Managing A Single Firewall Policy For Multiple Servers Using Firewall Builder - Page 2
Step 3 - Define cluster policy rules
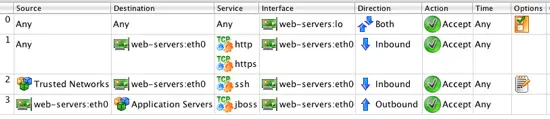
After you create the cluster, the Policy object is automatically opened in the Rules Panel. Make sure to create the rules in the cluster object, called web-servers in our example, and not in one of the individual firewalls that are members of the cluster. Remember we wanted both of our servers to have the following rules:
- Allow system to commuicate to its own loopback interface
- Allow inbound HTTP and HTTPS from anywhere to the server
- Allow inbound SSH from a specific set of trusted subnets
- Allow outbound connectivity to port 8009 (jboss) to a group of application servers
After you configure these rules in the web-servers Policy object the rules should look like this:
NOTE: For objects that are related to the firewall itself, such as interfaces, make sure to use the objects from the cluster when creating the rules. The cluster objects will automatically get translated to the correct object for the individual cluster members.
Step 4 - Compile and install rules
The next step is to compile and install the rules on our servers. When Firewall Builder compiles the cluster it will generate a firewall script for each of the cluster members including substituting the cluster objects used in the rules for the matching local object on the cluster member.
For example, the IP address for the eth0 cluster object is automatically translated to the correct address for web-01 (192.0.2.11) and web-02 (192.0.2.12).
You can see this substitution by inspecting the generated file for web-01 after the compile is completed. Note that the destination in the rule shown below is set to the IP address of web-01's eth0 interface.
echo "Rule 0 (eth0)"
#
$IPTABLES -A INPUT -i eth0 -p tcp -m tcp -m multiport \
-d 192.0.2.11 --dports 80,443 -m state --state NEW -j ACCEPT
Modifying rules
Now that you have a cluster setup to generate firewall policies for each of the server firewalls it is easy to make changes that affect all your servers. For example, to add a new rule to all members of the web-servers cluster to allow ICMP from the Trusted Networks object to servers simply add the rule in the cluster policy and compile and install it to the members.
Adding a new server to the cluster
To add a new server to the cluster you first need to create the firewall object to represent the server. You can do this manually, or you can follow the same duplication process we used to create the web-02 firewall object.
- Right-click on web-02 firewall and select Duplicate -> place in library User
- Edit the name of the newly created firewall object to web-03
- Click on the Host OS Settings and disable IPv4 Packet forwarding
- Double-click on web-03's IP object under the eth0 interface and set the IP address to 192.0.2.23 / 24
The next step is to add the new web-03 firewall object to the cluster.
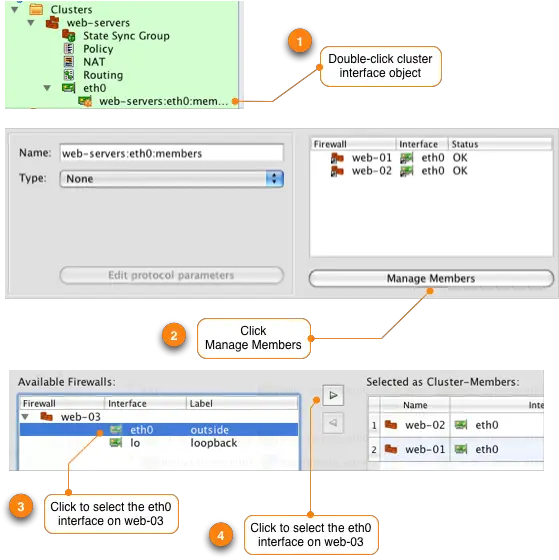
Repeat this process for the "lo" loopback interface. Remember the steps are:
- Double-click on the interface named web-servers:eth0:members
- Click on the Manage Members button at the bottom of the Editor Panel
- Click to select the "lo" interface under the web-03 object
- Click the right arrow > button to add the interface to the cluster member list
- Click Ok
Installing firewall policy on new server in cluster
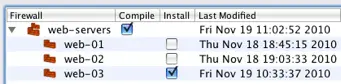
To deploy the firewall policy on web-03 you need to compile and install the cluster policy. Since the cluster policy hasn't changed we don't need to re-install the policy on web-01 or web-02 so we unselect them from the install list.
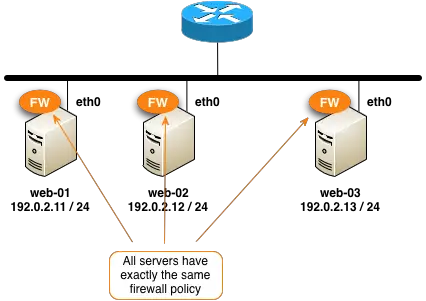
You can add and remove servers to the cluster as needed. Here's our configuration now that we have three servers in the cluster all running the same firewall rules.