Configuring CAS On Ubuntu For Two-Factor Authentication With WiKID - Page 2
User registration and logging In
Registering the token
Start your WiKID software token. Select Action, Create new domain. Enter the 12 digit domain identifier for your WiKID server. This is typically the zero-padded IP address.
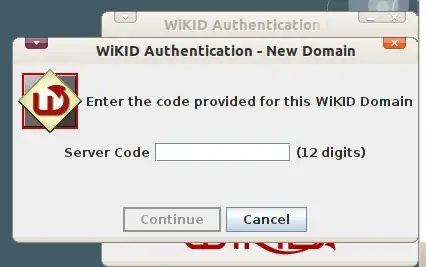
You will be prompted to set a PIN.
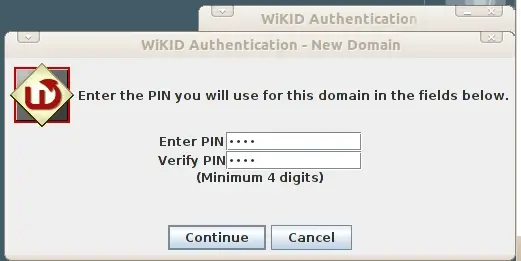
You will get back a registration code from the server. This registration must be validated for the user to login.
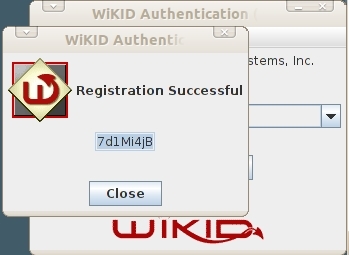
Log in to the WiKIDAdmin and click on the Users tab and then Manually validate a user. You will see your registration code.
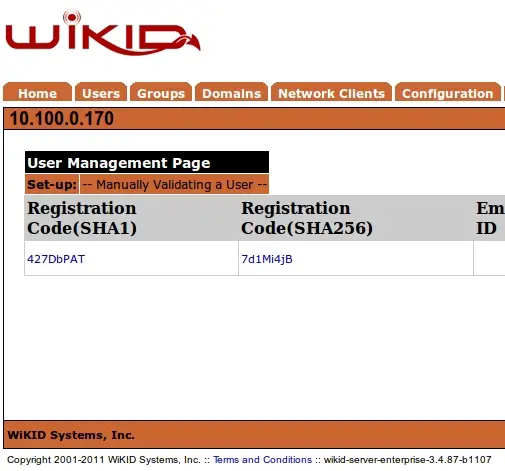
Click on the registration code and enter your username.

Now, head back to the token to the and select Get Passcode.
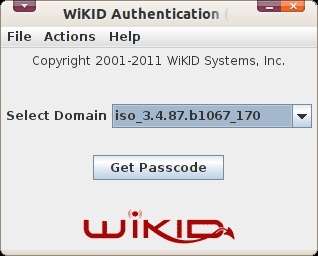
Enter your PIN.
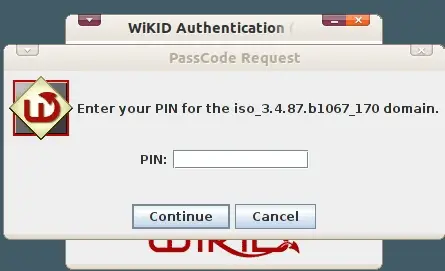
You will get back an OTP from the WiKID Strong Authentication Server.
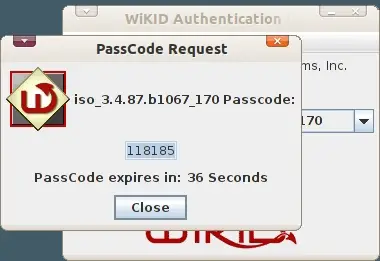
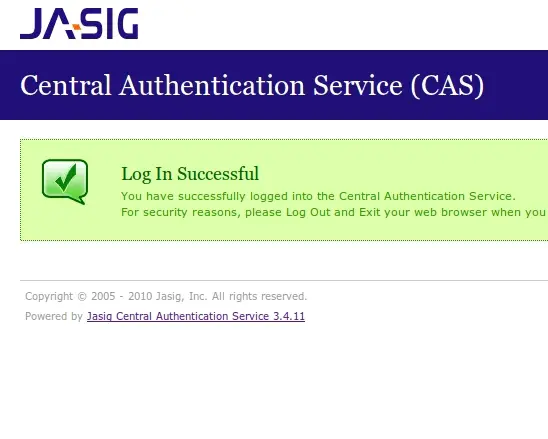
Additionally, your default browser will be opened the CAS login page as specified under the Registered URL.
CAS will forward the username and one-time passcode to the WiKID server using RADIUS. If the credentials match. the user will be authenticated.
If you run the software token in debug mode, you will see the token validating the SSL certificate for you:
Received 128 bytes from server.
validatedURL() processing response ...
validatedURL() returned url: https://cas.wikidsystems.com/cas/login
validatedURL() hash_from_server: 14Bqov7lBEMn+DavECDMovCBTF0=
validatedURL() hash_from_me: 14Bqov7lBEMn+DavECDMovCBTF0=
validatedURL() validated_url: https://cas.wikidsystems.com/cas/login
Validity check returning: https://cas.wikidsystems.com/cas/login
If there is a Man-in-the-Middle attack the user will get an error that the URL has changed and to contact the administrator. The debug output will show that the hashes do not match:
Received 128 bytes from server.
validatedURL() processing response ...
validatedURL() hash_from_server: 14Bqov7lBEMn+DavECDMovCBTF0=
validatedURL() hash_from_me: /HAtxIVzVL6yo1OjTkPca74xd8s=
Validity check returning: null
Conclusion
Single sign-in is a great tool but it creates a "keys to the kingdom" situation where compromising a single set of credentials can result in a much larger breach than without SSO. Additionally, organizations are using SSO for cloud-based services such as Google Apps.
Links
- Two-factor authentication from WiKID: http://www.wikidsystems.com
- Install Two-factor Authentication from WiKID on Ubuntu Linux: http://www.wikidsystems.com/support/wikid-support-center/installation-how-tos/How_to_install_the_WiKID_debs_on_Ubuntu
- Install Two-factor Authentication from WiKID on Redhat/Centos Linux: http://www.wikidsystems.comsupport/wikid-support-center/installation-how-tos/how-to-install-the-wikid-enterprise-rpms
- Integrating two-factor authentication and SSO with JOSSO and WiKID: https://www.howtoforge.com/adding-two-factor-authentication-to-josso

