How to Setup IKEv2 VPN Using Strongswan and Letsencrypt on Ubuntu
This tutorial exists for these OS versions
- Ubuntu 18.04 (Bionic Beaver)
- Ubuntu 16.04 (Xenial Xerus)
On this page
Strongswan is an open source multiplatform IPSec implementation. It's IPSec-based VPN solution that focuses on strong authentication method and mechanism, offers support for both IKEv1 and IKEv2 key exchange protocols, authentication based on X.509 certificates or pre shared keys, and secure IKEv2 EAP user authentication.
In this tutorial, we will show you step-by-step setup of the IPSec VPN server using Strongswan. We will create an IKEv2 VPN server with the 'EAP-MSCHAPv2' authentication and be using Letsencrypt certificates on Ubuntu 18.04 server.
Prerequisites
- Ubuntu 18.04
- Root privileges
What we will do?
- Install Strongswan on Ubuntu 18.04
- Generate SSL Letsencrypt
- Configure Strongswan
- Enable NAT and Port-Forwarding UFW Firewall
- Testing
Step 1 - Install Strongswan on Ubuntu
In this first step, we will install the strongswan IPsec implement software and all the required packages from the Ubuntu repository.
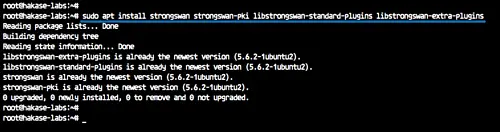
Update all repositories and install strongswan using the apt command below.
sudo apt update
sudo apt install strongswan strongswan-pki libstrongswan-standard-plugins libstrongswan-extra-plugins
Wait for all packages to get installed.
Step 2 - Generate SSL Letsencrypt
We will create the IKEv2 VPN server using a domain name 'vpn.hakase-labs.pw' and using certificates generated from letsencrypt.
In this step, we will install the letsencrypt tool 'certbot' and generate certificates for the server domain name 'vpn.hakase-labs.pw'.
Install 'certbot' letsencrypt tool.
sudo apt install certbot -y
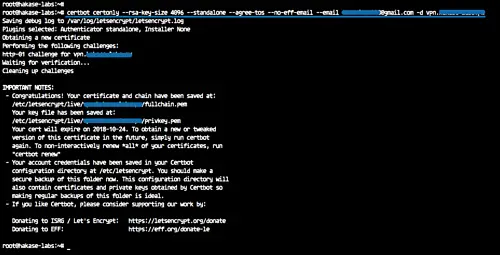
After the installation is complete, generate new SSL certificate files using the certbot command below.
certbot certonly --rsa-key-size 4096 --standalone --agree-tos --no-eff-email --email [email protected] -d vpn.hakase-labs.pw
Letsencrypt certificates for the vpn domain name 'vpn.hakase-labs.pw' have been generated, and are located at the '/etc/letsencrypt/live' directory.
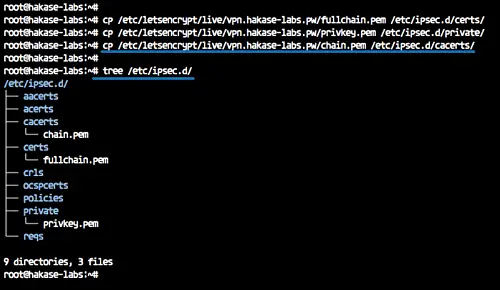
Next, we must copy the certificate files 'fullchain.pem', 'privkey.pem', and 'chain.pem' to the '/etc/ipsec.d/' directory.
Run commands below.
cp /etc/letsencrypt/live/vpn.hakase-labs.pw/fullchain.pem /etc/ipsec.d/certs/
cp /etc/letsencrypt/live/vpn.hakase-labs.pw/privkey.pem /etc/ipsec.d/private/
cp /etc/letsencrypt/live/vpn.hakase-labs.pw/chain.pem /etc/ipsec.d/cacerts/
All letsencrypt certificates for the Strongswan VPN named 'vpn.hakase-labs.pw' have been generated and copied to the '/etc/ipsec.d' directory.
tree /etc/ipsec.d/
Step 3 - Configure Strongswan
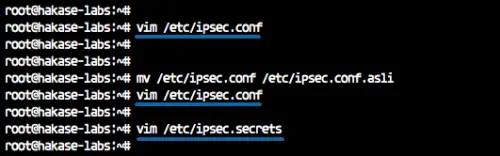
Backup the default configuration and create new one 'ipsec.conf' using vim editor.
mv /etc/ipsec.conf /etc/ipsec.conf.asli
vim /etc/ipsec.conf
Paste the configuration below.
#global configuration IPsec
#chron logger
config setup
charondebug="ike 1, knl 1, cfg 0"
uniqueids=no
#define new ipsec connection
conn hakase-vpn
auto=add
compress=no
type=tunnel
keyexchange=ikev2
ike=aes128-sha1-modp1024,aes128-sha1-modp1536,aes128-sha1-modp2048,aes128-sha256-ecp256,aes128-sha256-modp1024,aes128-sha256-modp1536,aes128-sha256-modp2048,aes256-aes128-sha256-sha1-modp2048-modp4096-modp1024,aes256-sha1-modp1024,aes256-sha256-modp1024,aes256-sha256-modp1536,aes256-sha256-modp2048,aes256-sha256-modp4096,aes256-sha384-ecp384,aes256-sha384-modp1024,aes256-sha384-modp1536,aes256-sha384-modp2048,aes256-sha384-modp4096,aes256gcm16-aes256gcm12-aes128gcm16-aes128gcm12-sha256-sha1-modp2048-modp4096-modp1024,3des-sha1-modp1024!
esp=aes128-aes256-sha1-sha256-modp2048-modp4096-modp1024,aes128-sha1,aes128-sha1-modp1024,aes128-sha1-modp1536,aes128-sha1-modp2048,aes128-sha256,aes128-sha256-ecp256,aes128-sha256-modp1024,aes128-sha256-modp1536,aes128-sha256-modp2048,aes128gcm12-aes128gcm16-aes256gcm12-aes256gcm16-modp2048-modp4096-modp1024,aes128gcm16,aes128gcm16-ecp256,aes256-sha1,aes256-sha256,aes256-sha256-modp1024,aes256-sha256-modp1536,aes256-sha256-modp2048,aes256-sha256-modp4096,aes256-sha384,aes256-sha384-ecp384,aes256-sha384-modp1024,aes256-sha384-modp1536,aes256-sha384-modp2048,aes256-sha384-modp4096,aes256gcm16,aes256gcm16-ecp384,3des-sha1!
fragmentation=yes
forceencaps=yes
dpdaction=clear
dpddelay=300s
rekey=no
left=%any
[email protected]
leftcert=fullchain.pem
leftsendcert=always
leftsubnet=0.0.0.0/0
right=%any
rightid=%any
rightauth=eap-mschapv2
rightsourceip=10.15.1.0/24
rightdns=1.1.1.1,8.8.8.8
rightsendcert=never
eap_identity=%identity
Save and exit.
Configuration details:
- Create a new IPSec VPN tunnel connection named 'hakase-vpn'.
- Specify the IKEv2 and ESP cipher suites for authentication.
- The 'left' server configuration using a domain name 'vpn.hakase-labs.pw' and using the letsencrypt certificate 'fullchain.pem' located at the '/etc/ipsec.d/certs' directory.
- The 'right' clients/remote setup with the EAP authentication method 'eap-mschapv2', assign the virtual IP address range '10.15.1.0/24' to all connected clients, and using public DNS Cloudflare and google.
Next, we need to edit the '/etc/ipsec.secrets' file to define the RSA server private key and EAP credentials.
Edit the 'ipsec.secrets' file using vim.
vim /etc/ipsec.secrets
And paste the configuration there.
: RSA "privkey.pem" hakase : EAP "hakase321@" tensai : EAP "tensai321@"
Save and exit.
Configuration details:
- Specify the RSA server private key using the letsencrypt certificate 'privkey.pem' located at the '/etc/ipsec.d/private' directory.
- Define the EAP user credentials format 'user : EAP "password"'.
The strongswan IPSec configuration has been completed, start the strongswan service and enable it to launch everytime at system boot.
systemctl start strongswan
systemctl enable strongswan
Step 4 - Enable NAT and Port-Forwarding UFW Firewall
In this step, we will enable the NAT mode, open ports that will be used for the strongswan IPSec VPN, and enable port-forwarding. We will be using the UFW firewall.
Before enabling the firewall on the server, we need to add the ssh service and strongswan UDP ports (500 and 4500) to the firewall service lists.
Run ufw firewall commands below.
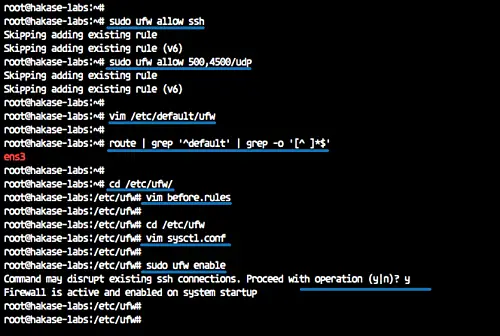
sudo ufw allow ssh
sudo ufw allow 500,4500/udp
The ssh service and strongswan ports have been added to the ufw firewall.
Next, we will enable NAT mode and port-forwarding on the UFW firewall by editing its configuration file.
Edit the default ufw configuration.
vim /etc/default/ufw
Change the 'DEFAULT_FORWARD_POLICY' to 'ACCEPT'.
DEFAULT_FORWARD_POLICY="ACCEPT"
Save and exit.
Now we need to check the network interface used for internet access using the route command below.
route | grep '^default' | grep -o '[^ ]*$'
You will get the network interface such as 'eth0', 'eth1', or 'ens3' etc.
Go to the '/etc/ufw' directory and edit the configuration file 'before.rules'.
cd /etc/ufw/
vim before.rules
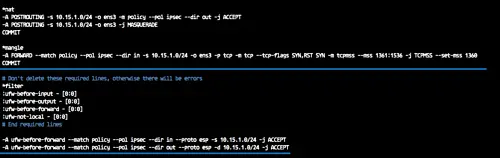
Paste the following nat and mangle configuration to the top of lines.
*nat -A POSTROUTING -s 10.15.1.0/24 -o ens3 -m policy --pol ipsec --dir out -j ACCEPT -A POSTROUTING -s 10.15.1.0/24 -o ens3 -j MASQUERADE COMMIT *mangle -A FORWARD --match policy --pol ipsec --dir in -s 10.15.1.0/24 -o ens3 -p tcp -m tcp --tcp-flags SYN,RST SYN -m tcpmss --mss 1361:1536 -j TCPMSS --set-mss 1360 COMMIT
And paste the custom chain ufw firewall under the '*filter' configuration.
*filter ..... -A ufw-before-forward --match policy --pol ipsec --dir in --proto esp -s 10.15.1.0/24 -j ACCEPT -A ufw-before-forward --match policy --pol ipsec --dir out --proto esp -d 10.15.1.0/24 -j ACCEPT
Save and exit.
Note:
- Change the interface 'ens3' with your own network interface.
- Change the Inetrnal/Private ip address as you want.
And for the port-forwarding configuration, edit the 'sysctl.conf' file present in the ufw directory.
cd /etc/ufw
vim sysctl.conf
Uncomment the 'net/ipv4/ip_forward' line.
net/ipv4/ip_forward=1
Save and exit.
Start and enable the ufw firewall.
sudo ufw enable
Type 'y' to confirm and press enter, and make sure there is no error. Then restart the strongswan service.
systemctl restart strongswan
And the UFW Firewall configuration for NAT mode and Port-Forwarding have been completed.
Step 5 - Testing
In this case, we will do test on MacOS X and Android phone.
On MacOS
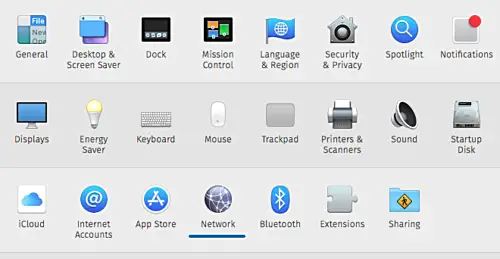
- Open the 'System Preferences' and click 'Network' menu.
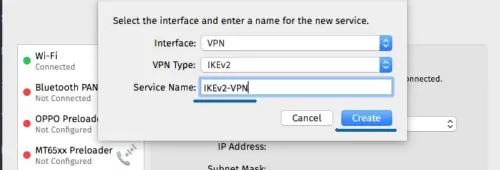
- Click the '+' button to create a new VPN connection.
- Interface: 'VPN'
- VPN Type: 'IKEv2'
- Service Name: 'IKEv2-vpn'
- On 'Server Address' and 'Remote ID', type the VPN domain name 'vpn.hakase-labs.pw'.
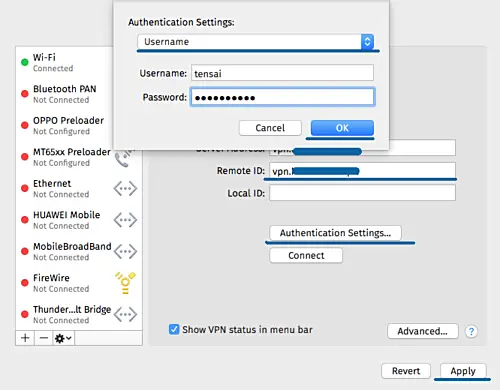
- Click 'Authentication Settings'.
- Authentication using a 'Username'.
- Type the username 'tensai' with password 'tensai321@'
- Click 'OK' and click 'Apply'.
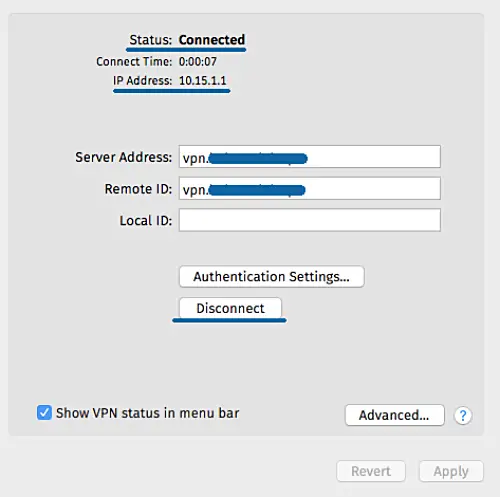
New IKEv2 VPN connection has been created on the client. Click the connect button.
And the client has been connected to the strongswan VPN server and has an internal/private IP address 10.15.1.1.
On Android
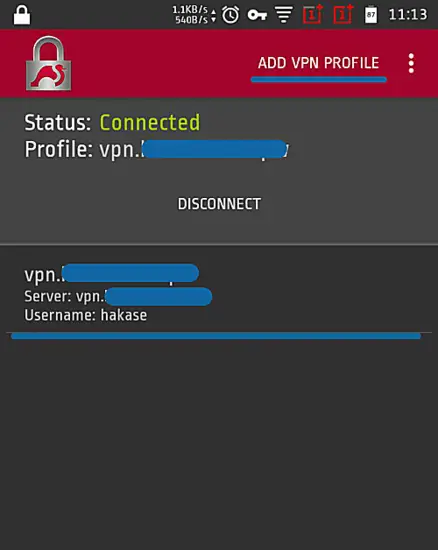
- Download and install the native strongswan android application from Google-Play.
- Add new VPN profile
- Type the server domain name 'vpn.hakase-labs.pw' and use the IKEv2 EAP Username and Password authentication.
Following is the result when we connected to the VPN server.
The IKEv2 IPSec-based VPN server has been created using Strongswan on Ubuntu 18.04 server.