How to Install Wekan Kanban with Nginx and Let's Encrypt SSL on Debian 10
Wekan is a free and open-source Kanban Board built with the Meteor JavaScript framework and is distributed under the MIT license. It is very similar to Workflowy and Trello that helps you to manage day-to-day tasks, prepare todo lists, managing other people, etc. It comes with a fully responsive web interface and translated into many languages. Wekan comes with a rich set of features including, Export Wekan board, Import Trello board, SMTP Settings, Restore an archived board, User management module, Drag and drop functions, and many more.
In this tutorial, we will show you how to install Wekan Kanban board with Nginx as a proxy server on Debian 10.
Prerequisites
- A server running Debian 10.
- A valid domain name pointed with your server IP.
- A root password is configured on your server.
Getting Started
Before starting, it is recommended to update your server with the latest version using the following command:
apt-get update -y
apt-get upgrade -y
Once your server is updated, restart it to implement the changes.
Install Wekan
The easiest way to install the Wekan on Debian 10 is by using snap. By default, the snap package is available in the Debian 10 repository. You can install it by running the following command:
apt-get install snapd -y
Once the snap is in/stalled, you can install the Wekan by running the following command:
snap install wekan
Once the Wekan is installed, it will start Wekan and Mongodb service automatically.
You can see the status of the Wekan service with the following command:
systemctl status snap.wekan.wekan
You should see the following output:
? snap.wekan.wekan.service - Service for snap application wekan.wekan
Loaded: loaded (/etc/systemd/system/snap.wekan.wekan.service; enabled; vendor preset: enabled)
Active: active (running) since Sun 2019-12-22 07:43:34 UTC; 7s ago
Main PID: 7836 (wekan-control)
Tasks: 11 (limit: 2359)
Memory: 156.3M
CGroup: /system.slice/snap.wekan.wekan.service
??7836 /bin/bash /snap/wekan/678/bin/wekan-control
??8522 /snap/wekan/678/bin/node main.js
Dec 22 07:43:35 debian10 wekan.wekan[7836]: HEADER_LOGIN_EMAIL=Header login email. Example for siteminder: HEADEREMAILADDRESS (default value)
Dec 22 07:43:35 debian10 wekan.wekan[7836]: LOGOUT_WITH_TIMER=false (default value)
Dec 22 07:43:35 debian10 wekan.wekan[7836]: LOGOUT_IN= (default value)
Dec 22 07:43:35 debian10 wekan.wekan[7836]: LOGOUT_ON_HOURS= (default value)
Dec 22 07:43:35 debian10 wekan.wekan[7836]: LOGOUT_ON_MINUTES= (default value)
Dec 22 07:43:35 debian10 wekan.wekan[7836]: DEFAULT_AUTHENTICATION_METHOD= (default value)
Dec 22 07:43:35 debian10 wekan.wekan[7836]: ATTACHMENTS_STORE_PATH= (default value)
Dec 22 07:43:35 debian10 wekan.wekan[7836]: MONGO_URL=mongodb://127.0.0.1:27019/wekan
Dec 22 07:43:37 debian10 wekan.wekan[7836]: Presence started serverId=ijqY8RbEWv8Hg9RSb
Dec 22 07:43:38 debian10 wekan.wekan[7836]: Meteor APM: completed instrumenting the app
By default, Wekan runs on the port 8080. If you want to change the Wekan port to 3001, run the following command:
snap set wekan port='3001'
Next, restart Wekan and MongoDB service to apply the changes:
systemctl restart snap.wekan.mongodb
systemctl restart snap.wekan.wekan
Manage Wekan and MongoDB Services
To start and stop Wekan service, run the following command:
systemctl stop snap.wekan.wekan
systemctl start snap.wekan.wekan
To start and stop MongoDB service, run the following command:
systemctl stop snap.wekan.mongodb
systemctl start snap.wekan.mongodb
Configure Nginx as a Reverse Proxy
Wekan is now installed and listening on the port 3001. Next, it is a good idea to run Wekan behind the Nginx proxy.
To do so, first install the Nginx web server using the following command:
apt-get install nginx -y
Once installed, open the /etc/nginx/nginx.conf file and set hash_bucket_size:
nano /etc/nginx/nginx.conf
Uncomment the following line:
server_names_hash_bucket_size 64;
Save and close the file when you are finished. Then, restart the Nginx service to apply the changes:
systemctl restart nginx
Next, create an Nginx virtual host file for Wekan as shown below:
nano /etc/nginx/conf.d/wekan.conf
Add the following lines:
map $http_upgrade $connection_upgrade {
default upgrade;
'' close;
}
server {
listen 80;
server_name wekan.linuxbuz.com;
if ($http_user_agent ~ "MSIE" ) {
return 303 https://browser-update.org/update.html;
}
location / {
proxy_pass http://127.0.0.1:3001;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade; # allow websockets
proxy_set_header Connection $connection_upgrade;
proxy_set_header X-Forwarded-For $remote_addr; # preserve client IP
}
}
Save and close the file when you are finished. Then, check the Nginx for any syntax error with the following command:
nginx -t
You should see the following output:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful
Finally, restart the Nginx service to apply the changes:
systemctl restart nginx
At this point, Nginx is configured to forward the request to Wekan port 3001.
Secure Wekan with Let's Encrypt Free SSL
Next, it is recommended to secure the Wekan with Let's Encrypt free SSL. To do so, you will need to install the Certbot client on your server. Certbot is a Let's Encrypt client that can be used to download free SSL and configure Nginx to use this certificate.
By default, the latest version of Certbot is not available in the Debian 10 default repository. So, you will need to add the Certbot repository on your server.
You can add the repository using the following command:
echo "deb http://ftp.debian.org/debian buster-backports main" >> /etc/apt/sources.list
Next, update the repository and install the Certbot client with the following command:
apt-get update -y
apt-get install python-certbot-nginx -t buster-backports
Once the installation has been completed, run the following command to obtain and install the SSL certificate for your domain:
certbot --nginx -d wekan.linuxbuz.com
You will be asked to provide your email address and accept the term of service as shown below:
Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator nginx, Installer nginx Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): [email protected] - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v02.api.letsencrypt.org/directory - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (A)gree/(C)ancel: A - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: N Obtaining a new certificate Performing the following challenges: http-01 challenge for wekan.linuxbuz.com Waiting for verification... Cleaning up challenges Deploying Certificate to VirtualHost /etc/nginx/conf.d/wekan.conf
Next, you will need to choose whether or not to redirect HTTP traffic to HTTPS:
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Type 2 and hit Enter to start the installation process. Once the installation has been finished, you should get the following output:
Redirecting all traffic on port 80 to ssl in /etc/nginx/conf.d/wekan.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations! You have successfully enabled https://wekan.linuxbuz.com You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=wekan.linuxbuz.com - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/wekan.linuxbuz.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/wekan.linuxbuz.com/privkey.pem Your cert will expire on 2020-03-25. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
Access Wekan Web Interface
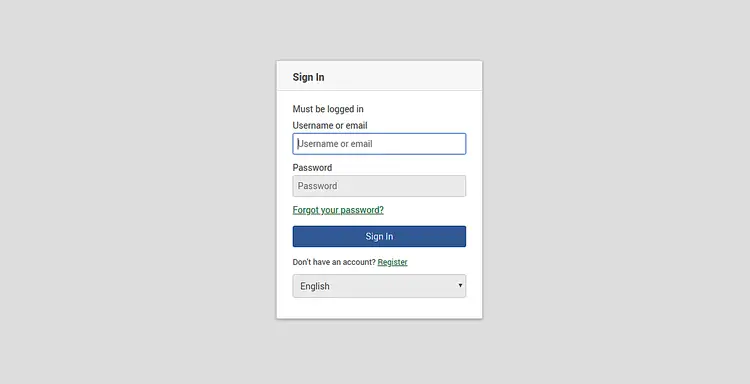
Now open your web browser and type the URL https://wekan.linuxbuz.com. You will be redirected to the following page:
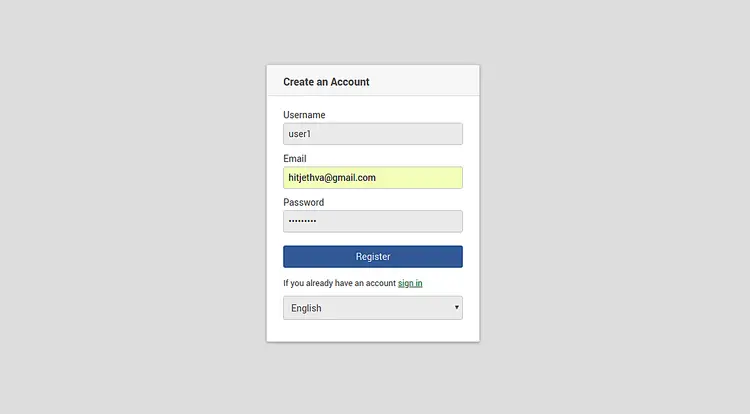
Click on the Register button. You should see the following page:
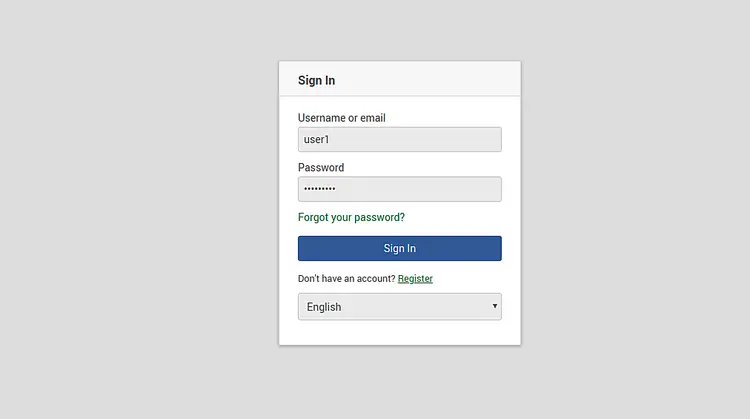
Provide your desired username, password, email and click on the Register button. Next, click on the sign in button. You should see the following page:
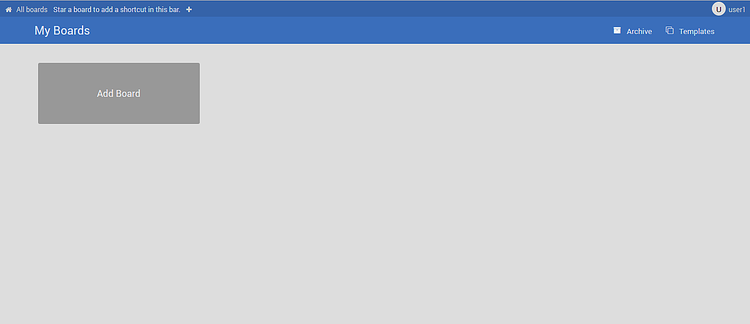
Provide your username, password and click on the Sign in button. You should see the Wekan dashboard in the following page:
That's it for now. You have successfully installed the Wekan Kanban on Debian 10 server and secure it with Let's Encrypt free SSL.