How to Encrypt Directories with eCryptfs on Ubuntu 16.04
This tutorial shows how to use eCryptfs to encrypt a directory on Ubuntu 16.04 (Xenial Xerus). eCryptfs is a POSIX-compliant enterprise-class stacked cryptographic filesystem for Linux. You can use it to encrypt partitions and also directories that don't use a partition of their own, no matter the underlying filesystem, partition type, etc.
1 Preliminary Note
In this tutorial, I will encrypt a new directory /home/secure. this is an ordinary directory and does not use a partition of its own.
2 Installing eCryptfs
eCryptfs can easily be installed as follows:
apt-get -y install ecryptfs-utils
3 Encrypting a directory with eCryptfs
I will now encrypt a new directory /home/secure/. Create the directory with the mkdir command:
mkdir /home/secure
If you use an existing directory then there might be already (unencrypted) files in that directory. In this case you have to take a backup of them so that you can restore them to the then encrypted /home/secure/ directory later on (otherwise these filles cannot be accessed/read while the directory is encrypted):
cp -pfr /home/secure/ /tmp/
I can now encrypt the directory /home/secure/ by mounting it with the file system type ecryptfs:
mount -t ecryptfs /home/secure /home/secure
When you do this for the first time, you will have to answer a few questions:
root@server1:~# mount -t ecryptfs /home/secure /home/secure
Passphrase: <-- Enter a secure password
Select cipher:
1) aes: blocksize = 16; min keysize = 16; max keysize = 32
2) blowfish: blocksize = 8; min keysize = 16; max keysize = 56
3) des3_ede: blocksize = 8; min keysize = 24; max keysize = 24
4) twofish: blocksize = 16; min keysize = 16; max keysize = 32
5) cast6: blocksize = 16; min keysize = 16; max keysize = 32
6) cast5: blocksize = 8; min keysize = 5; max keysize = 16
Selection [aes]: <-- Press ENTER
Select key bytes:
1) 16
2) 32
3) 24
Selection [16]: <-- 32
Enable plaintext passthrough (y/n) [n]: <-- Press ENTER
Enable filename encryption (y/n) [n]: <-- Press ENTER
Attempting to mount with the following options:
ecryptfs_unlink_sigs
ecryptfs_key_bytes=16
ecryptfs_cipher=aes
ecryptfs_sig=bd28c38da9fc938b
Mounted eCryptfs
root@server1:~#
The default settings that I have chosen here encrypt the content of the file but not the file name. If you wish to keep the files names secured as well, then please enable the filename encryption option during setup above.
Take a look at the output of
mount
and you should see that /home/secure/ is now encrypted:
root@server1:~# mount
sysfs on /sys type sysfs (rw,nosuid,nodev,noexec,relatime)
proc on /proc type proc (rw,nosuid,nodev,noexec,relatime)
udev on /dev type devtmpfs (rw,nosuid,relatime,size=1002992k,nr_inodes=250748,mode=755)
devpts on /dev/pts type devpts (rw,nosuid,noexec,relatime,gid=5,mode=620,ptmxmode=000)
tmpfs on /run type tmpfs (rw,nosuid,noexec,relatime,size=204440k,mode=755)
/dev/mapper/server1--vg-root on / type ext4 (rw,relatime,errors=remount-ro,data=ordered,jqfmt=vfsv0,usrjquota=quota.user,grpjquota=quota.group)
securityfs on /sys/kernel/security type securityfs (rw,nosuid,nodev,noexec,relatime)
tmpfs on /dev/shm type tmpfs (rw,nosuid,nodev)
tmpfs on /run/lock type tmpfs (rw,nosuid,nodev,noexec,relatime,size=5120k)
tmpfs on /sys/fs/cgroup type tmpfs (ro,nosuid,nodev,noexec,mode=755)
cgroup on /sys/fs/cgroup/systemd type cgroup (rw,nosuid,nodev,noexec,relatime,xattr,release_agent=/lib/systemd/systemd-cgroups-agent,name=systemd,nsroot=/)
pstore on /sys/fs/pstore type pstore (rw,nosuid,nodev,noexec,relatime)
cgroup on /sys/fs/cgroup/pids type cgroup (rw,nosuid,nodev,noexec,relatime,pids,nsroot=/)
cgroup on /sys/fs/cgroup/freezer type cgroup (rw,nosuid,nodev,noexec,relatime,freezer,nsroot=/)
cgroup on /sys/fs/cgroup/blkio type cgroup (rw,nosuid,nodev,noexec,relatime,blkio,nsroot=/)
cgroup on /sys/fs/cgroup/hugetlb type cgroup (rw,nosuid,nodev,noexec,relatime,hugetlb,nsroot=/)
cgroup on /sys/fs/cgroup/cpuset type cgroup (rw,nosuid,nodev,noexec,relatime,cpuset,nsroot=/)
cgroup on /sys/fs/cgroup/cpu,cpuacct type cgroup (rw,nosuid,nodev,noexec,relatime,cpu,cpuacct,nsroot=/)
cgroup on /sys/fs/cgroup/net_cls,net_prio type cgroup (rw,nosuid,nodev,noexec,relatime,net_cls,net_prio,nsroot=/)
cgroup on /sys/fs/cgroup/memory type cgroup (rw,nosuid,nodev,noexec,relatime,memory,nsroot=/)
cgroup on /sys/fs/cgroup/perf_event type cgroup (rw,nosuid,nodev,noexec,relatime,perf_event,nsroot=/)
cgroup on /sys/fs/cgroup/devices type cgroup (rw,nosuid,nodev,noexec,relatime,devices,nsroot=/)
systemd-1 on /proc/sys/fs/binfmt_misc type autofs (rw,relatime,fd=27,pgrp=1,timeout=0,minproto=5,maxproto=5,direct)
debugfs on /sys/kernel/debug type debugfs (rw,relatime)
hugetlbfs on /dev/hugepages type hugetlbfs (rw,relatime)
mqueue on /dev/mqueue type mqueue (rw,relatime)
fusectl on /sys/fs/fuse/connections type fusectl (rw,relatime)
/dev/sda1 on /boot type ext2 (rw,relatime,block_validity,barrier,user_xattr,acl)
tmpfs on /run/lxcfs/controllers type tmpfs (rw,relatime,size=100k,mode=700)
devices on /run/lxcfs/controllers/devices type cgroup (rw,relatime,devices,nsroot=/)
perf_event on /run/lxcfs/controllers/perf_event type cgroup (rw,relatime,perf_event,nsroot=/)
memory on /run/lxcfs/controllers/memory type cgroup (rw,relatime,memory,nsroot=/)
net_cls,net_prio on /run/lxcfs/controllers/net_cls,net_prio type cgroup (rw,relatime,net_cls,net_prio,nsroot=/)
cpu,cpuacct on /run/lxcfs/controllers/cpu,cpuacct type cgroup (rw,relatime,cpu,cpuacct,nsroot=/)
cpuset on /run/lxcfs/controllers/cpuset type cgroup (rw,relatime,cpuset,nsroot=/)
hugetlb on /run/lxcfs/controllers/hugetlb type cgroup (rw,relatime,hugetlb,nsroot=/)
blkio on /run/lxcfs/controllers/blkio type cgroup (rw,relatime,blkio,nsroot=/)
freezer on /run/lxcfs/controllers/freezer type cgroup (rw,relatime,freezer,nsroot=/)
pids on /run/lxcfs/controllers/pids type cgroup (rw,relatime,pids,nsroot=/)
name=systemd on /run/lxcfs/controllers/name=systemd type cgroup (rw,relatime,xattr,release_agent=/lib/systemd/systemd-cgroups-agent,name=systemd,nsroot=/)
lxcfs on /var/lib/lxcfs type fuse.lxcfs (rw,nosuid,nodev,relatime,user_id=0,group_id=0,allow_other)
tmpfs on /run/user/1000 type tmpfs (rw,nosuid,nodev,relatime,size=204440k,mode=700,uid=1000,gid=1000)
tmpfs on /run/user/0 type tmpfs (rw,nosuid,nodev,relatime,size=204440k,mode=700)
/home/secure on /home/secure type ecryptfs (rw,relatime,ecryptfs_sig=bd28c38da9fc938b,ecryptfs_cipher=aes,ecryptfs_key_bytes=32,ecryptfs_unlink_sigs)
root@server1:~#
When using a existing directory: Let's restore our backup to the now encrypted directory /home/secure/ and delete the backup afterwards:
cp -pfr /tmp/secure/ /home/
rm -fr /tmp/secure/
For testing purposes, let's copy some other file, e.g. /etc/hosts, to /home/secure/ to check if it really gets encrypted:
cp /etc/hosts /home/secure
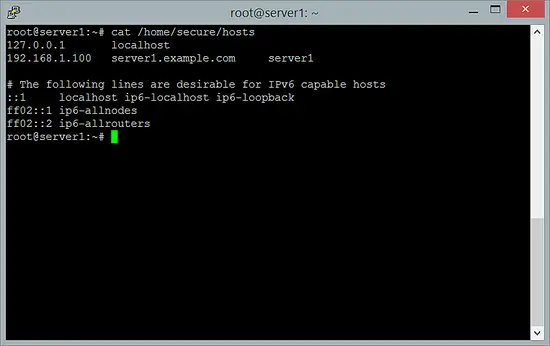
While /home/secure/ is mounted with the ecryptfs file system type, it should be possible to read the contents of /home/secure/hosts:
cat /home/secure/hosts
Now unmount /home/secure/...
umount /home/secure
... and try again to read /home/secure/hosts, and you should get some cryptic stuff:
cat /home/secure/hosts
4 Links
- eCryptfs: https://launchpad.net/ecryptfs
- Debian: http://www.debian.org/