How to Install the Etherpad Collaborative Web Editor on AlmaLinux 8
This tutorial exists for these OS versions
- AlmaLinux 9
- AlmaLinux 8
On this page
- Prerequisites
- Install and Configure MariaDB Database
- Install Node.js
- Install Etherpad on Alma Linux 8
- Create a Systemd Service File for Etherpad
- Configure Nginx as a Reverse Proxy for Etherpad
- Configure Firewall For Etherpad
- Access Etherpad Web Interface
- Secure Etherpad with Let's Encrypt SSL
- Conclusion
Etherpad is a free, open-source, web-based editing application that allows you to edit a document through the web browser. It is very similar to a multi-player editor that helps you to write articles, press releases, to-do lists, etc., together with your friends, fellow students, or colleagues, all working on the same document at the same time. It offers a set of plugins to customize the Etherpad instance to suit your needs.
This post will show you how to install Etherpad with Nginx and Let's Encrypt SSL on Alma Linux 8.
Prerequisites
- A server running Alma Linux 8.
- A valid domain name pointed with your server IP.
- A root password is configured on your server.
Install and Configure MariaDB Database
Etherpad uses a MariaDB as a database backend. So the MariaDB database server must be installed on your server. You can install the MariaDB server by running the following command:
dnf install mariadb-server -y
Once the MariaDB is installed, start and enable the MariaDB service with the following command:
systemctl start mariadb
systemctl enable mariadb
Next, secure the MariaDB installation and set the MariaDB root password with the following command:
mysql_secure_installation
Answer all the questions as shown below:
Enter current password for root (enter for none): Switch to unix_socket authentication [Y/n] Y Change the root password? [Y/n] Y Remove anonymous users? [Y/n] Y Disallow root login remotely? [Y/n] Y Remove test database and access to it? [Y/n] Y Reload privilege tables now? [Y/n] Y
Once the MariaDB is secured, log in to the MariaDB with the following command:
mysql -u root -p
Once you are log in, create a database and user with the following command:
MariaDB [(none)]> CREATE DATABASE etherpad;
MariaDB [(none)]> CREATE USER 'etherpad'@'localhost' identified by 'password';
Next, grant all the privileges to the Etherpad database with the following command:
MariaDB [(none)]> GRANT CREATE,ALTER,SELECT,INSERT,UPDATE,DELETE on etherpad.* to 'etherpad'@'localhost';
Next, flush the privileges and exit from the MariaDB shell with the following command:
MariaDB [(none)]> FLUSH PRIVILEGES;
MariaDB [(none)]> EXIT;
Once you are finished, you can proceed to the next step.
Install Node.js
Next, you will also need to install Node.js on your server. You can install it using the following command:
curl -fsSL https://rpm.nodesource.com/setup_16.x | bash -
dnf install nodejs -y
Next, verify the Node.js installation with the following command:
node --version
You should see the following output:
v16.13.1
Install Etherpad on Alma Linux 8
First, create a dedicated user for Etherpad using the following command:
adduser --system --home /opt/etherpad --create-home --user-group etherpad
Next, install the Git package using the following command:
dnf install git -y
Next, log in with Etherpad user and download the latest version of Etherpad with the following command:
su - etherpad
git clone --branch master git://github.com/ether/etherpad-lite.git
Next, change the directory to the downloaded directory and run the Etherpad with the following command:
cd etherpad-lite
./src/bin/run.sh
If everything is fine, you will get the following output:
[2022-01-07 08:40:10.167] [INFO] APIHandler - Api key file "/opt/etherpad/etherpad-lite/APIKEY.txt" not found. Creating with random contents. [2022-01-07 08:40:10.235] [INFO] server - Installed plugins: [2022-01-07 08:40:10.246] [INFO] console - Report bugs at https://github.com/ether/etherpad-lite/issues [2022-01-07 08:40:10.247] [INFO] console - Your Etherpad version is 1.8.16 (142a47c) [2022-01-07 08:40:11.840] [INFO] http - HTTP server listening for connections [2022-01-07 08:40:11.841] [INFO] console - You can access your Etherpad instance at http://0.0.0.0:9001/ [2022-01-07 08:40:11.841] [WARN] console - Admin username and password not set in settings.json. To access admin please uncomment and edit "users" in settings.json [2022-01-07 08:40:11.841] [WARN] console - Etherpad is running in Development mode. This mode is slower for users and less secure than production mode. You should set the NODE_ENV environment variable to production by using: export NODE_ENV=production [2022-01-07 08:40:11.841] [INFO] server - Etherpad is running
Press CTRL+C to stop the Etherpad. We will configure Etherpad to run as a daemon later.
Next, edit the settings.json file and define your database and proxy settings:
nano settings.json
Remove the following lines:
"dbType": "dirty",
"dbSettings": {
"filename": "var/dirty.db"
},
Next, change the following lines:
"dbType" : "mysql",
"dbSettings" : {
"user": "etherpad",
"host": "localhost",
"port": 3306,
"password": "password",
"database": "etherpad",
"charset": "utf8mb4"
},
"trustProxy": true,
Save and close the file then exit from the Etherpad user with the following command:
exit
Create a Systemd Service File for Etherpad
Next, you will need to create a systemd service file to manage the Etherpad. You can create it using the following command:
nano /etc/systemd/system/etherpad.service
Add the following lines:
[Unit] Description=Etherpad, a collaborative web editor. After=syslog.target network.target [Service] Type=simple User=etherpad Group=etherpad WorkingDirectory=/opt/etherpad Environment=NODE_ENV=production ExecStart=/usr/bin/node --experimental-worker /opt/etherpad/etherpad-lite/node_modules/ep_etherpad-lite/node/server.js Restart=always [Install] WantedBy=multi-user.target
Save and close the file then reload the systemd to apply the changes:
systemctl daemon-reload
Next, start and enable the Etherpad service with the following command:
systemctl enable etherpad --now
You can now check the status of the Etherpad with the following command:
systemctl status etherpad
You will get the following output:
? etherpad.service - Etherpad, a collaborative web editor.
Loaded: loaded (/etc/systemd/system/etherpad.service; enabled; vendor preset: disabled)
Active: active (running) since Fri 2022-01-07 08:42:28 UTC; 5s ago
Main PID: 10174 (node)
Tasks: 13 (limit: 11411)
Memory: 110.4M
CGroup: /system.slice/etherpad.service
??10174 /usr/bin/node --experimental-worker /opt/etherpad/etherpad-lite/node_modules/ep_etherpad-lite/node/server.js
Jan 07 08:42:28 linux node[10174]: [2022-01-07 08:42:28.641] [INFO] settings - Random string used for versioning assets: dacd04e4
Jan 07 08:42:28 linux node[10174]: [2022-01-07 08:42:28.891] [INFO] server - Starting Etherpad...
Jan 07 08:42:28 linux node[10174]: [2022-01-07 08:42:28.967] [INFO] plugins - Running npm to get a list of installed plugins...
Jan 07 08:42:29 linux node[10174]: [2022-01-07 08:42:29.259] [INFO] plugins - npm --version: 6.14.15
Jan 07 08:42:32 linux node[10174]: [2022-01-07 08:42:32.139] [INFO] plugins - Loading plugin ep_etherpad-lite...
Jan 07 08:42:32 linux node[10174]: [2022-01-07 08:42:32.141] [INFO] plugins - Loaded 1 plugins
Jan 07 08:42:32 linux node[10174]: [2022-01-07 08:42:32.793] [INFO] APIHandler - Api key file read from: "/opt/etherpad/etherpad-lite/APIKEY.>
Jan 07 08:42:32 linux node[10174]: [2022-01-07 08:42:32.854] [INFO] server - Installed plugins:
Jan 07 08:42:32 linux node[10174]: [2022-01-07 08:42:32.887] [INFO] console - Report bugs at https://github.com/ether/etherpad-lite/issues
Jan 07 08:42:32 linux node[10174]: [2022-01-07 08:42:32.888] [INFO] console - Your Etherpad version is 1.8.16 (142a47c)
At this point, Etherpad is started and listen on port 9001. You can check it using the following command:
ss -antpl | grep 9001
You will get the following output:
LISTEN 0 128 0.0.0.0:9001 0.0.0.0:* users:(("node",pid=10174,fd=27))
Once you are finished, you can proceed to the next step.
Configure Nginx as a Reverse Proxy for Etherpad
Next, you will need to configure the Nginx as a reverse proxy for Etherpad. First, install the Nginx package with the following command:
dnf install nginx -y
Once the Nginx is installed, start and enable the Nginx service using the following command:
systemctl start nginx
systemctl enable nginx
Next, create an Nginx virtual host configuration file using the following command:
nano /etc/nginx/conf.d/etherpad.conf
Add the following lines:
server {
listen 80;
server_name etherpad.exampledomain.com;
access_log /var/log/nginx/etherpad.access.log;
error_log /var/log/nginx/etherpad.error.log;
location / {
rewrite ^/$ / break;
rewrite ^/locales/(.*) /locales/$1 break;
rewrite ^/locales.json /locales.json break;
rewrite ^/admin(.*) /admin/$1 break;
rewrite ^/p/(.*) /p/$1 break;
rewrite ^/static/(.*) /static/$1 break;
rewrite ^/pluginfw/(.*) /pluginfw/$1 break;
rewrite ^/javascripts/(.*) /javascripts/$1 break;
rewrite ^/socket.io/(.*) /socket.io/$1 break;
rewrite ^/ep/(.*) /ep/$1 break;
rewrite ^/minified/(.*) /minified/$1 break;
rewrite ^/api/(.*) /api/$1 break;
rewrite ^/ro/(.*) /ro/$1 break;
rewrite ^/error/(.*) /error/$1 break;
rewrite ^/jserror(.*) /jserror$1 break;
rewrite ^/redirect(.*) /redirect$1 break;
rewrite /favicon.ico /favicon.ico break;
rewrite /robots.txt /robots.txt break;
rewrite /(.*) /p/$1;
proxy_pass http://127.0.0.1:9001;
proxy_buffering off;
proxy_set_header Host $host;
proxy_pass_header Server;
# proxy headers
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_http_version 1.1;
# websocket proxying
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $connection_upgrade;
}
}
map $http_upgrade $connection_upgrade {
default upgrade;
'' close;
}
Save and close the file then verify the Nginx for any syntax error:
nginx -t
You will get the following output:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful
Finally, restart the Nginx to apply the configuration changes:
systemctl restart nginx
You can now verify the Nginx status using the following command:
systemctl status nginx
You will get the following output:
? nginx.service - The nginx HTTP and reverse proxy server
Loaded: loaded (/usr/lib/systemd/system/nginx.service; disabled; vendor preset: disabled)
Drop-In: /usr/lib/systemd/system/nginx.service.d
??php-fpm.conf
Active: active (running) since Fri 2022-01-07 08:58:36 UTC; 6s ago
Process: 10238 ExecStart=/usr/sbin/nginx (code=exited, status=0/SUCCESS)
Process: 10236 ExecStartPre=/usr/sbin/nginx -t (code=exited, status=0/SUCCESS)
Process: 10234 ExecStartPre=/usr/bin/rm -f /run/nginx.pid (code=exited, status=0/SUCCESS)
Main PID: 10240 (nginx)
Tasks: 2 (limit: 11411)
Memory: 3.7M
CGroup: /system.slice/nginx.service
??10240 nginx: master process /usr/sbin/nginx
??10241 nginx: worker process
Jan 07 08:58:36 linux systemd[1]: nginx.service: Succeeded.
Jan 07 08:58:36 linux systemd[1]: Stopped The nginx HTTP and reverse proxy server.
Jan 07 08:58:36 linux systemd[1]: Starting The nginx HTTP and reverse proxy server...
Jan 07 08:58:36 linux nginx[10236]: nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
Jan 07 08:58:36 linux nginx[10236]: nginx: configuration file /etc/nginx/nginx.conf test is successful
Jan 07 08:58:36 linux systemd[1]: nginx.service: Failed to parse PID from file /run/nginx.pid: Invalid argument
Jan 07 08:58:36 linux systemd[1]: Started The nginx HTTP and reverse proxy server.
Configure Firewall For Etherpad
Next, you will need to allow ports 80 and 443 through the firewalld firewall. You can allow them with the following command:
firewall-cmd --zone=public --permanent --add-service=http
firewall-cmd --zone=public --permanent --add-service=https
Next, reload the firewalld to apply the changes:
firewall-cmd --reload
Access Etherpad Web Interface
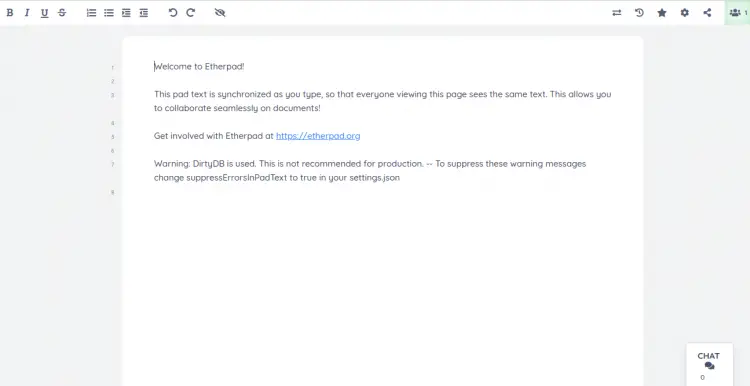
Now, open your web browser and access the Etherpad web interface using the URL http://etherpad.exampledomain.com. You should see the following screen:
Provide your pad name and click on the OK button. You should see the Etherpad page on the following screen:
Secure Etherpad with Let's Encrypt SSL
To secure the Etherpad with Let's Encrypt SSL, you must install the Certbot client to your system. You can install it with the following command:
dnf install epel-release -y
dnf install certbot -y
Next, run the following command to download and install the Let's Encrypt SSL for your Etherpad website:
certbot --nginx -d etherpad.exampledomain.com
You will be asked to provide your valid email and accept the term of service as shown below:
Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator nginx, Installer nginx Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): [email protected] - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v02.api.letsencrypt.org/directory - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (A)gree/(C)ancel: A - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - (Y)es/(N)o: Y Obtaining a new certificate Performing the following challenges: http-01 challenge for etherpad.exampledomain.com Waiting for verification... Cleaning up challenges Deploying Certificate to VirtualHost /etc/nginx/conf.d/etherpad.conf
Next, select whether or not to redirect HTTP traffic to HTTPS:
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS. You can undo this change by editing your web server's configuration. - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Type 2 and hit enter to start the process. Once the certificate has been installed, you should see the following output:
Redirecting all traffic on port 80 to ssl in /etc/nginx/conf.d/etherpad.conf - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Congratulations! You have successfully enabled https://etherpad.exampledomain.com You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=etherpad.exampledomain.com - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/etherpad.exampledomain.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/etherpad.exampledomain.com/privkey.pem Your cert will expire on 2022-04-10. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le - We were unable to subscribe you the EFF mailing list because your e-mail address appears to be invalid. You can try again later by visiting https://act.eff.org.
Conclusion
Congratulations! You have successfully installed Etherpad with Nginx and Let's Encrypt SSL on Alma Linux 8. You can now install additional plugins to extend Etherpad functionality. Feel free to ask me if you have any questions.