Exploring the Lynis Audit Report
On this page
Lynis is a free and open-source security auditing tool and released as a GPL licensed project and is available for Linux and Unix-based Operating systems like MacOS, FreeBSD, NetBSD, OpenBSD and so on.
What will we explore here?
In this tutorial, we will try to explore the Lynis audit report and learn to apply some of the reforms it suggests. Let's now get started with this guide.
Understanding the Lynis Audit Reports
The post lynis scan left us with an enormous summary of the tests performed. To benefit from these results it is vital to understand them and apply specific supplementary action. We will first give a short summary of a few sections of the audit and then jump to the suggestion sections. In this way we will get an idea on what each specific test means and how to apply suggestions.
1. Initializing the program
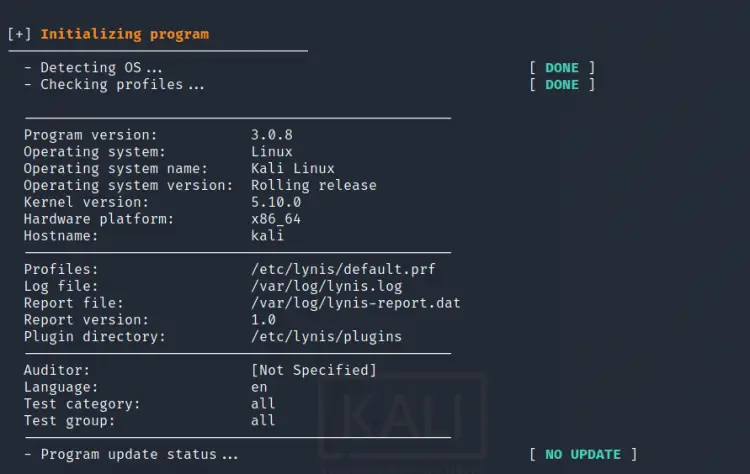
In the initialization phase, Lynis performs the basic check operation like detecting OS type, kernel version, CPU architecture, installed Lynis version, auditor name, checking for available Lynis update etc. Overall, this phase does only provides a static system and program information.
2. Plugins
Lynis provides plugins to further enhance the audit process. For e.g. the Firewall plugin provides firewall-specific services. These plugins include one or more tests, some of which are paid and available only with the enterprise edition of Lynis.
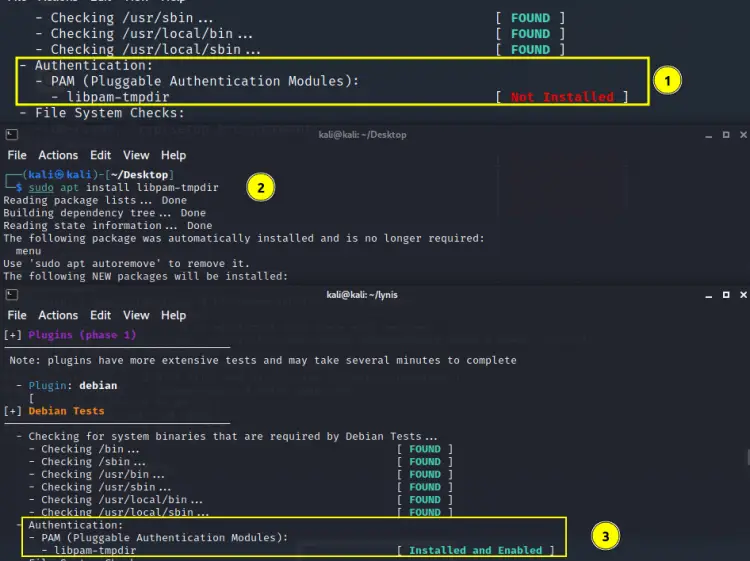
3. Debian Tests
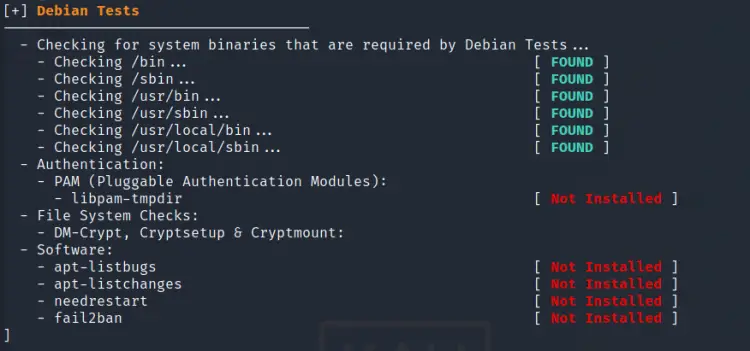
As mentioned on the test, this checks for the system utilities needed by Debian tests. For e.g. the above scan reports that ‘libpam-tmpdir’ is not installed. When we install this package the corresponding message changes from ‘Not Installed’ to ‘Installed and enabled’ as shown below:
4. Boot and Services
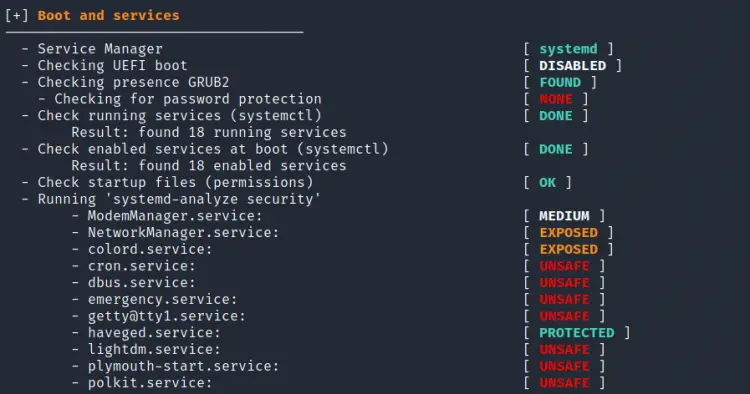
The section provides information about the service manager type(systemd in this case), running and boot-enabled service etc. Most importantly it labels the services based on their security level: Unsafe, Exposed, Protected, Medium.
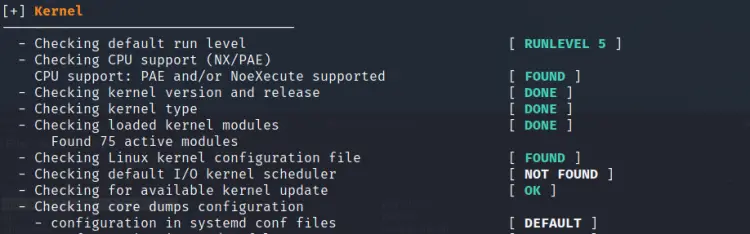
5. Kernel
Here Lynis performs a check for various kernel-specific parameters like run level, kernel version, and type, etc.
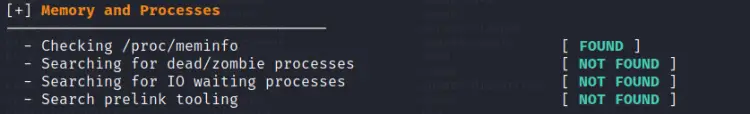
6. Memory and Processes
In this section Lynis checks for the state of processes, that is whether they are dead or in waiting state.
In a similar pattern, Lynis audits various sections of the system like services, softwares, networking, databases and so on. Describing each and every step will be a very lengthy task. Overall it generates suggestions and warnings for every section it audits. Fixing these warnings and applying subsequent suggestions help us further harden our systems. We will now move our focus on setting a few suggestions.
Fixing the Issues…
As mentioned in the previous section, Lynis populates the terminal with the scan results, it also generates a log file(lynis.log) and a report file(lynis-report.dat). You will have probably noticed that every warning and suggestion is followed by a short description and a link to the ‘Controls’ section of CISOfy website. For e.g. look at the below picture:
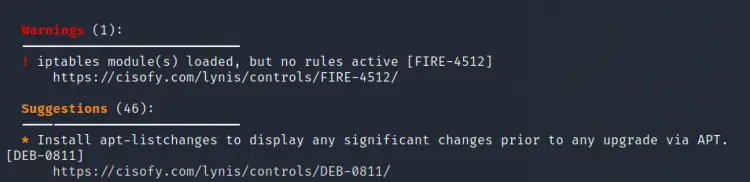
It shows that there are about 46 suggestions and 1 warning in total. It also depicts the first suggestion to install the apt-listchanges package and below it there is a link to the ‘Controls’ section of CISOfy website. Let us try to apply some of these suggestions:
1. Install apt-listchanges package
This package compares the version of an installed package with the new available one. To install this package, use:
$ sudo apt apt-listchanges
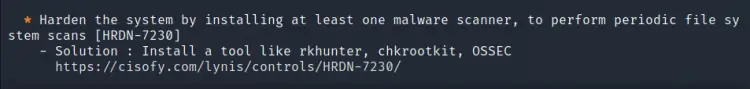
2. Malware scanner
Lynis is reporting that there is no malware scanner installed on our system. It also gives examples of such tools like rkhunter, chkrootkit and OSSEC. Let us install rkhunter on our Kali Linux:
$ sudo apt install rkhunter
3. Installing PAM security module
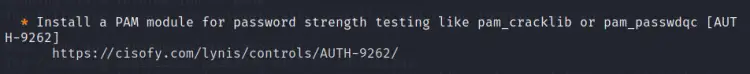
This finding suggests installing a PAM module to enable checking the password strength. For debian based systems the ‘libpam-cracklib’ package is used for this purpose. Install this tool with:
$ sudo apt install libpam-cracklib
Let us install all the above packages and re-run the Lynis audit to see if there is any reduction in the number of suggestions:
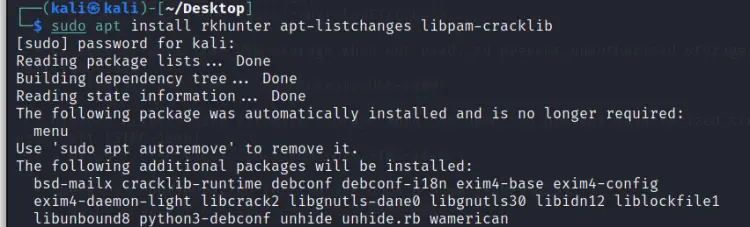
Once these packages are installed, run the audit again:
$ sudo ./lynis audit system
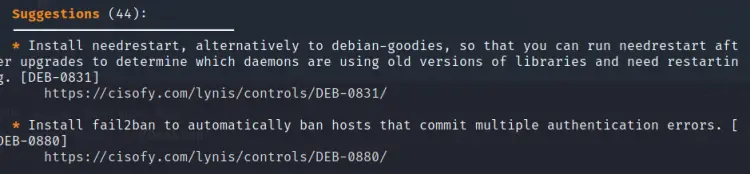
This time we can see the number of suggestions has been reduced to 44. The hardening index has also jumped from 62 to 65. Note that when we install new plugins (Lynis Enterprise edition) or fix some issue by installing new packages, the audit time may rise up, this is what happened in this case. The more you resolve issues and apply the suggestions the more your audit becomes extensive and your system becomes more hardened.
Note: While exploring a suggestion or warning, the 'show details' command can be used to see the full description using the 'test-id'. For e.g. to explore ‘KRNL-5830’ use the command:
sudo lynis show details KRNL-5830
Also, you can use the link below each test-id to see their description from the CISOfy websites.
Conclusion
One may get afraid after seeing many suggestions in the audit result for the first time. However, it is not a matter of worry. Take it as an outline for mapping your system security. Some of the suggestions are just installing a package, running a simple command while others may require you to tweak several configuration files. Just identify the issues and fix any vulnerability you discover.