How to install and use SoftHSM on Ubuntu 16.04 LTS
Hardware/software tokens or Hardware Security Modules (HSM) are used with different applications to store cryptographic keys (public & private ) and certificates. For example, NitroKey and Smartcard-HSM are a couple of HSMs. However, there also exist some software alternatives like SoftHSM(v2), which, specifically, is being developed as a part of the OpenDNSSEC project..
SoftHSM is basically an implementation of a cryptographic store accessible through a PKCS #11 interface. The PKCS#11 interface is used to communicate or access the cryptographic devices such as HSM (Hardware Security Modules) and smart cards. The primary purpose of HSM devices is to generate cryptographic keys and sign/encrypt information without revealing the private key to the others.
To give you a quick background, it was not possible for OpenDNSSEC users to buy new hardware token for the storage of cryptographic keys. So, to counter this issue, OpenDNSSEC started providing "SoftHSM", a software implementation of a generic cryptographic device with a PKCS#11 interface. SoftHSM is designed to meet the requirements of OpenDNSSEC and also work with other cryptographic products.
Dependencies
Botan or OpenSSL cryptographic libraries can be used with the SoftHSM project. If Botan is used with SoftHSM, then make sure that it has support for GNU MP (--with-gnump), something which will improve the performance during public key operations.
Installation
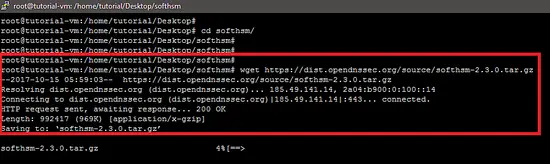
SoftHSM is available from the OpenDNSSEC website, and it can be download using the wget command in the following way.
wget https://dist.opendnssec.org/source/softhsm-2.3.0.tar.gz
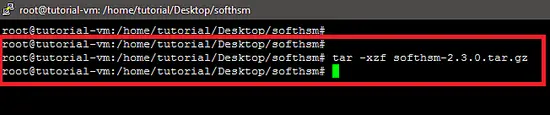
Now, extract the package using the tar command in the following way.
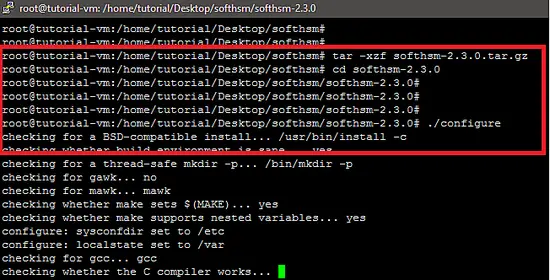
After extraction, run the configure script to check dependencies of the SoftHSM software.
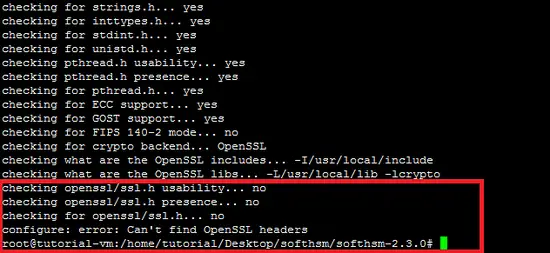
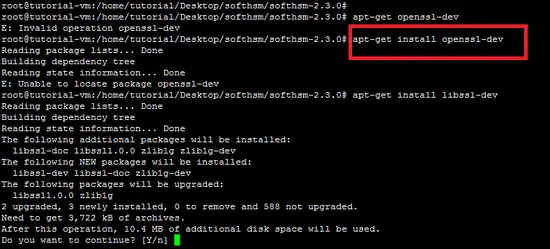
./configure The following snapshot shows that the configure script shows an error due to missing "OpenSSL header" package.
So resolve this, install the "openssl-dev" package in the way highlighted as below.
apt-get install openssl-dev
The output of the configure script shows that all required packages are now available for the compilation of the tool.
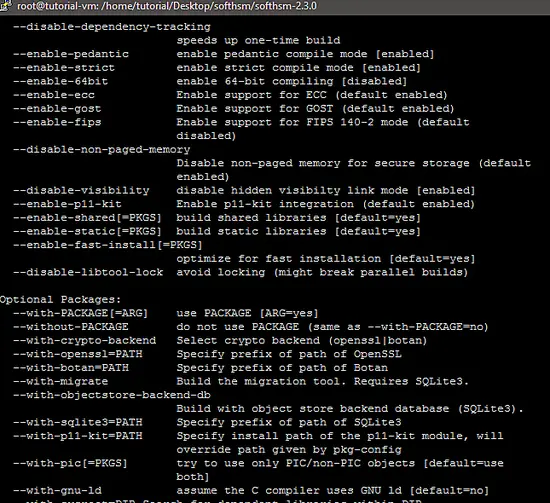
The following snapshot shows the options available for the configure script of the SoftHSM tool.
All options offered by the configure script can be accessed through the following command:
./configure --help --disable-ecc Disable support for ECC (default enabled)
--disable-gost Disable support for GOST (default enabled)
--disable-visibility Disable hidden visibilty link mode [enabled]
--with-crypto-backend Select crypto backend (openssl|botan)
--with-openssl=PATH Specify prefix of path of OpenSSL
--with-botan=PATH Specify prefix of path of Botan
--with-migrate Build the migration tool. Used when migrating
a SoftHSM v1 token database. Requires SQLite3
--with-objectstore-backend-db
Build with database object store (SQLite3)
--with-sqlite3=PATH Specify prefix of path of SQLite3
--disable-p11-kit Disable p11-kit integration (default enabled)
--with-p11-kit=PATH Specify install path of the p11-kit module, will
override path given by pkg-config
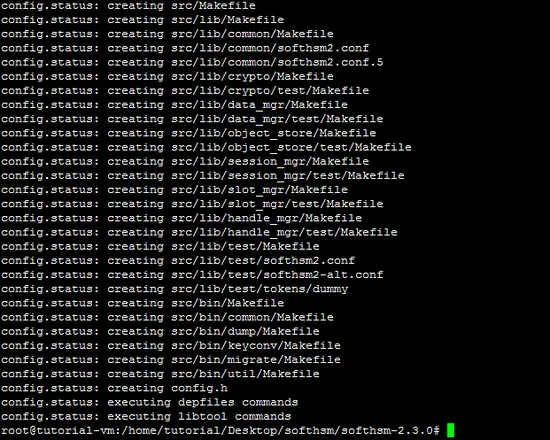
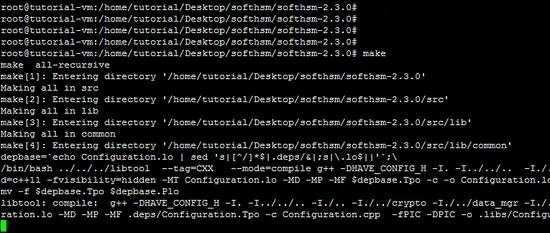
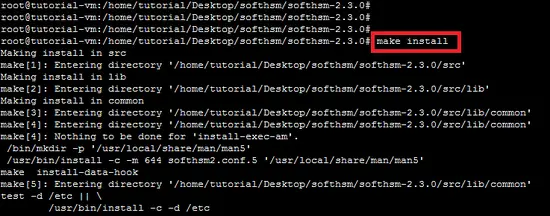
Now, run the make command to compile the source code of SoftHSM.
make Next, run "make install command" to install the SoftHSM tool.
make installConfiguration file
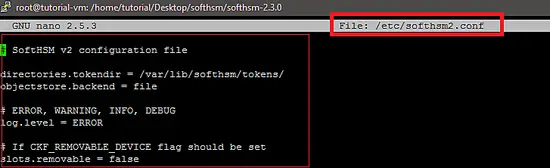
The default location of the config file is /etc/softhsm2.conf which can be changed by setting the SOFTHSM2_CONF environment variable.
export SOFTHSM2_CONF=Path_of_SoftHSM_Conf_fileThe default setting of SoftHSM is shown in the following snapshot.
Initialize Soft Token
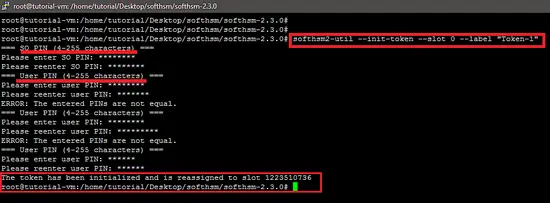
The very first step to use SoftHSM is to use initialize it. We can use the "softhsm2-util" or the "PKCS#11" interface to initialize the device. The following snapshot shows the initialization of the SoftHSM device.
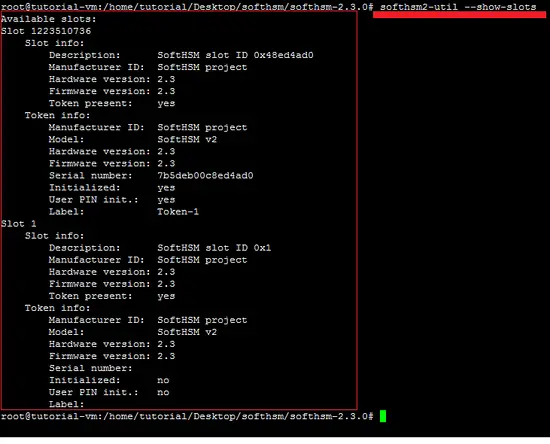
softhsm2-util --init-token --slot 0 --label "Token-1" The Security Officer (SO) PIN is used to re-initialize the token and the user PIN is handed out to the application so it can interact with the token (like usage with Mozilla Firefox). That's why, set both SO and user PIN. Once a token has been initialized, more slots will be added automatically to a new uninitialized token. Initialized tokens will be reassigned to another slot based on the token serial number. It is recommended to find and interact with the token by searching for the token label or serial number in the slot list/token info.
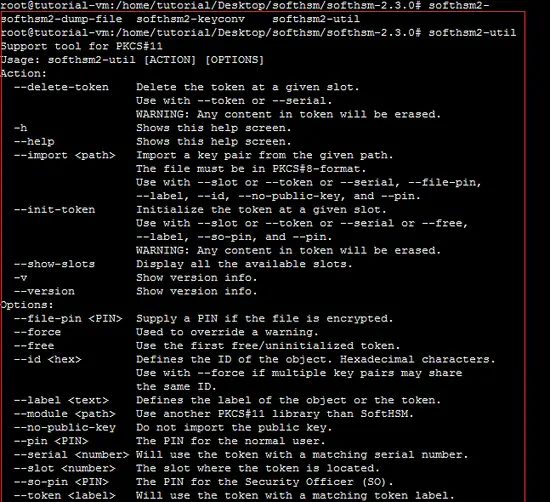
Other options of the "softhsm2-util" are shown below.
The following snapshot shows the slots of the token.
Backup
All tokens and their objects are stored in the location given by softhsm2.conf. Backup can thus be done as a regular file copy.
SoftHSM with OpenSC Utilities
In this tutorial, PKCS11 utilities of the OpenSC project are used to access the SoftHSM device. Details about the installation and usage of "OpenSC" is available on howtoforge site.
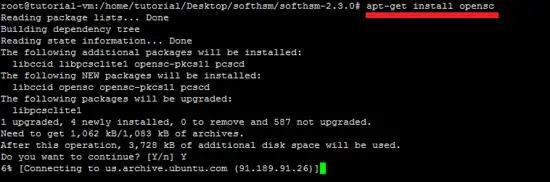
apt-get install opensc
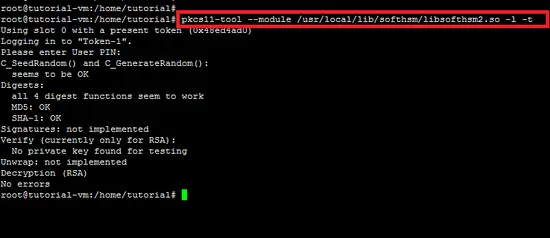
The following snapshot shows that PKCS#11 command is run on the SoftHSM. The "-t" switch is used to test the mechanism of SoftHSM.
pkcs11-tool --module /usr/local/lib/softhsm/libsofthsm2.so -l -t
Conclusion
In this article, we discussed how the software-based HSM tool SoftHSM can be installed and initialized on the Ubuntu platform. It can be configured using PKCS11 standard for the HSM/Smartcard to access the devices.