Stronghenge Application Firewall - Page 2
Configuration:
Log-in to the management console via a web browser: https://<<IP_OR_HOST_OF_APPLIANCE>>/
Username and Password: stronghenge
Configure user accounts:
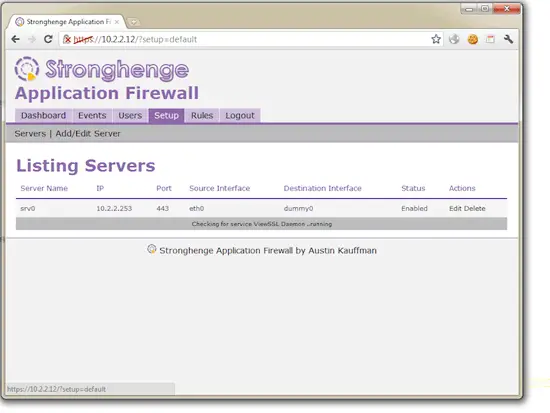
Configure SSL decryption:
The source interface is the interface that in promiscuous mode and that can see the traffic. The destination interface is where the decrypted traffic will be sent; in most cases this will be one of the dummy interfaces. Any modifications will automatically be applied to the running services.
If you won't be decrypting any SSL traffic, leave the default configuration.
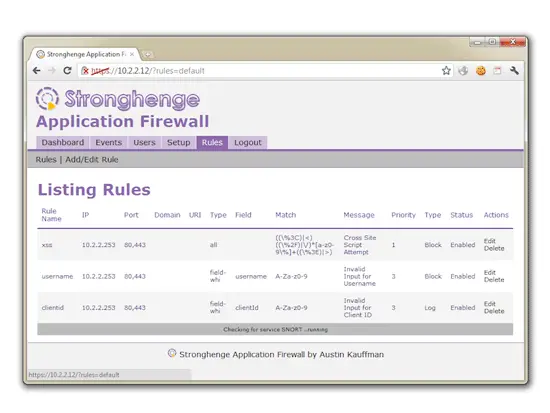
Configure rules:
This is where the power of this appliance can be realized. There are a couple of default rules to get you started.
Test rules:
SSL vs Non-SSL
Advanced Configuration:
Tweaking the promiscuous interface
Use ethtool to get get better RX performance. To find out the max the card can support issue the following command, put the correct interface for ethX:
ethtool -g ethX
Now set the max RX rate substituting the appropriate values for ethX and max_value.
ethtool -G ethX rx max_value
To automatically set the value on boot:
echo "ethtool -G ethX rx max_value" >> /etc/init.d/boot.local
Tweaking Snort
For high traffic environments add the following parameters to the existing options in: /etc/snort/snort.conf
preprocessor stream5_global: memcap 268435456 preprocessor stream5_tcp: max_queued_segs 1073741824, max_queued_bytes 1073741824