How to Install Passbolt Self-Hosted Password Manager on CentOS 7
This tutorial exists for these OS versions
- CentOS 8
- CentOS 7
On this page
- Prerequisites
- What we will do?
- Step 1 - Install Dependencies
- Step 2 - Install and Configure MySQL/MariaDB
- Step 3 - Install Nginx and PHP-FPM
- Step 4 - Generate SSL Letsencrypt
- Step 5 - Configure Nginx and PHP-FPM
- Step 6 - Download Passbolt and Generate OpenPGP Key
- Step 7 - Install Passbolt
- Step 8 - Passbolt Post-Installation
- Step 9 - Additional Security Server Setup
- Reference
Passbolt is a free and open source password manager for teams. It allows team members to store and share credentials/password securely. Passbolt is created with PHP and can be run under the LEMP stack or run as docker container.
In this tutorial, we will show you step-by-step install and configure open source password manager 'Passbolt' on CentOS 7 server. Passbolt is a web application developed with PHP, and we will run it under the LEMP (Linux, Nginx, MySQL/MariaDB, and PHP-FPM).
Prerequisites
- CentOS 7
- Root privileges
What we will do?
- Install Dependencies
- Install and Configure MariaDB Database
- Install Nginx and PHP-FPM
- Generate SSL Letsencrypt
- Configure Nginx and PHP-FPM
- Download Passbolt and Generate OpenPGP Key
- Install Passbolt
- Passbolt Post-Installation
- Additional Security Server Setup
Step 1 - Install Dependencies
The first thing that we will do for this guide is to install all package dependencies needed for the Passbolt installation, including installing EPEL and Remi PHP repositories, php composer, gcc etc.
Add the EPEL repository.
sudo yum -y install yum-utils epel-release
Add and enable the Remi PHP repository.
sudo yum -y install 'http://rpms.remirepo.net/enterprise/remi-release-7.rpm'
sudo yum-config-manager --enable 'remi-php72'
Now install packages dependencies composer, git gcc etc using the yum command below.
sudo yum -y install unzip wget composer policycoreutils-python git gcc
Wait for all packages installation.
Step 2 - Install and Configure MySQL/MariaDB
In this step, we will install the MariaDB database and then create a new database and user for Passbolt installation.
Install MariaDB server using the yum command below.
sudo yum -y install mariadb-server
After the installation is complete, start the MariaDB service and enable it to launch everytime at system boot time.
sudo systemctl start mariadb
sudo systemctl enable mariadb
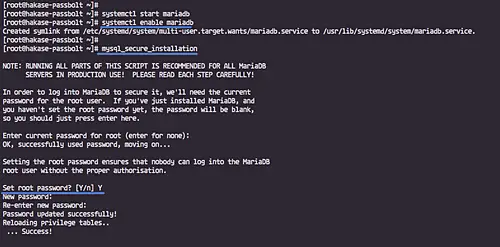
Now we need to configure the 'root' password for MariaDB. Run the 'mysql_secure_installation' command below.
mysql_secure_installation
Type your new root password.
And the MariaDB root password has been configured.
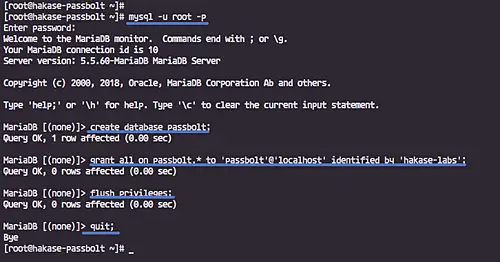
Next, login to the MySQL shell using the 'root' user.
mysql -u root -p
Create a new database and user named 'passbolt' with password 'hakase-labs', run MySQL queries below.
create database passbolt;
grant all on passbolt.* to 'passbolt'@'localhost' identified by 'hakase-labs';
flush privileges;
quit;
The MariaDB server has been installed on CentOS 7 server, and the database for 'Passbolt' installation has been created.
Step 3 - Install Nginx and PHP-FPM
After installing the MariaDB server, we will install Nginx from the EPEL repository, and PHP-FPM packages using the Remi repository.
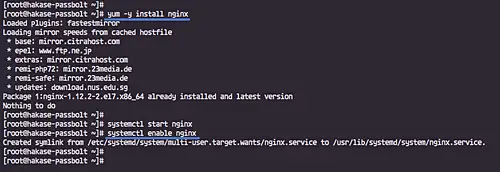
Install Nginx web server.
sudo yum -y install nginx
After the installation is complete, start the Nginx service and enable it to launch everytime at system boot.
sudo systemctl start nginx
sudo systemctl enable nginx
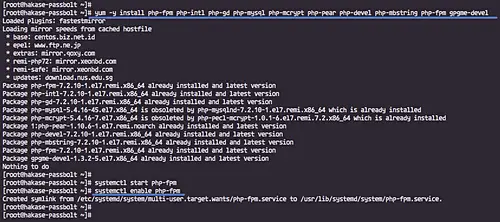
Now install PHP-FPM with all extensions needed using the yum command below.
sudo yum -y install php-fpm php-intl php-gd php-mysql php-mcrypt php-pear php-devel php-mbstring php-fpm gpgme-devel
And if the installation is complete, start the PHP-FPM service and enable it launch everytime at system boot.
sudo systemctl start php-fpm
sudo systemctl enable php-fpm
The Nginx web server and PHP-FPM has been installed.
Step 4 - Generate SSL Letsencrypt
Install the certbot tool on the system.
sudo yum -y install certbot
Now stop the nginx service.
sudo systemctl stop nginx
And generate SSL Letsencrypt for the passbolt domain name 'passbolt.hakase.io'.
Run the certbot command below.
sudo certbot certonly --standalone --agree-tos --no-eff-email --email [email protected] -d passbolt.hakase.io
The certbot tool will run a temporary web server for the verification.
And when it's complete, you will get your certificate on the '/etc/letsencrypt/live/' directory.
Step 5 - Configure Nginx and PHP-FPM
In this step, we will configure the Nginx web server by creating a new virtual host configuration for the Passbolt, and configure the PHP-FPM and install the PHP GnuPG support.
Configure PHP-FPM
Go to the '/etc/php-fpm.d' directory and edit the default pool configuration 'www.conf' using vim editor.
cd /etc/php-fpm.d/
sudo vim www.conf
Change the default user and group to the 'nginx' user.
user = nginx group = nginx
Change the port listen for PHP-FPM to the sock file as below.
listen = /var/run/php-fpm/php-fpm.sock
Uncomment those lines below and change listen.owner and listen.group for the sock file to 'nginx'.
listen.owner = nginx listen.group = nginx listen.mode = 0660
Save and exit.
Now we need to change the owner of the PHP session directory and install the PHP GnuPG extension support.
Change the permission of php session directory.
sudo chgrp nginx /var/lib/php/session
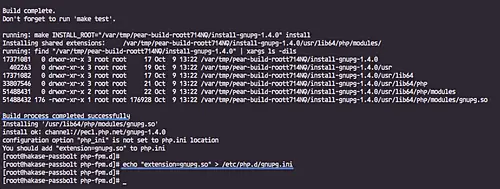
Install the PHP GnuPG extension using the pecl command and activate it.
sudo pecl install gnupg
echo "extension=gnupg.so" > /etc/php.d/gnupg.ini
The PHP GnuPG extension has been installed.
Configure Nginx Virtual Host
Go to the '/etc/nginx/conf.d' directory and create a new virtual host file 'passbolt.conf'.
cd /etc/nginx/conf.d/
sudo vim passbolt.conf
Paste configurations below.
server {
listen 443;
server_name passbolt.hakase.io;
ssl on;
ssl_certificate /etc/letsencrypt/live/passbolt.hakase.io/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/passbolt.hakase.io/privkey.pem;
ssl_protocols TLSv1.2;
ssl_prefer_server_ciphers on;
ssl_ciphers ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AESGCM:RSA+AES:RSA+3DES:!aNULL:!MD5:!DSS;
ssl_session_tickets off;
root /var/www/passbolt;
location / {
try_files $uri $uri/ /index.php?$args;
index index.php;
}
location ~ \.php$ {
fastcgi_index index.php;
fastcgi_pass unix:/var/run/php-fpm/php-fpm.sock;
fastcgi_split_path_info ^(.+\.php)(.+)$;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param SERVER_NAME $http_host;
}
location ~* \.(jpe?g|woff|woff2|ttf|gif|png|bmp|ico|css|js|json|pdf|zip|htm|html|docx?|xlsx?|pptx?|txt|wav|swf|svg|avi|mp\d)$ {
access_log off;
log_not_found off;
try_files $uri /webroot/$uri /index.php?$args;
}
}
Save and exit.
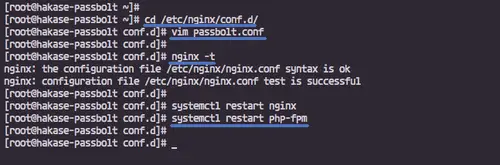
Test the nginx configuration and make sure there is no error.
sudo nginx -t
Now restart both Nginx and PHP-FPM services.
sudo systemctl restart nginx
sudo systemctl restart php-fpm
Configurations of Nginx web server and PHP-FPM has been completed successfully.
Step 6 - Download Passbolt and Generate OpenPGP Key
In this step, we will download the passbolt web application and generate a new OpenPGP key that will be used for the Passbolt API.
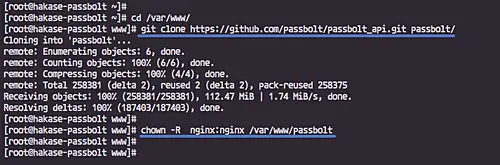
Go to the '/var/www' directory and clone the passbolt web application.
cd /var/www/
git clone https://github.com/passbolt/passbolt_api.git passbolt/
Now install the 'haveged' package and start the service.
sudo yum -y install haveged
sudo systemctl start haveged
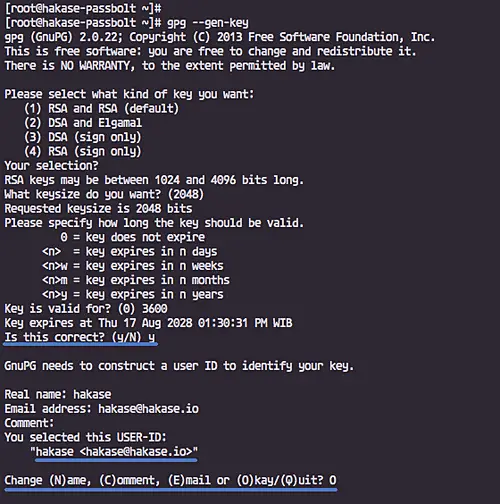
Generate a new OpenPGP key using the gpg command below.
gpg --gen-key
Type your details such as email, the expiration days etc.
Note:
- The PHP GnuPG extensions don't support the OpenPGP Key passphrase, so let the passphrase stay blank.
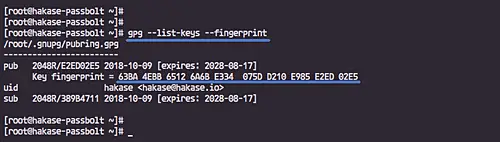
After it's complete, check all key available and write down the 'fingerprint' of your key.
gpg --list-keys --fingerprint
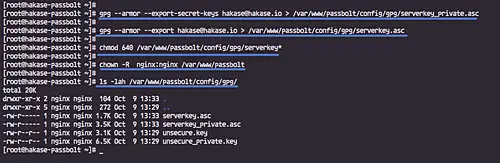
Now export the public and private key to the '/var/www/passbolt' directory.
gpg --armor --export-secret-keys [email protected] > /var/www/passbolt/config/gpg/serverkey_private.asc
gpg --armor --export [email protected] > /var/www/passbolt/config/gpg/serverkey.asc
And change all those keys permission and owner of the '/var/www/passbolt' directory.
sudo chmod 640 /var/www/passbolt/config/gpg/serverkey*
sudo chown -R nginx:nginx /var/www/passbolt
The Passbolt web application has been downloaded, and the OpenPGP key has been created.
Step 7 - Install Passbolt
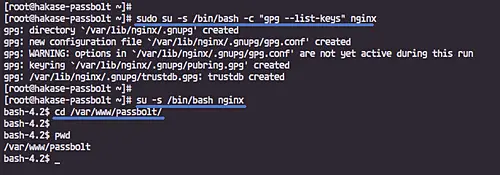
Before installing all dependencies for 'Passbolt', we need to initialize keyring of gpg key for nginx user.
Run the command below.
sudo su -s /bin/bash -c "gpg --list-keys" nginx
Now login to the 'nginx' user and go to the '/var/www/passbolt' directory.
su -s /bin/bash nginx
cd /var/www/passbolt/
Install all passbolt dependencies using the composer command below.
composer install --no-dev
When it's complete, copy the default config file of the app and edit it with vim.
cp config/passbolt.default.php config/passbolt.php
vim config/passbolt.php
In the 'App' section, change the domain name with your own domain name.
'App' => [
// A base URL to use for absolute links.
// The url where the passbolt instance will be reachable to your end users.
// This information is need to render images in emails for example
'fullBaseUrl' => 'https://passbolt.hakase.io',
],
In the 'Datasources' configuration, type your details database info.
// Database configuration.
'Datasources' => [
'default' => [
'host' => 'localhost',
//'port' => 'non_standard_port_number',
'username' => 'passbolt',
'password' => 'hakase-labs',
'database' => 'passbolt',
],
],
Under the database configuration, add a new 'ssl' configuration to force all connection to secure https.
'ssl' => [
'force' => true,
],
For the SMTP mail configuration, change everything with your details.
// Email configuration.
'EmailTransport' => [
'default' => [
'host' => 'localhost',
'port' => 25,
'username' => 'user',
'password' => 'secret',
// Is this a secure connection? true if yes, null if no.
'tls' => null,
//'timeout' => 30,
//'client' => null,
//'url' => null,
],
],
'Email' => [
'default' => [
// Defines the default name and email of the sender of the emails.
'from' => ['passbolt@your_organization.com' => 'Passbolt'],
//'charset' => 'utf-8',
//'headerCharset' => 'utf-8',
],
],
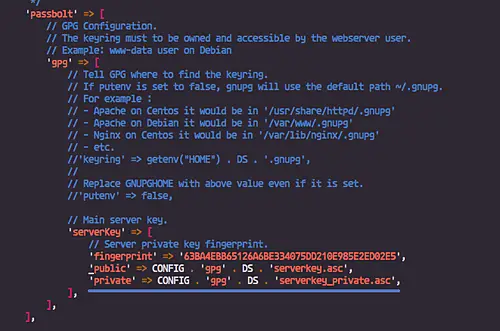
And lastly, paste the 'fingerprint' of your OpenPGP key and uncomment those public and private configuraiton lines.
'serverKey' => [
// Server private key fingerprint.
'fingerprint' => '63BA4EBB65126A6BE334075DD210E985E2ED02E5',
'public' => CONFIG . 'gpg' . DS . 'serverkey.asc',
'private' => CONFIG . 'gpg' . DS . 'serverkey_private.asc',
],
Save and exit.
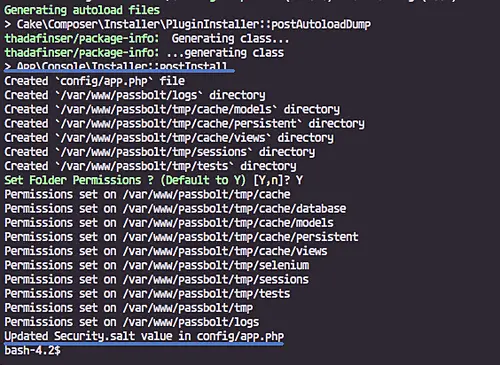
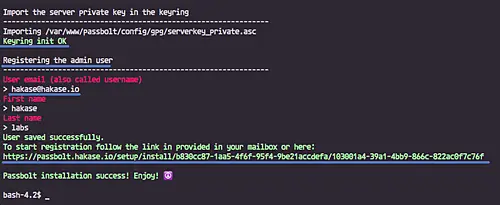
Now install 'Passbolt' using the command below.
./bin/cake passbolt install
You will be asked to create a new admin user and password - type your details.
And in the end, you will be given the 'registration' link, write it down on your note.
Step 8 - Passbolt Post-Installation
Open your web browser and install the 'Passbolt' extensions of your web browser.
Following is the link of passbolt extension for Chrome browser. Install the extension.
https://chrome.google.com/webstore/detail/passbolt-extension
Now open a new tab and paste the 'registration' link given to the address bar. Mine was:
https://passbolt.hakase.io/setup/install/b830cc87-1aa5-4f6f-95f4-9be21accdefa/103001a4-39a1-4bb9-866c-822ac0f7c76f
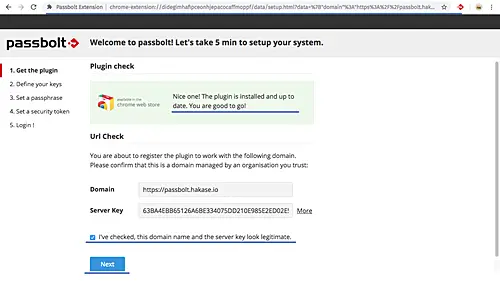
And you will a page similar to the one shown below.
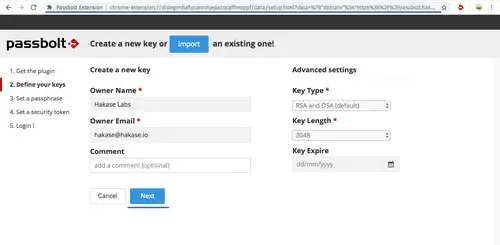
Check the box on the bottom and click the 'Next' button. Now you will be asked for creating a new key for the user.
Click 'Next' button.
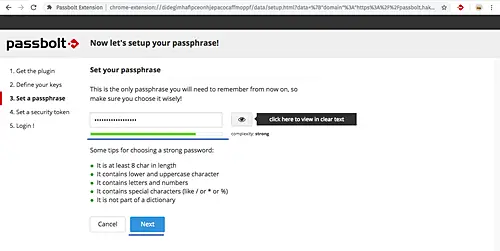
Setup the 'Passphrase', type your strong passphrase.
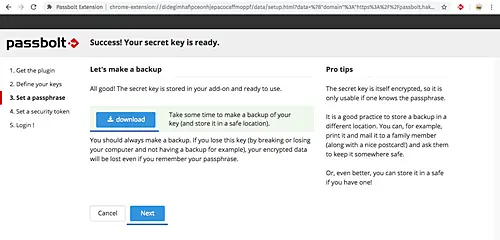
Click 'Next' button. Backup your key by pressing the 'Download' button and click 'Next' again.
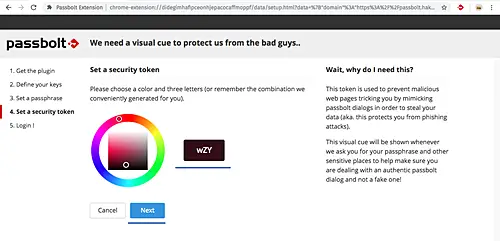
For the security token, leave it default and click 'Next'.
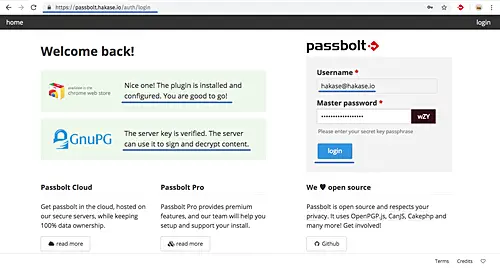
And you will be redirected to the Passbolt login page.
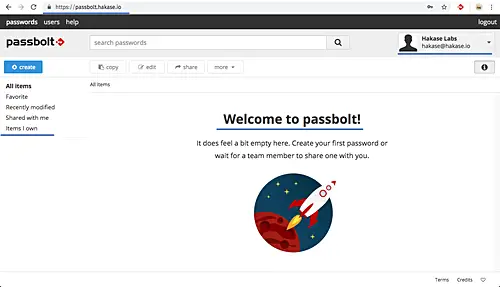
Type your 'Passphrase' and click 'Login'. And you will see the Passbolt user Dashboard as below.
Passbolt open source password manager installation on CentOS 7 has been completed successfully.
Step 9 - Additional Security Server Setup
- Setup the Firewalld
Open new HTTP, HTTPS, and SMTP ports on the server.
sudo firewall-cmd --add-service=http --permanent
sudo firewall-cmd --add-service=https --permanent
sudo firewall-cmd --add-service=smtp --permanent
Now reload the firewalld configuration.
sudo firewall-cmd --reload
- Setup Selinux Permission
Permission for the 'Passbolt' webroot directory.
sudo semanage fcontext -a -t httpd_sys_content_t '/var/www(/.*)?'
sudo semanage fcontext -a -t httpd_sys_rw_content_t '/var/www/passbolt/tmp(/.*)?'
sudo semanage fcontext -a -t httpd_sys_rw_content_t '/var/www/passbolt/logs(/.*)?'
sudo restorecon -Rv /var/www
Permission for the Nginx gnupg keyring directory.
sudo semanage fcontext -a -t httpd_sys_rw_content_t '/var/lib/nginx/.gnupg(/.*)?'
sudo restorecon -Rv /var/lib/nginx/.gnupg