How To Set Up And Integrate An Ubuntu 10.04 LTSPv5 Server Into A Windows 2008 Active Directory Domain
Introduction
With the current economic conditions, companies have been trying to do more with less by recycling old hardware and utilizing open source software. That's also true where I work. Between our call center, finance, distribution, warehouse, and sales departments over 50% of the company's employees are running on RHEL4 LTSP thin clients. Recently it was decided to update our LTSP environment from RHEL4 to Ubuntu 10.04 with LTSPv5. Using the following steps, I was able to setup and integrate an Ubuntu 10.04 LTSPv5 server into a Windows 2008 Active Directory domain.
Assumptions
It is assumed that you have a Windows 2008 Active Directory Domain setup and working properly along with a DHCP server. Your domain controller can be your DHCP server or you can setup a different box to distribute the DHCP leases. If your domain controller or DHCP server are not setup, please set these up first. It is also assumed that the reader has some basic Linux experience. You will need to know how to move around in the Linux terminal, install applications, and edit files using vi or nano.
Hardware
Ubuntu LTSP Server
Dell PowerEdge 2650
2 Dual Core Intel(R) Xeon(TM) CPU 1.80GHz CPU's
8 GB RAM
3 73 GB SCSI U320 10K Hard drives in RAID 5 configuration
Dual power supply
Thin Clients
Dell Optiplex GX260
1 GB RAM
On-board video
No HD
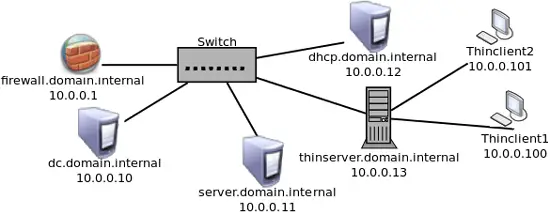
Network Layout
For the purpose of this tutorial, this is the layout of the domain.internal network on the 10.0.0.0/24 subnet.
dc.domain.internal
Windows 2008 Server running Active Directory and DNS
server.domain.internal
Windows 2003 Server hosting user home directories and file shares
thinserver.domain.internal
Ubuntu 10.04.2 server with LTSPv5
dhcp.domain.internal
CentOS 5.0 server running dhcpd
Ubuntu LTSP Installation
To install Ubuntu with LTSP, follow the instructions here.
If your server has more than 4 GB of RAM, make sure you install the Linux PAE Kernel.
sudo apt-get install linux-generic-pae linux-headers-generic-pae
Add thinserver to the Windows Domain
Before we add thinserver to the domain, we're going to have to install Samba along with some other packages.
sudo apt-get install samba smbclient winbind libpam-cracklib krb5-user
Make sure that thinserver is named correctly.
hostname
If the hostname command doesn't return thinserver.domain.internal, rename it to thinserver.domain.internal.
hostname thinserver.domain.internal
Edit the /etc/resolv.conf to use dc.domain.internal as the primary DNS server.
search domain.internal nameserver 10.0.0.10
On your domain controller create a host (A) record in your DNS for thinserver.
Verify that thinserver can resolve domain.internal:
nslookup domain.internal
The results should look something like this:
test@thinserver:~$ nslookup domain.internal
Server: 10.0.0.10
Address: 10.0.0.10
Name: domain.internal
Address: 10.0.0.10
Make sure that Samba and Winbind are not running:
/etc/init.d/smbd stop
/etc/init.d/winbind stop
Just to be safe lets backup the smb.conf, krb5.conf, and PAM common files. I like to append the date when I make a backup of a file so that I know when the changes were made.
d=`date "+%m%d%y"`
cp /etc/samba/smb.conf{,.$d}
cp /etc/krb5.conf{,.$d}
mkdir /etc/pam.d/backup
cd /etc/pam.d/
for file in `ls`;do cp $file{,.$d}; done
mv *.$d backup/
Edit the /etc/krb5.conf file to look like this:
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = DOMAIN.INTERNAL
default_keytab_name = FILE:/etc/krb5.keytab
default_tgs_entypes = rc4-hmac des-cbc-md5
default_tkt_entypes = rc4-hmac des-cbc-md5
permitted_entypes = rc4-hmac des-cbc-md5
dns_lookup_realm = true
dns_lookup_kdc = true
ticket_lifetime = 24h
forwardable = yes
[realms]
DOMAIN.INTERNAL = {
kdc = DC.DOMAIN.INTERNAL:88
default_domain = DOMAIN.INTERNAL
}
[domain_realm]
domain.internal = DOMAIN.INTERNAL
.domain.internal = DOMAIN.INTERNAL
[appdefaults]
forwardable = true
pam = {
minimum_uid = 16777216
debug = false
ticket_lifetime = 36000
renew_lifetime = 36000
krb4_convert = false
DOMAIN.INTERNAL = {
ignore_k5login = true
}
}
Edit the /etc/samba/smb.conf file to look like this:
[global] workgroup = DOMAIN password server = * realm = DOMAIN.INTERNAL local master = no security = ads idmap backend = tdb idmap uid = 16777216-33554431 idmap gid = 16777216-33554431 idmap config DOMAIN : backend = rid idmap config DOMAIN : range = 16777216-33554431 idmap cache time = 60 template homedir = /home/%u template shell = /bin/bash kerberos method = secrets and keytab dedicated keytab file = /etc/krb5.keytab winbind separator = + winbind use default domain = yes winbind refresh tickets = true winbind cache time = 10 winbind offline logon = true winbind enum users = Yes winbind enum groups = Yes passdb backend = tdbsam server string = Samba Server Version %v log file = /var/log/samba/%m.log max log size = 50
Moving forward it's advisable to have a second root terminal open just in case something doesn't work as expected. Happens to the best of us :o)
I would recommend creating a "linux_admins" group in Active Directory and adding it to the /etc/sudoers file. An alternative is to add the "domain admins" group and to login using the administrator account.
# Members of the admin group may gain root privileges %admin ALL=(ALL) ALL %linux_admins ALL=(ALL) ALL
Edit the PAM common file /etc/pam.d/common-account:
account sufficient pam_winbind.so use_first_pass cached_login account required pam_unix.so broken_shadow
Edit the PAM common file /etc/pam.d/common-auth:
auth [success=2 default=ignore] pam_unix.so nullok_secure auth [success=1 default=ignore] pam_winbind.so krb5_auth krb5_ccache_type=FILE cached_login try_first_pass auth requisite pam_deny.so auth required pam_permit.so
Edit the PAM common file /etc/pam.d/common-password:
password requisite pam_cracklib.so retry=3 minlen=8 difok=3 password [success=2 default=ignore] pam_unix.so obscure use_authtok try_first_pass sha512 password [success=1 default=ignore] pam_winbind.so use_authtok try_first_pass password requisite pam_deny.so password required pam_permit.so password optional pam_gnome_keyring.so
Edit the PAM common file /etc/pam.d/common-session:
session required pam_env.so session required pam_unix.so session required pam_winbind.so use_first_pass session required pam_limits.so session required pam_mkhomedir.so session [success=1 default=ignore] pam_succeed_if.so service in crond quiet use_uid
Edit the PAM common file /etc/pam.d/common-session-noninteractive:
session [default=1] pam_permit.so session requisite pam_deny.so session required pam_permit.so session optional pam_winbind.so cached_login session required pam_unix.so
Make sure that /etc/nsswitch.conf has the winbind entries for login.
passwd: compat winbind group: compat winbind shadow: compat
Now we're ready to add thinserver to the Windows Domain.
kinit [email protected]
net ads join -U administrator
net ads keytab create -U administrator
/etc/init.d/smbd start
/etc/init.d/winbind start
Verify that you are on the domain and that you can see all the users and groups in the domain.
wbinfo -u
wbinfo -g
getent passwd
You should now be able to log onto the server with your domain username and password. Verify that you're getting a Kerberos ticket.
klist