Installation and Usage of Maltrail detection system on Ubuntu 18.04
This topic is about another open source security project "Maltrail". It is a malicious traffic detection system which utilizes the publicly available spamlist/blacklists of malicious and suspicious trails. It also uses the static trails from the various AntiViruses reports and custom user-defined lists. The malicious domains of various malware, URL of known malicious executables and IP address of known attackers are trails for this system. It has the capability of advanced heuristic mechanisms for the discovery of unknown threats (e.g. new malware). The github address of the project is: https://github.com/stamparm/maltrail/
The github page shows the resources of blacklists (i.e. feeds), static entries and trails of various malware C&Cs or sinkholes which are utilized in this detection system.
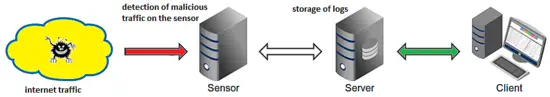
Deployment Architecture
As per the information is given on the project site, the Maltrail is based on the Traffic -> Sensor <-> Server <-> Client architecture.
Sensor(s) is a standalone component/machine running on Linux platform connected passively to the SPAN/mirroring port or transparently inline on a Linux bridge where it "monitors" the passing Traffic for blacklisted items/trails (i.e. domain names, URLs and/or IPs). The event detail is sent to the (central) Server In case of a positive match and stored inside the appropriate logging directory. If the Sensor and Server both run on the same machine (default configuration), logs are stored directly into the local logging directory. All events or log entries for the chosen (24h) period are transferred to the Client, the reporting web application is responsible for the presentation of the events. In this article, Server & Server components run on the same machine.
Prerequisites
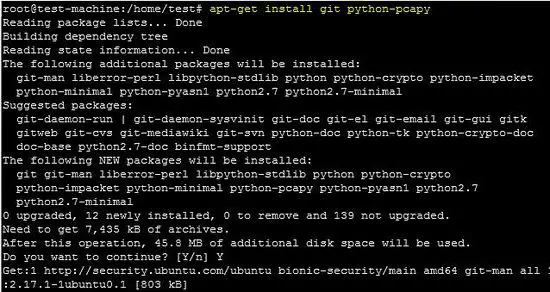
In this tutorial, Maltrail will be installed on an Ubuntu 18.04 LTS VM. To properly run Maltrail, Python 2.7 is required with pcapy package. There are no other requirements, other than to run the "Sensor and Server" component with the root privileges. The following command installs the python-pcapy package on the Ubuntu machine. It will also install required dependencies of the package.
apt-get install git python-pcapyIt can be downloaded from the corsecuity website and installed using the following command. If "python-setuptools" package is installed then install it before installation of pcapy package. The following command installs the setuptools package on Ubuntu platform.
apt-get install python-setuptools
python setup.py install
Running Maltrail System
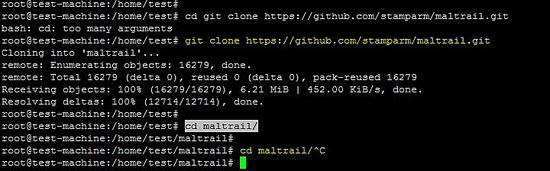
The following command downloads the latest package on the Ubuntu machine and after that run python scripts of server & sensor in the terminal
git clone https://github.com/stamparm/maltrail.git
cd maltrail/
Start Maltrail Sensor
The following command starts the sensor in the terminal.
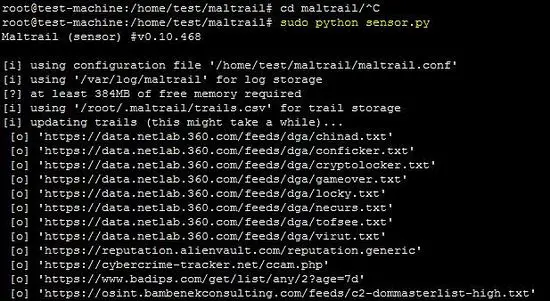
python sensor.py
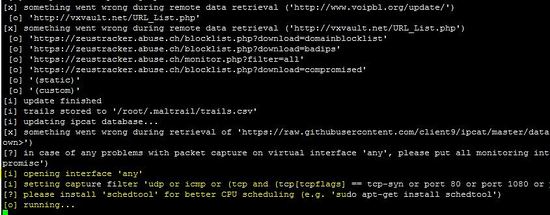
If the list of Maltrail is not updated then it will be updated while running sensor on the machine.
The above screenshot shows that the sensor is successfully running on the machine.
Start Maltrail Server
To start the "Server" on same the machine, open a new terminal and execute the following:
cd maltrail
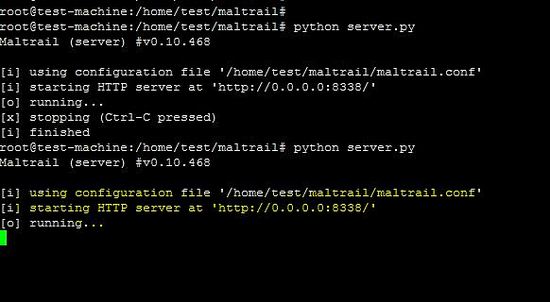
python server.py
As shown in the above snapshot, HTTP server is running on the 8338 port. The 8338 port should be allowed on the firewall if the web interface is accessed behind the firewall.
Maltrail Dashboard
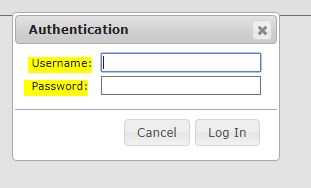
Access the reporting interface by visiting the http://local-p-ip:8338 (default credentials are admin:changeme! saved in the maltrail.conf file) from your web browser. As shown below, the user will be presented with the following authentication window. Enter credentials admin:changeme! to get inside the web portal of the Matrail.
Once inside the dashboard, admin user will be presented with the following reporting interface.
Testing Maltrail
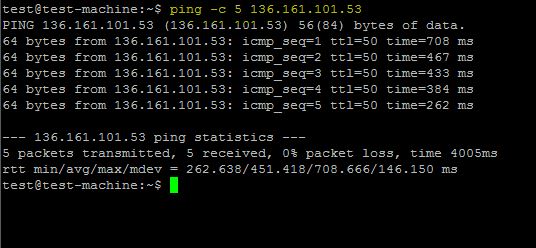
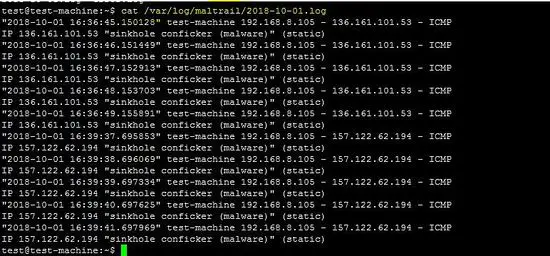
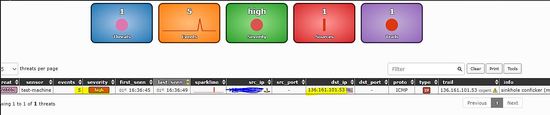
The following testing step is given on the project site. The IP address "136.161.101.53" is malicious address, so Maltrail detects it and shows in the Dashboard.
ping -c 5 136.161.101.53cat /var/log/maltrail/02-10-2018.log
As shown below both attacks (ping to a malicious IP address) are also shown in the frontend.
---------------------------------------------------------------------------------------
The top portion of the front end holds a sliding timeline and activated after clicking the current date label and/or the calendar icon. The Middle portion holds a summary of displayed events. The Events box represents the total number of events in a selected 24-hour period, where different colors represents different types of events like IP-based events, DNS-based events and URL-based events. Click on the boxes to get more detailed of each graph.
The Bottom part of the frontend holds a condensed representation of logged events in form of a paginated table.
The configuration of Maltrail Sensor/Server
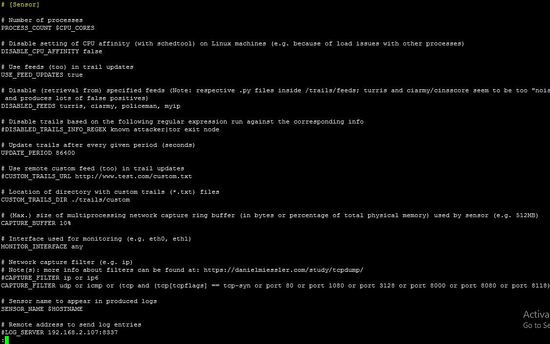
The Sensor's configuration of the Maltrail system is inside the maltrail.conf file's section [Sensor]. The configuration parameters are explained with comments. In this configuration file, user can define setting like update period of static feed, virtual or physical interface of the linux to run Maltrail system etc.
sensor section
--------------------------------------------------------------------------------------
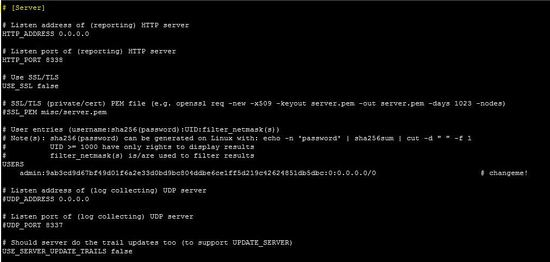
In the server section, a user can define the listening port and ip address. User can enable SSL service to protect the web traffic.
server section
Log Storage
All the detected events by Maltrail sensors are stored inside the Server's logging directory ( option LOG_DIR inside the maltrail.conf file's section to set the path of the file). All the detected events are stored with date wise.
Port sweep
It also detects too many connection attempts to certain TCP ports. The Maltrail system warns against possible port scanning because it detects heuristic mechanisms.
False positives
Maltrail is prone to "false positives", like all other security solutions,. In those kind of cases, Maltrail will (especially in case of suspicious threats) record a regular user's behaviour and mark it as malicious and/or suspicious. Like, Google search engine also scan the domains and IP address. So, sometimes legitimate IP address of the Google will become attacker because of several attempts on the legitimate domains/IP addresses.
Conclusion
This article is about he malicious traffic detection system "Maltrail" which detects the traffic using static feeds and heurisitc mechanism. It is developed in the Python and consist of two major compoents "sensor and server". It can be run on the single machine and detect traffic on any interface of the machine. It is useful to secure the network from the known attackers on the internet. Currently, it only support the detection of traffic. However, it can be integrated with other open source tools to perform blocking of IP address in the iptables firewall.