How to Install Fail2ban on Ubuntu 24.04 Server
Fail2ban is free and open-source IPS (Intrusion Prevention Software) that helps administrators secure Linux servers against malicious login and brute-force attacks. Fail2ban is written in Python and comes with filters for various services such as Apache2, SSH, FTP, etc. Fail2ban reduces malicious login attempts by blocking the IP addresses of the source attacks.
Fail2ban works by scanning log files of services (e.f /var/log/auth.log) and banning IP addresses that show malicious login attempts such as too many incorrect passwords, seeking exploits, etc. Fail2ban also supports multiple firewall backends such as iptables, ufw, and firewalld. Also allows you to set up an email notification for every blocked login attempt.
In this guide, you'll learn how to install Fail2ba on Ubuntu 24.04 server. You'll set up the Fail2ban jail, learn the basic 'fail2ban-client' command, and then learn how to ban and unban IP addresses using Fail2ban.
Prerequisites
To get started with this guide, make sure you have:
- An Ubuntu 24.04 server
- A non-root user with administrator privileges
Installing Fail2ban and UFW (Uncomplicated Firewall)
Fail2ban is an IPS (Intrusion Prevention Software) that protects servers against brute-force attacks. It is available by default on most Linux repositories and supports multiple firewall backends. In this section, you'll install Fail2ban and then set up UFW (Uncomplicated Firewall) which will be used as the firewall backend for the Fail2ban.
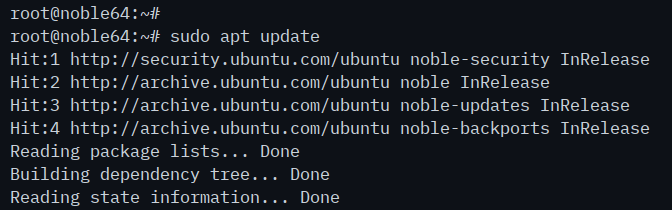
First, run the command below to update your Ubuntu package index.
sudo apt update
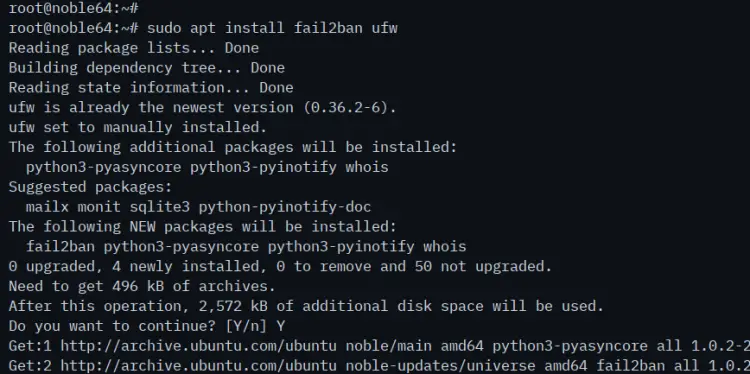
Now install the 'fail2ban' and 'ufw' packages with the following 'apt' command. Input 'Y' to confirm the installation.
sudo apt install fail2ban ufw
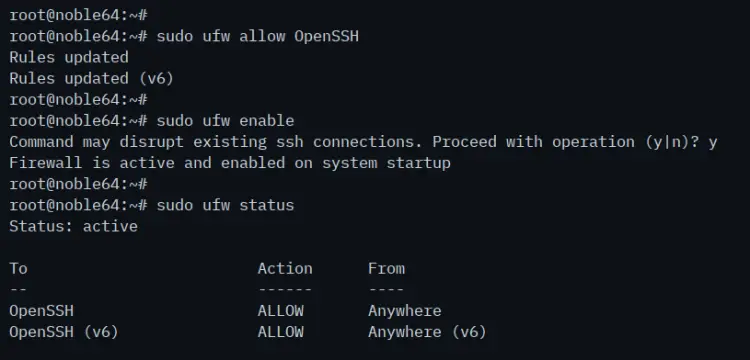
After the installation is complete, run the command below to open the port for SSH and enable UFW. Input 'Y' to confirm, start, and enable UFW.
sudo ufw allow OpenSSH
sudo ufw enable
Once UFW is enabled, you'll see an output 'Firewall is active and enabled on system startup'.
Next, run the following command to check the UFW status. You'll see the UFW is 'active' with the 'OpenSSH' enabled.
sudo ufw status
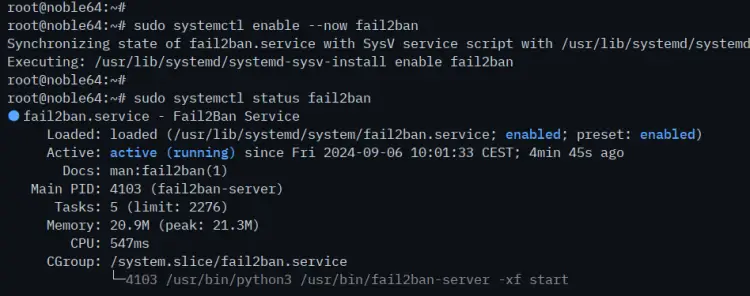
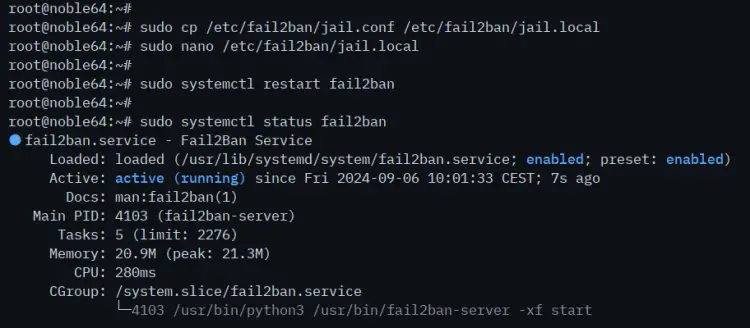
Lastly, run the 'systemctl' command below to start, enable, and verify the 'fail2ban' service.
sudo systemctl enable --now fail2ban
sudo systemctl status fail2ban
You can see below the 'fail2ban' is active (running) and enabled.
Configuring Fail2ban
After installing fail2ban, you must configure it before the Fail2ban takes an action (checking and blocking). In this section, you'll modify the fail2ban configuration '/etc/fail2ban/jail.local', set up the global configuration for 'bantime', 'maxretry', and 'findtime', setup default action and UFW firewall backend, and then enable the 'sshd' jail for protecting SSH service from brute force attacks.
To start, copy the default fail2ban configuration to '/etc/fail2ban/jail.local' with the following:
sudo cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
Open the file '/etc/fail2ban/jail.local' with the following 'nano' editor command.
sudo nano /etc/fail2ban/jail.local
Add your local network to the 'ignoreip' option. Any subnet within this option will not be blocked by fail2ban.
ignoreip = 127.0.0.1/8 ::1 192.168.1.0/24 192.168.10.20
Adjust the default configuration for 'bantime' (the time of IP address will be banned), 'findtime' (the duration between the number of failures before the ban action), and 'maxretry' (the number of failures for IP addresses to get banned). In this example, you'll set up the 'bantime' to '1 hour', the 'findtime' to '10 minutes', with the 'maxretry' to '5 times'.
bantime = 1h
findtime = 10m
maxretry = 5
Optionally, change the default 'action' to '%(action_mw)s' to ban IP addresses and send notification to the administrator via email. Also, make sure to change the 'destmail' and 'sender' options.
action = %(action_mw)s
destemail = [email protected]
sender = [email protected]
Change the default 'banaction' to 'ufw'. With this, IP addresses will be banned by fail2ban via UFW.
banaction = ufw
Now change the default jail for 'sshd' with the configuration below. In this example, the 'sshd' jail will have custom settings for 'bantime', 'maxretry', and the 'findtime'.
[sshd]
enabled = true
maxretry = 3
findtime = 15m
bantime = 3h
port = ssh
logpath = %(sshd_log)s
backend = %(sshd_backend)s
Save and exit the file when finished.
Lastly, run the 'systemctl' command below to restart the 'fail2ban' service and apply your changes.
sudo systemctl restart fail2ban
Checking fail2ban rules using fail2ban-client
At this point, the Fail2ban service is up and running with the 'sshd' jail enabled. Now you'll learn the basic command of 'fail2ban-client' for checking and managing Fail2ban installation.
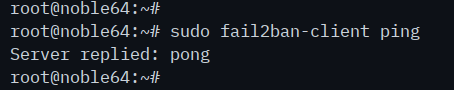
To ensure that fail2ban is running, run the 'fail2ban-client' command below.
sudo fail2ban-client ping
If fail2ban is running, you'll see an output 'PONG'.
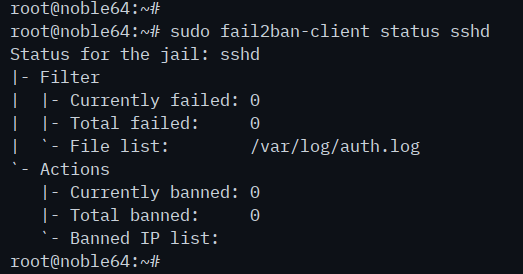
Now check the status of the 'sshd' jail with the following command. This will show you the list of detected and banned IP addresses for the 'sshd' jail.
sudo fail2ban-client status sshd
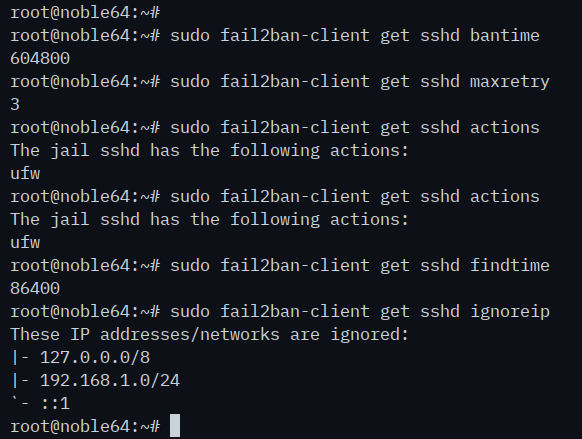
Next, run the 'fail2ban-client get' command below to check the specific rules of your fail2ban jail. In this section, you'll check the 'bantime', 'maxretry', 'actions', 'findtime', and 'ignoreip' from the 'sshd' jail.
sudo fail2ban-client get sshd bantime
sudo fail2ban-client get sshd maxretry
sudo fail2ban-client get sshd actions
sudo fail2ban-client get sshd findtime
sudo fail2ban-client get sshd ignoreip
How to Ban and Unban IP address with fail2ban-client
It's important to know how to ban or unban IP addresses manually using 'fail2ban-client'. With this, you can easily remove your IP address from the banned list. You'll be utilizing the 'fail2ban-client' command to ban and unban IP addresses on Fail2ban.
To ban IP addresses manually via fail2ban, run the 'fail2ban-client' command below. In this case, the banned IP address goes to the 'sshd' jail.
sudo fail2ban-client set sshd banip IP-ADDRESS
Now run the following command to unban the IP address from the fail2ban 'sshd' jail.
Sudo fail2ban-client set sshd unbanip IP-ADDRESS
Lastly, you can check the 'sshd' jail status using the command below. You'll see the IP address has been removed.
sudo fail2ban-client status sshd
Conclusion
Congratulations! You've completed the installation of fail2ban on the Ubuntu 24.04 server. You've also learned the basic configuration for configuring Fail2ban, including setting up global configuration and jail. Lastly, you've also learned the basic usage of the 'fail2ban-client' command to check the fail2ban status, jail status, jail configurations, and ban and unban IP addresses manually.