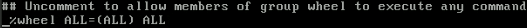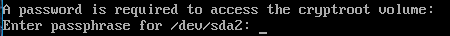How to install Arch Linux with Full Disk Encryption
On this page
In today's tutorial we are going to install Arch Linux with full disk encryption.
Before we proceed, I want you to backup your existing data.
In the previous tutorial we learnt what dm-crypt and LUKS are and how to encrypt single disk partition. While in the post today we will take a slightly different approach to encrypt the whole disk with dm-crypt LUKS and install Archlinux on it.
Let's start with disk erasing. Run lsblk to find your primary disk and replace /dev/sda where needed:
shred --verbose --random-source=/dev/urandom --iterations=3 /dev/sda
I ran the above command with '--iterations=15' on my 120GB SSD overnight and it finished after 7 hours.
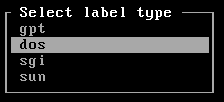
Once done, partition the disk. Unless your motherboard is using UEFI firmware, make sure to select 'dos' (msdos) label, otherwise go with the 'gpt' when you type:
cfdisk /dev/sda
After that create boot loader partition:
New-> Partition Size: 100M -> primary -> Bootable
The last one will be the root partition. The partition size should be automatically set to your remaining free space.
New-> Partition Size: xxxGB -> primary
Write the changes and quit from cfdisk.
In order to boot your encrypted root partition, the boot loader partition /dev/sda1 that will be mounted in /boot won't be encrypted. I will place couple links at the end of this post that will guide you how to encrypt and even move the boot partition on a CD/DVD/USB.
Create cryptographic device mapper device in LUKS encryption mode:
cryptsetup --verbose --cipher aes-xts-plain64 --key-size 512 --hash sha512 --iter-time 5000 --use-random luksFormat /dev/sda2
Unlock the partition, note that cryptroot will be the device mapper name that we will operate on.
cryptsetup open --type luks /dev/sda2 cryptroot
Create the boot and root file systems:
mkfs.ext4 /dev/sda1
mkfs.ext4 /dev/mapper/cryptroot
Mount them:
mount -t ext4 /dev/mapper/cryptroot /mnt
mkdir -p /mnt/boot
mount -t ext4 /dev/sda1 /mnt/boot
Install the base and base-devel systems:
pacstrap -i /mnt base base-devel
Generate the fstab:
genfstab -U -p /mnt >> /mnt/etc/fstab
Chroot to configure the base system:
arch-chroot /mnt
Uncomment the en_US locale:
sed -i 's/#en_US.UTF-8 UTF-8/en_US.UTF-8 UTF-8/g' /etc/locale.gen
Generate the locale:
locale-gen
Create configuration file that would instruct the system what language locale it should be using:
echo LANG=en_US.UTF-8 > /etc/locale.conf
Export the locale
export LANG=en_US.UTF-8
Create a symbolic link with the desired time zone:
ln -s /usr/share/zoneinfo/Europe/Berlin /etc/localtime
Set the hardware clock to UTC:
hwclock --systohc --utc
Set the desired hostname:
echo CookieMonster > /etc/hostname
Set the root password:
passwd
Add a system user:
useradd -m -g users -G wheel,games,power,optical,storage,scanner,lp,audio,video -s /bin/bash username
Set the system user password:
passwd username
Install sudo (base-devel) and the boot loader grub and os-prober:
pacman -S sudo grub-bios os-prober
Allow the system user to use sudo and run commands (temporary) as root:
EDITOR=nano visudo
Press CTRL + W and type wheel, then uncomment the following line:
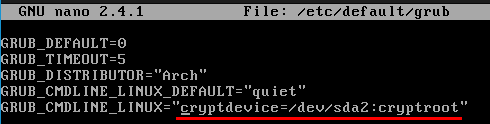
Add the following kernel parameter to be able to unlock your LUKS encrypted root partition during system startup:
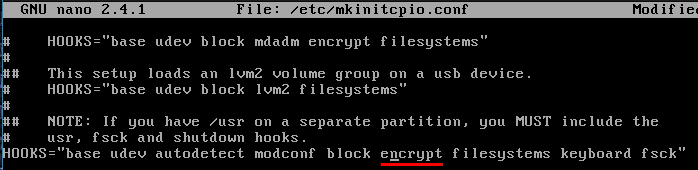
Add encrypt hook:
Since we added new hook in the mkinitcpio configuration file, we should re-generate our initrams image (ramdisk):
mkinitcpio -p linux
Install grub and save it's configuration file:
grub-install --recheck /dev/sda
grub-mkconfig --output /boot/grub/grub.cfg
Exit from chroot, unmount the partitions, close the device and reboot (remove the installation media):
exit
umount -R /mnt/boot
umount -R /mnt
cryptsetup close cryptroot
systemctl reboot
Once you type in your password and login as system user, start dhcpcd.
sudo systemctl start dhcpcd
ping -c2 youtube.com
Install Xorg and copy .xinitrc over your $HOME dir:
sudo pacman -S xorg-server xorg-server-utils xorg-xinit mesa xterm xorg-twm xorg-xclock
cp /etc/X11/xinit/xinitrc ~/.xinitrc
There is a special wiki page that contains useful information for the GPU drivers, check it out https://wiki.archlinux.org/index.php/xorg#Driver_installation and if it happens your GPU brand to be amd/ati, intel or nvidia install the appropriate drivers listed there.
Type startx and you should see couple terminals side-by-side, now type exit
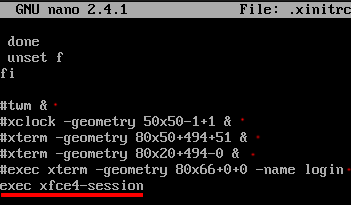
Comment in the following lines in .xinitrc and add some to specify that we want the xfce desktop environment to be started upon successful login:
Install xfce, external display manager and network manager:
sudo pacman -S slim archlinux-themes-slim xfce4 networkmanager network-manager-applet
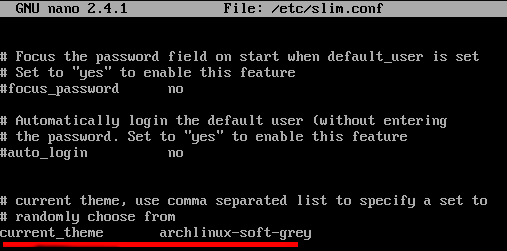
Exchange the default slim theme:
Stop dhcpcd, enable slim, enable NetworkManager, startx:
sudo systemctl stop dhcpcd
sudo systemctl enable NetworkManager
sudo systemctl enable slim
startx
That was it, hope you enjoyed this post.
If you ever manage to f*ck up your system and have to chroot from removable media, the order is:
cryptsetup open --type luks /dev/sda2 cryptroot
mount -t ext4 /dev/mapper/cryptroot /mnt
mount -t ext4 /dev/sda1 /mnt/boot
arch-chroot /mnt
To unmount them:
umount -R /mnt/boot
umount -R /mnt
cryptsetup close cryptroot
Links
The promised links, read the 8th and 9th links carefully if you got SSD: