Server Monitoring With munin And monit - Page 2
This tutorial exists for these OS versions
- Debian 10 (Buster)
- Debian 8 (Jessie)
- Debian 7 (Wheezy)
- Debian 6 (Squeeze)
- 0
- Debian 3.1 (Sarge)
On this page
4 Install And Configure monit
To install monit, we do this:
apt-get install monit
Now we must edit /etc/monit/monitrc. The default /etc/monit/monitrc has lots of examples, and you can find more configuration examples on http://www.tildeslash.com/monit/doc/examples.php. However, in my case I want to monitor proftpd, sshd, mysql, apache, and postfix, I want to enable the monit web interface on port 2812, I want a https web interface, I want to log in to the web interface with the username admin and the password test, and I want monit to send email alerts to root@localhost, so my file looks like this:
vi /etc/monit/monitrc
set daemon 60 |
The configuration file is pretty self-explaining; if you are unsure about an option, take a look at the monit documentation: http://www.tildeslash.com/monit/doc/manual.php
In the apache part of the monit configuration you find this:
if failed host www.example.com port 80 protocol http |
which means that monit tries to connect to www.example.com on port 80 and tries to access the file /monit/token which is /var/www/www.example.com/web/monit/token because our web site's document root is /var/www/www.example.com/web. If monit doesn't succeed it means Apache isn't running, and monit is going to restart it. Now we must create the file /var/www/www.example.com/web/monit/token and write some random string into it:
mkdir /var/www/www.example.com/web/monit
echo "hello" > /var/www/www.example.com/web/monit/token
Next we create the pem cert (/var/certs/monit.pem) we need for the SSL-encrypted monit web interface:
mkdir /var/certs
cd /var/certs
We need an OpenSSL configuration file to create our certificate. It can look like this:
vi /var/certs/monit.cnf
# create RSA certs - Server |
Now we create the certificate like this:
openssl req -new -x509 -days 365 -nodes -config ./monit.cnf -out /var/certs/monit.pem -keyout /var/certs/monit.pem
openssl gendh 512 >> /var/certs/monit.pem
openssl x509 -subject -dates -fingerprint -noout -in /var/certs/monit.pem
chmod 700 /var/certs/monit.pem
Afterwards we edit /etc/default/monit to enable the monit daemon. Change startup to 1 and set CHECK_INTERVALS to the interval in seconds that you would like monit to check your system. I choose 60 (seconds) so my file looks like this:
vi /etc/default/monit
# Defaults for monit initscript |
Finally, we can start monit:
/etc/init.d/monit start
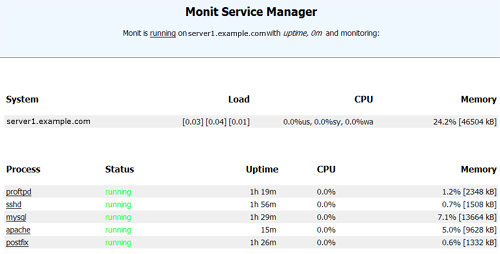
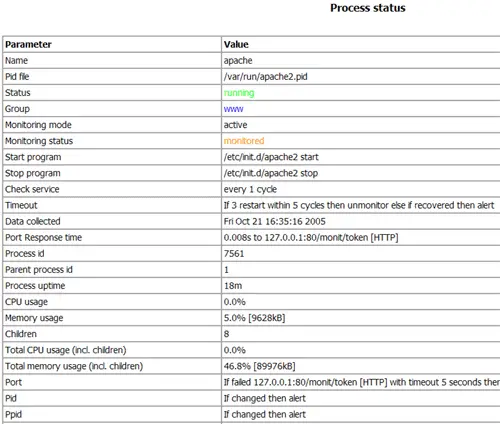
Now point your browser to https://www.example.com:2812/ (make sure port 2812 isn't blocked by your firewall), log in with admin and test, and you should see the monit web interface. It should look like this:
(Main Screen)
(Apache Status Page)
Depending on your configuration in /etc/monit/monitrc monit will restart your services if they fail and send notification emails if process IDs of services change, etc.
Have fun!