How to Audit a Remote Linux system with Lynis Security Tool
Lynis is a free and open-source security auditing tool and released as a GPL licensed project and is available for Linux and Unix-based Operating systems like MacOS, FreeBSD, NetBSD, OpenBSD and so on. People, in general, are unaware that we can also use Lynis for remote system auditing. In this way, we can install Lynis on one system and conduct an audit on other remote systems.
What will we explore here?
In this tutorial, we will provide instructions on how to perform a Lynis security audit on a remote system. Let's now get started with this HowTo.
Prerequisites
- ‘Git’ and ‘Lynis’ should be installed on the Kali Linux system.
- ‘SSH’ connection should be set up between the two systems.
- Internet connectivity for the two systems.
Experimental Setup
In this tutorial we are using two Linux systems: 1) Kali Linux 2) Ubuntu 20.04.
On the Kali Linux system, we have a working Lynis setup. We have installed Lynis using the ‘Git’ tool as a result we will be running it from the fetched ‘lynis’ directory. Our lynis commands will start from the prefix: ‘./lynis’. If you have installed it using the apt package manager, you can invoke it from anywhere and directly using the name of the tool: ‘lynis’.
Ubuntu 20.04 is our remote system on which we will be conducting our audit. The IP configuration of these machines are as below:
- Kali Linux: 192.168.199.161/24
- Ubuntu: 192.168.199.150/24
Steps to audit a remote system
Now we will proceed with the below steps to perform a security system audit on our remote target.
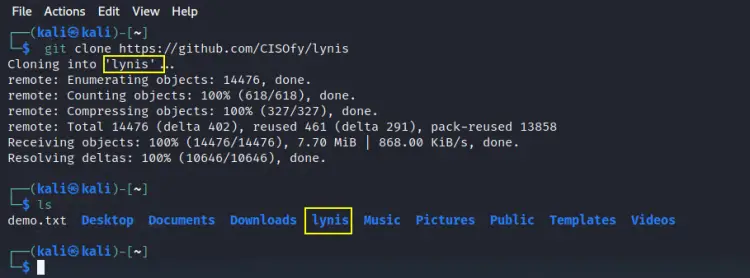
Step 1. Start by logging in to your Kali Linux system. We now need to fetch the Lynis setup files from the GitHub repository, so open a terminal and execute the below command:
$ git clone https://github.com/CISOfy/lynis
Step 2. Once the git files are fetched, a folder named as ‘lynis’ should appear on your system:
$ ls
Now move to the ‘lynis’ folder and create a folder ‘ files’:
$ cd files && mkdir files
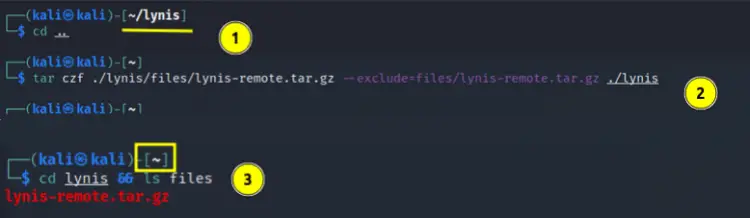
Step 3. Create a tar file of the lynis folder by executing the below commands from ‘outside’ this folder:
$ cd ..
$ tar czf ./lynis/files/lynis-remote.tar.gz --exclude=files/lynis-remote.tar.gz ./lynis
Now again move inside the lynis folder and check if a file named as ‘lynis-remote.tar.gz’ is inside the ‘files’ folder:
$ cd lynis && ls files/
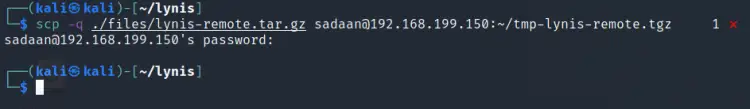
Step 4. It's time to copy the above tar file to our target machine i.e. Ubuntu with 192.168.199.150/24. We are using the ‘scp’ command for this task:
$ scp -q ./files/lynis-remote.tar.gz ‘YOUR_USERNAME’@192.168.199.150:~/tmp-lynis-remote.tgz
Note: In every command replace ‘YOUR_USERNAME’ and IP address with the username and IP address of the target system.
Confirm the authenticity of the target system and enter its password to make the transfer work.
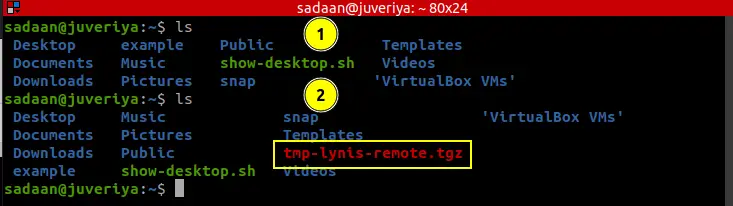
Step 5. After running the above command, a folder named as ‘tmp-lynis-remote.tgz' should appear on the target system.
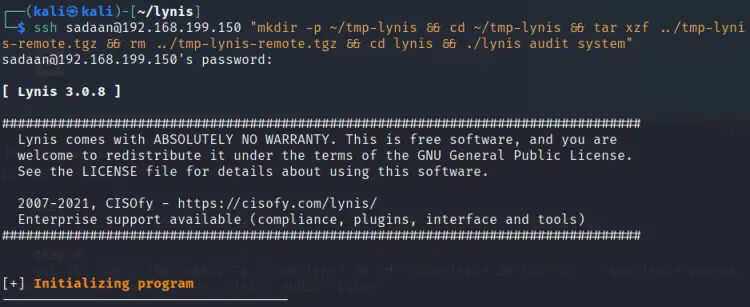
Step 6. Awesome, our tar file has now reached on the target machine, we now need to fire the below command to start scanning the target machine:
$ ssh ‘YOUR_USERNAME’@192.168.199.150 "mkdir -p ~/tmp-lynis && cd ~/tmp-lynis && tar xzf ../tmp-lynis-remote.tgz && rm ../tmp-lynis-remote.tgz && cd lynis && ./lynis audit system"
It will take some time, depending on scan size, to complete the scan, so be patient. In most cases it lasts for 2 minutes. On the terminal, you can see various tests performed by Lynis:
Sample Output:
[+] Kernel
------------------------------------
- Checking default run level [ RUNLEVEL 5 ]
- Checking CPU support (NX/PAE)
CPU support: PAE and/or NoeXecute supported [ FOUND ]
- Checking kernel version and release [ DONE ]
- Checking kernel type [ DONE ]
- Checking loaded kernel modules [ DONE ]
Found 147 active modules
- Checking Linux kernel configuration file [ FOUND ]
- Checking default I/O kernel scheduler [ NOT FOUND ]
- Checking for available kernel update [ OK ]
- Checking core dumps configuration
- configuration in systemd conf files [ DEFAULT ]
- configuration in etc/profile [ DEFAULT ]
- 'hard' configuration in security/limits.conf [ DEFAULT ]
- 'soft' configuration in security/limits.conf [ DEFAULT ]
- Checking setuid core dumps configuration [ PROTECTED ]
- Check if reboot is needed [ NO ]
[+] Memory and Processes
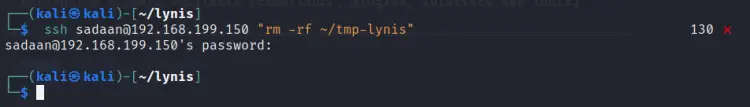
Step 7. Once the scan process is complete we can simply clean up the extracted directory ‘tmp-lynis’ on the remote machine of step 6.
$ ssh ‘YOUR_USERNAME’@192.168.199.150 "rm -rf ~/tmp-lynis"
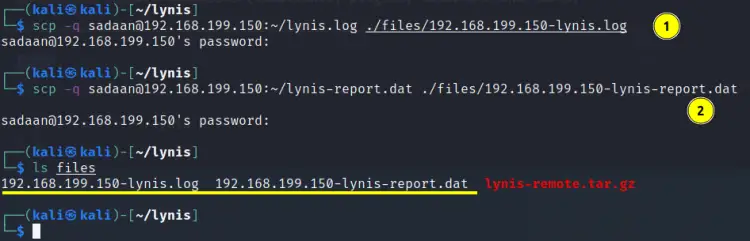
Step 8. The scan results are displayed on the Kali Linux terminal. We can also retrieve the scan log and report from the remote machine using:
scp -q ‘YOUR_USERNAME’@192.168.199.150:~/lynis.log ./files/192.168.199.150-lynis.log
scp -q ‘YOUR_USERNAME’@192.168.199.150:~/lynis-report.dat ./files/192.168.199.150-lynis-report.dat
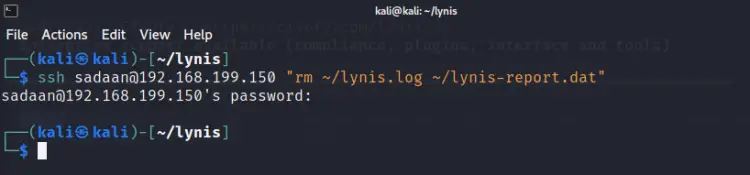
Step 9: To clean up the lynis log files (when using non-privileged account) created on the remote system, run the command:
ssh ‘YOUR_USERNAME’@192.168.199.150 "rm ~/lynis.log ~/lynis-report.dat"
That's all done. We have successfully scanned our remote system.
Wrapping Up
In this tutorial, we have learned how to scan a remote system with Lynis. If you have properly followed this tutorial, you will notice that we have not left any trace of auditing on the remote system. Lynis is a great tool for anyone looking to test their system security level. The scans are quick and provide insightful suggestions for improving the overall system security. In the next tutorial we expect to explore various details of a Lynis scan like warnings, suggestions, etc., so keep tuned with us.