How to use Cloudformation to create a VPC on AWS
Using Cloudformation, we can create and manage AWS resources very easily. Cloudformation can be used to manage all AWS resources using a text file. Cloudformation allows us to create and model our infrastructure and applications without having to perform actions manually. Cloudformation helps us to manage our complete infrastructure in a text file, or template. Cloudformation template is a formatted text file in JSON or YAML language that describes our AWS infrastructure.
In this article, we will see a Cloudformation to create a VPC with 2 Public and 2 Private Subnets.
Pre-requisites
- AWS Account (Create if you don’t have one).
- Basic understanding of Cloudformation Templates.
What we will do?
- Login to AWS.
- Create a template.
- Create a Cloudformation Stack
Login to AWS
- Click here to go to AWS Login Page.
When we hit the above link, we will see a web page as follows where we are required to login using our login details.
Once we login into AWS successfully, we will see the main console with all the services listed as follows.
Create a template
Before we proceed with creating a stack, we should have a template that will be used to create a VPC. Copy the following code and save in on a local machine.
---
AWSTemplateFormatVersion: 2010-09-09
Description: >
This Templates creates a VPC with 3 public and 3 private subnets.
Parameters:
VpcCIDR:
Type: String
Description: VPC CIDR (Do Not Change if no customization is required).
Default: 10.10.0.0/16
PrivateAZ1SubnetCIDR:
Type: String
Description: Subnet CIDR for 1st Availability Zone (Do Not Change if no customization is required).
Default: 10.10.80.0/21
PrivateAZ2SubnetCIDR:
Type: String
Description: Subnet CIDR for 2nd Availability Zone (Do Not Change if no customization is required).
Default: 10.10.88.0/21
PrivateAZ3SubnetCIDR:
Type: String
Description: Subnet CIDR for 3rd Availability Zone (Do Not Change if no customization is required).
Default: 10.10.96.0/21
PublicAZ1SubnetCIDR:
Type: String
Description: Subnet CIDR for 1st Availability Zone (Do Not Change if no customization is required).
Default: 10.10.0.0/21
PublicAZ2SubnetCIDR:
Type: String
Description: Subnet CIDR for 2nd Availability Zone (Do Not Change if no customization is required).
Default: 10.10.8.0/21
PublicAZ3SubnetCIDR:
Type: String
Description: Subnet CIDR for 3rd Availability Zone (Do Not Change if no customization is required).
Default: 10.10.16.0/21
Metadata:
AWS::CloudFormation::Interface:
ParameterGroups:
- Label:
default: VPC
Parameters:
- VpcCIDR
- Label:
default: Availabilty Zone 1
Parameters:
- PublicAZ1SubnetCIDR
- PrivateAZ1SubnetCIDR
- Label:
default: Availabilty Zone 1
Parameters:
- PublicAZ2SubnetCIDR
- PrivateAZ2SubnetCIDR
- Label:
default: Availabilty Zone 1
Parameters:
- PublicAZ3SubnetCIDR
- PrivateAZ3SubnetCIDR
Resources:
Vpc:
Type: AWS::EC2::VPC
Properties:
CidrBlock: !Ref VpcCIDR
Tags:
- Key: Name
Value: !Sub ${AWS::StackName}
InternetGateway:
Type: AWS::EC2::InternetGateway
Properties:
Tags:
- Key: Name
Value: !Sub ${AWS::StackName}
VPCGatewayAttachment:
Type: AWS::EC2::VPCGatewayAttachment
Properties:
InternetGatewayId: !Ref InternetGateway
VpcId: !Ref Vpc
# Public Subnets - Route Table
PublicRouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref Vpc
Tags:
- Key: Name
Value: !Sub ${AWS::StackName}-public
- Key: Type
Value: public
PublicSubnetsRoute:
Type: AWS::EC2::Route
Properties:
RouteTableId: !Ref PublicRouteTable
DestinationCidrBlock: 0.0.0.0/0
GatewayId: !Ref InternetGateway
DependsOn: VPCGatewayAttachment
# Public Subnets
PublicAZ1Subnet:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref Vpc
CidrBlock: !Ref PublicAZ1SubnetCIDR
AvailabilityZone: !Select [0, !GetAZs ""]
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: !Sub
- ${AWS::StackName}-public-${AZ}
- { AZ: !Select [0, !GetAZs ""] }
- Key: Type
Value: public
PublicAZ1SubnetRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PublicAZ1Subnet
RouteTableId: !Ref PublicRouteTable
PublicAZ2Subnet:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref Vpc
CidrBlock: !Ref PublicAZ2SubnetCIDR
AvailabilityZone: !Select [1, !GetAZs ""]
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: !Sub
- ${AWS::StackName}-public-${AZ}
- { AZ: !Select [1, !GetAZs ""] }
- Key: Type
Value: public
PublicAZ2SubnetRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PublicAZ2Subnet
RouteTableId: !Ref PublicRouteTable
PublicAZ3Subnet:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref Vpc
CidrBlock: !Ref PublicAZ3SubnetCIDR
AvailabilityZone: !Select [2, !GetAZs ""]
MapPublicIpOnLaunch: true
Tags:
- Key: Name
Value: !Sub
- ${AWS::StackName}-public-${AZ}
- { AZ: !Select [2, !GetAZs ""] }
- Key: Type
Value: public
PublicAZ3SubnetRouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PublicAZ3Subnet
RouteTableId: !Ref PublicRouteTable
# Private Subnets - NAT Gateways
AZ1NatGatewayEIP:
Type: AWS::EC2::EIP
Properties:
Domain: vpc
DependsOn: VPCGatewayAttachment
AZ1NatGateway:
Type: AWS::EC2::NatGateway
Properties:
AllocationId: !GetAtt AZ1NatGatewayEIP.AllocationId
SubnetId: !Ref PublicAZ1Subnet
AZ2NatGatewayEIP:
Type: AWS::EC2::EIP
Properties:
Domain: vpc
DependsOn: VPCGatewayAttachment
AZ2NatGateway:
Type: AWS::EC2::NatGateway
Properties:
AllocationId: !GetAtt AZ2NatGatewayEIP.AllocationId
SubnetId: !Ref PublicAZ2Subnet
AZ3NatGatewayEIP:
Type: AWS::EC2::EIP
Properties:
Domain: vpc
DependsOn: VPCGatewayAttachment
AZ3NatGateway:
Type: AWS::EC2::NatGateway
Properties:
AllocationId: !GetAtt AZ3NatGatewayEIP.AllocationId
SubnetId: !Ref PublicAZ3Subnet
# Private Subnets
PrivateAZ1Subnet:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref Vpc
CidrBlock: !Ref PrivateAZ1SubnetCIDR
AvailabilityZone: !Select [0, !GetAZs ""]
Tags:
- Key: Name
Value: !Sub
- ${AWS::StackName}-private-${AZ}
- { AZ: !Select [0, !GetAZs ""] }
- Key: Type
Value: private
PrivateAZ1RouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref Vpc
Tags:
- Key: Name
Value: !Sub
- ${AWS::StackName}-private-${AZ}
- { AZ: !Select [0, !GetAZs ""] }
- Key: Type
Value: private
PrivateAZ1Route:
Type: AWS::EC2::Route
Properties:
RouteTableId: !Ref PrivateAZ1RouteTable
DestinationCidrBlock: 0.0.0.0/0
NatGatewayId: !Ref AZ1NatGateway
PrivateAZ1RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateAZ1Subnet
RouteTableId: !Ref PrivateAZ1RouteTable
PrivateAZ2Subnet:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref Vpc
CidrBlock: !Ref PrivateAZ2SubnetCIDR
AvailabilityZone: !Select [1, !GetAZs ""]
Tags:
- Key: Name
Value: !Sub
- ${AWS::StackName}-private-${AZ}
- { AZ: !Select [1, !GetAZs ""] }
- Key: Type
Value: private
PrivateAZ2RouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref Vpc
Tags:
- Key: Name
Value: !Sub
- ${AWS::StackName}-private-${AZ}
- { AZ: !Select [1, !GetAZs ""] }
- Key: Type
Value: private
PrivateAZ2Route:
Type: AWS::EC2::Route
Properties:
RouteTableId: !Ref PrivateAZ2RouteTable
DestinationCidrBlock: 0.0.0.0/0
NatGatewayId: !Ref AZ2NatGateway
PrivateAZ2RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateAZ2Subnet
RouteTableId: !Ref PrivateAZ2RouteTable
PrivateAZ3Subnet:
Type: AWS::EC2::Subnet
Properties:
VpcId: !Ref Vpc
CidrBlock: !Ref PrivateAZ3SubnetCIDR
AvailabilityZone: !Select [2, !GetAZs ""]
Tags:
- Key: Name
Value: !Sub
- ${AWS::StackName}-private-${AZ}
- { AZ: !Select [2, !GetAZs ""] }
- Key: Type
Value: private
PrivateAZ3RouteTable:
Type: AWS::EC2::RouteTable
Properties:
VpcId: !Ref Vpc
Tags:
- Key: Name
Value: !Sub
- ${AWS::StackName}-private-${AZ}
- { AZ: !Select [2, !GetAZs ""] }
- Key: Type
Value: private
PrivateAZ3Route:
Type: AWS::EC2::Route
Properties:
RouteTableId: !Ref PrivateAZ3RouteTable
DestinationCidrBlock: 0.0.0.0/0
NatGatewayId: !Ref AZ3NatGateway
PrivateAZ3RouteTableAssociation:
Type: AWS::EC2::SubnetRouteTableAssociation
Properties:
SubnetId: !Ref PrivateAZ3Subnet
RouteTableId: !Ref PrivateAZ3RouteTable
Outputs:
VpcId:
Description: VPC Id
Value: !Ref Vpc
Export:
Name: !Sub "${AWS::StackName}-VPC-ID"
Create a Cloudformation Stack
To create a Cloudformation Stack, click on “Services” in the top left and search for “Cloudformation”.
On the main dashboard, click on “Create stack” -> "With new resorces(standard)".
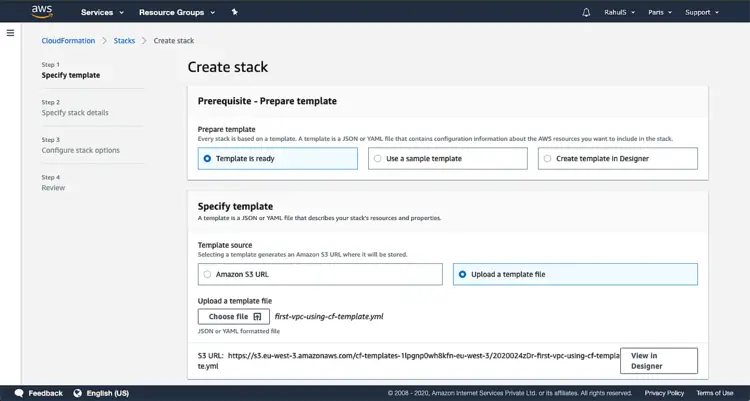
The stack needs a template file which can be a local file or an object file in the S3 Bucket. Since we will be having a local template, click on “Template is ready” -> “Upload a template file”, click on “Choose file” and select the local template file and proceed further.
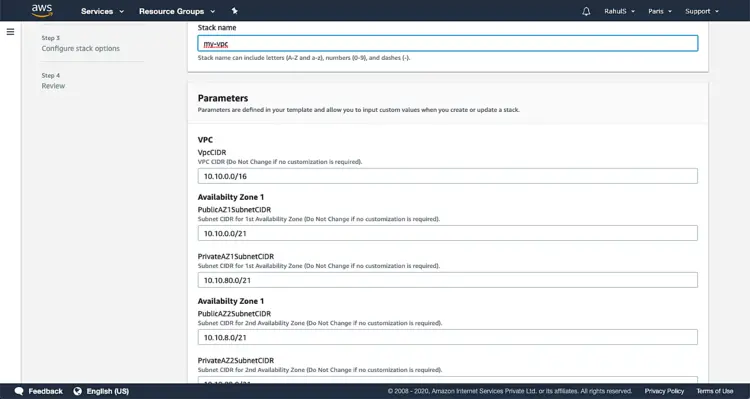
Give a name to the stack, keep all other parameters unchanged.
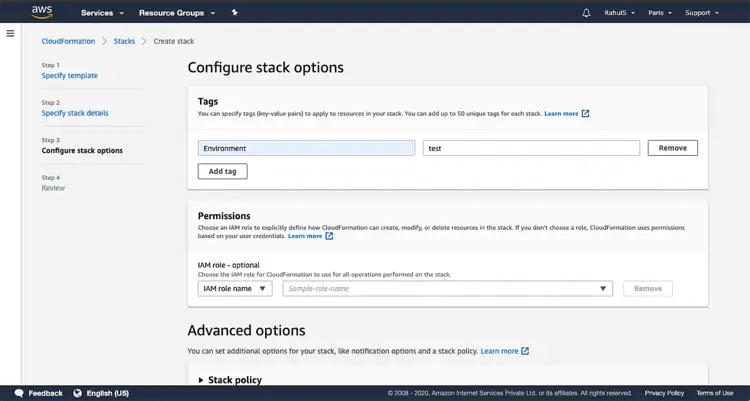
Give Tags if required.
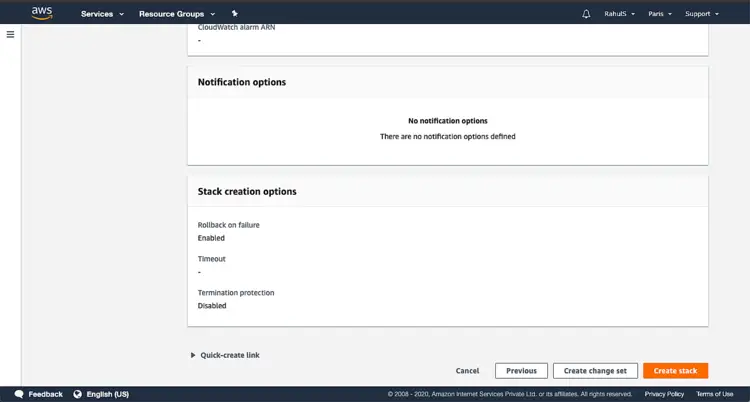
Scroll down the page and click on “Create stack”
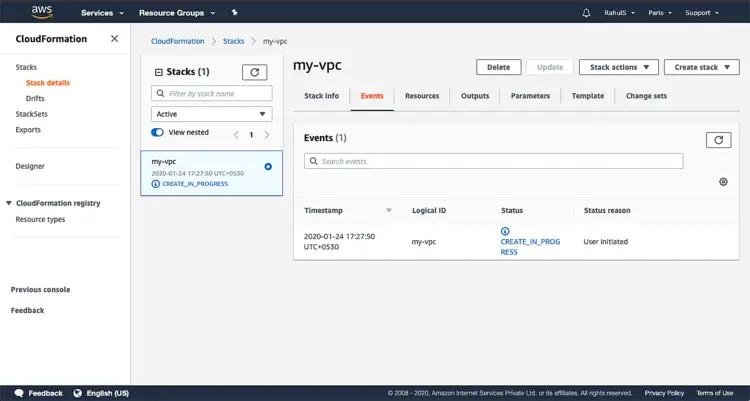
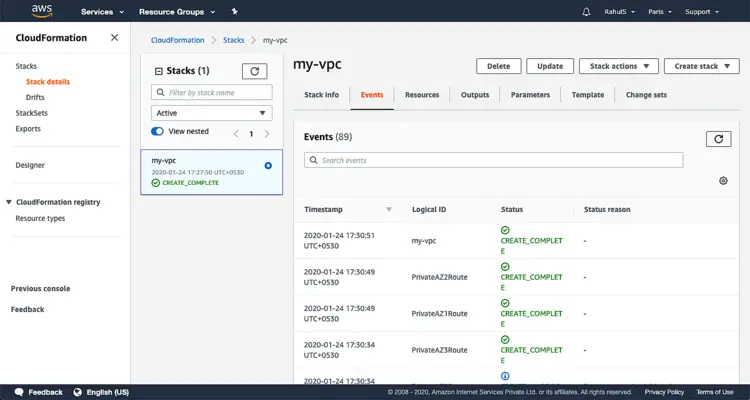
This will take some time, wait till then.
You can see the status or event taking place under “Events” tab.
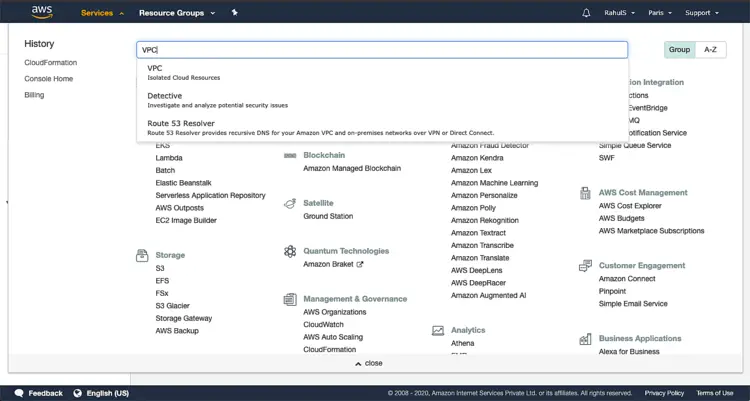
Now, you can go to VPC and check for the VPC that got created. To go to VPC, click on “Services” at the top and left search for VPC.
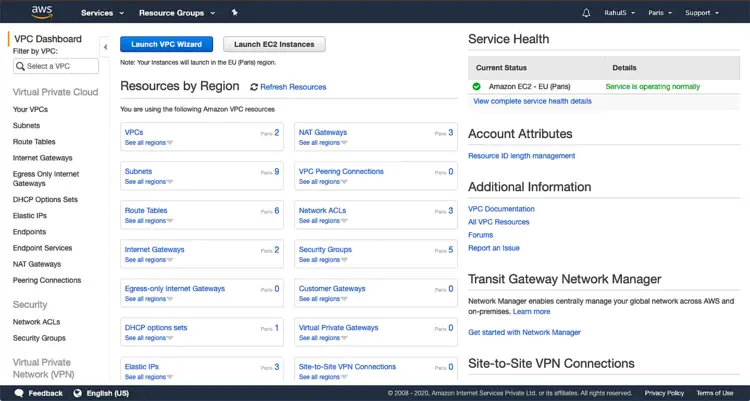
In the main dashboard, you can see the number of VPC, Subnets, Route Tables, Internet Gateway, Nat Gateway which got created.
You can delete the VPC by just deleting the Stack if you no more need it.
Conclusion
In this article, we saw the steps to create a Cloudformation Stack to create a VPC with 2 Public and 2 Private Subnet.