How to manage AWS IAM using aws-cli
Managing IAM Users, Groups, and Roles from your terminal is easy and interesting, you just need to execute the commands to achieve the task. In this article, we will see the commands to create Users, Groups, and Roles. We will also see commands to attach and detach policies to the IAM user, group, and role we create. This guide will help you get started with managing IAM resources from the terminal.
Before we proceed, it is assumed that you are familiar with IAM Users, Groups, Roles, Policies.
A few of the commands that we have covered in this article are as follows.
- list-users: Get a list of existing users.
- list-groups: Get a list of existing groups.
- list-roles: Get a list of existing roles.
- create-user: Create a new user.
- create-group: Create a new group.
- create-role: Create a new role.
- add-user-to-group: Add a user to the existing group.
- get-group: Get a list of users that are there in the group
- attach-user-policy: Attach the managed policy to the existing user.
- attach-group-policy: Attach the managed policy to the existing group.
- attach-role-policy: Attach the managed policy to the existing role.
- list-attached-user-policies: List policies attached to the user.
- list-attached-group-policies: List policies attached to the group.
- list-attached-role-policies: List policies attached to the role.
- detach-user-policy: Remove the managed policy from the existing user.
- detach-group-policy: Remove the managed policy from the existing group.
- detach-user-policy: Remove the managed policy from the existing role.
- remove-user-from-group: Remove a user from the groups
- delete-user: Delete an IAM user.
- delete-group: Delete an IAM group.
- delete-role: Delete an IAM role
Visit the official AWS documentation here to know all the aws-cli commands for IAM.
Pre-requisites
- AWS Account (Create if you don’t have one).
- Basic understanding of IAM (Click here to learn to create an IAM user, group, role from the AWS Console).
- AWS IAM user with AdministratorAccess policy attached to it and its access and secret keys (Click here to learn to create an IAM User).
- AWS CLI installed on your local machine.
What will we do?
- Check aws cli and export the AWS access & secret key on your local machine.
- Manage IAM using aws-cli
Check aws cli and export the AWS access & secret key on your local machine.
Check if you have aws-cli installed on your local machine.
aws --version #aws-cli/2.0.0 Python/3.8.2 Darwin/19.2.0 botocore/2.0.0dev7
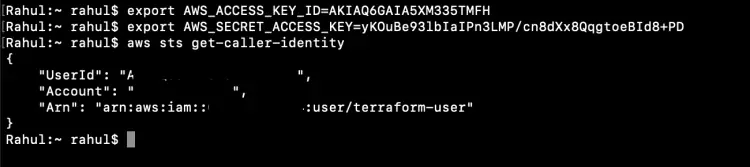
The next step is to export your AWS user access and secret key in your terminal. The keys will be different for you, do not use the ones mentioned below.
export AWS_ACCESS_KEY_ID=<your-iam-user-access-key-here>
export AWS_SECRET_ACCESS_KEY=<your-iam-user-secret-key-here>
Execute the following command to check the identity of the user you exported keys of.
aws sts get-caller-identity
Manage IAM using aws-cli
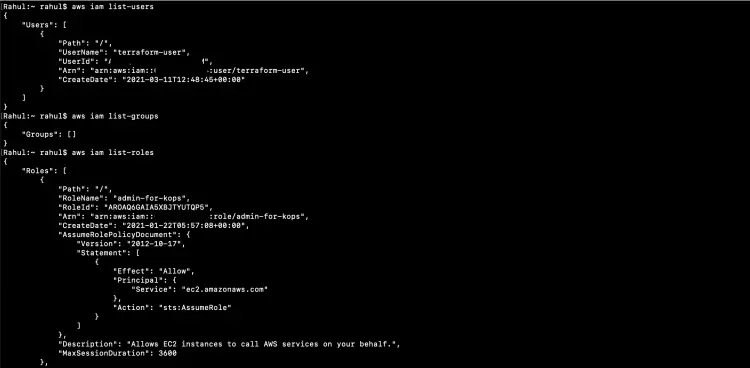
To get started with IAM, let's first check existing IAM users, groups, and roles in the account.
aws iam list-users
aws iam list-groups
aws iam list-roles
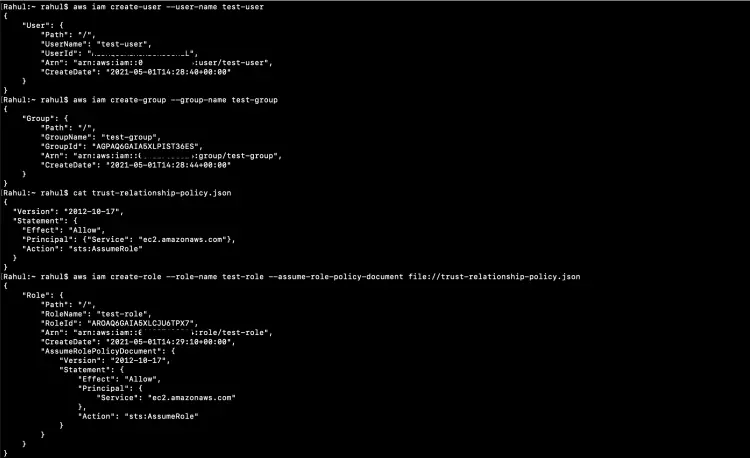
To create an IAM User execute the following command.
aws iam create-user --user-name test-user
Let's create an IAM Group.
aws iam create-group --group-name test-group
While creating a role, we also need to attach a trust relationship. For this, we need a policy.
Create a file on your local system with the following content, name the file as "trust-relationship-policy.json". The following policy allows EC2 service to assume the role.
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Principal": {"Service": "ec2.amazonaws.com"},
"Action": "sts:AssumeRole"
}
}
Now, we are ready to create an IAM role.
aws iam create-role --role-name test-role --assume-role-policy-document file://trust-relationship-policy.json
Till this point, we have an IAM User, Group, and Role.
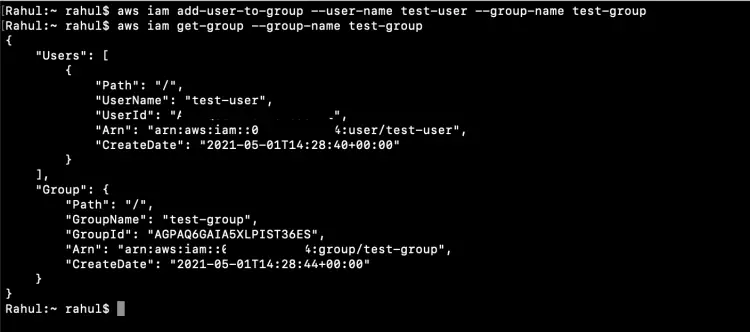
We can now add a user to the group we created using the following command.
aws iam add-user-to-group --user-name test-user --group-name test-group
Check details of the group after adding the user to it.
aws iam get-group --group-name test-group
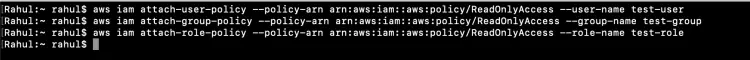
Let's add the "ReadOnlyAccess" policy to the User, Group, and Role we created.
aws iam attach-user-policy --policy-arn arn:aws:iam::aws:policy/ReadOnlyAccess --user-name test-user
aws iam attach-group-policy --policy-arn arn:aws:iam::aws:policy/ReadOnlyAccess --group-name test-group
aws iam attach-role-policy --policy-arn arn:aws:iam::aws:policy/ReadOnlyAccess --role-name test-role
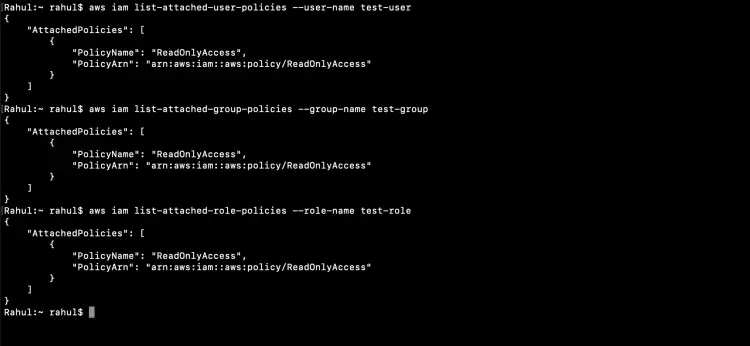
Verify if the policy was added to the user, Group and Role.
aws iam list-attached-user-policies --user-name test-user
aws iam list-attached-group-policies --group-name test-group
aws iam list-attached-role-policies --role-name test-role
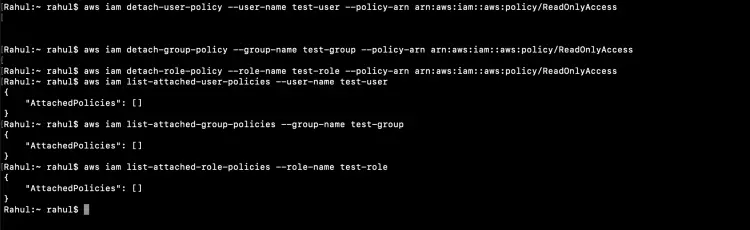
The way we added a policy to the User, Group, and Role, we can also detach it.
To detach a policy we need to pass its arn to the command.
aws iam detach-user-policy --user-name test-user --policy-arn arn:aws:iam::aws:policy/ReadOnlyAccess
aws iam detach-group-policy --group-name Testers --policy-arn arn:aws:iam::aws:policy/ReadOnlyAccess
aws iam detach-group-policy --group-name test-group --policy-arn arn:aws:iam::aws:policy/ReadOnlyAccess
aws iam detach-role-policy --role-name test-role --policy-arn arn:aws:iam::aws:policy/ReadOnlyAccess
After detaching the policy, we can make sure that the policy is no more attached to the User, Group and Role.
aws iam list-attached-user-policies --user-name test-user
aws iam list-attached-group-policies --group-name test-group
aws iam list-attached-role-policies --role-name test-role
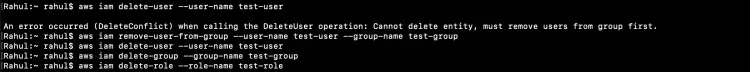
If we no longer need the User, Group and Role we created, we can delete them by executing the following command.
aws iam delete-user --user-name test-user
Make a note that, before you delete a User, you need to remove it from the Group it was added to.
aws iam remove-user-from-group --user-name test-user --group-name test-group
aws iam delete-user --user-name test-user
aws iam delete-group --group-name test-group
aws iam delete-role --role-name test-role
Conclusion
In this article, we saw the command to manage IAM User, Group, and Role. We first created these IAM resources and then added IAM managed policies to them. We also saw how policies can be detached from the user, Group and Role. Later, we also saw the command to delete the IAM resources we created. You can now try other commands and manage IAM using aws-cli.