How To Encrypt Mails With SSL Certificates (S/MIME) - Page 3
4.2 Evolution
The procedure is almost the same for the Evolution client. Go to Edit > Preferences:
4.2.1 Import a Self Signed Certificate
Open the Certificates section on the left, select the Your Certificates tab and click on Import.
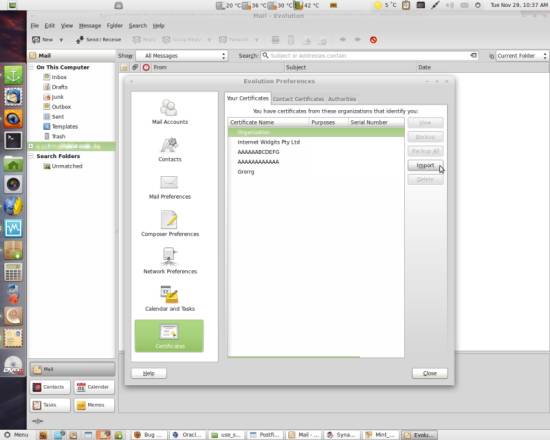
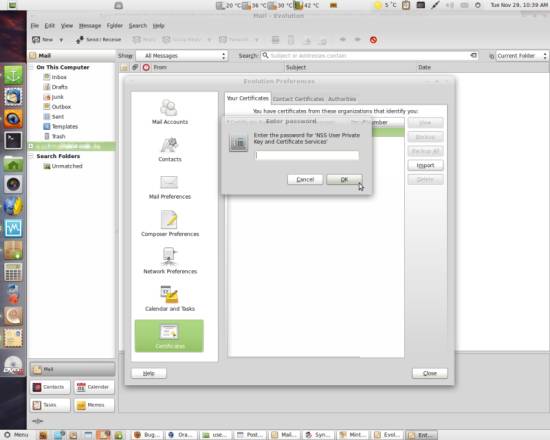
Browse the certificate you need and import it. You will be asked for the certificate key:
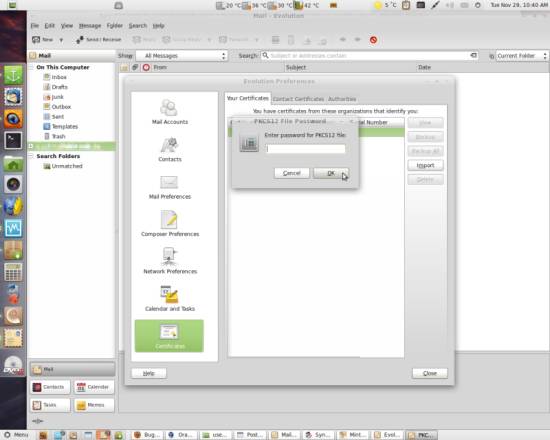
And then for the export password of the .p12 file.
That's it for single certificates. You only need the next step if you created a certificate authority.
4.2.2 Import CA Signed Certificates
In the Preferences windows, go to the Authorities tab and click on Import.
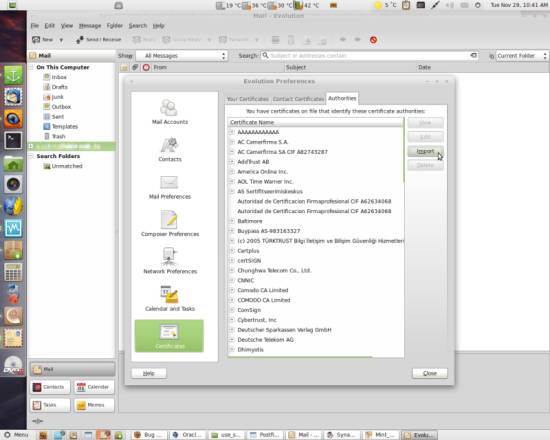
Browse the CA .crt file that you want to import and do so. You'll be asked how far you want to trust it - since you're using it to verify emails, activate Trust the CA to identify email users and hit OK:
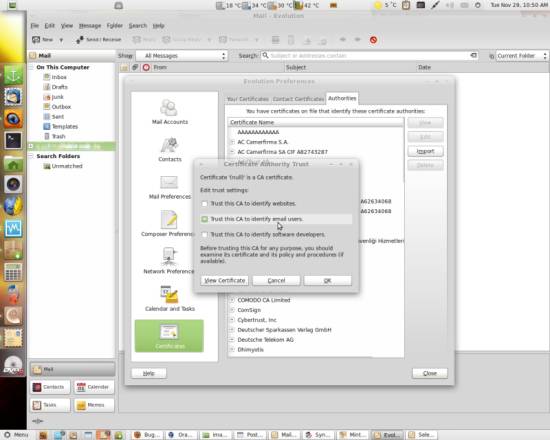
4.2.3 Assign the Certificate to an Account and Encrypt a Mail
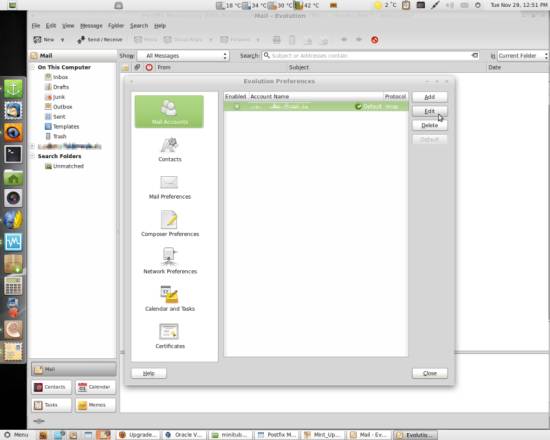
Before you can sign and encrypt mails, you have to assign the certificate you just imported to an account - to do that, go to Edit > Preferences, Mail Accounts, select the account you want to assign a certificate to and click Edit:
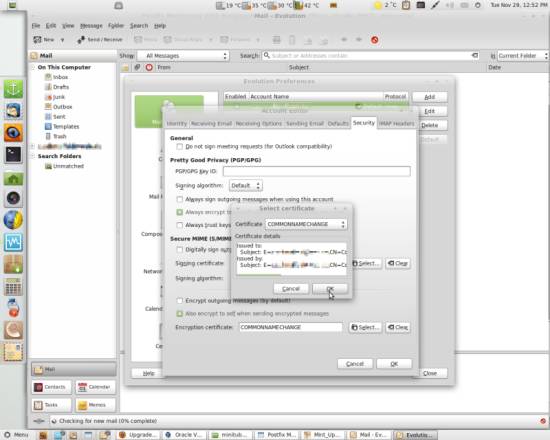
Go to the Security tab and click Select... next to the Signing certificate and Encryption certificate fields in the Secure MIME (S/MIME) section:
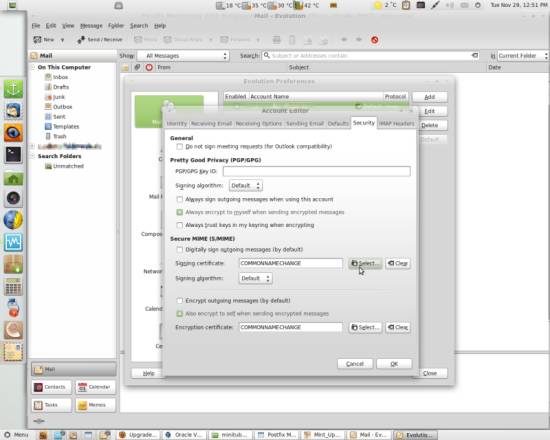
On the appearing window, select the desired certificate from the dropdown-menu and hit OK:
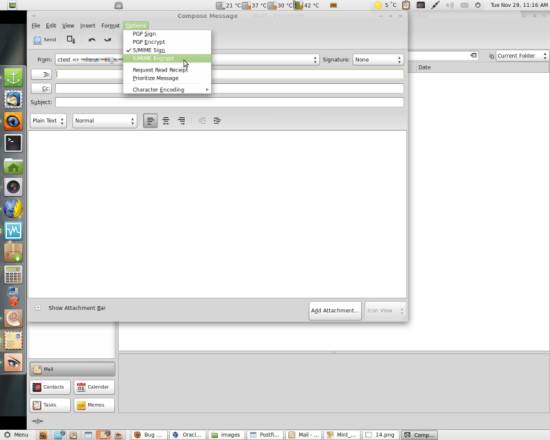
If you compose a new email, you can now select the menu items S/MIME Sign and S/MIME Encrypt from the Options menu in the new mail window:
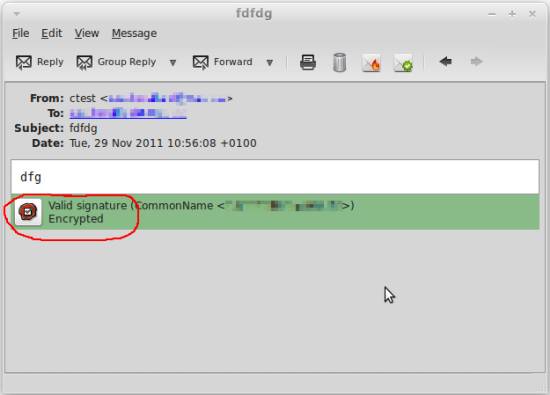
The indicator symbol for a signed mail looks as follows. An extra string is shown if the mail is also encrypted:
5 Links
- OpenSSL: http://www.openssl.org/
- Thunderbird: http://www.mozilla.org/en-US/thunderbird/
- Evolution: http://projects.gnome.org/evolution/
- StartSSL: https://www.startssl.com/

