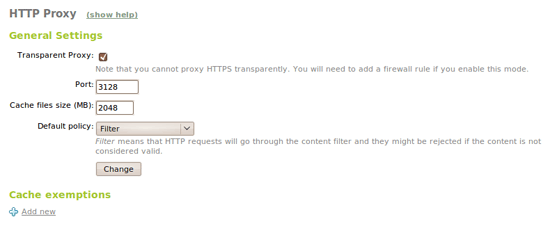
We will be able to set up the default policy and the domains that won't be stored on the Squid cache under HTTP Proxy -> General Configuration. Default policy can be:
- Always allow: Allow all requests
- Filter: Filter all requests
- Always deny: Deny all requests, only allow explicitly defined
Authorized options are not compatible with Transparent Proxy so these won't be considered for this scenario.
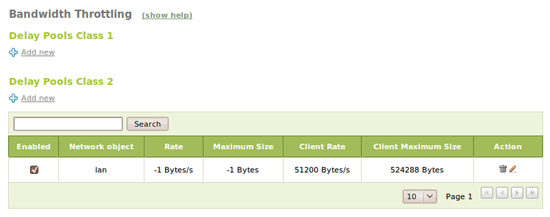
7.2.- Bandwidth throttling
The HTTP Proxy -> Bandwidth Throttling feature allows to control large downloads. When downloading a file, after the defined file size, the proxy speeds down the download to the defined rate. This policy can be applied to the whole LAN using the Delay Pools Class 1 or per client using the Delay Pools Class 2. On this example we are not limiting the download speed per subnet but per client: a file smaller than 50KB is downloaded at full speed, on larger ones, after these first 50KB, the limit speed is set to 512 KBps:
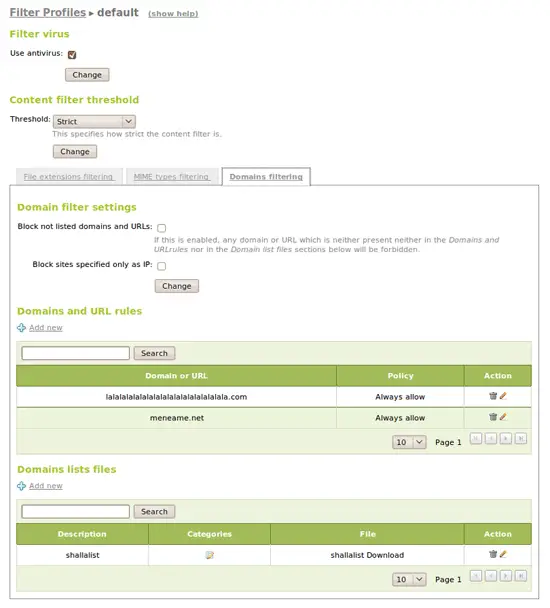
7.3.- Filtering profiles
On HTTP Proxy -> Filter Profiles we can define different filtering profiles. The default profile is applied to everyone. With these profiles you can force virus analysis on downloaded files, dynamic filtering based on keywords level, file extensions and MIME types policies. You can also define blacklists, whitelists, block unknown addresses and upload URL databases to allow or forbid categories.
When authenticated, these different profiles can be applied to different groups and when using Transparent Proxy, to network objects. You can also apply the default policies Always allow or Always deny for each group or object: