How To Set Up SSL Vhosts Under Nginx + SNI Support (Ubuntu 11.04/Debian Squeeze) - Page 3
8 Configure Firefox To Trust CAcert.org (Optional)
If you use a CAcert.org certificate, your browser most likely doesn't trust this certificate and will show a warning. This chapter explains how you can import the CAcert.org root certificate into Firefox so that it won't show this warning anymore (please read http://wiki.cacert.org/BrowserClients for other browsers like MSIE, Safari or Opera).
Please note that if you run an e-commerce web site, you should better buy a certificate from a trusted CA because you can't ask all your visitors to reconfigure their browsers.
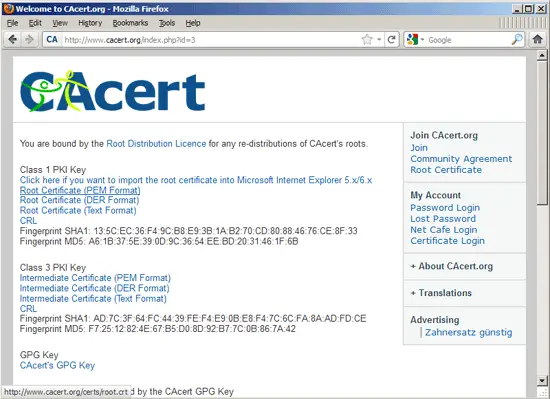
Please visit http://www.cacert.org/index.php?id=3 and click on the Root Certificate (PEM Format) link (http://www.cacert.org/certs/root.crt):
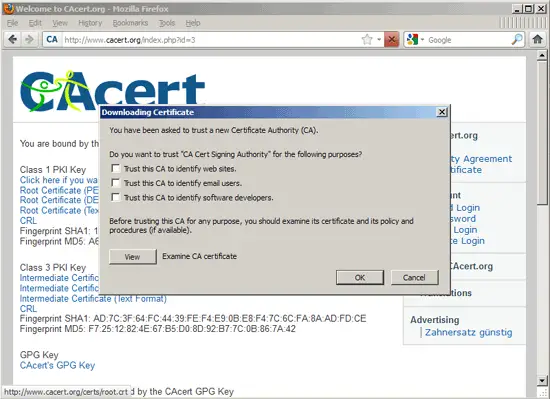
The Downloading Certificate dialogue opens. Click on View to examine the certificate:
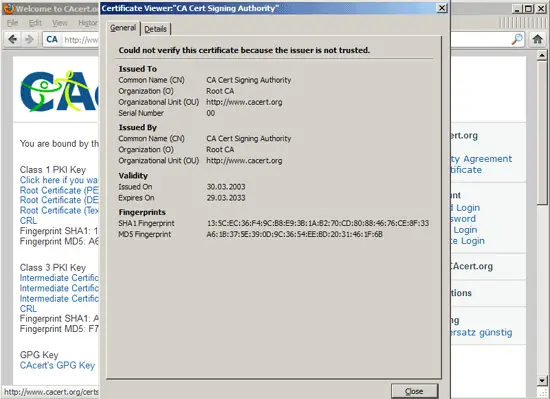
Please make sure that the fingerprints are as follows:
SHA1 Fingerprint: 135C EC36 F49C B8E9 3B1A B270 CD80 8846 76CE 8F33
MD5 Fingerprint: A6:1B:37:5E:39:0D:9C:36:54:EE:BD:20:31:46:1F:6B
Click on Close afterwards:
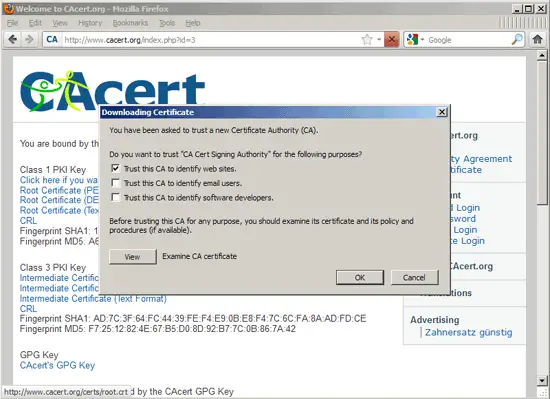
Next check Trust this CA to identify web sites. and click on OK:
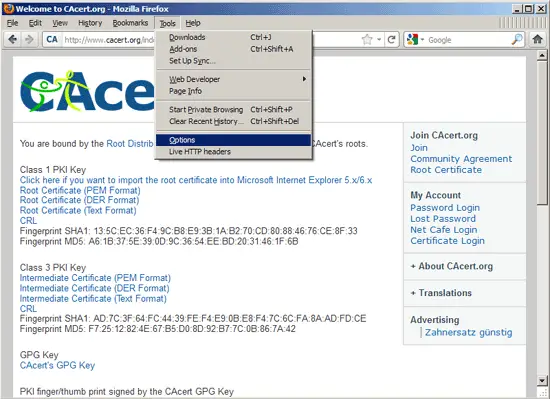
Now go to Tools > Options...
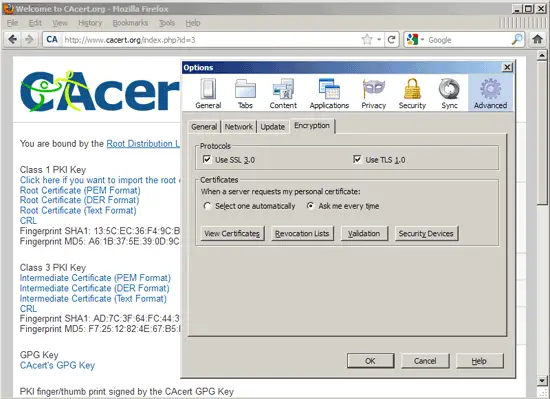
... and then to Advanced > Encryption. Click on Revocation Lists:
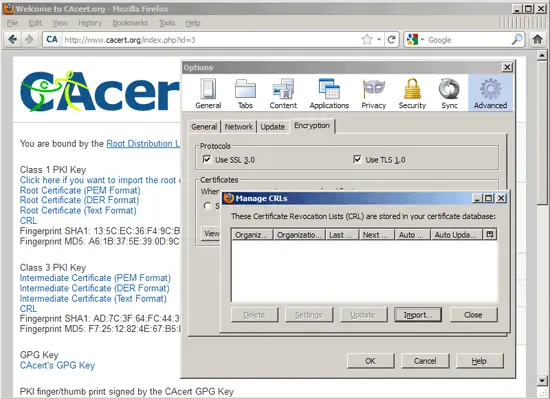
The Manage CRLs window opens. Click on Import...:
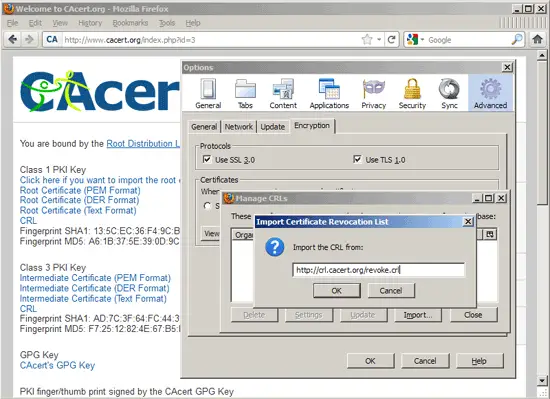
Fill in the following URL and click on OK: http://crl.cacert.org/revoke.crl
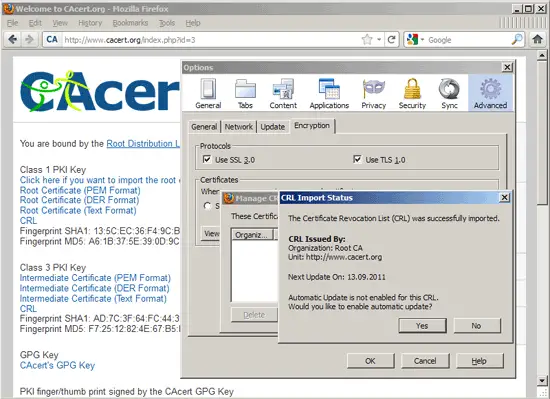
After a few moments you should see the following message. Click on Yes to enable automatic updates:
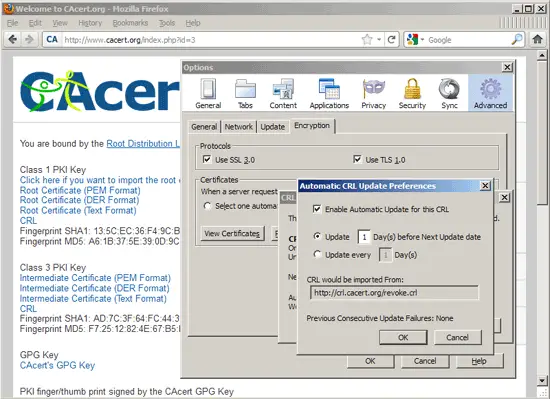
Check Enable Automatic Update for this CRL and click on OK:
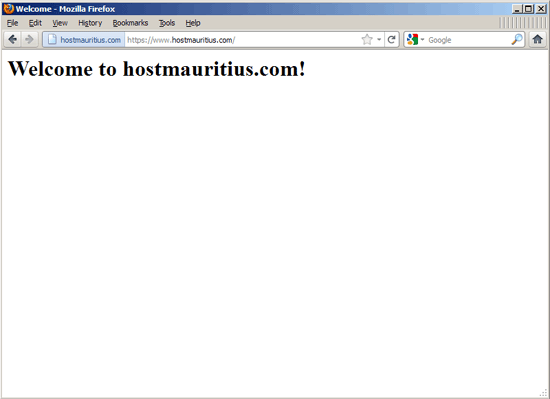
That's it. You should now be able to go to your SSL vhost without getting a browser warning:
9 Running Multiple SSL Vhosts On One IP Address With SNI (Server Name Indication)
Please note that currently SNI is not supported by all browsers/operating systems:
Browsers/clients with support for TLS server name indication:
- Opera 8.0 and later (the TLS 1.1 protocol must be enabled)
- Internet Explorer 7 or later (under Windows Vista and later only, not under Windows XP)
- Firefox 2.0 or later
- Curl 7.18.1 or later (when compiled against an SSL/TLS toolkit with SNI support)
- Chrome 6.0 or later (on all platforms - releases up to 5.0 only on specific OS versions)
- Safari 3.0 or later (under OS X 10.5.6 or later and under Windows Vista and later)
To find out if your browser supports SNI, you can go to https://alice.sni.velox.ch/.
If your nginx supports SNI, you don't need any special configuration to use it - you just configure a second, third, ... SSL vhost on the same IP as shown in chapter 5.
To find out if your nginx supports SNI, run:
nginx -V
If it does, you will see the line TLS SNI support enabled in the output:
root@server1:~# nginx -V
nginx version: nginx/0.8.54
TLS SNI support enabled
configure arguments: --conf-path=/etc/nginx/nginx.conf --error-log-path=/var/log/nginx/error.log --http-client-body-temp-path=/var/lib/nginx/body --http-fastcgi-temp-path=/var/lib/nginx/fastcgi --http-log-path=/var/log/nginx/access.log --http-proxy-temp-path=/var/lib/nginx/proxy --http-scgi-temp-path=/var/lib/nginx/scgi --http-uwsgi-temp-path=/var/lib/nginx/uwsgi --lock-path=/var/lock/nginx.lock --pid-path=/var/run/nginx.pid --with-debug --with-http_addition_module --with-http_dav_module --with-http_geoip_module --with-http_gzip_static_module --with-http_image_filter_module --with-http_realip_module --with-http_stub_status_module --with-http_ssl_module --with-http_sub_module --with-http_xslt_module --with-ipv6 --with-sha1=/usr/include/openssl --with-md5=/usr/include/openssl --with-mail --with-mail_ssl_module --add-module=/build/buildd/nginx-0.8.54/debian/modules/nginx-upstream-fair
root@server1:~#
I can now simply create another SSL host (this time for www.hostmauritius.net) as follows:
vi /etc/nginx/sites-available/www.hostmauritius.net.vhost
If you use nginx >= 0.8.21:
server {
listen 80; ## listen for ipv4
listen [::]:80; ## listen for ipv6
listen 443 ssl;
listen [::]:443 ssl;
ssl_certificate /etc/ssl/certs/www.hostmauritius.net.pem;
ssl_certificate_key /etc/ssl/private/www.hostmauritius.net.key;
server_name www.hostmauritius.net hostmauritius.net;
root /var/www/www.hostmauritius.net/web;
if ($http_host != "www.hostmauritius.net") {
rewrite ^ $scheme://www.hostmauritius.net$request_uri permanent;
}
location / {
index index.php index.html index.htm;
}
location ~ \.php$ {
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME /var/www$fastcgi_script_name;
include fastcgi_params;
}
location ~ /\. {
deny all;
}
}
|
If you use nginx < 0.8.21:
server {
listen 80; ## listen for ipv4
listen [::]:80; ## listen for ipv6
listen 443;
listen [::]:443;
ssl_certificate /etc/ssl/certs/www.hostmauritius.net.pem;
ssl_certificate_key /etc/ssl/private/www.hostmauritius.net.key;
server_name www.hostmauritius.net hostmauritius.net;
root /var/www/www.hostmauritius.net/web;
if ($http_host != "www.hostmauritius.net") {
rewrite ^ $scheme://www.hostmauritius.net$request_uri permanent;
}
location / {
index index.php index.html index.htm;
}
location ~ \.php$ {
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME /var/www$fastcgi_script_name;
include fastcgi_params;
}
location ~ /\. {
deny all;
}
}
|
(Make sure that you create the certificate and the private key as shown in chapters 4, 6, and 7. You might also have to append a chain file or intermediate certificate to the certificate for this vhost, as described in chapter 7.1. Also, if this is a new vhost, make sure its document root exists.)
If this is a new vhost, you must create a link to it from the /etc/nginx/sites-enabled/ directory to enable it:
cd /etc/nginx/sites-enabled/
ln -s /etc/nginx/sites-available/www.hostmauritius.net.vhost www.hostmauritius.net.vhost
Reload nginx afterwards:
/etc/init.d/nginx reload
If all goes well, you can now go to all your SSL sites which run on the same IP without getting a browser warning.
10 Links
- nginx: http://nginx.org/
- nginx Wiki: http://wiki.nginx.org/
- OpenSSL: http://www.openssl.org/
- CACert.org: http://www.cacert.org/
- Ubuntu: http://www.ubuntu.com/
- Debian: http://www.debian.org/
About The Author

Falko Timme is the owner of ![]() Timme Hosting (ultra-fast nginx web hosting). He is the lead maintainer of HowtoForge (since 2005) and one of the core developers of ISPConfig (since 2000). He has also contributed to the O'Reilly book "Linux System Administration".
Timme Hosting (ultra-fast nginx web hosting). He is the lead maintainer of HowtoForge (since 2005) and one of the core developers of ISPConfig (since 2000). He has also contributed to the O'Reilly book "Linux System Administration".