How to Install Mattermost on Rocky Linux 9
On this page
- Prerequisites
- Installing PostgreSQL and Nginx
- Opening HTTP and HTTPS ports
- Creating PostgreSQL user and database
- Downloading Mattermost
- Configuring Mattermost with PostgreSQL
- Running Mattermost as a systemd service
- Setting up Nginx as a reverse proxy
- Creating the first workspace with Mattermost
- Conclusion
Mattermost is an open-source and self-hosted messaging system for your organization. It is an alternative to services like Slack and Microsoft Teams. Mattermost combines multiple features, including file sharing, search, automation, and numerous third-party integrations. It is a collaboration platform and messaging system for your internal organization and companies.
This guide teaches you how to install Mattermost on the Rocky Linux 9 server. You'll set up Mattermost with PostgreSQL as the database and Nginx as a reverse proxy and then create the first workspace in Mattermost.
Prerequisites
Moving forward, make sure you have the following requirements:
- A Rocky Linux 9 server
- A non-root user with administrator privileges
- A domain name pointed to server IP address
- SELinux with the status permissive
- Firewalld enabled
Installing PostgreSQL and Nginx
In this section, you'll be installing dependencies for Mattermost, which includes the PostgreSQL server, Nginx web server, and Certbot. You'll also add the EPEL repository and enable the repository module for PostgreSQL 16.
First, run the 'dnf' command below to add the EPEL repository to your system.
sudo dnf install epel-release -y
Then enable the PostgreSQL 16 repository module with the following.
sudo dnf module enable postgresql:16
Now install dependencies such as PostgreSQL, Nginx web server, and Certbot as dependencies for Mattermost. Input 'Y' to confirm with the installation.
sudo dnf install postgresql-server postgresql-contrib nginx certbot wget curl
For the PostgreSQL server, to make it work, execute the command below to initialize the PostgreSQL data directory.
sudo /usr/bin/postgresql-setup --initdb
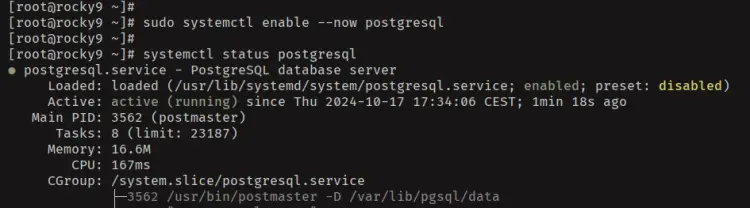
Next, run the 'systemctl' command below to start and enable the 'postgresql' service. Then, verify it to ensure that PostgreSQL is running.
sudo systemctl enable --now postgresql
sudo systemctl status postgresql
The following output shows that the PostgreSQL server is enabled and running.
Lastly, start and enable the Nginx web server with the command below. And then, check the Nginx service.
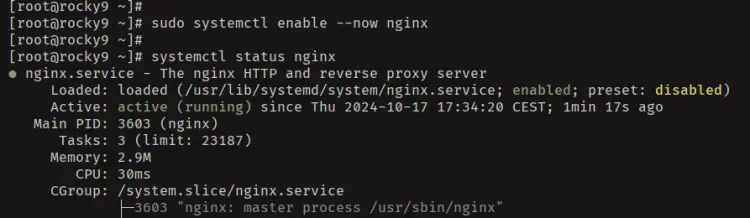
sudo systemctl enable --now nginx
sudo systemctl status nginx
As seen in the following Nginx is running and enabled.
Opening HTTP and HTTPS ports
After dependencies are installed, you need to open both HTTP and HTTPS ports on your system. On Rocky Linux, you'll use firewalld, managed through the 'firewall-cmd' utility.
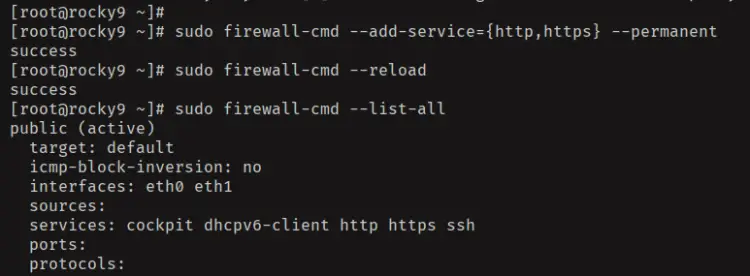
Open both HTTP and HTTPS services on firewalld using the 'firewall-cmd' command below. Once added, you'll see an output 'success'.
sudo firewall-cmd --add-service={http,https} --permanent
Now reload the firewalld with the following to apply the new rules.
sudo firewall-cmd --reload
Lastly, check the rules on your firewalld using the command below. You'll see both HTTP and HTTPS services are enabled in firewalld.
sudo firewall-cmd --list-all
Creating PostgreSQL user and database
In this section, you'll set up the PostgreSQL authentication method to 'scram-sha-256', and then create a new database and user that will be used by Mattermost via 'psql' or PostgreSQL shell.
To change the default password authentication method, open the PostgreSQL configuration '/var/lib/pgsql/data/pg_hba.conf' with the 'nano' editor.
sudo nano /var/lib/pgsql/data/pg_hba.conf
Change the default authentication method for localhost connections with the 'scram-sha-256' like the following:
# TYPE DATABASE USER ADDRESS METHOD
# "local" is for Unix domain socket connections only
local all all peer
# IPv4 local connections:
host all all 127.0.0.1/32 scram-sha-256
# IPv6 local connections:
host all all ::1/128 scram-sha-256
Save the file and exit the editor.
Now run the 'systemctl' command below to restart PostgreSQL and apply your changes.
sudo systemctl restart postgresql
After PostgreSQL is configured, you'll be creating a new database and user for Mattermost.
Log in to the PostgreSQL server with the 'psql' command below.
sudo -u postgres psql
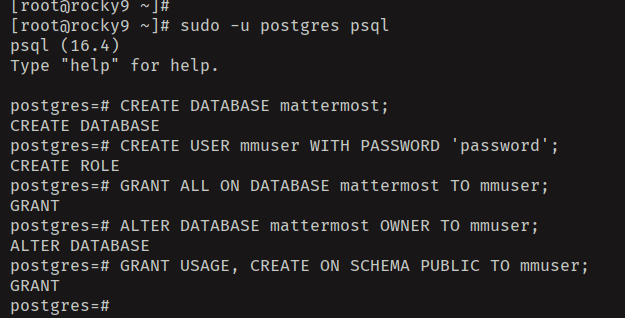
Now run the following queries to create a new database 'mattermost', a new user 'mmuser' with the password 'password'.
CREATE DATABASE mattermost;
CREATE USER mmuser WITH PASSWORD 'password';
GRANT ALL ON DATABASE mattermost TO mmuser;
ALTER DATABASE mattermost OWNER TO mmuser;
GRANT USAGE, CREATE ON SCHEMA PUBLIC TO mmuser;
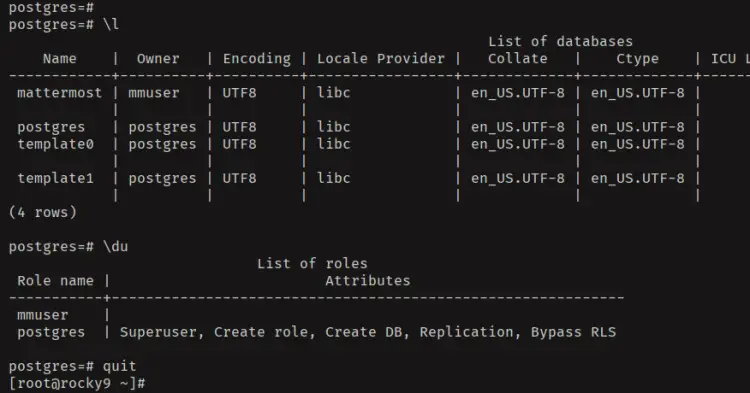
Check the list of databases and users in your PostgreSQL with the following - You'll see the database 'mattermost' and user 'mmuser' is created.
\l
\du
Type 'quit' to exit from the PostgreSQL server.
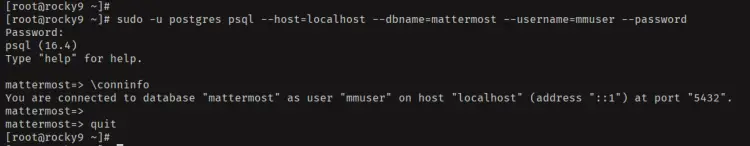
Next, run the 'psql' command below to log in to the PostgreSQL server with the 'mmuser' to the database 'mattermost'. Enter your password when prompted.
sudo -u postgres psql --host=localhost --dbname=mattermost --username=mmuser --password
If successful, check the connection status with the following query. You'll see that you've connected to the 'mattermost' database using the 'mmuser'.
\conninfo
Lastly, type 'quit' to exit.
Downloading Mattermost
Now that you've configured PostgreSQL, you'll be creating a new user, downloading Mattermost source code, and then configuring Mattermost installation directory.
Before downloading Mattermost, run the command below to add a new user 'mattermost' on your system.
sudo useradd --system --user-group mattermost
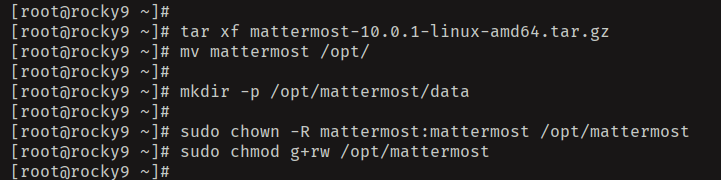
Download Mattermost source code with the 'wget' command and extract it using the 'tar' command below. The Mattermost source code will be extracted to the 'mattermost' directory.
wget https://releases.mattermost.com/10.0.1/mattermost-10.0.1-linux-amd64.tar.gz
tar xf mattermost-10.0.1-linux-amd64.tar.gz
Move the 'mattermost' directory to the '/opt' and create a new 'data' directory on top of it. In this case, Mattermost will be installed in the '/opt/mattermost' directory.
mv mattermost /opt/
mkdir -p /opt/mattermost/data
Lastly, run the following command to change the ownership of the '/opt/mattermost' directory to the 'mattermost' user. Also, make sure that group 'mattermost' has the read and write access.
sudo chown -R mattermost:mattermost /opt/mattermost
sudo chmod g+rw /opt/mattermost
Configuring Mattermost with PostgreSQL
In this section, you'll configure Mattermost with PostgreSQL. You'll be editing the Mattermost config file '/opt/mattermost/config/config.json', setting up a domain name for Mattermost, and then adding your PostgreSQL database to Mattermost.
Open the default Mattermost configuration '/opt/mattermost/config/config.json' using the 'nano' editor.
sudo nano /opt/mattermost/config/config.json
Change the default 'SiteURL' with your Mattermost domain name. In this case, we'll be using a domain name 'https://space.howtoforge.local'.
"ServiceSettings": {
"SiteURL": "https://mattermost.howtoforge.local",
Move to the 'SqlSettings' section and change the database configuration like the following. Make sure to adjust the database name, user, and password.
"SqlSettings": {
"DriverName": "postgres",
"DataSource": "postgres://mmuser:password@localhost/mattermost?sslmode=disable\u0026connect_timeout=10\u0026binary_parameters=yes",
When finished, save the file and exit the editor.
Running Mattermost as a systemd service
Now that you've integrated Mattermost with PostgreSQL, you'll be creating a new service file for Mattermost. This allows you to run Mattermost in the background and manage Mattermost easily through the 'systemctl' command line.
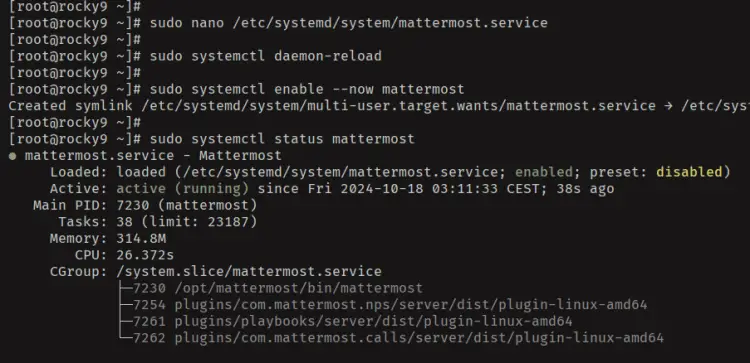
Create a new systemd service file '/etc/systemd/system/mattermost.service' using the 'nano' editor.
sudo nano /etc/systemd/system/mattermost.service
Insert the following configuration to run Mattermost as a systemd service.
[Unit]
Description=Mattermost
After=network.target
After=postgresql.service
BindsTo=postgresql.service
[Service]
Type=notify
ExecStart=/opt/mattermost/bin/mattermost
TimeoutStartSec=3600
KillMode=mixed
Restart=always
RestartSec=10
WorkingDirectory=/opt/mattermost
User=mattermost
Group=mattermost
LimitNOFILE=49152
[Install]
WantedBy=multi-user.target
Save and exit the file.
Now run the 'systemctl' command below to reload the systemd manager and apply the new 'mattermost' service.
sudo systemctl daemon-reload
Once systemd reloaded, run the following 'systemctl' command to start and enable the 'mattermost' service. And then, verify it to ensure that the service is running.
sudo systemctl enable --now mattermost
sudo systemctl status mattermost
If everything goes well, you'll see a configuration that the 'mattermost' service is running and enabled like the following:
Setting up Nginx as a reverse proxy
At this point, Mattermost is up and running on your Rocky Linux server. To make it accessible, you'll be setting up Nginx as a reverse proxy with secure HTTPS enabled.
Before configuring the Nginx web server, run the following command to stop the Nginx service and generate SSL certificates from letsencrypt. Make sure to change the domain name and email address with your information.
sudo systemctl stop nginx
sudo certbot --certonly --standalone --agree-tos --no-eff-email --staple-ocsp --preferred-challenges http -m [email protected] -d space.howtoforge.local
After the process is complete, your SSL certificates will be available in the '/etc/letsencrypt/live/domain.com' directory.
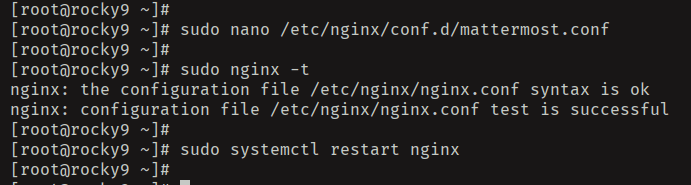
Next, create a new Nginx configuration '/etc/nginx/conf.d/mattermost.conf' using the 'nano' editor.
sudo nano /etc/nginx/conf.d/mattermost.conf
Insert the following configuration and make sure to change the domain name and the path of SSL certificates with your information.
upstream backend {
server 127.0.0.1:8065;
keepalive 32;
}
server {
listen 80;
server_name space.howtoforge.local;
return 301 https://$server_name$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name space.howtoforge.local;
http2_push_preload on; # Enable HTTP/2 Server Push
ssl_certificate /etc/letsencrypt/live/mattermost.howtoforge.local/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/mattermost.howtoforge.local/privkey.pem;
ssl_session_timeout 1d;
# Enable TLS versions (TLSv1.3 is required upcoming HTTP/3 QUIC).
ssl_protocols TLSv1.2 TLSv1.3;
# Enable TLSv1.3's 0-RTT. Use $ssl_early_data when reverse proxying to
# prevent replay attacks.
#
# @see: https://nginx.org/en/docs/http/ngx_http_ssl_module.html#ssl_early_data
ssl_early_data on;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384';
ssl_prefer_server_ciphers on;
ssl_session_cache shared:SSL:50m;
# HSTS (ngx_http_headers_module is required) (15768000 seconds = six months)
add_header Strict-Transport-Security max-age=15768000;
# OCSP Stapling ---
# fetch OCSP records from URL in ssl_certificate and cache them
ssl_stapling on;
ssl_stapling_verify on;
add_header X-Early-Data $tls1_3_early_data;
location ~ /api/v[0-9]+/(users/)?websocket$ {
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
client_max_body_size 50M;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Frame-Options SAMEORIGIN;
proxy_buffers 256 16k;
proxy_buffer_size 16k;
client_body_timeout 60s;
send_timeout 300s;
lingering_timeout 5s;
proxy_connect_timeout 90s;
proxy_send_timeout 300s;
proxy_read_timeout 90s;
proxy_http_version 1.1;
proxy_pass http://backend;
}
location / {
client_max_body_size 100M;
proxy_set_header Connection "";
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Frame-Options SAMEORIGIN;
proxy_buffers 256 16k;
proxy_buffer_size 16k;
proxy_read_timeout 600s;
proxy_http_version 1.1;
proxy_pass http://backend;
}
}
# This block is useful for debugging TLS v1.3. Please feel free to remove this
# and use the '$ssl_early_data' variable exposed by NGINX directly should you
# wish to do so.
map $ssl_early_data $tls1_3_early_data {
"~." $ssl_early_data;
default "";
}
Save the file and exit the editor when you're finished.
Next, run the 'nginx' command below to verify your Nginx syntax. If you've proper syntax, you'll see an output 'syntax is ok - test is successful'.
sudo nginx -t
Lastly, run the 'systemctl' command below to restart the Nginx service and apply your changes.
sudo systemctl restart nginx
Creating the first workspace with Mattermost
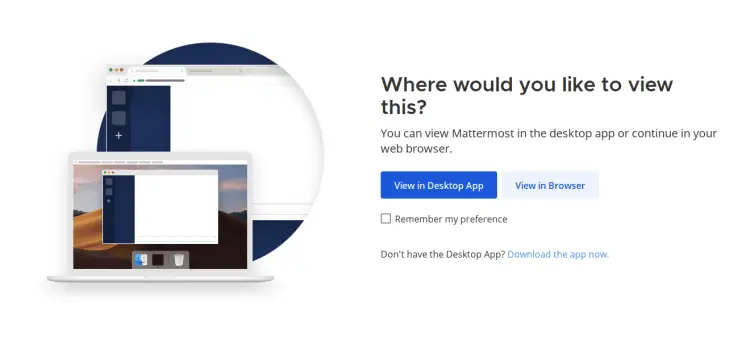
Open your web browser and visit your Mattermost installation such as 'https://space.howtoforge.local'. If the installation is successful, you'll see the installation wizard.
Click the 'View in browser' button to set up Mattermost via a web browser.
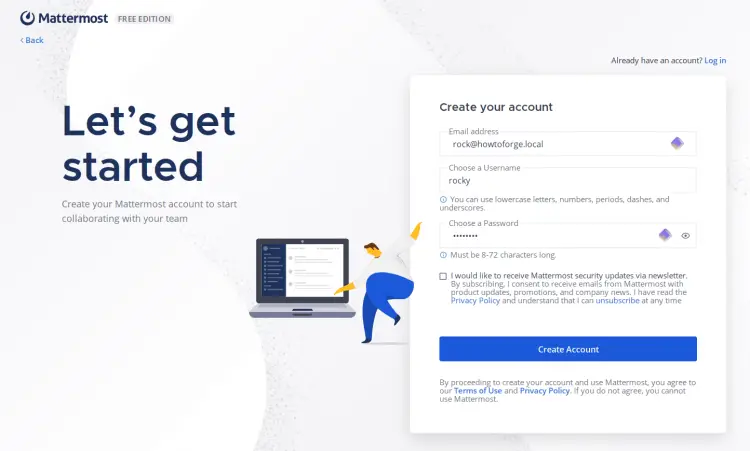
Input the new admin user, email address, and password, then click 'Create account' to continue.
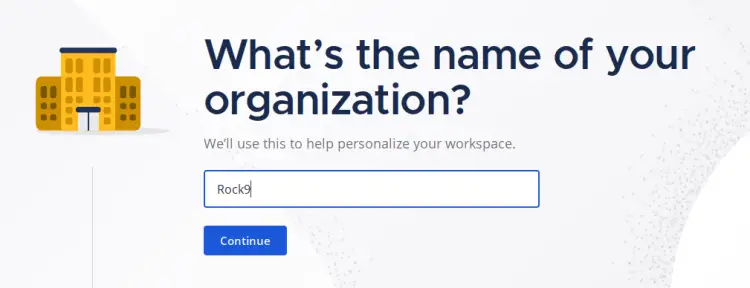
Input your organization name.
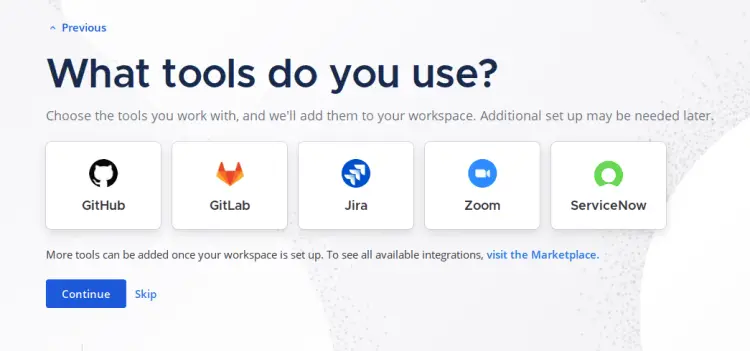
For now, you can skip the integration with third-party applications.
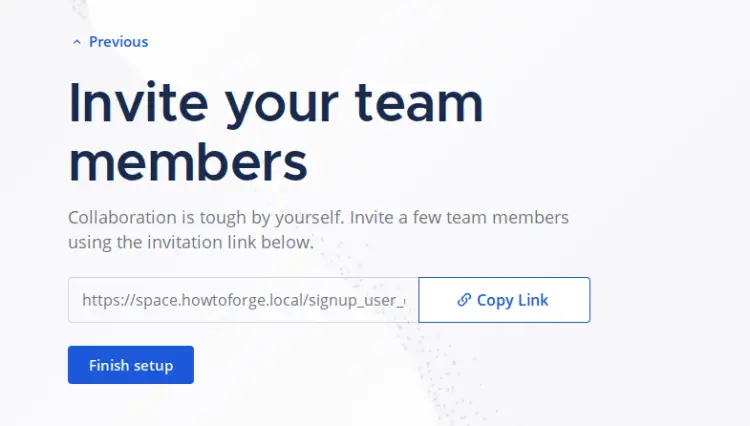
Now click 'Finish setup' to complete the Mattermost installation.
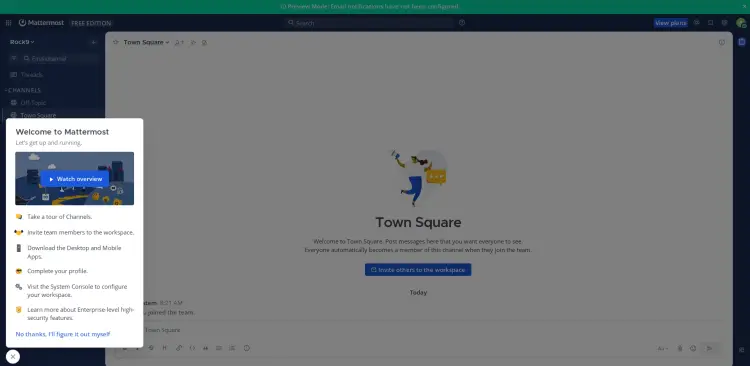
Once finished, you'll be redirected to your first Mattermost workspace.
Conclusion
Congratulations! You've completed the installation of Mattermost on the Rocky Linux 9 server. You've Mattermost up and running in the background as a systemd service with PostgreSQL as the database and Nginx as a reverse proxy. You've also secured Mattermost with HTTPS and created your first workspace in Mattermost. From here, you can integrate Mattermost with third-party applications such as GitHub, GitLab, and Bitbucket.