Two factor authentication with Yubikey for harddisk encryption with LUKS
The yubikey is a cool device that is around for a while and several of us know it and love it. It is a device that is recognizes as a USB HID device and can emit one time passwords on a button press.
Quite for a while the yubikey supports a challenge response mode, where the computer can send a challenge to the yubikey and the yubikey will answer with a response, that is calculated using HMAC-SHA1.
In this howto I will show, how you can use the yubikey to protect your encrypted harddisk and thus addind two factor authentication to your pre boot authentication.
The user enters a password, this password is transmitted to the yubikey as a challenge and the response is sent back. A LUKS key slot holds the response, so that in terms of LUKS the response acts as the slot passphrase.
Getting it all togeather
This solution is based on my github project yubikey-luks. You can either fetch this project in source or you can use the repository at launchpad where I uploaded a ready made package for Ubuntu 14.04LTS. This solution works fine with Ubuntu 14.04, but it can also run on other debian-like distributions. I assume that you are running Ubuntu 14.04.
Add the repository to your system:
add-apt-repository ppa:privacyidea/privacyidea
Rrefresh package information and install the tool:
apt-get update
apt-get install yubikey-luks
Enroll Yubikey
Insert your yubikey and run the command:
ykpersonalize -2 -ochal-resp -ochal-hmac -ohmac-lt64 -oserial-api-visible
The Yubikey has two slots. We use slot 2 so that you can use the slot 1 for "normal" OTP usage.
Add to LUKS
To assign the yubikey to your LUKS slot, use the command yubikey-luks-enroll. The script at /usr/bin/yubikey-luks-enroll assumes, that your LUKS partition is /dev/sda5. If it is another one, please copy the script to your homedirectory and adapt the line:
DISK="/dev/sda5"
The Yubikey response will be written to LUKS slot 7. Be sure to have a normal password availbale at some other slot. You can check this with:
cryptsetup luksDump
Insert the yubikey and run the yubikey-luks-enroll script. The script asks for a new password, which is the password, that is now sent to the yubikey to generate the repsone and which you will use at boot time.
Done.
Going live!
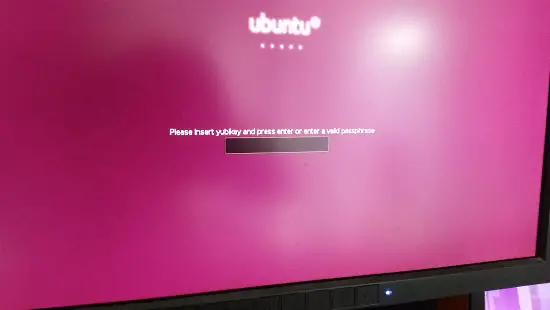
The boot screen welcomes you with the hint, to insert the yubikey. You can as well use old passphrases...
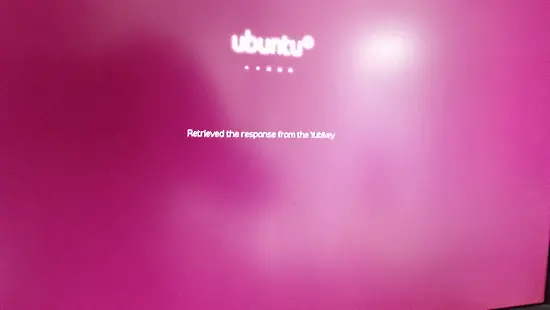
Data is retrieved from the Yubikey.
Success!
Conclusion
The bootup hooks were modified so that you can either login with a usual password or with the Yubikey plus a new password - thus increasing security in untrusted environments.
The two factor authenticaton management system privacyIDEA provides means to manage several yubikeys and assign those Yubikeys to different client machiens. Stay tuned!