How to Install and Use SFTP on Linux Servers
SFTP or SSH File Transfer Protocol is a method for securely transferring data between two computers and more. It's FTP that runs on top of SSH protocol and takes advantage of its security, and fully supports its authentication.
Today, it's recommended that SFTP be used instead of legacy FTP or FTP/S protocol. SFTP is secure by default because that is how SSH works. From a security standpoint, SFTP also protects you against password sniffing and man-in-the-middle attack (MiTM).
Just like SSH, SFTP protects data integrity using encryption and cryptographic hash function. It also supports multiple secure authentication methods, including password and key-based authentication. Also, it reduces the server's open port to the outside network because it's run on the same port as the SSH protocol.
Prerequisites
In this guide, you will learn how to set up SFTP Server on a Linux system. Also, you'll learn the basic command of the sftp client.
Below is the current environment for the implementation:
- A Linux Server - you can use Debian, Ubuntu, CentOS, Fedora, Rocky, or any other Linux distribution.
- Make sure OpenSSH packages are available on your Linux system.
- SFTP client - sftp command-line or any GUI client as you preferred.
Verify OpenSSH Packages
To set up an SFTP server, OpenSSH packages must be installed on your Linux system. Almost all Linux distribution servers have the OpenSSH packages installed by default. But, in case you don't have the OpenSSH package on your system, you can install it from the official repository.
1. To make sure that OpenSSH packages are installed on your Linux system, use the following command.
For Debian or Ubuntu servers, you can use the dpkg command below.
dpkg -l | grep ssh
Below is the output from our Debian system.
ii libssh2-1:amd64 1.9.0-2 amd64 SSH2 client-side library
ii openssh-client 1:8.4p1-5 amd64 secure shell (SSH) client, for secure access to remote machines
ii openssh-server 1:8.4p1-5 amd64 secure shell (SSH) server, for secure access from remote machines
ii openssh-sftp-server 1:8.4p1-5 amd64 secure shell (SSH) sftp server module, for SFTP access from remote machines
The first column 'ii' means the package is installed. The package 'openssh-sftp-server' is installed on the Debian/Ubuntu system.
You can use the rpm command below for RHEL/CentOS/Fedora/Rocky Linux/AlmaLinux users.
rpm -qa | grep ssh
Create Group and User
At this step, you will create a new group and user for the SFTP server. Users within this group will be allowed to access the SFTP server. For security reasons, SFTP users cannot access the SSH service; they can only access the SFTP server.
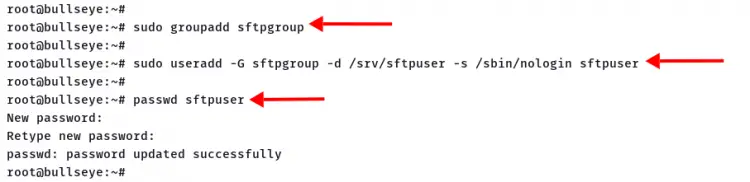
1. Execute the following command to create a new group 'sftpgroup'.
sudo groupadd sftpgroup
2. Create a new user 'sftpuser' using the following command.
sudo useradd -G sftpgroup -d /srv/sftpuser -s /sbin/nologin sftpuser
Detailed options:
- -G : automatically add the user to the 'sftpgroup'.
- -d : specify the home directory for the new user.
- -s : set the default for the new user to '/sbin/nologin', which means the user cannot access the SSH Server.
3. Next, create the password for user 'sftpuser' using the command below.
passwd sftpuser
Type your strong password and repeat, then press 'Enter' to confirm.
To add more users, repeat stages number 2 and 3, and most importantly, all SFTP users must be in the group 'sftpgroup' with no shell access through SSH.
Setup Chroot Jail Directory
After creating a new group and user, you must create and configure the chroot directory for SFTP users.
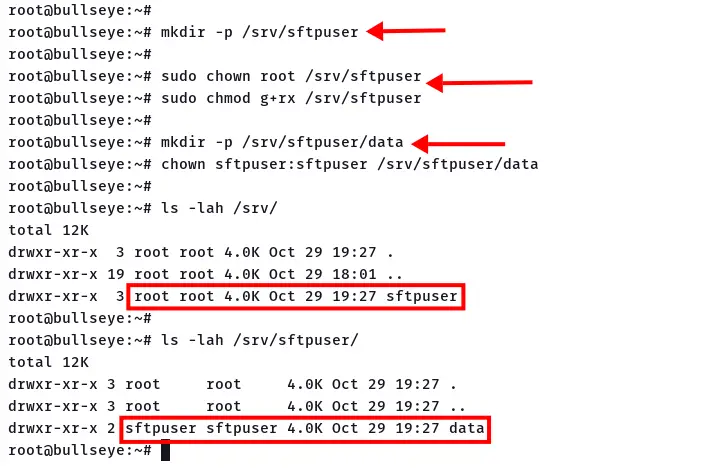
1. For the user 'sftpuser', the new home directory will be at the '/srv/sftpuser'. Execute the command below to create it.
mkdir -p /srv/sftpuser
2. To set up chroot for user 'sftpuser', you must change the ownership of the directory to the user root, but remain the group to read and execute without write access.
Change the ownership of the directory to user 'root' using the following command.
sudo chown root /srv/sftpuser
Give the group permission to read and execute, but not to write.
sudo chmod g+rx /srv/sftpuser
3. Next, create a new 'data' directory inside the '/srv/sftpuser' directory and change the ownership of that 'data' directory to the user 'sftpuser'.
mkdir -p /srv/sftpuser/data
chown sftpuser:sftpuser /srv/sftpuser/data
So far, below details configuration for the SFTP user directory.
- The directory '/srv/sftuser' is the default home directory.
- The user 'sftpuser' cannot write to the directory '/srv/sftpuser', but can read inside that directory.
- The user 'sftpuser' can upload files to the SFTP server at the directory '/srv/sftpuser/data'.
Enable SFTP on SSH Server
To enable the SFTP server on the OpenSSH, you must edit the SSH configuration '/etc/ssh/sshd_config'.
1. Edit the ssh configuration '/etc/ssh/sshd_config' using nano or vim.
sudo nano /etc/ssh/sshd_config
2. Comment the following configuration to disable the standalone 'sftp-server' feature.
#Subsystem sftp /usr/lib/openssh/sftp-server
3. Paste the following configuration to the bottom of the line.
Subsystem sftp internal-sftp
Match Group sftpgroup
ChrootDirectory %h
X11Forwarding no
AllowTCPForwarding no
ForceCommand internal-sftp
Save the configuration and exit.
Detailed configuration:
- Instead of using the sub-process 'sftp-server', we're using the 'internal-sftp'.
- The SFTP server enabled for group 'sftpgroup'.
4. To apply a new configuration, restart the ssh service using the command below.
sudo systemctl restart sshd
The SFTP server is ready and accessible, and it's running on the same port as the SSH service.
Access the SFTP Server
On the client-side, we will use the sftp command line, which is installed by default on most Linux Distributions. But, you can also be using another command-line client or GUI FTP client such as FileZilla, Cyberduck, etc.
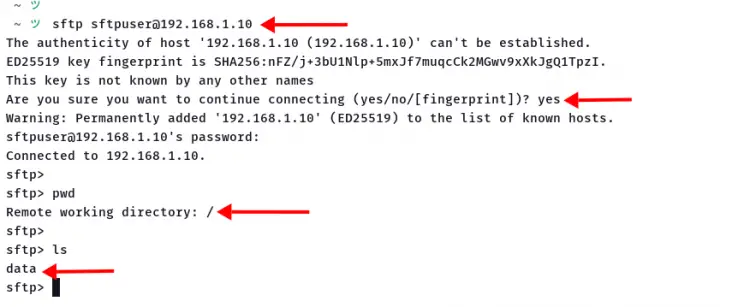
1. To connect to the SFTP server, execute the sftp command as below.
sftp ftpuser@SERVER-IP
If your SFTP and/or SSH server running on the custom port, you can use the sftp command as below.
sftp -P PORT ftpuser@SERVER-IP
Type the password for the 'sftpuser'.
2. Once you are connected to the SFTP server, execute the following command.
Show current path working directory and list all available files and directories.
pwd
ls
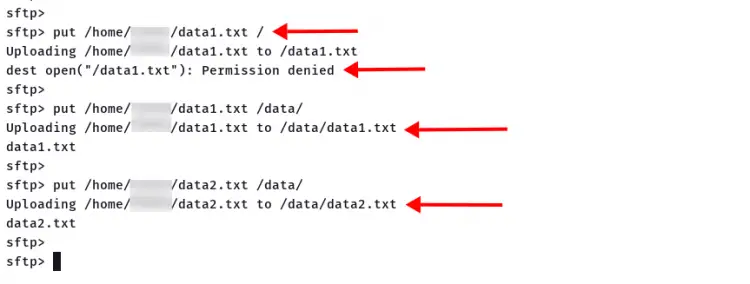
3. Upload a local file to the SFTP server on the directory '/', which will result as 'permission denied', because it's the chroot directory.
put /path/to/file/on/local /
4. Upload a local file to the directory '/data/' on the SFTP server. If your configuration is correct, your file will be uploaded to the '/data/' directory.
put /path/to/file1/on/local1 /data/
put /path/to/file2/on/local /data/
5. Now check available files on the '/data' directory using the following command.
ls /data/
And you will see your file uploaded to the SFTP server.
Conclusion
Congratulations! You've successfully configured the SFTP Server on the Linux system. This type of configuration can be applied on most Linux systems with OpenSSH installed on top of it. Also, you've learned how to set up the chroot directory for SFTP users and learned the basic sftp client command.