Install Observium Network Monitoring Software on Debian 9
This tutorial exists for these OS versions
- Debian 11 (Bullseye)
- Debian 9 (Stretch)
- Debian 9 (Stretch)
On this page
In this guide, we’ll show you how to install and configure the latest version of Observium Network Monitoring software (Community Edition) on Debian 9 release, in order to monitor the network equipment at your premises.
Observium is a powerful and flexible free and open source auto-discovery network monitoring software written mostly in PHP programming language and deployed in Linux under Apache/Nginx web servers, PHP and MySQL/MariaDB database management system, also known as LAMP or LEMP stack. Ovservium uses SNMP protocol to query the state of network hosts, servers, routers, switches, and other network devices, supporting a large array of network hardware and operating systems, such as Linux, Windows, Cisco, HP, FreeBSD, Juniper, Brocade, Dell, and other important network devices vendors. The process of managing the application can be easily achieved via a simple and intuitive web based interface.
Requirements
- Debian 9 minimal installation on a bare-metal server machine or on a virtual private server
- sudo root privileges for a local or remote account or direct access to root account
- A static IP address configured for one of your system network interfaces cards
- A domain name, private or public, depending on your deployment, with proper DNS records configured for web services. If you don’t have a valid or a registered domain name you can perform the installation and access the website via your server IP address
- If you want to use Observium e-mail notifications, you should have a running mail server properly configured at your premises with remote access to its IMAP and SMTP services. For the same task you can also use a public email service, such as Gmail or Yahoo! Mail.
Install Apache, PHP, and MySQL
Before starting with the installation and configuration of Observium from sources in your own server, first assure the system meets all the software requirements for compiling and installing the application. In the first step, update your system repositories and software packages by issuing the following command.
apt update
apt upgrade
Next, execute the following command in order to install some necessary utilities that will be used to further manage your system from command line.
apt install wget bash-completion curl
After the system has been fully updated and the required utilities to manage your server have been installed, setup the name of your system by executing the following command. Replace your hostname variable accordingly.
hostnamectl set-hostname www.mynet.com
Verify machine hostname and hosts file by issuing the following commands.
hostnamectl
cat /etc/hostname
hostname –s
hostname –f
Finally, reboot Debian server in order to apply kernel updates and the hostname changes properly.
systemctl reboot
Observium is a web-based network monitoring platform written in PHP server-side programming language. In order to execute the PHP file scripts of the application, a web server, such as Apache HTTP server, and a PHP processing gateway must be installed and made operational in the system. In order to install Apache web server and the PHP interpreter alongside with all required PHP modules needed by the application to run properly, issue the following command in your server console.
apt install apache2 libapache2-mod-php7.0 php7.0 php7.0-gd php7.0-opcache php7.0-json php7.0-mbstring php7.0-mcrypt php-pear php7.0-cli php7.0-snmp
Issue the following command in order to verify if all the installed PHP modules are enabled in your system
php –m
Also, make sure you install the following utilities required by Observium to query and monitor network devices via SNMP protocol, detect and insert other network parameters and display system resources graphs.
apt install fping rrdtool graphviz ipmitool snmp whois mtr-tiny imagemagick python-mysqldb
After Apache and PHP has been installed, test if the web server is up and running and listening for network connections on port 80 by issuing the following command with root privileges.
netstat –tlpn
In case netstat network utility is not installed by default in your Debian system, execute the following command to install it.
apt install net-tools
By inspecting the netstat command output, you can see that apache web server is listening for incoming network connections on port 80. For the same task you can also use the ss command, which is automatically installed, by default, in Debian 9.
ss- tulpn
In case you have a firewall enabled in your system, such as UFW firewall application, you should add a new rule to allow HTTP traffic to pass through firewall by issuing the following command.
ufw allow WWW
or
ufw allow 80/tcp
If you’re using iptables raw rules to manage Firewall rules in your Debian server, add the following rule to allow port 80 and 22 (for SSH) inbound traffic on the firewall so that other network administrators can browse the online application.
apt-get install -y iptables-persistent
iptables -I INPUT -p tcp --destination-port 80 -j ACCEPT
iptables -I INPUT -p tcp --destination-port 22 -j ACCEPT
netfilter-persistent save
systemctl restart netfilter-persistent
systemctl status netfilter-persistent
systemctl enable netfilter-persistent.service
Next, enable and apply the following Apache modules required by the application to run properly, by issuing the following commands.
a2enmod rewrite
systemctl restart apache2
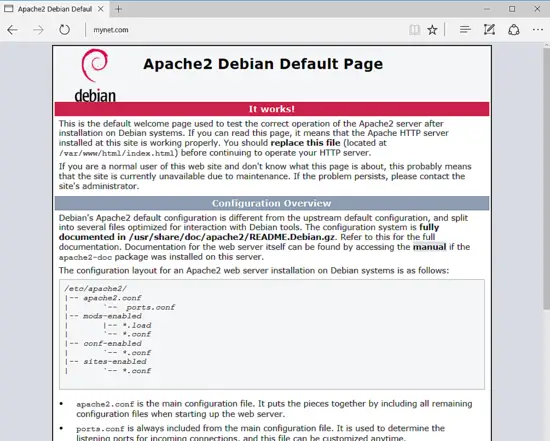
Finally, test if Apache web server default web page can be displayed in your client's browsers by visiting your Debian machine IP address or your domain name or server FQDN via HTTP protocol, as shown in the below image. If you don’t know your machine IP address, execute ifconfig or ip a commands to reveal the IP address of your server.
http://your_domain.tld
In order to install and access Observium web admin dashboard via HTTPS protocol (that will secure the traffic for your clients) issue the following command to enable Apache web server SSL module and SSL site configuration file.
a2enmod ssl
a2ensite default-ssl.conf
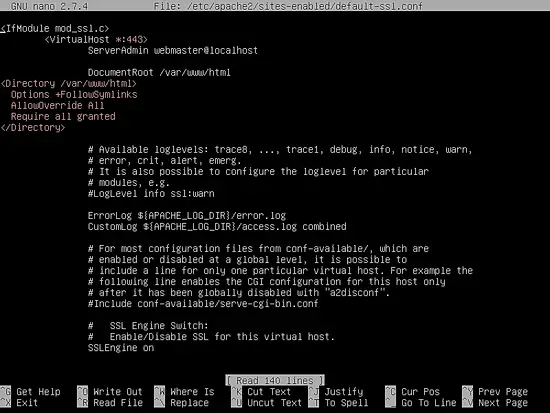
Next, open Apache default SSL site configuration file with a text editor and enable URL rewrite rules by adding the following lines of code after DocumentRoot directive, as shown in the below sample:
nano /etc/apache2/sites-enabled/default-ssl.conf
SSL site configuration file excerpt:
<Directory /var/www/html>
Options +FollowSymlinks
AllowOverride All
Require all granted
</Directory>
Also, make a change to VirtualHost line to look like the following:
<VirtualHost *:443>
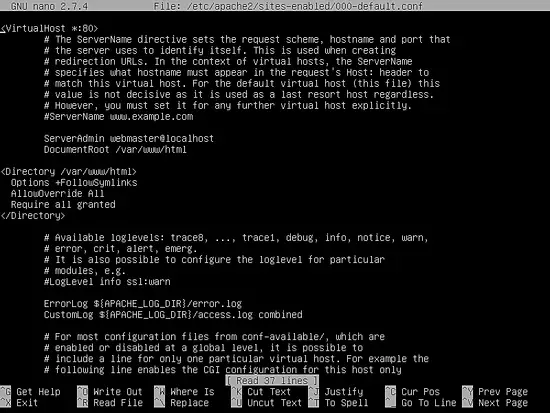
Close the SSL Apache file and open /etc/apache2/sites-enabled/000-default.conf file for editing and add the same URL rewrite rules as for SSL configuration file. Insert the following lines of code after DocumentRoot statement:
<Directory /var/www/html>
Options +FollowSymlinks
AllowOverride All
Require all granted
</Directory>
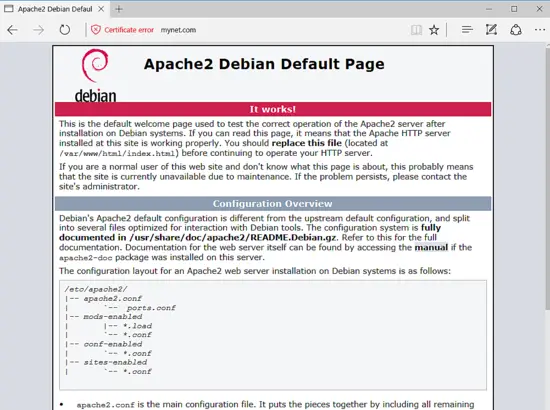
Finally, restart the Apache daemon to apply all rules configured so far and visit your domain via HTTP protocol. Because you’re using the automatically Self-Signed certificates pairs issued by Apache at installation, certificate that is untrusted by the browser, an error warning should be displayed in the browser.
systemctl restart apache2
https://yourdomain.tld
Accept the warning in order to accept the untrusted certificate and continue to be redirected to Apache default web page, as illustrated in the following image.
In case the UFW firewall application blocks incoming network connections to HTTPS port, you should add a new rule to allow HTTPS traffic to pass through firewall by issuing the following command.
ufw allow ‘WWW Full’
or
ufw allow 443/tcp
If iptables is the default firewall application installed to protect your Debian system at network level, add the following rule to allow port 443 inbound traffic in the firewall so that visitors can browse your domain name.
iptables -I INPUT -p tcp --destination-port 443 -j ACCEPT
netfilter-persistent save
systemctl restart netfilter-persistent
systemctl status netfilter-persistent
In the next step, we need to make some further changes to PHP default configuration file in order to assure that the following PHP variables are enabled and the PHP timezone setting is correctly configured and matches your system's geographical location. Open the /etc/php/7.0/apache2/php.ini file for editing and assure that the following lines are setup as shown. Also, initially, make a backup of PHP configuration file.
cp /etc/php/7.0/apache2/php.ini{,.backup}
nano /etc/php/7.0/apache2/php.ini
Search, edit and change the following variables in the php.ini configuration file:
file_uploads = On
default_charset = UTF-8
error_reporting = E_ALL & ~E_NOTICE
date.timezone = Europe/London
Replace the date.timezone variable according to your server geographical location by consulting the list of time zones provided by PHP docs at the following link http://php.net/manual/en/timezones.php
If you want to increase the load speed of your website pages via OPCache plugin available for PHP7, append the following OPCache settings at the bottom of the PHP interpreter configuration file, below the [opcache] statement, as detailed below:
nano /etc/php/7.0/apache2/php.ini
[opcache]
opcache.enable=1
opcache.enable_cli=1
opcache.interned_strings_buffer=8
opcache.max_accelerated_files=10000
opcache.memory_consumption=128
opcache.save_comments=1
opcache.revalidate_freq=1
Close the php.ini configuration file and verify the end of PHP configuration file to check if the OPCache variables have been correctly added by issuing the below command.
grep opcache /etc/php/7.0/apache2/php.ini
After you’ve made all changes explained above, restart apache daemon to apply the new changes by issuing the following command.
systemctl restart apache2
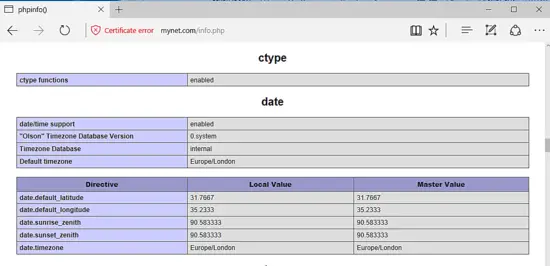
Finally, create a PHP info file by executing the following command and check if the PHP time zone has been correctly configured by visiting the PHP info script file from a browser at the following URL, as illustrated in the below image. Scroll down to date setting to check PHP time zone configuration.
echo '<?php phpinfo(); ?>'| tee /var/www/html/info.php
https://domain.tld/info.php
Observium web application stores different configurations, such as users, sessions, contacts, network devices, IP addresses, network interfaces, and other data, in an RDBMS database. In this guide, we’ll configure the Observium application to use MariaDB database as backend. Issue the following command to install MariaDB database and the PHP module needed to access the MySQL database.
apt install mariadb-server php7.0-mysql mariadb-client
After you’ve installed MariaDB, check by running the netstat command if the daemon is running and listening for connections on localhost, port 3306.
netstat –tlpn | grep mysql
Then, log in to MySQL console and secure MariaDB root account by issuing the following commands.
mysql -h localhost
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 2
Server version: 10.1.26-MariaDB-0+deb9u1 Debian 9.1
Copyright (c) 2000, 2017, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> use mysql;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [mysql]> update user set plugin='' where user='root';
Query OK, 1 row affected (0.00 sec)
Rows matched: 1 Changed: 1 Warnings: 0
MariaDB [mysql]> flush privileges;
Query OK, 0 rows affected (0.00 sec)
MariaDB [mysql]> exit
Bye
On the next step, secure MariaDB by executing the script mysql_secure_installation provided by the installation packages from Debian stretch repositories. While running the script will ask a series of questions designed to secure MariaDB database, such as: to change MySQL root password, to remove anonymous users, to disable remote root logins and delete the test database. Execute the script by issuing the following command and assure you type yes to all questions asked in order to fully secure MySQL daemon. Use the following script output excerpt as a guide.
mysql_secure_installation
NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL MariaDB SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP CAREFULLY! In order to log into MariaDB to secure it, we'll need the current password for the root user. If you've just installed MariaDB, and you haven't set the root password yet, the password will be blank, so you should just press enter here. Enter current password for root (enter for none): OK, successfully used password, moving on... Setting the root password ensures that nobody can log into the MariaDB root user without the proper authorisation. You already have a root password set, so you can safely answer 'n'. Change the root password? [Y/n] y New password: Re-enter new password: Password updated successfully! Reloading privilege tables.. ... Success! By default, a MariaDB installation has an anonymous user, allowing anyone to log into MariaDB without having to have a user account created for them. This is intended only for testing, and to make the installation go a bit smoother. You should remove them before moving into a production environment. Remove anonymous users? [Y/n] y ... Success! Normally, root should only be allowed to connect from 'localhost'. This ensures that someone cannot guess at the root password from the network. Disallow root login remotely? [Y/n] y ... Success! By default, MariaDB comes with a database named 'test' that anyone can access. This is also intended only for testing, and should be removed before moving into a production environment. Remove test database and access to it? [Y/n] y - Dropping test database... ... Success! - Removing privileges on test database... ... Success! Reloading the privilege tables will ensure that all changes made so far will take effect immediately. Reload privilege tables now? [Y/n] y ... Success! Cleaning up... All done! If you've completed all of the above steps, your MariaDB installation should now be secure. Thanks for using MariaDB!
In order to test MariaDB security, try logging into the database from console with no root password. The access to the database should be denied if no password is provided for the root account, as illustrated in the below command excerpt:
mysql -h localhost -u root
ERROR 1045 (28000): Access denied for user 'root'@'localhost' (using password: NO)
If the password is supplied, the login process should be granted to MySQL console, as shown in the command following sample:
mysql -h localhost -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 15
Server version: 10.1.26-MariaDB-0+deb9u1 Debian 9.1
Copyright (c) 2000, 2017, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> exit
Bye
Next, log in to the MariaDB database console and create by issuing the following commands a database for Observium application and a user with a password that will be used to manage the application database. Replace the database name, user, and password accordingly.
mysql –u root -p
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 2
Server version: 10.1.26-MariaDB-0+deb9u1 Debian 9.1
Copyright (c) 2000, 2017, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> create database observium_db;
Query OK, 1 row affected (0.00 sec)
MariaDB [(none)]> grant all privileges on observium_db.* to 'observium_user'@'localhost' identified by 'password1234';
Query OK, 0 rows affected (0.00 sec)
MariaDB [(none)]> flush privileges;
Query OK, 0 rows affected (0.00 sec)
MariaDB [(none)]> exit
Bye
In order to apply all changes made so far, restart MySQL and Apache daemons and verify if daemons are running by issuing the following commands.
systemctl restart mysql apache2
systemctl status mysql apache2
Install Observium Network Monitoring Platform
After all system requirements are met to install the application, visit Observium official page at www.observium.org and grab the latest gzip compressed archive by issuing the following command.
wget http://www.observium.org/observium-community-latest.tar.gz
After the gzip archive download finishes, extract Observium archive file to your current working directory and list the extracted files by issuing the following commands. Also, remove the default index.html file installed by Apache web server to webroot path and also delete the info.php file created earlier.
tar xfz observium-community-latest.tar.gz
ls
rm /var/www/html/index.html
rm /var/www/html/info.php
The installation files of Observium are located in your current working directory in the observium/ directory. Issue ls command to list this directory files. Copy all the content of the extracted directory to your web server document root path one level up (/var/www/ directory) by issuing the following commands. Also, make sure you copy the hidden files to installation directory and create the logs and rrd directories in this location.
cp -rf observium/* /var/www/
cp observium/.scrutinizer.yml /var/www/
mkdir /var/www/logs
mkdir /var/www/rrd
ls -al /var/www/
Next, execute the following commands in order to grant Apache runtime user with full write permissions to the web root path and application’s rrd and logs directories. Use ls command to list permissions for application’s installed files, located in the /var/www/html/ and rrd and logs directories.
chown -R www-data:www-data /var/www/rrd/
chown -R www-data:www-data /var/www/logs/
chown -R www-data:www-data /var/www/html/
ls -al /var/www/html/
In the next step, create a new application configuration file based on Observium default template configuration file by issuing the following commands.
cd /var/www/
cp config.php.default config.php
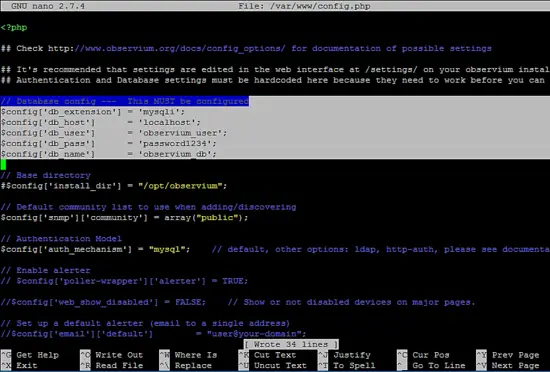
Next, start editing the Observium configuration file and replace the following MySQL connection variables accordingly.
nano /var/www/ config.php
On top of the config.php file, search and update MySQL database name and credentials according to your own settings, as shown in the following file excerpt:
$config['db_extension'] = 'mysqli';
$config['db_host'] = 'localhost';
$config['db_user'] = 'observium_user';
$config['db_pass'] = 'password1234';
$config['db_name'] = 'observium_db';
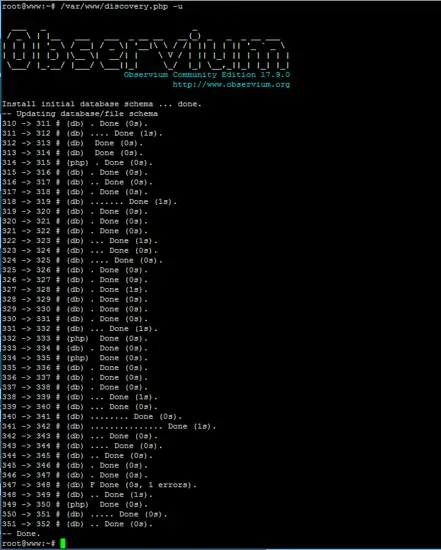
Next, save and close the config.php file and import Observium MySQL database schema by executing the discover.php script with the –u flag as shown in the following screenshot. The PHP script is located in the /var/www/ directory.
/var/www/discovery.php –u
Next, add the first Observium admin account with the highest privileges level (10) by executing the adduser.php script located in the /var/www/ directory. Choose a strong password for Observium admin account.
/var/www/adduser.php observium_admin strongpass123 10
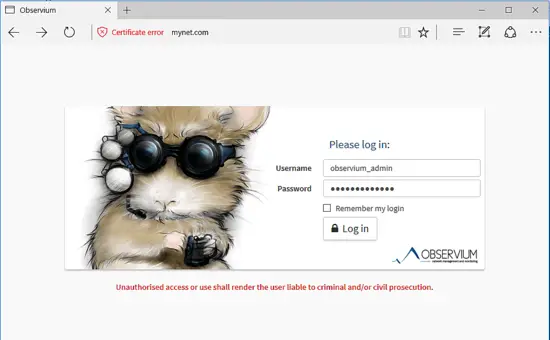
To log in to Observium web admin panel, open a browser and navigate your server’s IP address or domain name or server FQDN via HTTPS protocol. Log in to Observium dashboard with the username and password configured for admin account in the above step.
https://yourdomain.tld
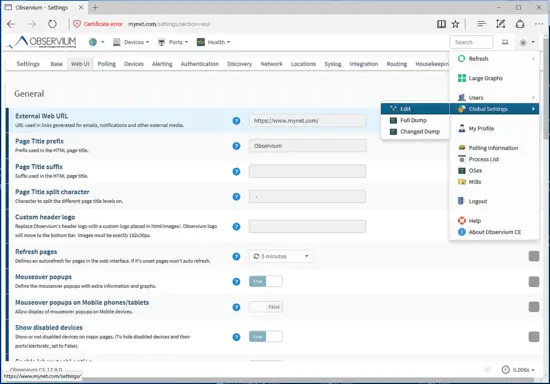
After you log in to the application with the admin credentials, you further tune-up the application settings by navigating to /settings/ URL or click on Global Settings -> Edit menu, as illustrated in the following screenshot. The Observium parameters configured via web interface can also be hardcoded into the application configuration file: /var/www/config.php
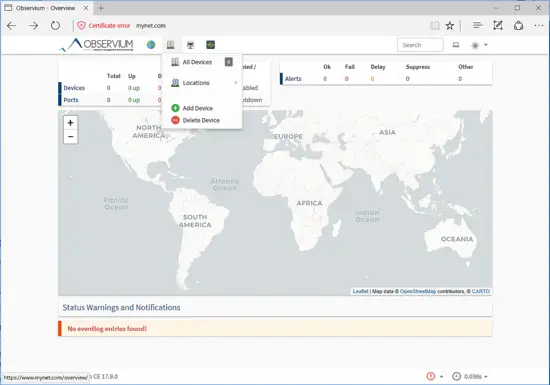
In order to monitor a network device via the SNMP protocol, hit on the top left menu and select Add Device from the pop-down menu, as shown in the image below. You can also add a new device via the command line.
/var/www/add_device.php hostname_or_IP SNMP_community_string v2c
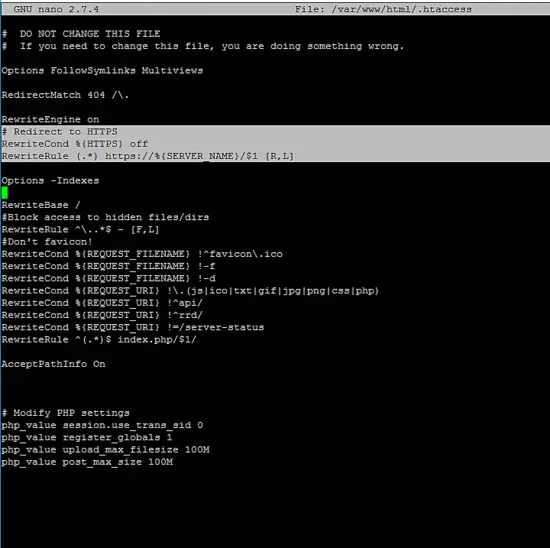
Finally, to force visitors to securely browse the Observium interface via HTTPS protocol that encrypts the traffic between the server and clients browsers, return to your server’s terminal and edit the .htaccess file located in your website document root path, by issuing the below command.
nano /var/www/html/.htaccess
Add the following rules in .htaccess file after RewriteEngine on line, in order to automatically redirect domain traffic to HTTPS.
.htaccess file excerpt:
# Redirect to HTTPS
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule (.*) https://%{SERVER_NAME}/$1 [R,L]
You can also disable Apache HTTP server web document listing by adding the following line after redirect to HTTPS lines:
Options -Indexes
At the bottom of the file you can change the native PHP server settings with the following configuration examples. Modify the PHP settings to match your own server resources and configurations.
# Modify PHP settings
php_value session.use_trans_sid 0
php_value register_globals 1
In order for the application to automatically discover and add new network devices into the database and check and update their status every five minutes, add the following crontab jobs to be executed under Apache runtime user privileges:
crontab –u www-data –e
crontab file excerpt:
# Run a complete discovery of all devices once every 6 hours
33 */6 * * * /var/www/discovery.php -h all >> /dev/null 2>&1
# Run automated discovery of newly added devices every 5 minutes
*/5 * * * * /var/www/discovery.php -h new >> /dev/null 2>&1
# Run multithreaded poller wrapper every 5 minutes
*/5 * * * * /var/www/poller-wrapper.py 4 >> /dev/null 2>&1
That’s all! You have successfully installed and configured Observium network monitoring application in Debian 9. However, because Apache HTTP server uses Self-Signed certificates to encrypt the traffic between the server and visitor browser, a warning message will always be generated and displayed in visitor’s browser. This warning can be annoying by network administrators that visit the web application via a new browser or IP address. In this case you should buy a certificate issued by a trusted Certificate Authority or get a free certificate pair from Let’s Encrypt CA.
For other custom configurations regarding Observium application, visit the documentation page at the following address: http://docs.observium.org/