New Features In Firewall Builder 4.0
- "Single rule compile"
- Changes and improvements in the GUI
- Password caching in built-in installer
- Customazable templates ("configlets")
- Changes in the structure of generated Linux firewall script
- Support for high availability firewall configurations
-
- Failover and state synchronization groups in a Linux cluster
- Failover and state synchronization groups in an OpenBSD cluster
- Failover and state synchronization groups in a PIX cluster
- Handling of the cluster rule set and member firewalls rule sets
- Examples of cluster configurations
- Support for OpenWRT and DD-WRT
- Branching rules in NAT
- Incremental management of IP addresses, VLAN, bridge and bonding interface configuration
- Built-in installer is much faster when working with Cisco routers and ASA (PIX) firewalls
- Using EEM for automatic rollback of the configuration changes with Cisco routers
- Automatic generation of "mirrored" rules for Cisco routers
Firewall Builder 4.0 is a major upgrade, it adds many improvements across all components of the program. To name a few, it adds support for the high availability firewall configurations; improves the way generated script manages IP addresses and adds ability to manage VLAN, bridge and bonding interfaces; the GUI now has undo/redo facility of unlimited depth and can compile a single rule and immediately show the result. There are many other improvements and changes, all listed in the Firewall Builder 4.0 Release Notes.
If you are not familiar with Firewall Builder, you can find many introductory articles on the Internet and our own project web site. Here is a short list:
Firewall Builder 4.0 is currently in public beta testing. Latest binary packages and source tar.gz archives are distributed from the SourceForge download pages, commercial binary Windows and Mac OS X packages are available for download from the project web site. Please file bug reports using Source Forge bug tracking system.
In this article I am going to explore most interesting and significant new features of the new version. You can find more information on each feature and detailed HOWTO guides in the Firewall Builder Users Guide.
"Single rule compile"
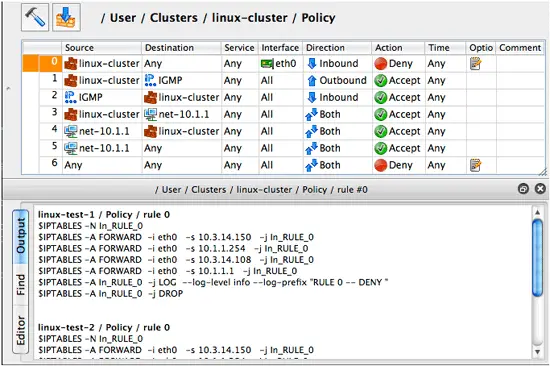
While you're developing your firewall policy, you can now compile individual rules to confirm that they do what you intend. To do this, right-click anywhere in the rule to open context menu, then select menu item "Compile". Or, highlight the rule and use keyboard shortcut "x". This is a great way to experiment with fwbuilder and see what it generates for different rule configurations built in the GUI. This feature works for all supported firewall platforms and all types of rules (Policy, NAT and routing).
Figure 1. Generated iptables script for the rule #0 is shown in the GUI
Changes and improvements in the GUI
The GUI was redesigned to help reduce unnecessary clicks and streamline the workflow, especially for situations with many objects in the object tree. The editor panel and object tree are now detachable. You can "float" these windows and rearrange them on the screen any way you want. If you work with several data files opened simulteneously, each of them appears its own project window with object tree and rules but they all share the same editor panel.
Figure 2. Floating object tree panel
Object editor panel can also float, making it easier to keep the tree, rule set panel and editor open on a machine with small screen such is a laptop, and still have enough rules visible at once. You can also change the font used to show objects in the tree and in rules.
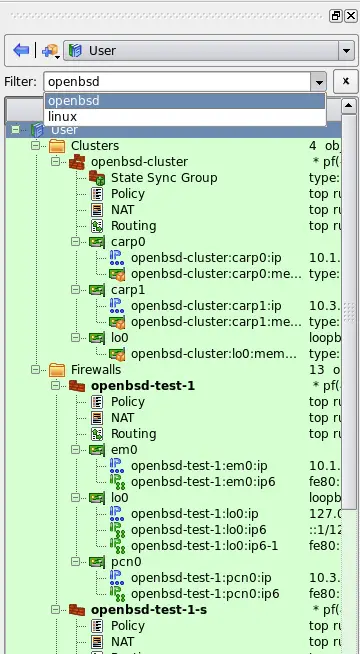
A new "Filter" input field has been added above the object tree. Typing fragment of the name in this field automatically limits set of objects shown in the tree to those that match what was typed. The filter maintain history of strings entered in it for the duration of the session.
Figure 3. Applying filter to the object tree
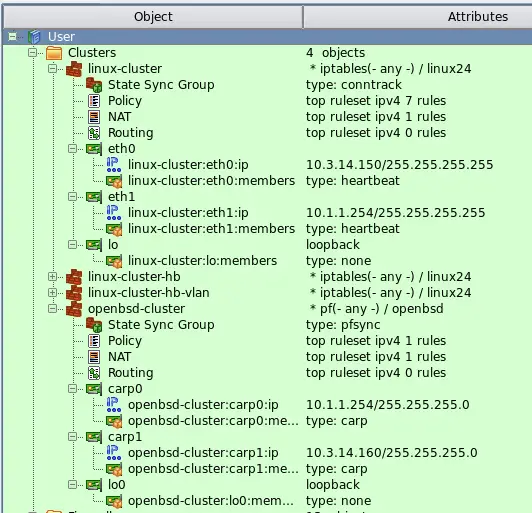
The GUI can show brief summary of object attributes in the second column in the object tree. This is controlled by a checkbox in the global preferences dialog, tab "Objects" and is off by default. The first column always shows object icon and its name, the second (optional) column shows its attributes.
Figure 4. Second column shows attributes of the objects in the tree
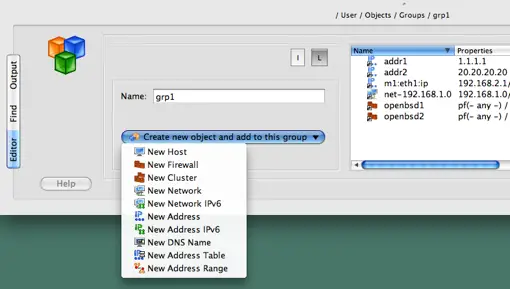
Another convenient shortcut is a new button called "Add object to a groups directly from the group dialog" that appears in the group object dialog. When you click this button, a menu appears that allows you to create new object and add it to the group in one operation. This is shown in the screenshot below:
Figure 5.
The GUI now has unlimited Undo/Redo facility accessible via standard keyboard shortcuts Ctrl-Z and Ctrl-Y (Cmd-Z and Cmd-Y on Mac OS X). You monitor undo stack using special panel that you can open using menu "View/Undo stack". Clicking on the entries in undo stack rolls operations back or forward.
One of the most annoying features of the old version was the neccesity to click "Apply" after each change made to an object. This amounted to significant number of clicks when you had to cerate and edit many objects. Firewall Builder 4.0 did away with this button, all changes made in an object dialog are saved into the object immediately. This does not change the data in the .fwb file, only objects in memory. Combined with Undo, this allows for faster object editing and roll back of changes.
Error and warning messages generated by the policy compilers are highlighted in the compiler output panel when you compile single rule. When you compile all rules of the firewall using toolbar buttons or main menu items "Compile" or "Install", errors and warnings are also highlighted in the dialog. Clicking on the error or warning message opens corresponding firewall and selects the rule that caused it.
Firewall Builder has a great way to help you create new firewall object from scratch faster, that is a collection of template objects. These objects come preconfigured with interfaces, ip addresses and basic rules. Unfortunately, most likely these ip addresses do not match addresses you use in your network, which means in the past you had change addresses of interfaces after the new firewall object has been created. This is not too difficult, but it wasn't enough. You had to use search and replace function to change addresses of all objects used in the rules as well. This was more tedious and potentially error-prone.
Now you can change ip addresses of interfaces of the new firewall while it is being created in the wizard dialog. When you create new firewall object from a template, the "new firewall" wizard includes interface editor page where you can change addresses as well as interface names and types (static or dynamic). The program not only changes addresses of interfaces, it also scans policy and NAT rules of the template looking for network objects that match original template addresses and replaces them with network objects that match new ones.
Password caching in built-in installer
Built-in policy installer uses ssh to communicated with the firewall and needs user name and password for authentication. Firewall Builder does not store passwords permanently, which means you have to enter the password every time you want to update configuration of the firewall. Ssh agent certainly helps alleviate this problem, but if you do not use the agent, you still have to type the password again and again. Some devices do not even support ssh agent authentication, these are Cisco routers and ASA firewalls.
Firewall Builder 4.0 introduces password caching that can help in this situation. Built-in installer can remember firewall password (and enable password for Cisco) for the duration of the session. Passwords are never stored permanently in any form, encrypted or plain text, they are only kept in memory of working Firewall Builder GUI instance. You need to enter password once when you activate generated policy for the firs time. If you keep the program open and need to modify and activate policy again, the password fields in the installer dialog can be filled automatically. The feature is optional and is off by default.
Warning: using this feature creates certain risk if working Firewall Builder GUI is left unattended on unlocked workstation. Someone may walk up to the machine and make changes to the firewall using cached password of the administrator who used the same GUI session before. Always lock the screen or exit Firewall Builder GUI when leaving computer.