How to Install and Use Vuls Vulnerability Scanner on Ubuntu 18.04 LTS
This tutorial exists for these OS versions
- Ubuntu 22.04 (Jammy Jellyfish)
- Ubuntu 18.04 (Bionic Beaver)
On this page
Vuls is a free and open-source Vulnerability Scanner written in Go. It is used to perform security vulnerability analysis and software updates on a daily basis. Vuls is specially designed to scan the Applications, Computers, middleware, Network devices and programming language libraries for a known vulnerability. Vuls send you notification once the servers are affected by a vulnerability. Vuls can be installed on all major operating systems like Linux, FreeBSD, SUSE, Ubuntu, Debian, CentOS, Oracle Linux and many more. Vuls can also able to scan the remote system using the ssh protocol. Vuls uses three scan modes fast, fast root and deep, you can select any one as per your requirement.
In this tutorial, we will explain, how to install and configure Vuls Vulnerability Scanner on Ubuntu 18.04 server.
Requirements
- A server running Ubuntu 18.04.
- A root password is configure on your system.
Getting Started
Before starting, you will need to update your system with the latest version. You can do this by running the following command:
apt-get update -y
apt-get upgrade -y
Once your server is updated, restart your server to apply the changes.
Install Required Dependencies
Vuls uses SQLite to store their vulnerability information. So, you will need to install SQLite and other required packages to your system. You can install all of them with the following command:
apt-get install sqlite3 git debian-goodies gcc make wget -y
Once installed, you will need to download and install the latest version of Go on your system.
First, download the Go source with the following command:
wget https://dl.google.com/go/go1.13.linux-amd64.tar.gz
Once downloaded, extract the downloaded file to the /usr/local directory with the following command:
tar -C /usr/local -xzf go1.13.linux-amd64.tar.gz
Next, you will need to set up a few environment variables for Go. You can set up it by editing /etc/profile file:
nano /etc/profile
Add the following lines at the end of the file:
export GOPATH=$HOME/go export PATH=$PATH:/usr/local/go/bin
Save and close the file when you are finished. Then, reload the environment variables with the following command:
source /etc/profile
Next, create a directory structure for Go with the following command:
mkdir /root/go
mkdir -p $GOPATH/src/github.com/kotakanbe
Once you have done, you can proceed to the next step.
Install and Configure go-cve-dictionary
The go-cve-dictionary is a tool to build a local copy of the NVD (National Vulnerabilities Database). You can access the NVD (National Vulnerability Database) using Go package. Then, you will need to run it and fetch vulnerability data for Vuls to use. So, you will need to download and install go-cve-dictionary to your system.
First, change the directory to $GOPATH/src/github.com/kotakanbe and download the go-cve-dictionary source from the Git repository with the following command:
cd $GOPATH/src/github.com/kotakanbe
git clone https://github.com/kotakanbe/go-cve-dictionary.git
Once the download is completed, install it with the following command:
cd go-cve-dictionary
make install
The above command will take some time to finish. Once the installation has been completed successfully, you will need to copy go-cve-dictionary binary to the /usr/local/bin directory. You can do it with the following command:
cp $GOPATH/bin/go-cve-dictionary /usr/local/bin/
go-cve-dictionary also required log and data directory to store their log and data. So you will need to create a log and data directory. You can create them with the following command:
mkdir /var/log/vuls
mkdir /usr/share/vuls-data
chmod 700 /var/log/vuls
Next, fetches vulnerability data from NVD and inserts into sqlite3 with the following command:
for i in `seq 2002 $(date +"%Y")`; do go-cve-dictionary fetchnvd -dbpath /usr/share/vuls-data/cve.sqlite3 -years $i; done
The above command will download the NVD data from the year 2002 to current year.
Once you have done, you can proceed to the next step.
Install and Configure goval-dictionary
The goval-dictionary is a tool to build a local copy of the OVAL(Open Vulnerability and Assessment Language). Go package also providesaccess to the OVAL database for Ubuntu. So, you will need to download and install goval-dictionary to your system.
First, download the goval-dictionary source from the Git repository with the following command:
cd $GOPATH/src/github.com/kotakanbe
git clone https://github.com/kotakanbe/goval-dictionary.git
Next, install it with the following command:
cd goval-dictionary
make install
Next, copy it to the /usr/local/bin directory with the following command:
cp $GOPATH/bin/goval-dictionary /usr/local/bin/
Next, fetch the OVAL data for Ubuntu 18.04 with the following command:
goval-dictionary fetch-ubuntu -dbpath=/usr/share/vuls-data/oval.sqlite3 18
Once you have done, you can proceed to the next step.
Install and Configure Vuls
Next, you will need to download Vuls source and install it to your system. You can download it from the Git repository with the following command:
mkdir -p $GOPATH/src/github.com/future-architect
cd $GOPATH/src/github.com/future-architect
git clone https://github.com/future-architect/vuls.git
Next, change the directory to vuls and install it with the following command:
cd vuls
make install
Once installed, you will need to copy vuls binary to the /usr/local/bin directory. You can do it with the following command:
cp $GOPATH/bin/vuls /usr/local/bin/
Next, you will need to create a vuls configuration file in /usr/share/vuls-data directory:
cd /usr/share/vuls-data
nano config.toml
Add the following lines:
[cveDict] type = "sqlite3" SQLite3Path = "/usr/share/vuls-data/cve.sqlite3" [ovalDict] type = "sqlite3" SQLite3Path = "/usr/share/vuls-data/oval.sqlite3" [servers] [servers.localhost] host = "localhost" port = "local" scanMode = [ "fast" ]
Save and close the file, when you are finished.
Next, test the configuration file with the following command:
vuls configtest
If everything is fine, you should see the following output:
[Sep 17 16:01:39] INFO [localhost] Validating config... [Sep 17 16:01:39] INFO [localhost] Detecting Server/Container OS... [Sep 17 16:01:39] INFO [localhost] Detecting OS of servers... [Sep 17 16:01:39] INFO [localhost] (1/1) Detected: localhost: ubuntu 18.04 [Sep 17 16:01:39] INFO [localhost] Detecting OS of static containers... [Sep 17 16:01:39] INFO [localhost] Detecting OS of containers... [Sep 17 16:01:39] INFO [localhost] Checking Scan Modes... [Sep 17 16:01:39] INFO [localhost] Checking dependencies... [Sep 17 16:01:39] INFO [localhost] Dependencies... Pass [Sep 17 16:01:39] INFO [localhost] Checking sudo settings... [Sep 17 16:01:39] INFO [localhost] sudo ... No need [Sep 17 16:01:39] INFO [localhost] It can be scanned with fast scan mode even if warn or err messages are displayed due to lack of dependent packages or sudo settings in fast-root or deep scan mode [Sep 17 16:01:39] INFO [localhost] Scannable servers are below... localhost
Once you have done, you can proceed to the next step.
Scan Your System Using Vuls
Vuls is now installed and configured to scan your local system. To scan your local system, run the following command:
vuls scan
You should see the following output:
[Sep 17 16:02:20] INFO [localhost] Start scanning [Sep 17 16:02:20] INFO [localhost] config: /usr/share/vuls-data/config.toml [Sep 17 16:02:20] INFO [localhost] Validating config... [Sep 17 16:02:20] INFO [localhost] Detecting Server/Container OS... [Sep 17 16:02:20] INFO [localhost] Detecting OS of servers... [Sep 17 16:02:20] INFO [localhost] (1/1) Detected: localhost: ubuntu 18.04 [Sep 17 16:02:20] INFO [localhost] Detecting OS of static containers... [Sep 17 16:02:20] INFO [localhost] Detecting OS of containers... [Sep 17 16:02:20] INFO [localhost] Checking Scan Modes... [Sep 17 16:02:20] INFO [localhost] Detecting Platforms... [Sep 17 16:02:21] INFO [localhost] (1/1) localhost is running on other [Sep 17 16:02:21] INFO [localhost] Detecting IPS identifiers... [Sep 17 16:02:21] INFO [localhost] (1/1) localhost has 0 IPS integration [Sep 17 16:02:21] INFO [localhost] Scanning vulnerabilities... [Sep 17 16:02:21] INFO [localhost] Scanning vulnerable OS packages... [Sep 17 16:02:21] INFO [localhost] Scanning in fast mode One Line Summary ================ localhost ubuntu18.04 537 installed To view the detail, vuls tui is useful. To send a report, run vuls report -h.
Vuls also store their vulnerabilities report in the log file. You can see it later with the following command:
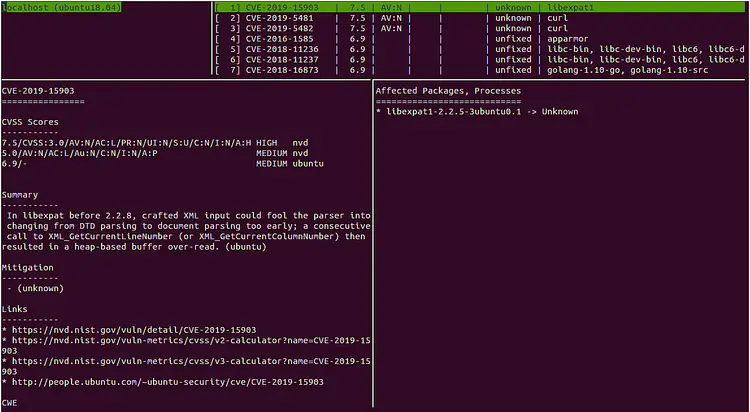
vuls tui
You should see the following screen:
You can now press Enter and navigate with the keyboard arrows.
Congratulations! you have successfully installed and configured Vuls vulnerability scanner on Ubuntu 18.04 server. You can now easily scan the local system as well as multiple remote systems and generate vulnerabilities report for each. For more information, you can visit the Vuls official documentation at Vuls Doc. Feel free to ask me if you have any questions.