How to configure a Nessus Vulnerability Scan Policy
On this page
Vulnerabilities arise every day with the security specialist engaged in fixing it and the hackers working to exploit it. A Vulnerability scanner checks a system with the already known vulnerabilities which can be exploited by attackers to compromise a system. There are many tools available in the market for vulnerability scanning. Nessus is one such powerful scanning tool for discovering vulnerabilities. It is developed and maintained by Tenable Network Security Inc. It was once ranked first in the security tools checklist of Nmap Software LLC. Although it is now dropped to the third position in the list, it is still a powerful remote security scanning tool.
What will we cover?
In this guide we will explore how to configure a scan policy on Nessus, later we will also use this policy to create a scan. We will then select a target system for scanning. We are using Kali Linux for this tutorial. Let’s get started now.
Prerequisites
- User account with administrative credentials.
- Basic idea of Network Security and Vulnerability Assessment.
- Nessus essential should be installed on your system.
Ready to Rock...
The very first step towards launching a Nessus scan is to select a Scan template. One can use the available Scan templates from Nessus or create a custom policy. The latter creates a user defined scan template which can be found under the User Defined scan templates section. Every setting we set in this policy will be automatically applied to any scan under that policy.
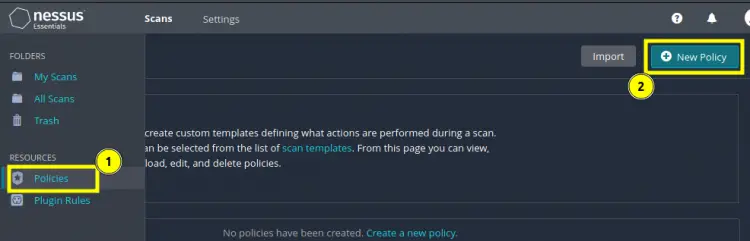
Step 1. Let’s go ahead and create a scan policy. First login on the web interface of Nessus by navigating to "https://kali:8834". On the landing page, click the ‘Policies’ label on the left vertical panel. This is labeled as ‘1’ in the image below. Now click on the button ‘New Policy’ on the top right side corner (labeled as ‘2’).
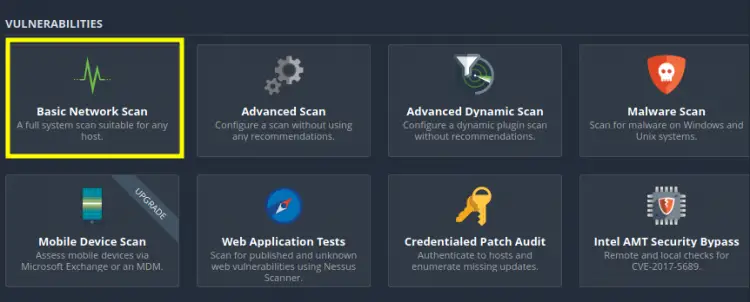
Step 2. There are many Scanner templates we can choose from. Overall, there are three broad categories: Discovery, Vulnerabilities, and Compliance. Since we are working on a Vulnerability scan policy, we will select one from this heading. Let us start with the Basic Network Scan policy. This policy is meant for full system scan, that means it searches for any vulnerability on our system.
On this new screen select the option ‘Basic Network Scan’.
Step 3. Now that we have selected a scan policy, give it a suitable name and for now leave the rest of the settings as they are. The name of the policy in our case is ‘Policy1_HTF’.
You would have noted that our custom policies are based on the Tenable-provided templates.
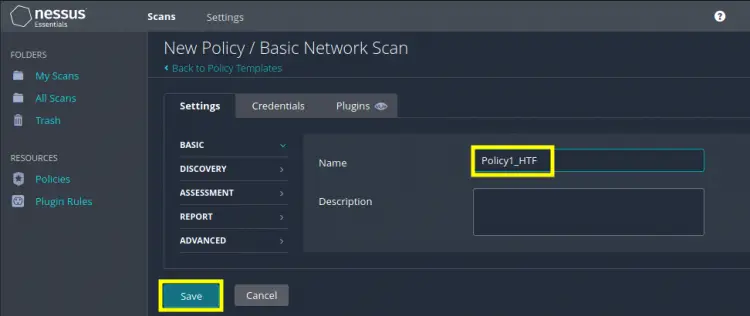
Step 4. After saving the policy, we are all set to create a new scan under this policy. Now select the ‘My Scans’ label on the top left corner, under the folders section and hit the ‘New Scan’ button. See the picture below for your reference.
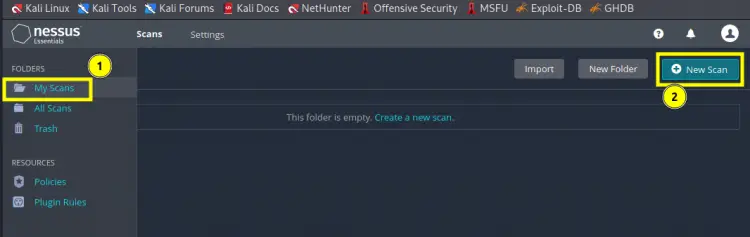
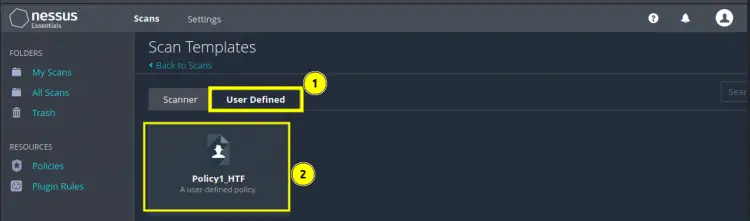
Step 5. On the new page, go to the ‘User Defined’ tab and select our custom policy (Policy1_HTF) which we created in Step 3.
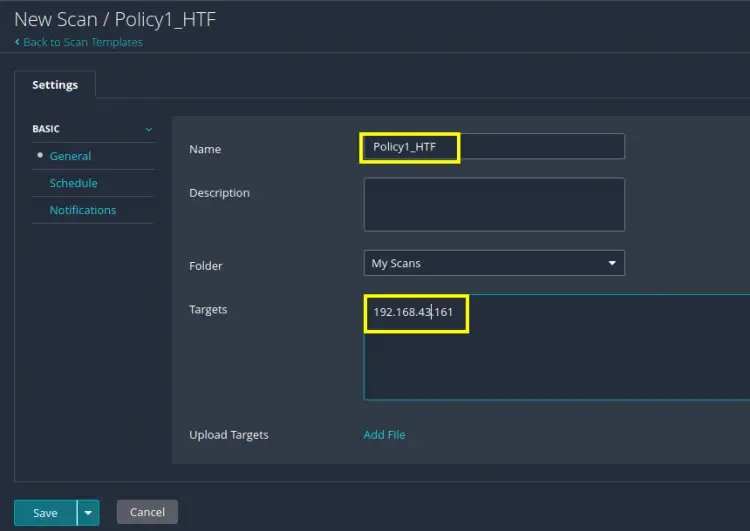
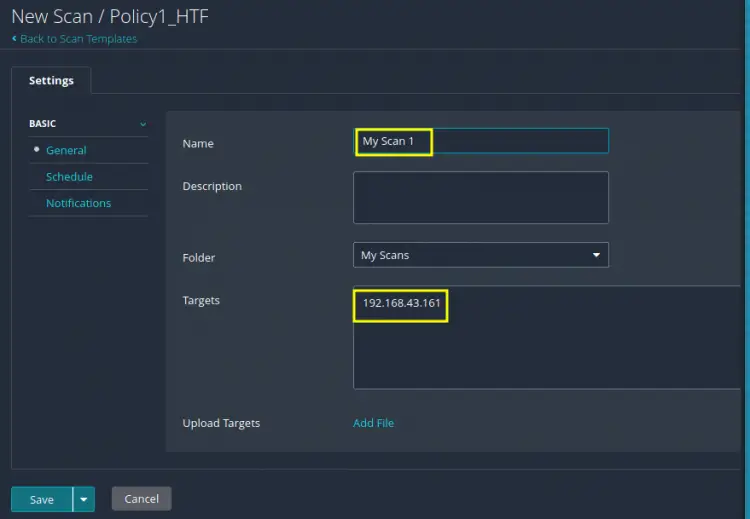
Step 6. The new scan has name same as that of our custom policy as shown here:
We will be changing this name to ‘My Scan 1’ to avoid any confusion. You can also give an optional description for this Scan, we have left it blank. In the text field corresponding to the label ‘Targets’, put the hostnames or IP addresses of the target system you want to scan. Save the file to continue.
Step 7. Now all configuration has finished. We are now just left to launch the Scan to see if it is working properly. On the new window, you will notice a Play button, click on it to start scanning.
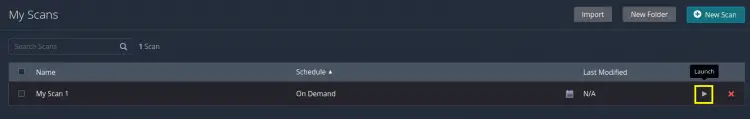
The Play icon will change to two rounded rotating arrows indicating the scan is running. It will take some time for the scan to finish.
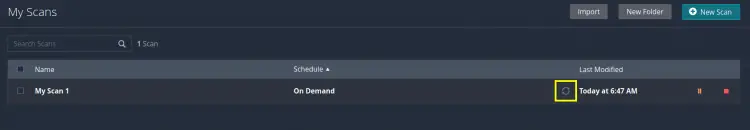
The rotating arrows are now changed to a checkmark symbol, this means our scanning process is successful.
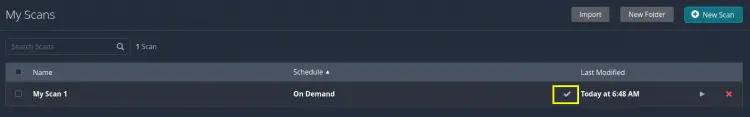
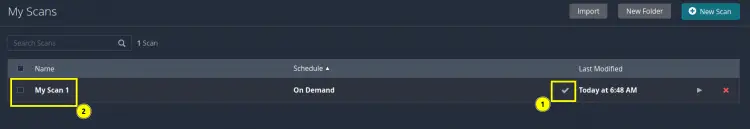
Cool, we can now check the scan report for our target system. Click on the scan name (‘My Scan 1’ in our case).
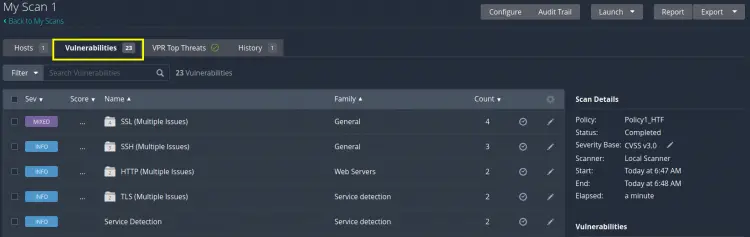
On the new window, click on the ‘Vulnerabilities’ tab to see the report summary. We can also export these Scans in Nessus file or a Nessus DB file format and the scan reports can be generated in HTML, CSV or PDF formats.
Congratulations, you have completed your first vulnerability scan using Nessus.
Wrapping up…
We have now completed our today's guide of the Nessus scanning tool. We have seen how we can create a policy and use it to scan a target system. For interpreting a Nessus report one needs in-depth knowledge of the tool as well as a better understanding of the Network security concept. Tenable also provides on-demand training to effectively use its product. If you are interested in learning Nessus, you can use the free trial provided by the company.