How to secure an SSL VPN with one-time passcodes and mutual authentication - Page 2
Configure SSL-Explorer
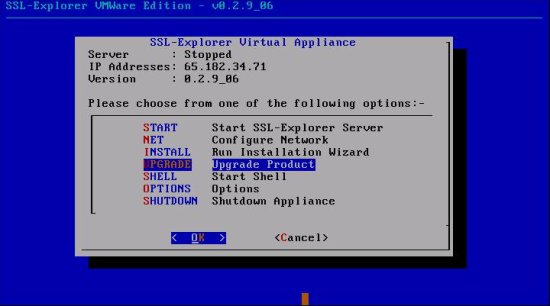
Update the VMware image
The first thing to do is to make sure that you have updated to the latest VMware version. From the shell, select Upgrade:
We are using the 0.2.14_01 Enterprise Edition of SSL-Explorer.
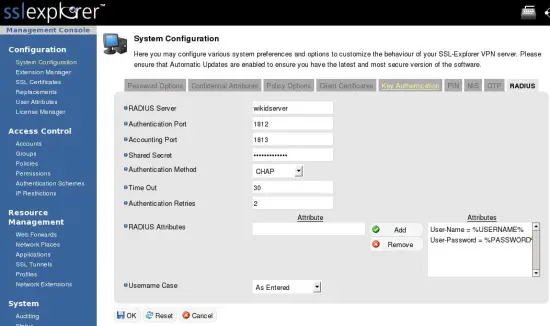
Add the WiKID Server via Radius
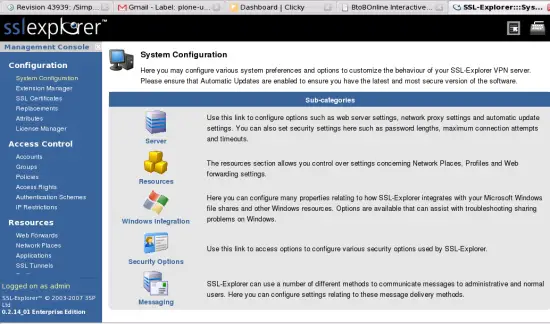
Starting from the Main screen, click on Security Options
Then click on the Radius tab and enter the domain name of your WiKID server and the shared secret. Those are the only fields that need changing.
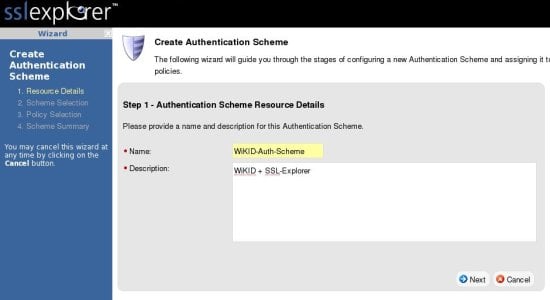
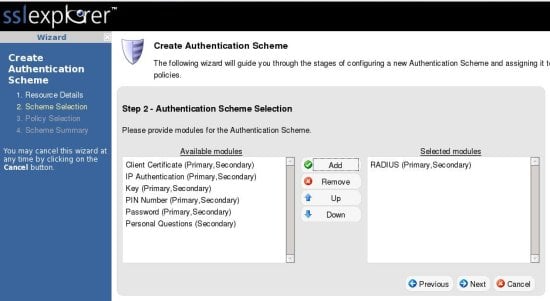
Next we will create an authentication scheme for WiKID. From the main screen, click on the Authentication Scheme link in the left hand pane, then click on Create New Scheme on the right hand side. That will bring up the scheme creation wizard:
Now assign the Radius module to this scheme:
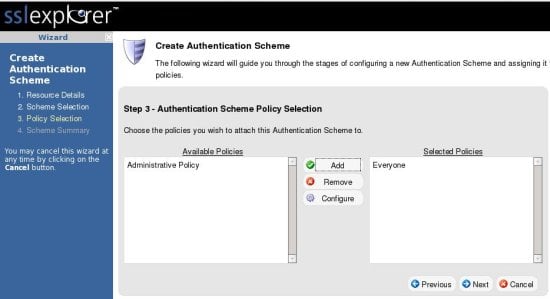
And assign the policy to Everyone. You could also create a new policy and add selective users.
Click Finish on the next screen to save the scheme.
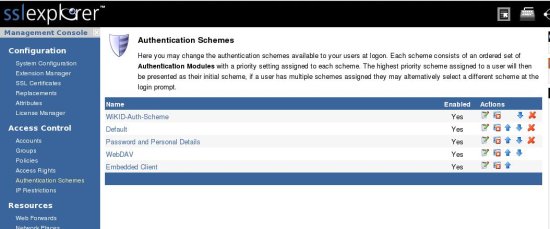
Now, from the main Authentication Scheme page, move the newly created WiKID-Auth-Scheme to the top.
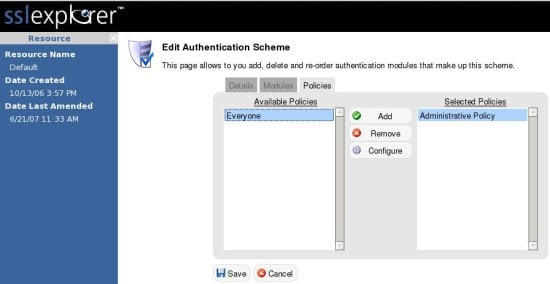
In order to require WiKID two-factor authentication, you will need to turn off the Default and Password and Personal Details Schemes for Everyone. Remember to not turn them off from the Administrative Policy until after you have setup the Admin user in WiKID! Click on each of the two policies to be removed and their respective policy tabs and move Everyone from the Selected box to the Available box:
Test Mutual Authentication
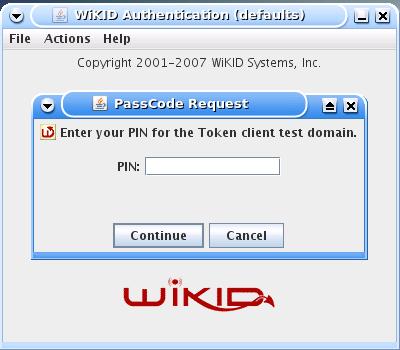
Lauch the WiKID token client and select the SSL-Explorer VPN domain you created and enter your PIN:
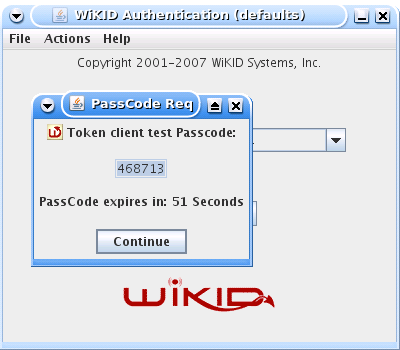
In the background, the token client is going to the domain's registerered URL, getting the SSL certificate and hashing it so it can compare it to the downloaded hash. If the hashes match, you will get the one-time passcode back, and it will automatically be pasted into the clipboard:
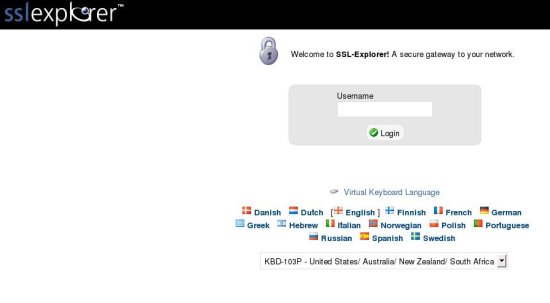
and your default browser will be launched to the registered URL:
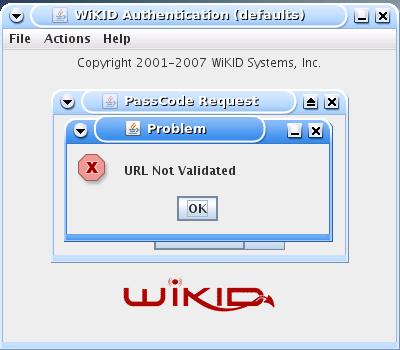
However, if the certificates do not match, the user will get an error:
This message tells the user that something is amiss and not to proceed.
Conclusion
SSL VPNs gained popularity as a ubiquituous access method that was more secure than PPTP and far simpler than IPSec VPNs. Unfortunately, they also gained popularity before the weaknesses of WiFi were widely known and before new compliance mandated two-factor authentication for so many companies. There is no need to dump your SSL-based VPNs. You just need to address the increased risk of man-in-the-middle attacks by deploying one-time passwords for session authentication and strong, mutual authentication.